Cisco XDR served because the Tier-1 & 2 detection and response platform for the GovWare SOC, taking part in a pivotal function all through the operations. Built-in with Splunk, Endace, Safe Community Analytics (SNA), Safe Malware Analytics (SMA), Cisco Safe Firewall, Cisco Safe Entry (CSA), and third-party intelligence sources, it enabled real-time correlation and evaluation to shortly determine potential safety dangers and incidents. This integration considerably diminished each the Imply Time to Detect (MTTD) and the Imply Time to Reply (MTTR).
In the course of the GovWare SOC operation, Cisco XDR detected a complete of 39 incidents. Amongst them, 12 incidents had a direct affect on GovWare’s safety posture, whereas the remaining 27 had been categorized as low-risk occasions that posed no fast risk. Confirmed threats accounted for 30.7% of all detected incidents. The SOC crew carried out in-depth evaluation and response actions for every case, and the extra essential incidents had been promptly reported to the GovWare NOC.
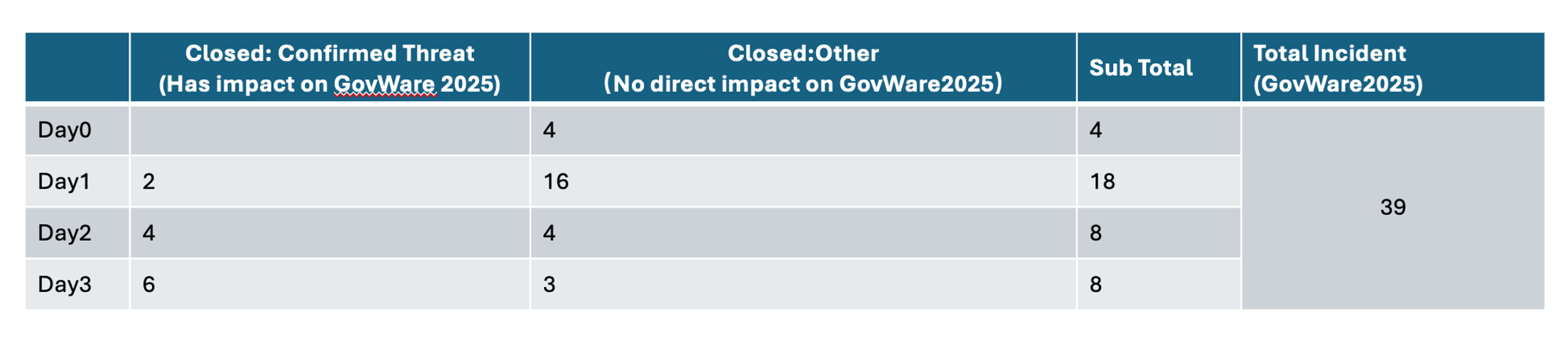

The next is an inventory of the 12 confirmed incidents that posed a direct risk to GovWare.
