Your safety is a muscle. You spend money on its power with Firewalls, XDR, Risk Intelligence, Observability and extra. However how have you learnt it should maintain up below actual stress? You let an expert sparring associate check it.
October is Cybersecurity Consciousness Month – a really perfect second to go proactive.
Right here’s how Cisco’s Evaluation and Penetration Testing (APT) workforce mirrors actual attacker tradecraft (safely), turns findings into enterprise outcomes, and how one can begin constructing offensive abilities at this time with the Cisco Certificates in Moral Hacking program.
Why “assume like an adversary” now
Safety is strongest when it’s examined towards the methods attackers truly work. Penetration testing is the managed, licensed rehearsal of these techniques – executed with guardrails – so you’ll be able to uncover and repair points earlier than they’re exploited. There’s a customary methodology being adopted however there may be at all times the underlying theme “What occurs if I do that….” and pondering exterior the field. Through the Cybersecurity Consciousness Month, many organizations revisit fundamentals; probably the most precious fundamental is to validate assumptions with adversary-minded testing.
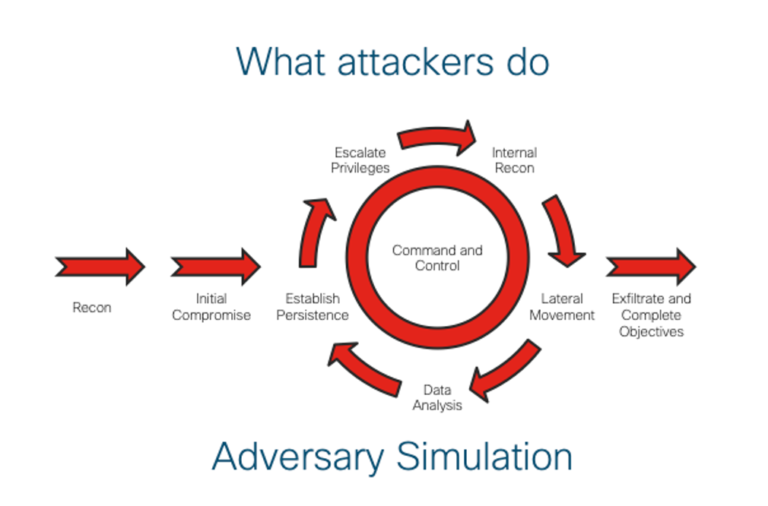

Determine 1 – Cisco APT Adversary Simulation Assault Circulate
Pen check vs. crimson workforce vs. vulnerability scan (and why it issues)
- Vulnerability scan: Automated discovery of recognized points. Quick, broad, low depth.
- Penetration check: Human-led exploitation makes an attempt for the agreed-upon scope to reveal the impression of found vulnerabilities. Publicity discovery centered.
- Purple workforce: Goal-driven simulation towards individuals, course of, and know-how—usually throughout longer time home windows and with detection evasion. Assault detection and response centered.
Cisco presents all three, however this sequence focuses on Penetration Testing & Purple Teaming – the place human ingenuity issues most.
How Cisco executes – safely and credibly
- Scoping & Guidelines of Engagement (ROE). We outline targets, success standards, time home windows, communications, and “cease circumstances.” Security and enterprise continuity come first. Important findings reported instantly.
- Risk-informed method. Based mostly on the shopper’s high of thoughts considerations, trade vertical, and deployed infrastructure. For community penetration testing and Purple Staff workouts, we map hypotheses to MITRE ATT&CK® techniques related to your setting and sector.
- Proof with out disruption. We craft minimal proof-of-concepts (PoCs) to validate exploitability – no dangerous stunts, no noisy chaos. Flexibility to conduct particular testing at most well-liked instances.
- Purple-team loops. When acceptable, we work immediately together with your safety operations heart (SOC). As we execute a way, we assist your defenders see what it appears to be like like of their instruments. This usually means constructing and testing detection guidelines dwell of their SIEM, like Splunk, to make sure they’ll spot the actual factor.
- Motion-ready reporting. Findings are prioritized by chance × impression. We offer clear remediation steerage and, crucially, detection logic. This could embrace ready-to-use search queries and correlation guidelines for platforms like Splunk, empowering your workforce to right away hunt for and alert on the TTPs we used.
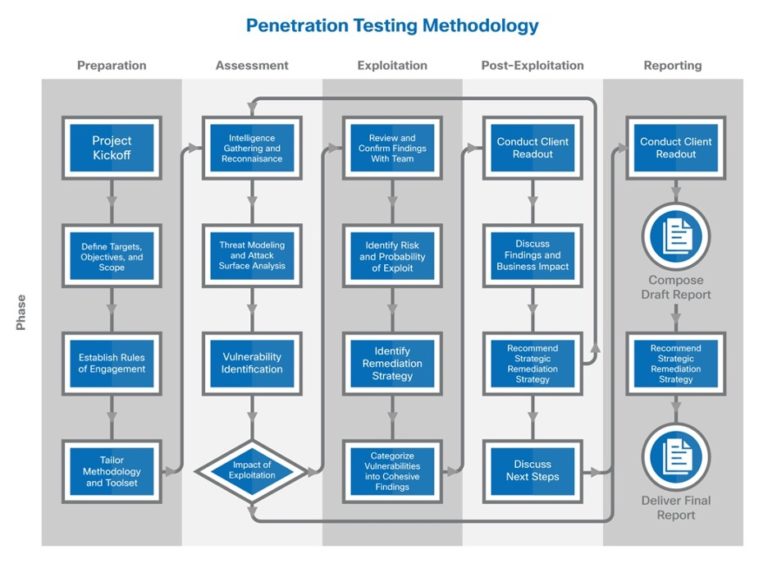

