
A brand new phishing equipment named ‘CoGUI’ despatched over 580 million emails to targets between January and April 2025, aiming to steal account credentials and fee knowledge.
The messages impersonate main manufacturers like Amazon, Rakuten, PayPal, Apple, tax businesses, and banks.
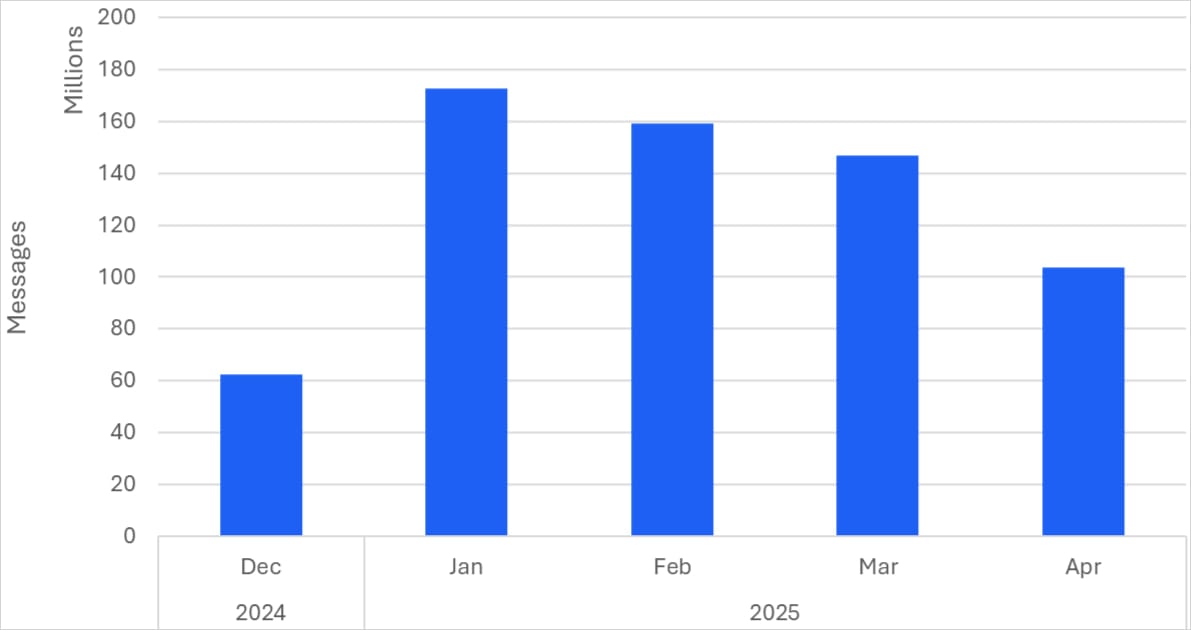
The exercise culminated in January 2025, the place 170 campaigns despatched 172,000,000 phishing messages to targets, however the next months maintained equally spectacular volumes.
Proofpoint researchers who found the CoGUI campaigns famous that it is the highest quantity phishing marketing campaign they presently monitor. The assaults primarily goal Japan, although smaller-scale campaigns had been additionally directed at the USA, Canada, Australia, and New Zealand.
CoGUI has been lively since at the least October 2024, however Proofpoint began monitoring it in December and onward.
Supply: Proofpoint
The analysts discovered a number of similarities to the Darcula phishing equipment, which has been linked to China-based operatives, and initially believed that the origin of the CoGUI assaults is identical.
Nevertheless, upon deeper examination, Proofpoint concluded that the 2 phishing kits are unrelated although they’re each utilized by Chinese language menace actors.
CoGUI assault chain
The assault begins with a phishing e mail impersonating a trusted model, usually having pressing topic strains requiring the recipient’s motion.
The messages embrace a URL that redirects to a phishing web site hosted on the CoGUI phishing platform, however the hyperlink solely resolves if the goal meets particular standards pre-defined by the attackers.
These standards embrace their IP deal with (location), browser language, working system, display decision, and machine kind (cell or desktop).
If the factors aren’t met, victims are redirected to the model’s authentic website that was impersonated to cut back suspicion.
Legitimate targets are redirected to a phishing web page that includes a faux login type that mimics the design of the true model, tricking victims into getting into their delicate info.
