In an period of more and more refined cyber-attacks, organizations are below strain to align their safety postures with real-world adversary habits. To satisfy this rising demand, Cisco has launched a globally accessible Menace Modeling Safety Evaluation service, delivered by means of Buyer Expertise’s skilled companies arm. Designed for security-conscious clients looking for a extra structured and threat-informed method to cyber safety, the service affords a sensible strategy to perceive, priorities, and defend towards the threats that matter most to them.
Menace Modeling, Reimagined for the Actual World
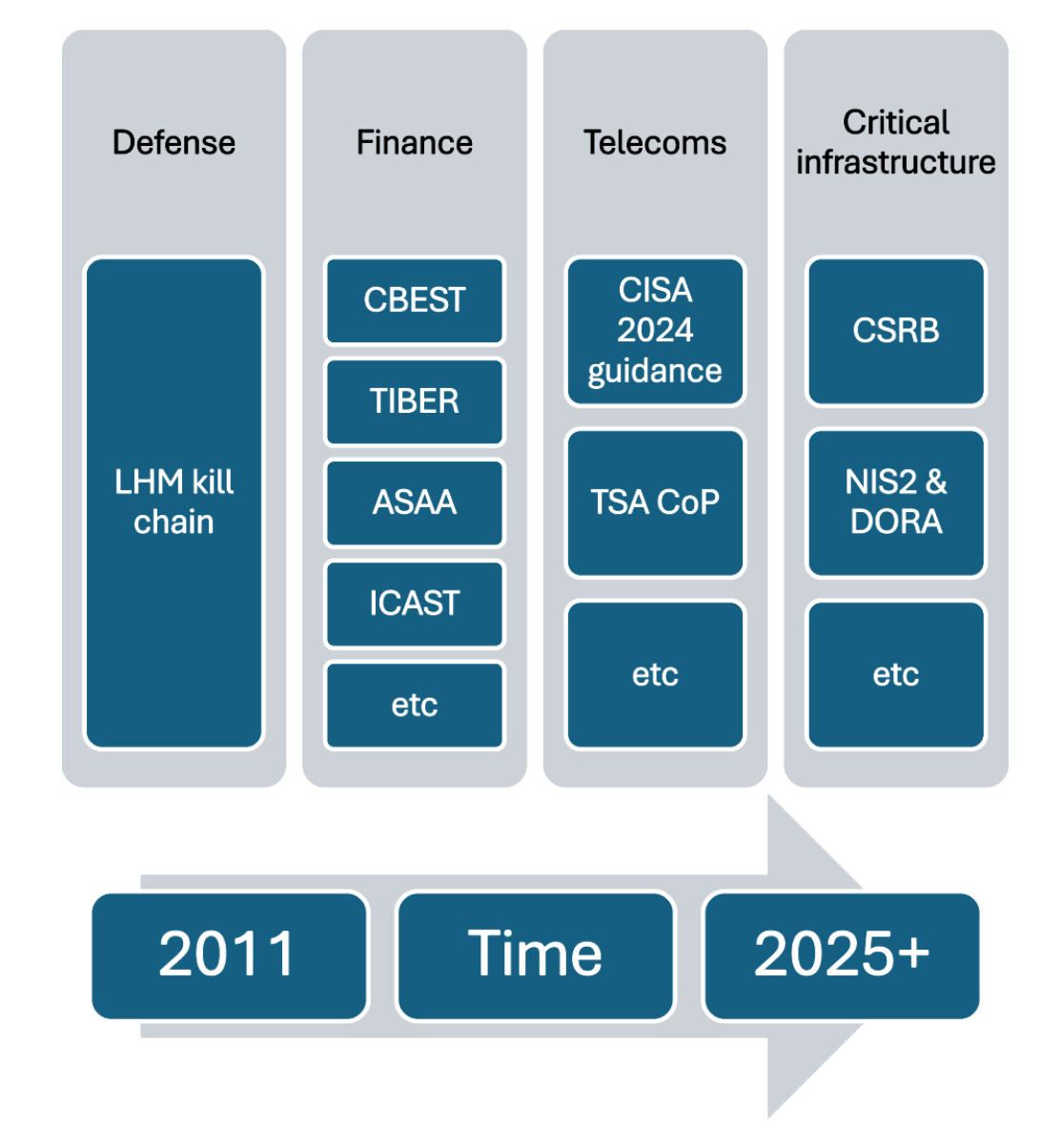
Cisco’s service is grounded in industry-accepted threat-centric frameworks, together with STRIDE (Spoofing, Tampering, Repudiation, Info Disclosure, Denial of Service, and Elevation of Privilege) and MITRE ATT&CK’s TTPs (Techniques, Strategies and Procedures), giving clients a structured and evidence-based lens by means of which to evaluate danger. Initially constructed to assist threat-led penetration testing frameworks such because the UK’s CBEST program which takes a threat-led method to monetary resiliency, the service has matured right into a complete method that permits organizations and their safety groups to map adversary habits on to the techniques that influence confidentiality, integrity and availability and which in flip, have the largest influence on income technology and value administration.
