
Right this moment’s menace panorama, assault surfaces are increasing quicker than most safety groups can monitor. Each new cloud asset, uncovered API, forgotten subdomain, or misconfigured service turns into a possibility for an attacker to use.
Fashionable menace actors are leveraging Assault Floor Administration (ASM) to map out your digital footprint earlier than you even notice what’s uncovered. Via automated reconnaissance, asset discovery instruments, and open-source intelligence, they’re considering like purple teamers, performing like bug bounty hunters, and exploiting gaps in real-time.
The excellent news is you possibly can beat them at their very own sport.
This text explores how Sprocket Assault Floor Administration Device was constructed to grasp the attacker playbook and reclaim visibility and management over your increasing assault floor.
Sprocket Safety CEO, Casey Cammilleri, shares the distinction between Sprocket ASM and different instruments out there may be “Seeing the hacker’s perspective and a heavyweight on change detection. What has modified from yesterday and does it impression my safety? That is how we have considered constructing [Sprocket] ASM.”
The Attacker’s Perspective: Mapping Your Assault Floor
An attacker’s perspective of ASM mirrors that of a respectable safety skilled, with gathering intelligence or discovery. Because of publicly out there instruments and automation, discovering uncovered belongings, ignored endpoints, and shadow IT is simpler than ever for an attacker. Adversaries can shortly assemble an in depth map of your external-facing infrastructure.
Within the Sprocket Safety Pink Teamers’ expertise, most organizations unintentionally expose greater than they notice. Legacy dev environments, deserted domains, or forgotten SaaS integrations are all low-hanging fruits that attackers love. They’ll construct their very own ASM workflows utilizing a mix of open-source instruments, like Amass, and customized scripts to automate these findings at scale.
If an attacker has a extra up-to-date or correct map of your infrastructure than your personal, that’s the place the true hazard lies.
Use Case: Broadcom’s VMware ESXi Vulnerability Exploits (2023-2024)
Risk actors launched mass exploitation campaigns towards hundreds of internetexposed VMware ESXi servers utilizing recognized vulnerabilities.
These flaws had been actively exploited within the wild, permitting attackers on a digital machine with administrative privileges to flee the sandbox and execute code on the host system. Regardless of patches being out there, over 37,000 internet-exposed VMware ESXi servers remained susceptible, highlighting the dangers of unpatched, publicly accessible belongings.
“If it’s uncovered to the web, you higher deal with it prefer it’s already underneath assault. Repeatedly scan your exterior assault floor as if you happen to’re the attacker. Flag any highvalue belongings after which patch, isolate, or take away them. Don’t look ahead to the headlines. Act as quickly as a vulnerability is disclosed earlier than it’s exploited.” – Michael Belton, Head of Service Supply at Sprocket Safety.
Are you able to see what a hacker would see if that they had free reign over your assault floor?
Take the following step in turning into safer by creating an account with Sprocket ASM.
Sprocket ASM: Turning Recon into Prevention
If attackers can map your infrastructure, then it’s essential to do the identical solely quicker, deeper, and repeatedly. Sprocket ASM Device was designed to provide the similar reconnaissance capabilities attackers depend on, however with context, validation, and steady monitoring. As a substitute of manually going via asset inventories or reacting to alerts after the actual fact, you need to use Sprocket ASM to see what attackers see in actual time.
Cammilleri’s insights are “If in case you have ASM, you possibly can spend much less time in discovery phases and transfer straight into testing and validation phases. You may be extra environment friendly and scalable in your offensive testing.”
Profitable ASM isn’t nearly visibility although. It’s about actionable insights. Many organizations miss key exposures as a result of they rely too closely on inner CMDBs or legacy inventories. By the point these methods catch up, attackers could already be exploiting an ignored dev occasion or forgotten S3 bucket.
The important thing to turning recon into prevention? Operationalizing ASM. Integrating it into every day workflows, connecting it with vulnerability administration, and making certain your group acts on exposures with the urgency that an attacker has already found them.
For those who don’t monitor your digital infrastructure from the skin in, another person will.
Easy methods to Get Began: Beat the Dangerous Guys to Your Blind Spots
Sprocket ASM Device was created by penetration testers who perceive attacker behaviors. Defenders want the identical perspective and pace as their adversaries to remain safe. This no-cost software delivers unparalleled visibility into your assault floor and offers perception into the evolving surroundings.
By revealing what attackers can exploit, our software permits your group to behave proactively and mitigate dangers earlier than they escalate.
“It’s the identical engine that our purple group and testers use of their steady pentesting follow. You are going to get notifications on new discoveries and modifications,” shares Cammilleri, “However then you possibly can seed the ASM with extra belongings you personal and handle.
If there’s one thing that an attacker can be completely blind to on the Web, you can nonetheless feed in that info into the ASM and begin monitoring it for modifications and safety points.”