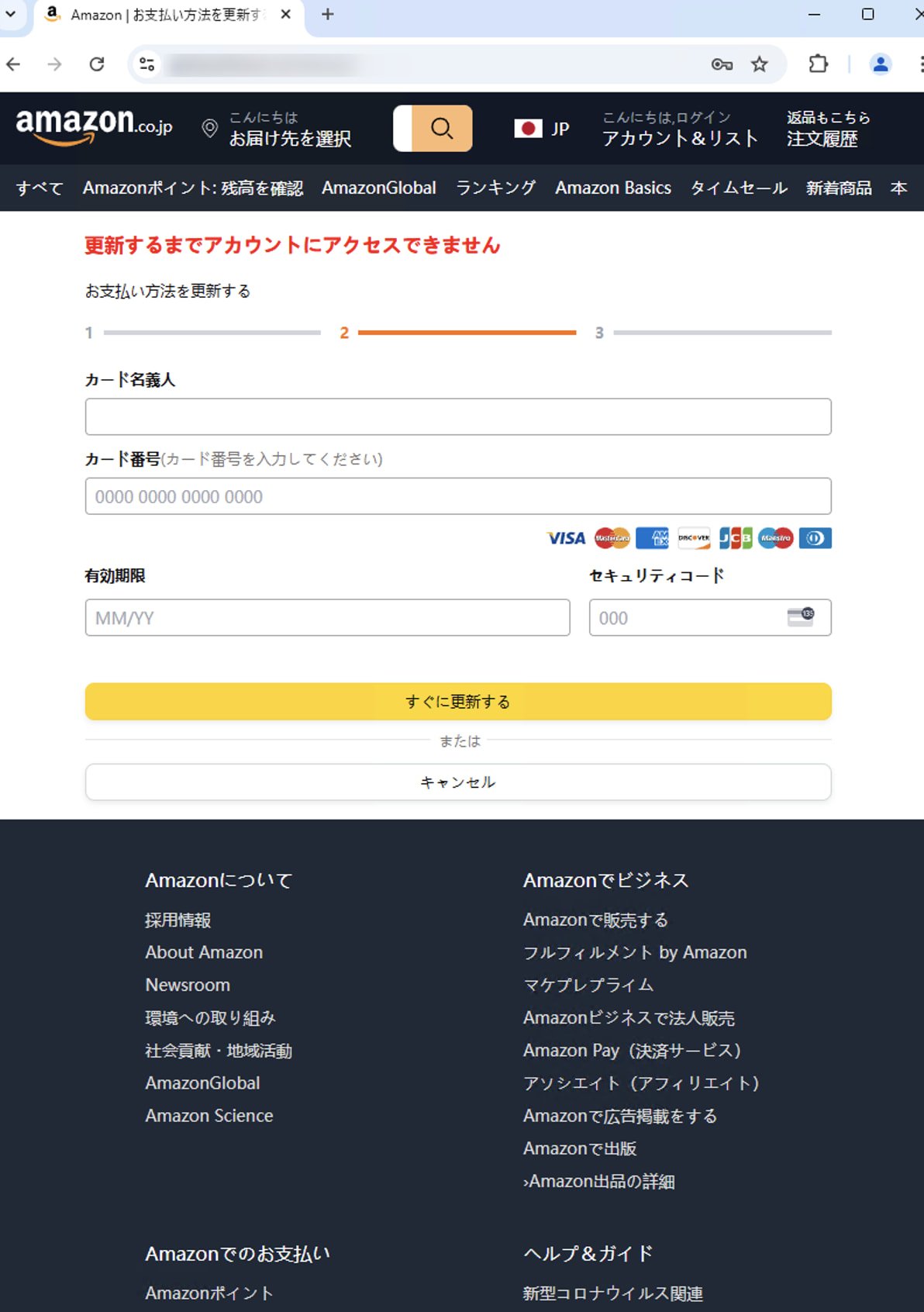
Supply: Proofpoint
Proofpoint has additionally discovered that CoGUI was behind smishing campaigns focusing on the USA with ‘excellent toll fee’ lures. Nevertheless, it famous that the majority of that exercise has now migrated to Darcula.
The researchers consider CoGUI facilitates the operations of a number of menace actors, primarily from China, who predominantly goal Japanese customers.
Nevertheless, the equipment could possibly be adopted by different cybercriminals with a unique focusing on scope at any second, leading to huge assault waves hitting different international locations.
One of the best ways to mitigate phishing dangers is rarely to behave with haste when receiving emails requesting pressing motion, and all the time log in to the claimed platform independently as a substitute of following embedded hyperlinks.



