
Risk actors linked to lesser-known ransomware and malware tasks now use AI instruments as lures to contaminate unsuspecting victims with malicious payloads.
This improvement follows a development that has been rising since final 12 months, beginning with superior menace actors utilizing deepfake content material mills to contaminate victims with malware.
These lures have turn into broadly adopted by info-stealer malware operators and ransomware operations trying to breach company networks.
Cisco Talos researchers have found that the identical method is now adopted by smaller ransomware groups often known as CyberLock, Lucky_Gh0$t, and a brand new malware named Numero.
The malicious payloads are promoted by way of search engine marketing poisoning and malvertising to rank them excessive in search engine outcomes for particular phrases.
AI instrument impersonation
CyberLock is PowerShell-based ransomware delivered by a faux AI instrument web site (novaleadsai[.]com) posing because the authentic novaleads.app.
.jpg)
Supply: Cisco Talos
Victims are lured by presents of a free 12-month subscription, main them to obtain a .NET loader that deploys the ransomware.
As soon as executed on the sufferer’s machine, CyberLock encrypts information throughout a number of disk partitions, appending the .cyberlock extension on locked information.
The ransom notice calls for a $50,000 ransom to be paid within the hard-to-trace Monero cryptocurrency, claiming that the funds will assist humanitarian causes in Palestine, Ukraine, Africa, and Asia.
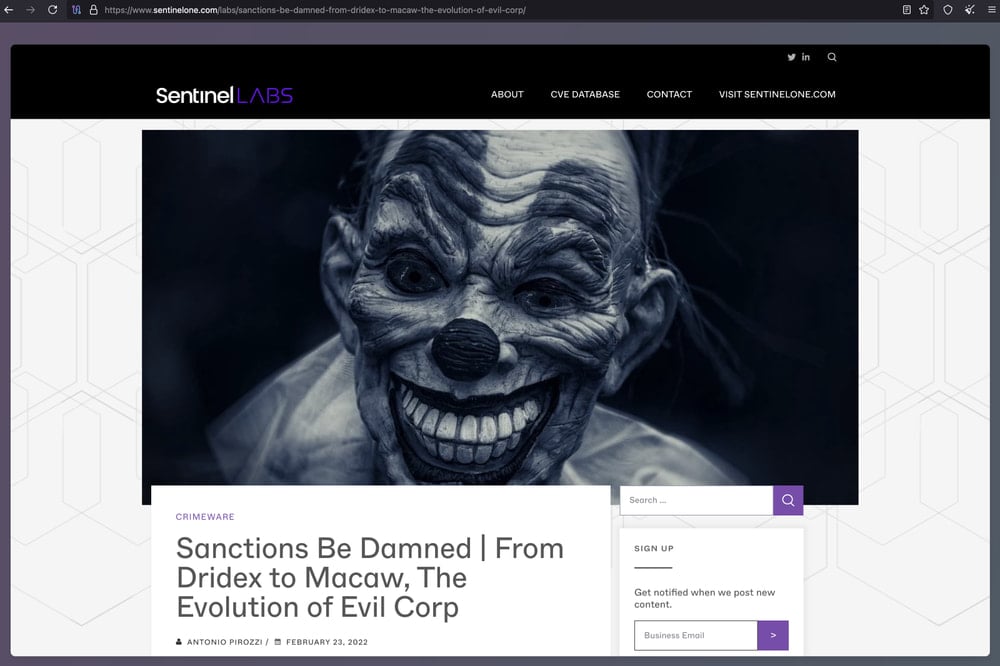
Supply: Cisco Talos
Lucky_Gh0$t is a brand new ransomware pressure derived from Yashma, which itself is predicated on the Chaos ransomware.
Cisco analysts noticed it being distributed as a faux ChatGPT installer (“ChatGPT 4.0 full model – Premium.exe”) packaged in a self-extracting archive.
The package deal contains authentic Microsoft open-source AI instruments alongside the ransomware payload, more likely to evade antivirus detection.
If executed, it encrypts information smaller than 1.2GB, appending random four-character extensions, whereas bigger information are changed with a same-size junk file and deleted.