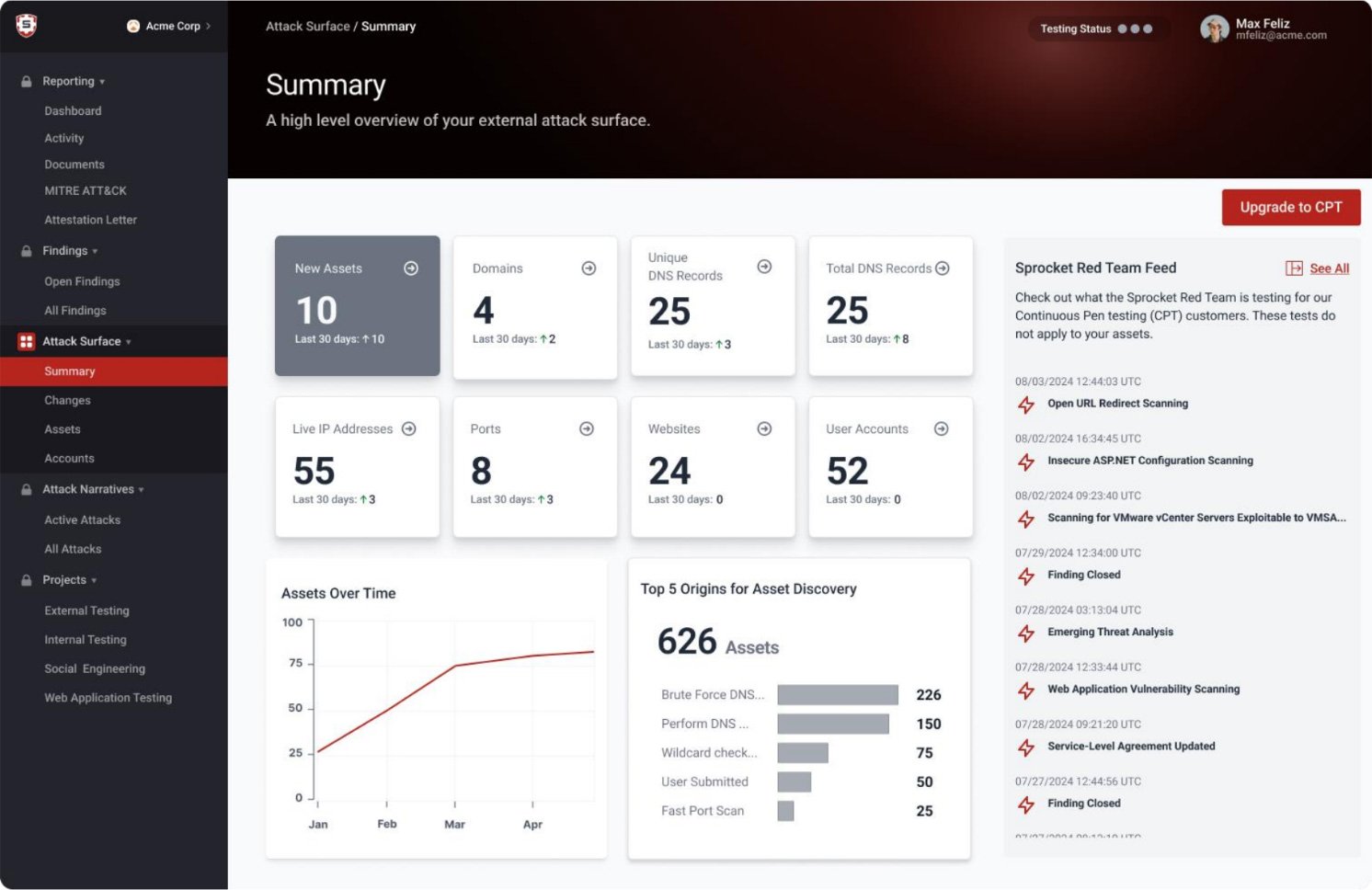
After creating your free account, you possibly can:
✓ Uncover all of your uncovered belongings — domains, IP addresses, providers, and way more — mechanically.
✓ Minimize via the noise and deal with what issues most with clear, actionable danger priorities.
✓ Achieve management of your safety posture with proactive asset discovery and efficient administration
Watch our complete ASM software demo to uncover much more advantages of using Sprocket ASM.
Take the Offensive: Shut Your Gaps
Attackers aren’t ready for permission. They’re already scanning, mapping, and exploiting uncovered belongings. For those who’re not taking a look at your assault floor the way in which an attacker would, you’re already at an obstacle. You can not safe what you don’t know exists.
Unknown belongings, shadow IT, and misconfigured providers are the weak hyperlinks that attackers love to search out, and conventional safety instruments typically miss.
That’s why visibility is foundational. Use visibility to harden, not hurt, by repeatedly discovering your exterior assault floor, prioritizing publicity by real-world danger, and shutting gaps earlier than adversaries exploit them.
With options like Sprocket ASM, you possibly can cease taking part in catch-up and begin seeing your infrastructure the way in which attackers do and that’s how one can beat them.
Sponsored and written by Sprocket Safety.


