
A weak spot in Apple’s Safari internet browser permits menace actors to leverage the fullscreen browser-in-the-middle (BitM) method to steal account credentials from unsuspecting customers.
By abusing the Fullscreen API, which instructs any content material on a webpage to enter the browser’s fullscreen viewing mode, hackers can exploit the shortcoming to make guardrails much less seen on Chromium-based browsers and trick victims into typing delicate knowledge in an attacker-controlled window.
SquareX researchers noticed a rise use of this sort of malicious exercise and say that such assaults are significantly harmful for Safari customers, as Apple’s browser fails to correctly alert customers when a browser window enters fullscreen mode.
“SquareX’s analysis workforce has noticed a number of cases of the browser’s FullScreen API being exploited to deal with this flaw by displaying a fullscreen BitM window that covers the father or mother window’s handle bar, in addition to a limitation particular to Safari browsers that makes fullscreen BitM assaults particularly convincing,” describes the report.
How BitM works
A typical BitM assault includes tricking customers into interacting with an attacker-controlled distant browser that reveals a reputable login web page. That is achieved via instruments like noVNC – an open-source VNC browser shopper, which opens a distant browser on prime of the sufferer’s session.
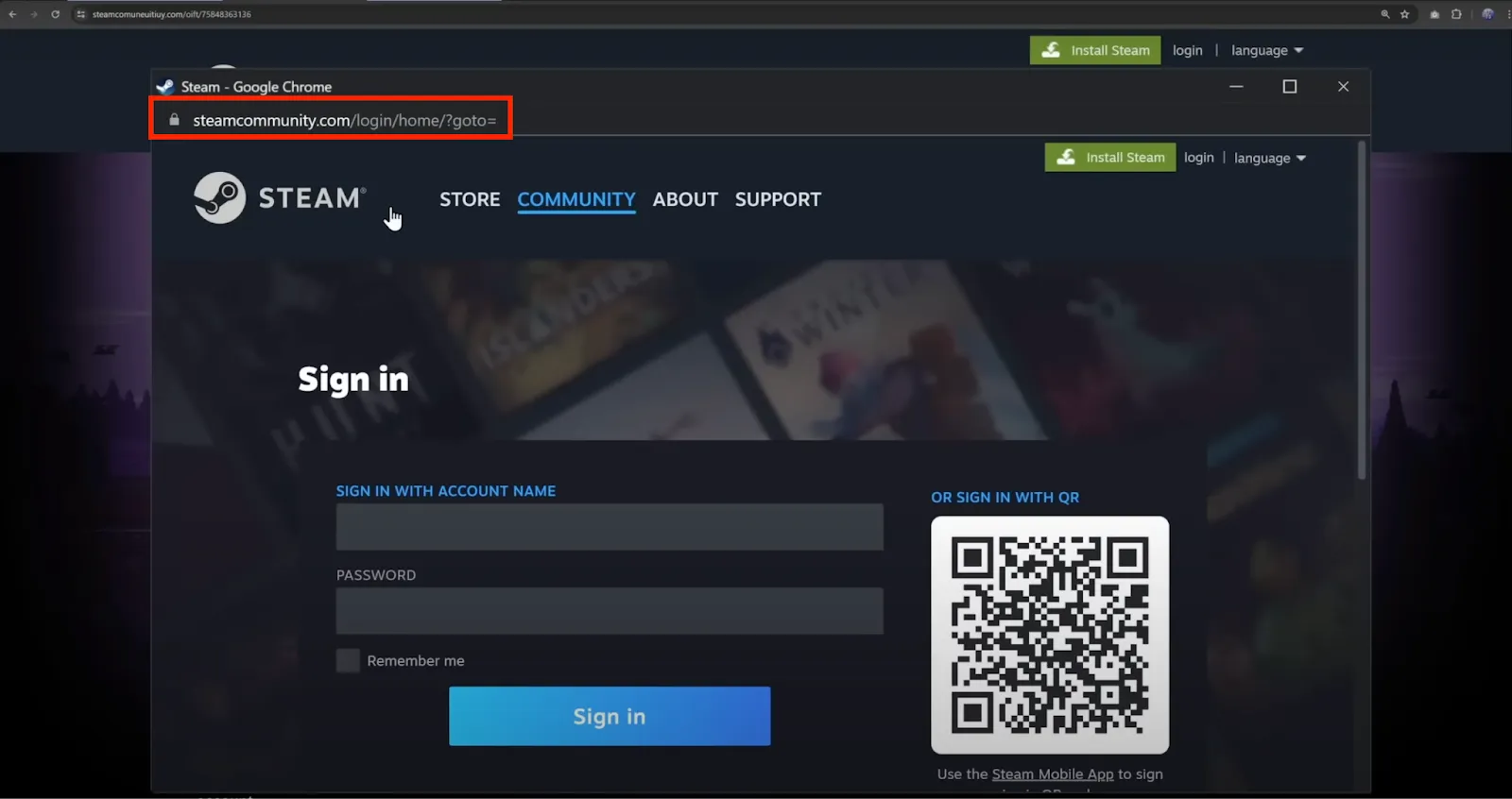
Supply: SquareX
For the reason that log in course of occurs within the attacker’s browser, the credentials are collected however the sufferer additionally efficiently accesses their account unaware of the theft.
The assault nonetheless requires tricking the sufferer into clicking on a malicious hyperlink that redirects them to a pretend web site impersonating the goal service. Nonetheless, this may be simply achieved via sponsored adverts in internet browsers, social media posts, or feedback.
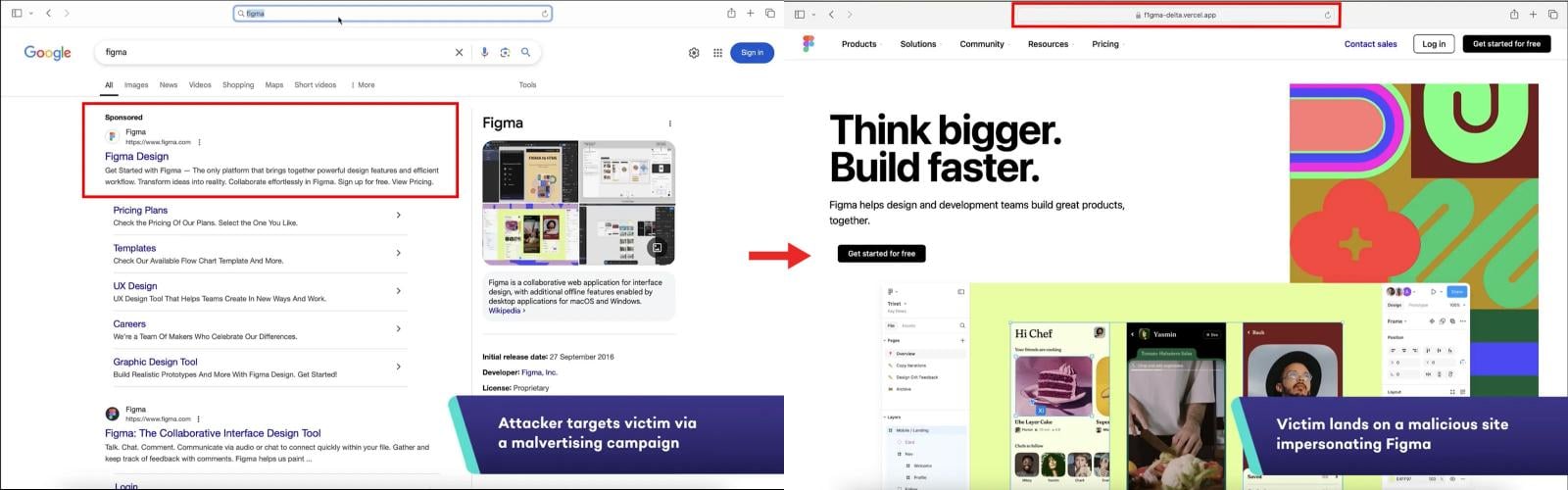
Supply: SquareX
Fullscreen deception
If customers miss the suspicious URL within the browser bar and click on on the log in button, the BitM window turns into lively. Till triggered, the window stayed hidden from the sufferer in minimized mode.