Determine 2 – Cisco APT Penetration Check Methodology
What we discover most frequently (The Three Widespread Traps We See within the Wild)
- Authentication Exposures. Weak passwords….nonetheless! (e.g. Password123, Company123, Fall2025!), multi-factor authentication (MFA) blind spots, token reuse, weak lockout insurance policies, over-privileged service accounts.

Determine 3 – Cisco APT Working “Password Spray” Assault
-
- Influence: This implies a single compromised credential might give an attacker the ‘keys to the dominion.’ Harder to detect nefarious exercise when legitimate credentials are getting used.
- Software points. Lacking patches, lack of enter validation, insecure direct object reference (IDOR), Server-Facet Request Forgery (SSRF), deserialization flaws, JWT weaknesses – usually in APIs.
- Influence: Unauthorized entry to vital knowledge or programs. Important knowledge cannot solely be seen but additionally modified.
- Cloud misconfigurations. Public objects, permissive roles, unmanaged workload identities, uncovered construct pipelines.
- Influence: Unauthorized entry to delicate data. Delicate data could be seen or modified.
- Delicate knowledge publicity. Important system configuration data (i.e. passwords), delicate buyer Personally Identifiable Data (PII), confidential company tasks, and many others.
- Influence. The impression of exposing delicate knowledge consists of extreme monetary losses, authorized liabilities, and reputational injury for organizations, whereas people can endure from identification theft, monetary fraud, and lack of privateness.
Turning findings into outcomes executives care about
- Enterprise impression framing. We hyperlink technical threat to affected processes, knowledge, and regulatory publicity. At undertaking kickoff, vital enterprise capabilities and the supporting infrastructure are recognized.
- Prioritized roadmap. “Quick wins” (config modifications, management toggles) vs. “strategic fixes” (identification tiering, segmentation). Penetration testing and Purple Staff outcomes identifies short-term priorities to considerably enhance safety posture.
- Metrics that matter. Dwell time discount, management protection, detection constancy, and closure SLAs.
Construct the skillset: Cisco Certificates in Moral Hacking is your on-ramp
When you’re interested by how this work truly feels, begin free with the Moral Hacker course at netacad.com – a part of the Cisco Certificates in Moral Hacking program. You’ll cowl recon, net vulnerabilities, protected exploitation fundamentals, and reporting practices. Cisco Certificates in Moral Hacking can be a robust basis for superior certs like OSCP or CEH.
Begin studying free: Go to netacad.com → “Moral Hacker”.
Validate your abilities: Try a CTF problem on Cisco U. to earn your Cisco Certificates in Moral Hacking.
Join with like-minded friends: Ask questions if you’re caught, and share ideas that may assist others within the Cisco Certificates in Moral Hacking Neighborhood.
The place to go subsequent
- Prepared to check with guardrails? Discover Cisco Penetration Testing & Purple Teaming providers and request a scoped engagement. Contact your Cisco consultant.
- Need extra TTP element? Coming quickly on this weblog sequence, up subsequent: From Recon to Preliminary Entry – a more in-depth take a look at early-phase methods and easy methods to cease them.
Ethics & security notice: All testing described is carried out below express authorized authorization, outlined scope, and strict ROE to guard consumer programs and knowledge.