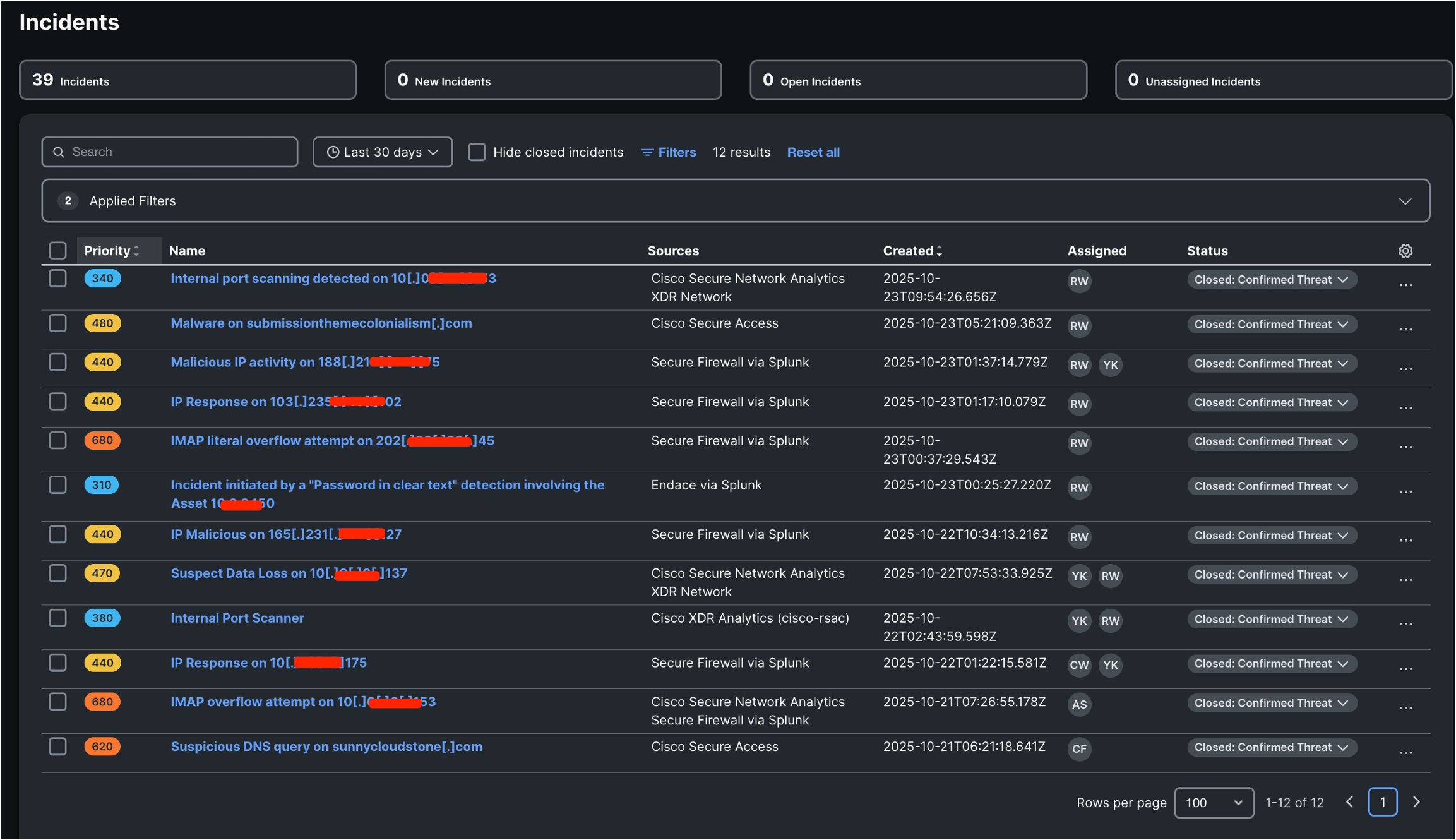

A better evaluation of those incidents reveals that their sources originated from the Community, SNA, Safe Firewall, Endace, Safe Entry, and different platforms, together with integration with Splunk. By XDR’s correlation and evaluation, these incidents had been recognized and will be categorized into the next assault varieties:
- Malicious port scanning
- Malicious area entry
- Malicious web IP deal with entry
- Passwords transmitted in clear textual content for essential functions and property
- Electronic mail vulnerability exploitation
- Suspected knowledge loss
The next offers an in-depth evaluation of two significantly consultant assault circumstances, serving as case research and classes discovered.
Case Examine 1: Risk Looking Unencrypted Essential File Transmission
Investigation Steps
- Integration and Community Context: Endace captures the SPAN visitors. It may extract information and generate Zeek logs. The Zeek logs are despatched to Splunk. The extracted information are despatched to Cisco Safe Malware Analytics (SMA) by way of Splunk Assault Analyzer, which is built-in with Cisco XDR.
- Incident Initiation: An automatic workflow in Cisco XDR repeatedly displays occasions from SMA. Each time a essential file is detected being transmitted over an unencrypted protocol, it mechanically generates an incident alert and sends it to the SOC analyst.
- Looking Key Indicators in Splunk: By operating an SPL search in Splunk, we are able to discover the logs that matches this file transmission. From the logs with the identical file UID, we recognized the true supply IP deal with for the incident.