If customers miss the suspicious URL within the browser bar and click on on the log in button, which prompts the BitM window that was hidden from the sufferer in minimized mode.
As soon as activated, the attacker-controlled browser window enters fullscreen mode and covers the pretend web site, exhibiting to the person the reputable web site they needed to entry.
Safety options like EDRs or SASE/SSE gained’t set off any warnings when this occurs, because the assault abuses normal browser APIs.
The researchers clarify that Firefox and Chromium-based browsers (e.g. Chrome and Edge) present an alert at any time when fullscreen is lively. Though many customers could miss the warning, it’s nonetheless a guardrail that lowers the danger of a BitM assault.
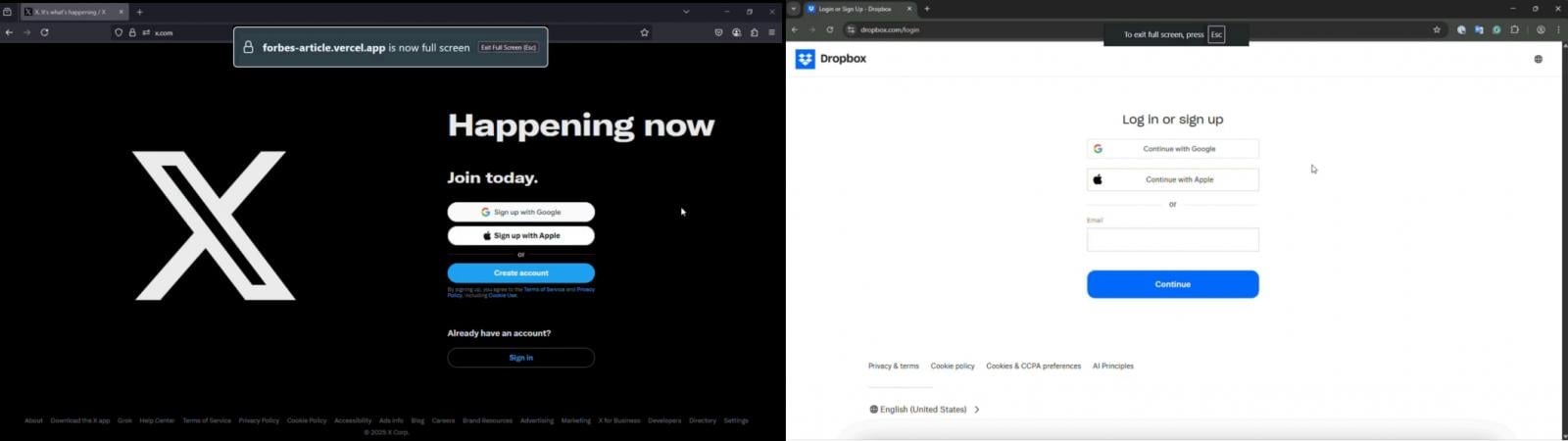
Supply: SquareX
Nonetheless, on Safari there’s no alert and the one signal of a browser getting into fullscreen mode is a “swipe” animation that may be simply missed.
“Whereas the assault works on all browsers, fullscreen BiTM assaults are significantly convincing on Safari browsers as a result of lack of clear visible cues when going fullscreen,” SquareX researchers say.
SquareX contacted Apple with its findings and acquired a “wontfix” reply, the reason acquired being that the animation is current to point adjustments, and that must be sufficient.
BleepingComputer has additionally reached out to Apple for a remark, however we’re nonetheless ready for his or her response.



