In as we speak’s panorama, organizations of all sizes are more and more adopting the default assumption that adversaries might already be persistent inside their networks. This pragmatic perspective underscores the important want and inherent worth of an lively segmentation program.
Segmentation introduces important management factors, regulating who and what can entry the community surroundings and its functions. It additionally facilitates the creation of artifacts important for reporting and compliance validation. Moreover, segmentation considerably restricts the “blast radius” of an incident, enormously aiding incident response by clarifying the “who, what, and the way” of an assault.
Many readers would possibly instantly consider Zero Belief, minimal privilege entry, and the great accounting of each gadget and session throughout their networks. Nonetheless, based mostly on years of working with and advising shoppers on segmentation, I’ve noticed that overly bold objectives typically result in implementation challenges and potential failure. The adage, “Don’t let perfection be the enemy of fine,” is especially related right here.
I persistently method the segmentation journey with my prospects by framing it as a round cycle. This cycle begins with visibility, progresses by way of identification context, coverage choice, and coverage enforcement, in the end returning to enhanced visibility. See determine 1.
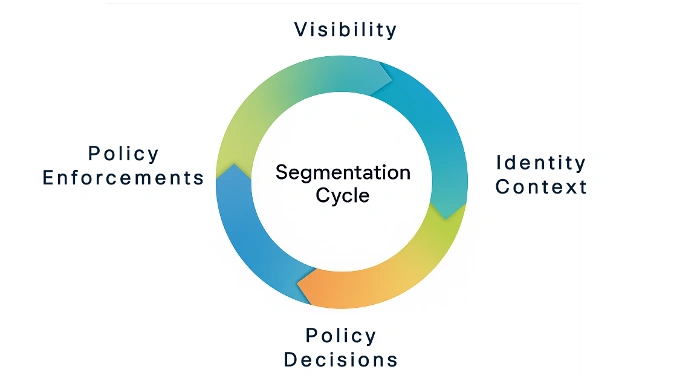

Visibility
The segmentation cycle each begins and ends with sturdy visibility. Gaining clear visibility into endpoints and community site visitors throughout the surroundings is essential for efficient discovery. A important preliminary step entails establishing a baseline by monitoring “regular” community conduct, using instruments like NetFlow information or monitor mode on Catalyst switches for passive endpoint profiling.
Every extra telemetry supply additional contributes to a extra complete understanding of the surroundings. The insights gained right here information coverage creation because the deployment and help workforce’s skills mature.
Identification Context
Identification might be represented in varied kinds, such because the VLAN a tool connects to, a wi-fi SSID, IP handle, MAC handle, or info obtained by way of lively or passive authentication.
Context, however, encompasses all different attributes that may positively or negatively have an effect on that identification. For example, if Mark is utilizing his issued laptop computer, however its native firewall is disabled, the gadget’s state can be deemed “unhealthy.” These mixed attributes collectively outline the Identification Context.
Coverage Task
Coverage Task, also known as the Coverage Resolution Level (PDP) in NIST SP 800-207, represents the “what” in our segmentation cycle. It dictates what an recognized consumer or endpoint is permitted to do.
This project might be dynamic, that means the chosen coverage is instantly influenced by the Identification’s Context. Returning to our instance, “unhealthy” Mark on his laptop computer will probably be assigned a unique coverage than “wholesome” Mark, with the latter doubtless receiving broader entry.
Coverage Enforcement
Coverage Enforcement is the place the principles are put into motion. As outlined in NIST SP 800-207, a Coverage Enforcement Level (PEP) is the place the assigned coverage for an recognized consumer or endpoint is utilized to allow or deny entry to a goal useful resource.
This stage represents the “how.” A goal useful resource might be various—a web site, an enterprise utility, a file server, or every other asset to which the group seeks to regulate entry.
Returning to Visibility
The cycle’s return to visibility is paramount, because it supplies actionable information confirming that insurance policies are being enforced, helps pinpoint poorly aligned insurance policies, and serves as a important level for detecting uncommon conduct and potential adversarial actions.
Why This Works
This framework provides a easy and repeatable method relevant to any entry situation. The insurance policies assigned might be instantly aligned with enterprise goals and mapped to actual operational use circumstances, offering a transparent construction to facilitate segmentation adoption.
Insurance policies can initially be coarse-grained, providing broad entry permissions, after which evolve into extra refined controls because the identification’s context develops.
Sensible Purposes
In upcoming weeks, I’ll discover sensible functions of this method throughout varied segments of a typical enterprise community, together with fast wins for reaching higher segmentation with out “boiling the ocean”:
- Distant consumer utility entry: Guarantee safe connections for distributed groups.
- Safe department (SD-WAN): Simplify segmentation throughout branches.
- Safe campus (wired/wi-fi): Enhance segmentation for native customers and units.
- Conventional information facilities: Improve safety of legacy infrastructure.
- Cloud-native environments (Kubernetes, OpenShift, hyperscalers): Apply segmentation in hybrid and multi-cloud environments.
Ultimate Ideas
One last, essential piece of recommendation: don’t embark on a segmentation journey with out securing government management help and an enough finances. Like every important enterprise, anticipate the sudden. Challenges will come up that demand decisive motion, and never each determination will garner common settlement.
Bear in mind: don’t let perfection be the enemy of progress.
We’d love to listen to what you assume! Ask a query and keep linked with Cisco Safety on social media.
Cisco Safety Social Media