Victims of Lucky_Gh0$t obtain a private ID and are instructed to contact the attacker by the safe messenger platform Session for ransom negotiations and decryption.
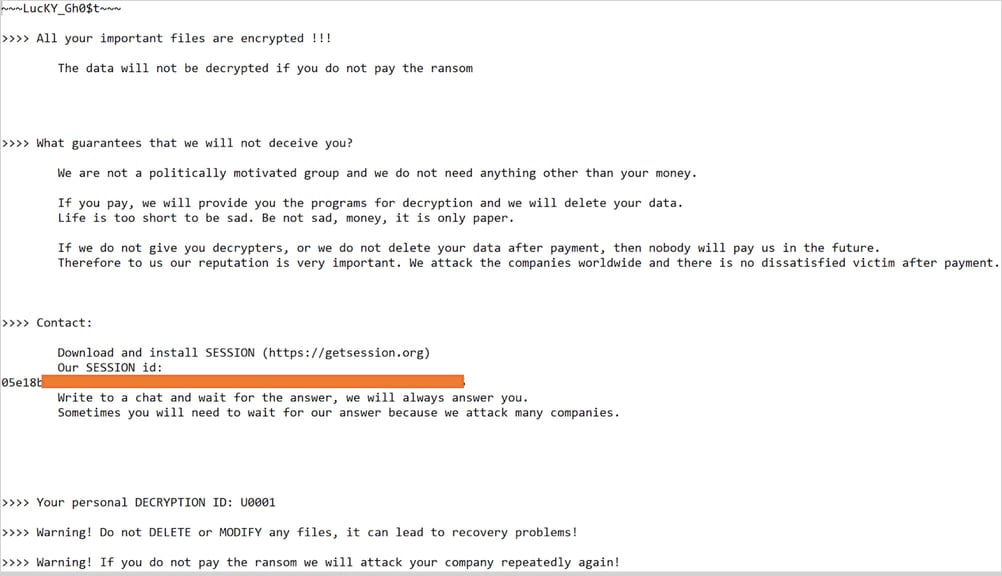
Supply: Cisco Talos
Lastly, a brand new malware referred to as Numero masquerades as an InVideo AI installer however is designed to assault Home windows programs.
The malware is delivered in a dropper containing a batch file, VB script, and an executable named wintitle.exe.
It executes in an infinite loop, constantly corrupting the sufferer’s graphical person interface by overwriting window titles, buttons, and content material with the numeric string “1234567890.”
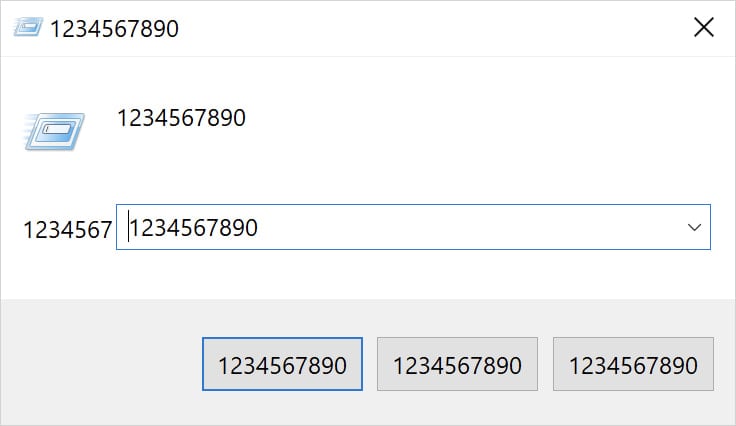
Supply: Cisco Talos
Though no knowledge is destroyed or encrypted by Numero, the malware renders Home windows programs it infects utterly unusable. On the similar time, the infinite loop it runs ensures the system is “locked” on this visually corrupted state.
As extra cybercriminals try and reap the benefits of folks’s rising curiosity in AI instruments, warning is suggested with information downloaded from doubtful web sites.
It will be extra prudent to stay to main AI tasks as a substitute of experimenting with new instruments and supply the installers from the official web sites as a substitute of following hyperlinks from promoted outcomes or social media posts.



