
A brand new variant of the Konfety Android malware emerged with a malformed ZIP construction together with different obfuscation strategies that permit it to evade evaluation and detection.
Konfety poses as a legit app, mimicking innocuous merchandise accessible on Google Play, however options not one of the promised performance.
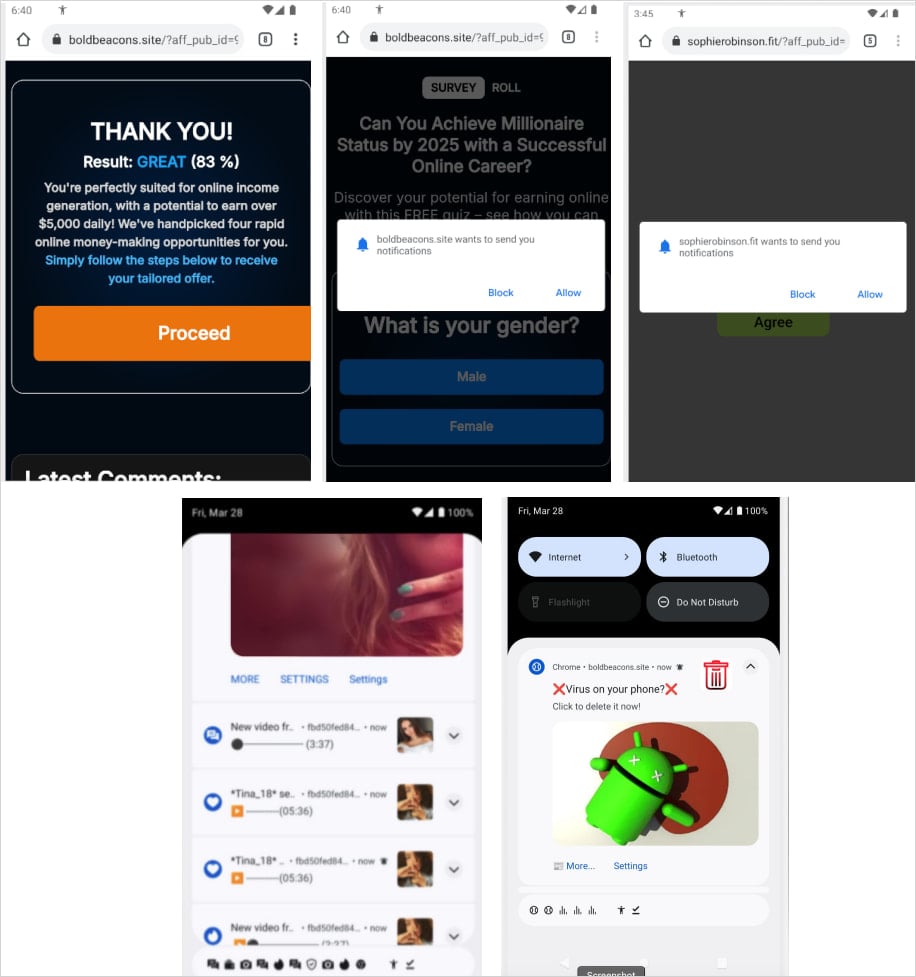
The capabilities of the malware embody redirecting customers to malicious websites, pushing undesirable app installs, and faux browser notifications.
As a substitute, it fetches and renders hidden adverts utilizing the CaramelAds SDK and exfiltrates data reminiscent of put in apps, community configuration, and system data.
Supply: Zimperium
Though Konfety is not a adware or RAT device, it contains an encrypted secondary DEX file contained in the APK, which is decrypted and loaded at runtime, containing hidden companies declared within the AndroidManifest file.
This leaves the door open for putting in extra modules dynamically, thus permitting the supply of extra harmful capabilities on present infections.
Evasion techniques
Researchers at cell safety platform Zimperium found and analyzed the newest Konfety variant and report that the malware makes use of a number of strategies to obfuscate its actual nature and exercise.
