
CoinMarketCap, the favored cryptocurrency value monitoring web site, suffered an internet site provide chain assault that uncovered web site guests to a pockets drainer marketing campaign to steal guests’ crypto.
On Friday night, January 20, CoinMarketCap guests started seeing Web3 popups asking them to attach their wallets to the positioning. Nonetheless, when guests related their wallets, a malicious script drained cryptocurrency from them.
The corporate later confirmed menace actors utilized a vulnerability within the web site’s homepage “doodle” picture to inject malicious JavaScript into the positioning.
“On June 20, 2025, our safety group recognized a vulnerability associated to a doodle picture displayed on our homepage. This doodle picture contained a hyperlink that triggered malicious code by way of an API name, leading to an sudden popup for some customers when visited our homepage,” reads an announcement posted on X.
“Upon discovery, We acted instantly to take away the problematic content material, recognized the foundation trigger, and complete measures have been applied to isolate and mitigate the difficulty.”
“We will verify all methods are actually totally operational, and CoinMarketCap is secure and safe for all customers.”
Cybersecurity agency c/facet defined that the assault labored by the menace actors by some means modifying the API used by the positioning to retrieve a doodle picture to show on the homepage. This tampered JSON payload now included a malicious script tag that injected a pockets drainer script into CoinMarketCap from an exterior web site named “static.cdnkit[.]io”.
When somebody visited the web page, the script would execute and show a faux pockets join popup exhibiting CoinMarketCap branding and mimicking a reliable Web3 transaction request. Nonetheless, this script was truly a pockets drainer designed to steal related wallets’ property.
“This was a provide chain assault, which means the breach didn’ goal CMC’s personal servers however a third-party device or useful resource utilized by CMC,” explains c/facet.
“Such assaults are onerous to detect as a result of they exploit trusted parts of a platform.”
Extra particulars in regards to the assault got here later from a menace actor referred to as Rey, who stated that the attackers behind the CoinMarketCap provide chain assault shared a screenshot of the drainer panel on a Telegram channel.
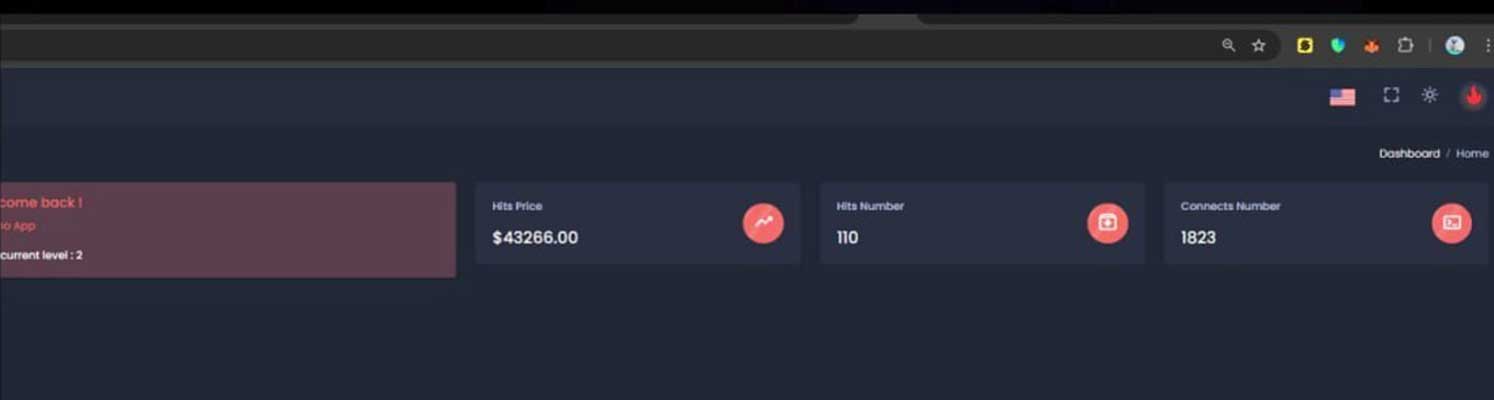
This panel indicated that $43,266 was stolen from 110 victims as a part of this provide chain assault, with the menace actors talking in French on the Telegram channel.
Supply: Rey
As the recognition of cryptocurrency has boomed, so has the menace from pockets drainers, that are generally utilized in assaults.
In contrast to conventional phishing, these kinds of assaults are extra usually promoted by way of social media posts, ads, spoofed websites, and malicious browser extensions that embrace malicious wallet-draining scripts.
Reviews point out that pockets drainers stole nearly $500 million in 2024 by way of assaults focusing on greater than 300,000 pockets addresses.
The issue has develop into so pervasive that Mozilla just lately launched a brand new system to detect pockets drainers in browser add-ons uploaded to the Firefox Add-on repository.
Patching used to imply complicated scripts, lengthy hours, and infinite hearth drills. Not anymore.
On this new information, Tines breaks down how trendy IT orgs are leveling up with automation. Patch sooner, scale back overhead, and give attention to strategic work — no complicated scripts required.



