
Cybercriminals are abusing Meta’s promoting platforms with pretend gives of a free TradingView Premium app that spreads the Brokewell malware for Android.
The marketing campaign targets cryptocurrency belongings and has been operating since a minimum of July twenty second by an estimated 75 localized advertisements.
Brokewell has been round since early 2024 and incorporates a broad set of capabilities that embrace stealing delicate knowledge, distant monitoring and management of the compromised machine.
Taking on the machine
Researchers at cybersecurity firm Bitdefender investigated the advertisements within the marketing campaign, which use the TradingView branding and visuals and lure potential victims with the promise of a free premium app for Android.
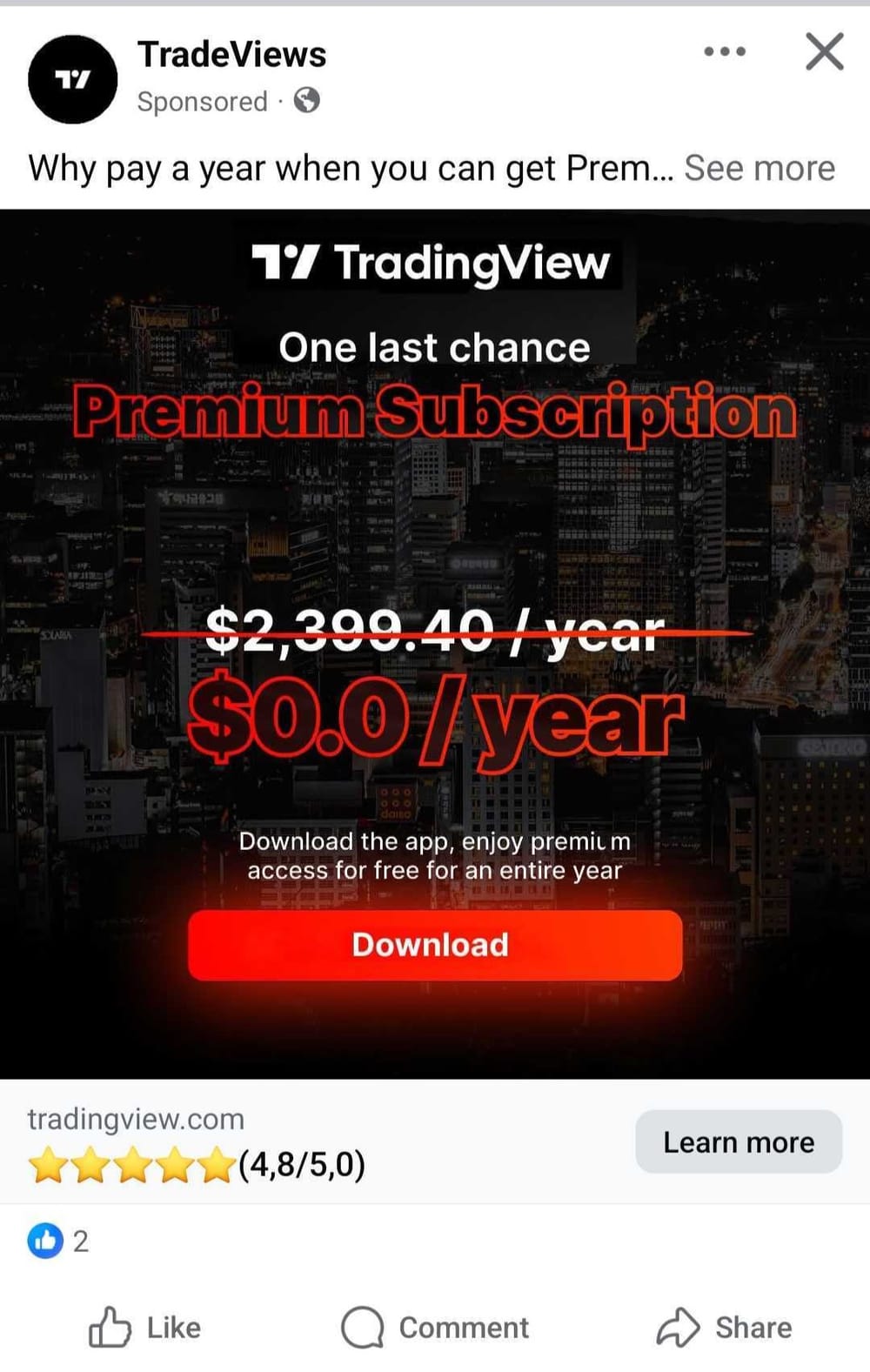
sourcce Bitdefender
They be aware that the marketing campaign was particularly designed for cellular customers, as accessing the advert from a unique working system would result in innocent content material.