Whether or not you might be working crucial telecoms infrastructure, managing banking and different monetary information, or operating transport and industrial companies, the evaluation identifies how menace actors would goal these belongings – so you possibly can plan accordingly.
How Menace-Knowledgeable Frameworks Are Affecting Important Sectors At present

Menace-Led, Knowledge-Pushed, and Professional-Knowledgeable
One of many core differentiators of Cisco’s providing is the way it analyses the menace panorama by means of each geographic and industry-specific lenses, powered by the MITRE
ATT&CK framework. This ensures assessments are related, quite than theoretical, contemplating the widespread threats seen throughout related kinds of group and areas.
The service additionally contains customized analytics to foretell every asset’s “place within the kill chain”. This evaluation is predicated on a mixture of things together with:
- The asset’s location inside your community
- The kind of know-how and its configuration
- Identified vulnerabilities (CVE, KEV and many others.) and different weaknesses which have traditionally affected the asset
- How the asset is used and administered in your group
By understanding the place an asset sits in an attacker’s kill chain and what it protects, processes or shops, organizations can higher prioritize defenses and anticipate possible assault paths.
Think about How the International Menace Panorama Can Have an effect on Your Group
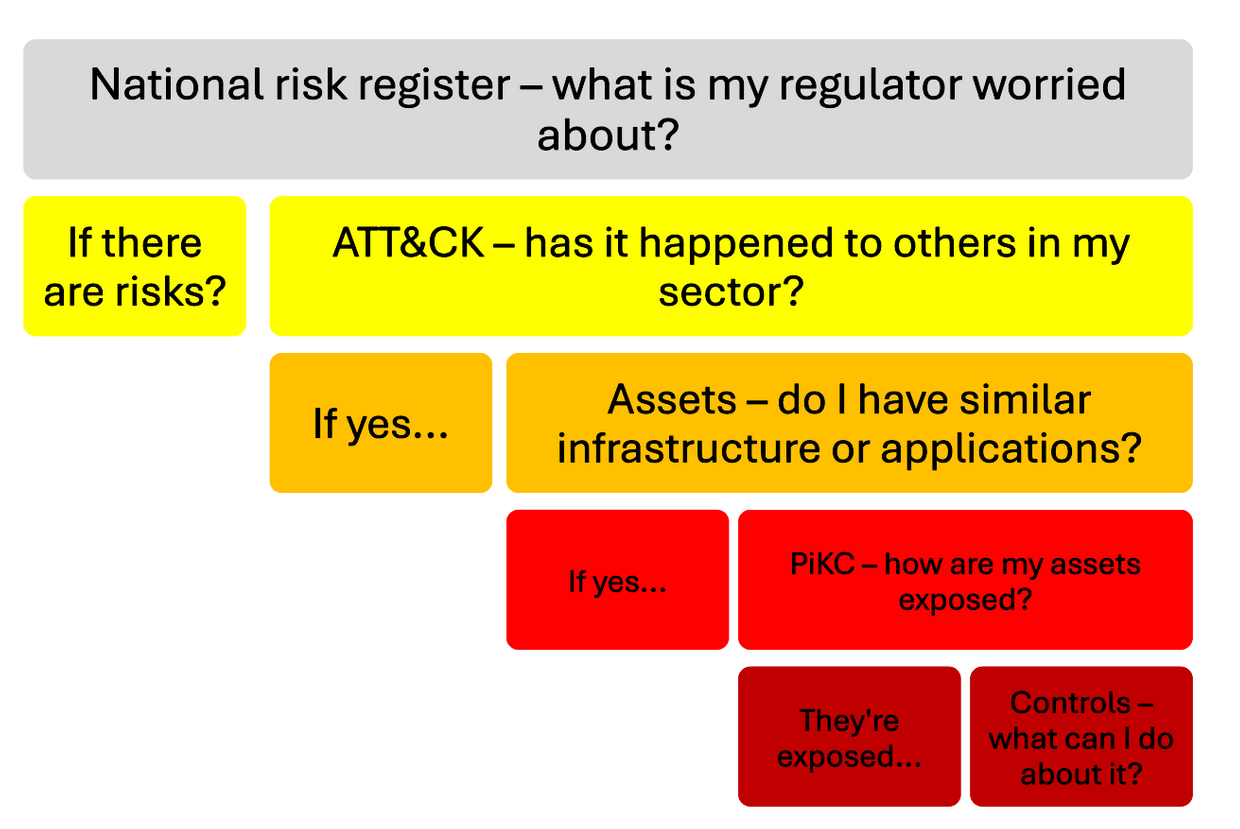
 Maybe most significantly, clients get entry to Cisco specialists with deep expertise in ATT&CK’s TTPs and vulnerability analysis. This experience ensures that the evaluation isn’t solely complete but in addition operationally real looking, supporting significant and defensible safety selections.
Maybe most significantly, clients get entry to Cisco specialists with deep expertise in ATT&CK’s TTPs and vulnerability analysis. This experience ensures that the evaluation isn’t solely complete but in addition operationally real looking, supporting significant and defensible safety selections.
From Idea to Observe: Actual-World Use Instances
Menace modeling is not only a tutorial train – it’s a foundational functionality that each group must be utilizing, to tell the selections they make in order higher put together for the menace panorama they inhabit. Cisco’s Menace Modeling Safety Evaluation helps organizations flip intelligence into motion. Widespread use circumstances embody:
- Defining Menace Intelligence necessities for a service supplier: As a substitute of drowning in information, organizations can outline particular intelligence priorities primarily based on adversaries more than likely to focus on their group.
- Enabling defensive practices for a financial institution: By understanding which methods adversaries use to use software program flaws, growth and engineering groups can construct with particular assault paths in thoughts – bringing safety to the beginning of the challenge lifecycle.
- Aligning Architectural Critiques to manage wants for a retailer: Safety structure opinions are sometimes generic. With menace modeling, opinions grow to be contextual, aligned to the ways, methods, and procedures (TTPs) which can be most related.
- Enhancing Detection Engineering for an airport: By mapping threats to belongings and figuring out assault paths, detection engineers can create extra focused and efficient guidelines and playbooks.
This service acts as a bridging perform. Taking summary vertical-specific elements that your group depends upon and translating them into software program and {hardware} artifacts and related information that menace actors would possibly search to focus on.
Designed for Resilience, Pushed by Organizational Necessities
Cisco’s Menace Modeling Safety Evaluation is greater than a technical train – it’s a strategic functionality for organizations that wish to align cyber safety efforts with organizational aims and operational resilience wants. Whether or not you might be regulated, security-mature, or simply starting to formalize your threat-informed protection, this service gives the perception and construction to make each a part of your safety program more practical.
In at this time’s menace panorama, resilience depends upon understanding how your adversaries function in addition to understanding your individual setting. Cisco’s new service affords that readability – decreasing the hole between intelligence, structure, and operations.
For organizations critical about defending what issues most, Cisco’s Menace Modeling Safety Evaluation is a strong step in the direction of a extra threat-informed future.


