Securing a reside convention could be like menace searching on laborious mode. You’re coping with various gadgets, short-term networks, visitor credentials, and 1000’s of customers, all whereas threats must be recognized and addressed in real-time. Efficient menace searching on this atmosphere requires extra than simply detecting anomalies; it calls for the power to rapidly pivot from high-level alerts to granular packet-level forensics. Throughout my latest work defending GovWare 2025, I found that integrating Splunk Enterprise and Splunk Assault Analyzer (SAA) with Endace created a robust menace searching workflow that bridged the hole between safety analytics and community forensics. This mix reworked our means to not solely determine suspicious exercise however to quickly examine and validate threats with definitive proof. On this put up, I’ll share how this integration labored in observe and the important thing classes I realized about menace searching at scale.
We leveraged Splunk Assault Analyzer’s strong API to connect with Endace, a sophisticated community recording software that gives packet-level visibility into community exercise. Endace (by way of Zeek) mechanically submitted suspicious recordsdata and URLs (aka “sources”) detected in community visitors to SAA. Most of the recordsdata submitted have been benign, so it was eye-catching when SAA flagged a file with a rating of 100. The file in query was a zipper file that contained a malicious executable file .exe. We have been notably concerned with operating this file via Cisco’s SMA’s (Safe Malware Analytics) sandbox which we built-in with SAA. The truth is, 22 out of the 28 detections for this file got here from this sandbox, previously generally known as Menace Grid. These detections play an important position within the evaluation, as there may be some detection logic utilized.
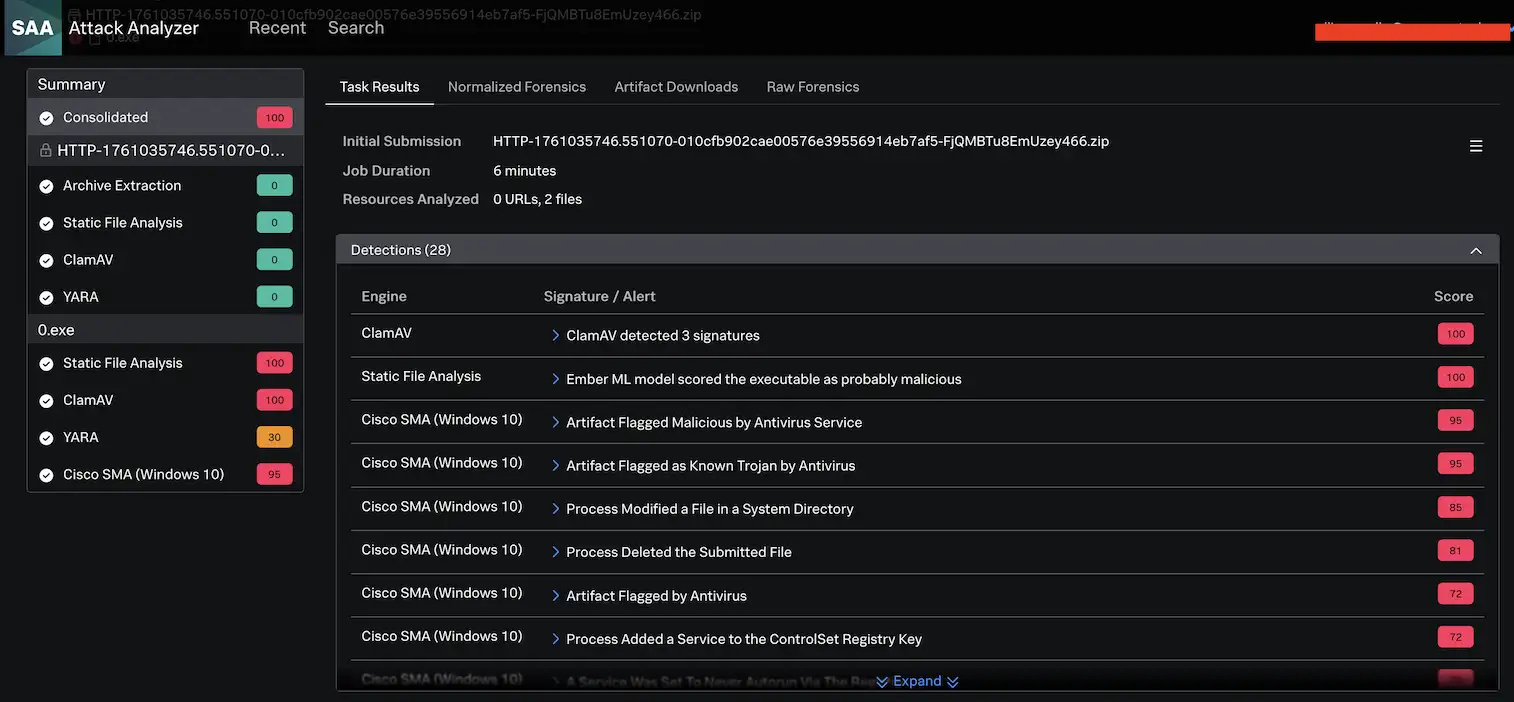