Konfety methods victims into putting in it by copying the title and branding of legit apps can be found on Google Play and distributing it by way of third-party shops – a tactic that researchers at Human referred to as “evil twin” or “decoy twin.”
The operators of the malware are selling it on third-party app shops.
These marketplaces are sometimes the place customers search for “free” variants of premium apps as a result of they need to keep away from Google monitoring, have an Android machine that’s now not supported, or do not have entry to Google companies.
The dynamic code loading, the place the malicious logic is hidden in an encrypted DEX file that hundreds at runtime, is one other efficient obfuscation and evasion mechanism that Konfety employs.
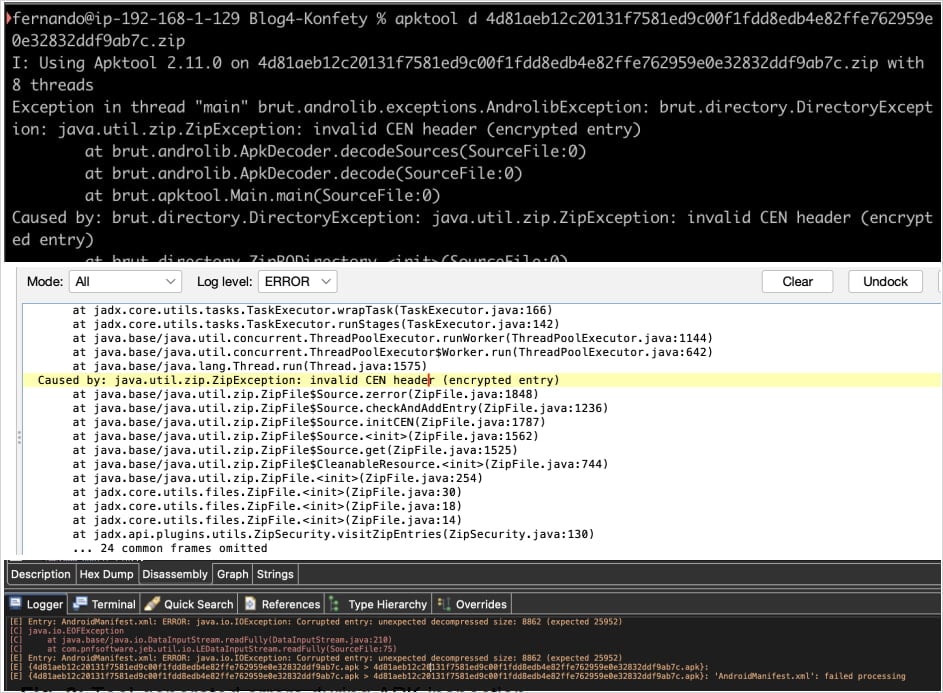
One other unusual anti-analysis technique in Konfety is to control the APK recordsdata in a manner that confuses or breaks static evaluation and reverse engineering instruments.
First, the APK units the Basic Objective Bit Flag to ‘bit 0,’ signaling that the file is encrypted, though it isn’t. This triggers false password prompts when attempting to examine the file, blocking or delaying entry to the APK’s contents.
Secondly, important recordsdata within the APK are declared utilizing BZIP compression (0x000C), which is not supported by evaluation instruments like APKTool and JADX, leading to a parsing failure.
Supply: Zimperium
In the meantime, Android ignores the declared technique and falls again to default processing to take care of stability, permitting the malicious app to put in and run on the machine with out challenge.
After set up, Konfety hides its app icon and title and makes use of geofencing to vary conduct in keeping with the sufferer’s area.
Compression-based obfuscation has been noticed previously in Android malware, as highlighted in a Kaspersky report from April 2024 on SoumniBot malware.
In that case, SoumniBot declared an invalid compression technique in AndroidManifest.xml, declared a pretend file dimension and knowledge overlay, and confused evaluation instruments with very giant namespace strings.
It’s usually advisable to keep away from putting in APK recordsdata from third-party Android app shops and solely belief software program from publishers you already know.