Clicking from Android, nevertheless, redirected to a webpage mimicking the unique TradingView web site that supplied a malicious tw-update.apk file hosted at tradiwiw[.]on-line/
“The dropped utility asks for accessibility, and after receiving it, the display is roofed with a pretend replace immediate. Within the background, the applying is giving itself all of the permissions it wants,” the researchers say in a report this week..
Moreover, the malicious app additionally tries to acquire the PIN for unlocking the machine by simulating an Android replace request that wants the lockscreen password.
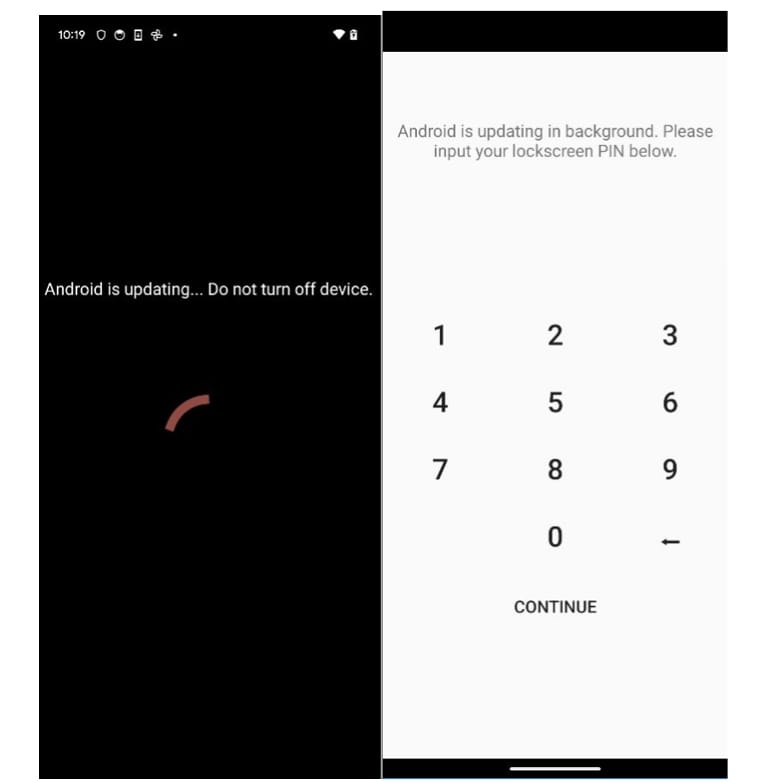
supply: Bitdefender
In response to Bitdefender, the pretend TradingView app is “a complicated model of the Brokewell malware” that comes “with an unlimited arsenal of instruments designed to watch, management, and steal delicate data:”
- Scans for BTC, ETH, USDT, checking account numbers (IBANs)
- Steals and exports codes from Google Authenticator (2FA bypass)
- Steals account by overlaying pretend login screens
- Information screens and keystrokes, steals cookies, prompts the digital camera and microphone, and tracks the placement
- Hijacks the default SMS app to intercept messages, together with banking and 2FA codes
- Distant management – can obtain instructions over Tor or Websockets to ship texts, place calls, uninstall apps, and even self-destruct
The researchers present a technical overview of how the malware works and an prolonged checklist of supported instructions that features greater than 130 rows.
Bitdefender says that this marketing campaign is a component of a bigger operation that originally used Fb advertisements impersonating “dozens of well-known manufacturers” to focus on Home windows customers.



