At Cisco Dwell Melbourne 2025, the SOC noticed many fascinating behaviors from the varied purchasers of the convention community. One of many extra fascinating ones was observations pertains to the DNS visitors emitted by Home windows purchasers on the community, searching for their group’s Lively Listing Area Controllers. With our Endace full packet seize for the occasion, we had been in a position to seize DNS visitors from purchasers on the community and carry out evaluation utilizing Splunk Enterprise.
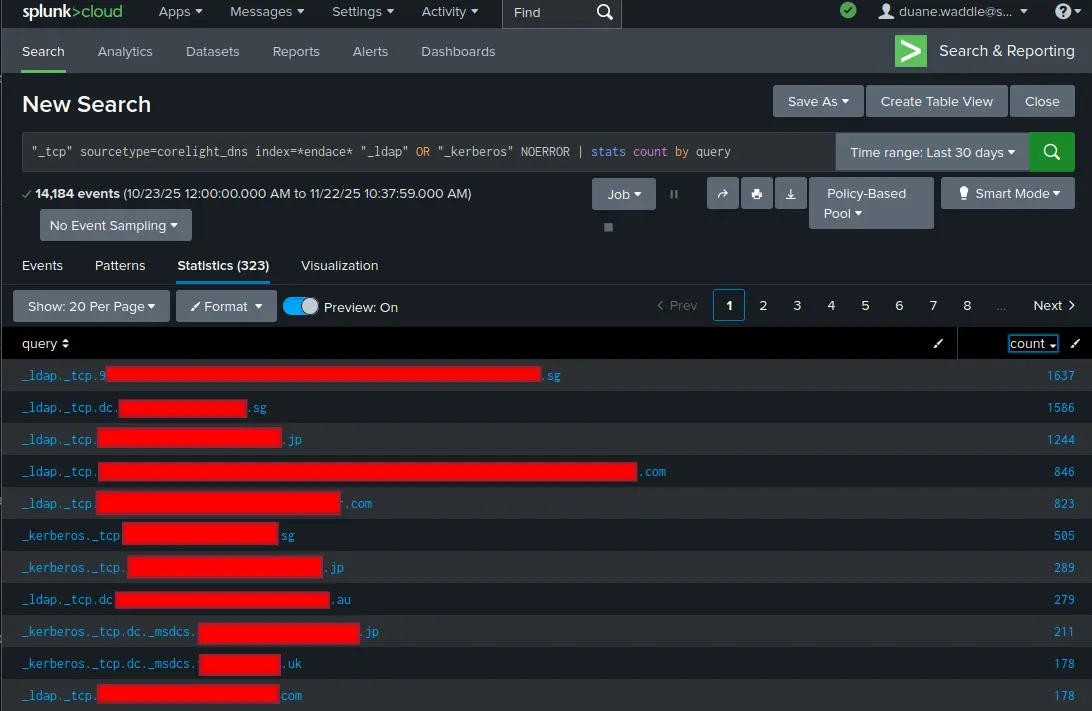
As a reminder, when a Home windows shopper is looking for to speak to a site controller it would make DNS queries for SRV information for names like _kerberos._tcp.dc._msdcs.DOMAINNAME or _ldap._tcp.dc._msdcs.DOMAINNAME. These DNS requests allow the shopper to seek out close by Kerberos or LDAP servers for his or her area.
Within the Cisco Dwell Melbourne 2025 SOC, we noticed purchasers ship out DNS queries for roughly 3,800 distinct names beginning with “_ldap” or “_kerberos”. Whereas most of them returned a failure of some kind (NXDOMAIN or SERVFAIL), roughly 300 had a profitable DNS response. A few of these had been profitable in subsequent makes an attempt to connect with the service (that means the area controllers are accessible in some vogue from the general public web), and some had been adopted up by cleartext LDAP BINDs, leaking credential data throughout the native community and Web. (SEE DANIEL’S BLOG POST)

There are a number of issues to contemplate from this.
First, there’s an open-source intelligence (OSINT) facet to this. The operators of any wi-fi community that you just connect with together with your laptop computer achieve telemetry about your group.
Second, a malicious wi-fi community may – relying on how your purchasers are configured – trick the shopper into sharing authentication data with it. Instruments resembling Responder are designed for this goal. Correctly configured trendy Home windows purchasers will use SMB signing, LDAP over TLS, LDAP channel binding, and different types of safety in opposition to a hostile community atmosphere. Are you positive your purchasers are configured in a method that makes them strong in opposition to a hostile community?
Third, in case your group has Lively Listing area controllers on the general public Web, are you taking the mandatory steps to guard them?
Lastly, the Cisco Dwell community is designed to be a secure community for attendees to make use of. However that’s no assure that – elsewhere – the identical SSID couldn’t be used to face up a hostile community. Shoppers will normally auto-connect after they see a wi-fi community they’ve related to earlier than.
One dependable mitigation for all of it is a VPN shopper. A correctly configured VPN shopper like Cisco Safe Consumer can assist each a full tunnel VPN and “Begin Earlier than Login”. With this function, the shopper laptop connects to the VPN as early as doable. All visitors, together with DNS lookups, are despatched over the VPN. Whereas this doesn’t get rid of all these dangers, it raises the security bar considerably.
Try the opposite blogs by my colleagues within the Cisco Dwell Melbourne 2026 SOC.
We’d love to listen to what you assume! Ask a query and keep related with Cisco Safety on social media.
Cisco Safety Social Media