- Deep Dive with Packet Seize: We searched and filtered visitors by supply and vacation spot IP addresses, and situated the unique session associated to this incident in Endace. We retrieved the unique information and examined the detailed session and packet content material with the Wireshark in Endace.
- Takeaway and Response: By the investigation in XDR, SMA, Splunk, and Endace, we recognized the supply IP, vacation spot IP, URL, file identify, and protocol. We confirmed this was a high-risk incident involving the unencrypted transmission of essential enterprise information. The incident has been reported to the GovWare Group. Attendees had been reminded to keep away from utilizing unencrypted protocols when transmitting essential enterprise information, to scale back the danger of information leakage.
Case Examine 2: Looking Malicious Scans Focusing on the Web Gateway
Investigation Steps
- Integration and Community Context: The SPAN visitors from the attendees is distributed to the Cisco Telemetry Dealer (CTB). CTB converts the visitors into NetFlow and sends it to Safe Community Analytics (SNA) and XDR Analytics. On the identical time, the firewall sends its connection and occasion logs to XDR. SNA analyzes the NetFlow knowledge and might generate port scan occasions. XDR Analytics analyzes each the NetFlow and log knowledge, and it may generate an Inner Port Scanner occasion.
- Incident Initiation: These occasions are correlated by the XDR engine to create an incident associated to a malicious scan. The information sources for this incident embrace SNA and XDR Community. Though the precedence is marked as low, after correlation, the incident is already extremely correct, so the potential affect needs to be thought-about excessive.
- Examine in Safe Community Analytics (SNA): Within the SNA Host Posture interface, we may see the asset group that the host belonged to, the interior teams and Web places it accessed, and a safety occasion clearly indicating a port scan from this host.
- Examine in XDR Analytics: We noticed that it additionally triggered an Inner Port Scanner alert in XDR Analytics. The three IP addresses performing the malicious scans had been correlated and grouped collectively. Their targets had been the identical Web Gateway addressed on the Cisco Safe Firewall. It was noticed that the identical supply IP despatched a lot of connection makes an attempt to a number of ports on the Web Gateway. Despite the fact that no response packets had been obtained, the IP stored attempting new ones, clearly displaying malicious scanning conduct.
- Takeaway and Response: The Web gateway is the Cisco Safe Firewall that efficiently blocked the malicious scan makes an attempt. Nonetheless, such scans can affect the community, so we reported the incident to the GovWare NOC Group for continued monitoring.
Past the 2 detailed investigations above, XDR additionally detected different incidents equivalent to passwords transmitted in clear textual content, malicious area entry, and malicious Web IP deal with entry. These Incidents have been escalated to Tier3 crew, they will conduct the investigations and experiences.
Closing Ideas
As an automatic and clever safety detection and response platform, Cisco XDR performed a essential function within the GovWare SOC operations. It enabled SOC analysts to detect and examine actual incidents in actual time.
Whereas investigating incidents inside XDR, analysts may evaluate the assault chain, add notes to the worklog, replace the incident standing, and escalate to Splunk, Endace, Firewall, Safe Entry groups and Talos groups when additional motion was required.
All through the SOC operation, XDR’s automation, correlation, workflow, and intelligence considerably improved the SOC’s detection, investigation, and response capabilities, and successfully safeguarded the GovWare convention.
Take a look at the different blogs by my colleagues within the GovWare SOC.
About GovWare
GovWare Convention and Exhibition is the area’s premier cyber info and connectivity platform, providing multi-channel touchpoints to drive group intel sharing, coaching, and strategic collaborations.
A trusted nexus for over three many years, GovWare unites policymakers, tech innovators, and end-users throughout Asia and past, driving pertinent dialogues on the newest developments and significant info circulate. It empowers progress and innovation by means of collective insights and partnerships.
Its success lies within the belief and assist from the cybersecurity and broader cyber group that it has had the privilege to serve through the years, in addition to organisational companions who share the identical values and mission to counterpoint the cyber ecosystem.
We’d love to listen to what you suppose! Ask a query and keep related with Cisco Safety on social media.
Cisco Safety Social Media