When wanting on the “Normalized Forensics” tab for this process, of explicit curiosity is the “Strings & Configs” tab which comprises macro code that was extracted or emulated. For this doc we may see that SAA extracted a string for the web site “sogou[.]com”, a legit Chinese language search engine and know-how firm. Nevertheless, one other string that was extracted included “Gh0st Replace”, which has been noticed within the notorious Gh0st RAT malware.
Gh0st RAT is infamous for establishing persistence to make sure it runs after a system reboot. This usually includes modifying registry keys or creating companies. SAA’s evaluation revealed textbook Gh0st RAT ways:
- Persistence via registry and repair manipulation
- Evasion by way of Armadillo packing and file obfuscation
- Suspicious reminiscence operations suggesting code injection
- Clear C2 communication makes an attempt
The 22 detections from our Cisco sandbox painted an unmistakable image of superior malware conduct.
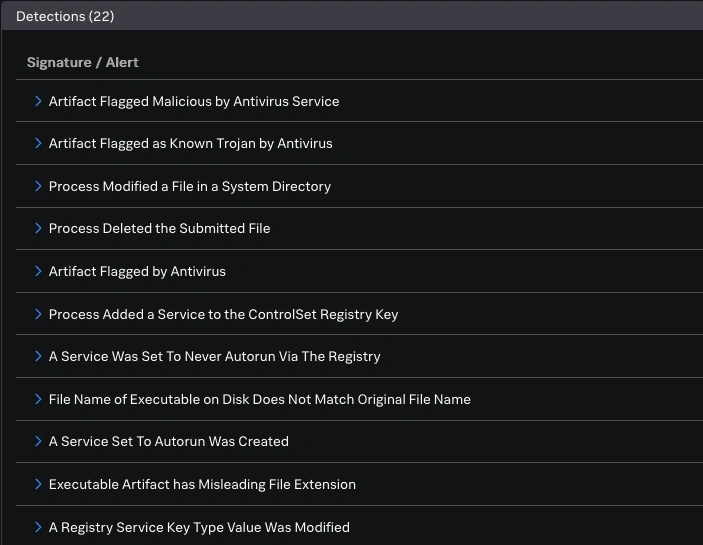

Whereas the SAA forensics outcomes clearly indicated C2 makes an attempt, the community exercise logs inside SAA initially confirmed solely inner DNS and DHCP visitors. This was a vital level of investigation: if the RAT was making an attempt to “telephone dwelling,” the place was the exterior communication? This led us to pivot from the sandbox’s inner view to our broader community logs in Splunk Enterprise.
With little visibility into endpoints, our DNS and DHCP logs grew to become our main supply of fact. We knew the Gh0st RAT variant doubtless employed a Area Era Algorithm (DGA) to search out its C2 server, that means it will try to resolve randomly generated domains, usually leading to NXDOMAIN (Non-Existent Area) responses.

We meticulously sifted via all NXDOMAIN responses from the convention visitor community throughout the related timeframe. Many have been typical noise: reverse DNS lookups, service discovery makes an attempt from attendees’ company gadgets, or legit companies that merely weren’t resolvable on our visitor community. Admittedly, that is the place our hunt got here to an finish as we decided that one among our engineers had submitted this file as a check. Nevertheless, it was a enjoyable rabbit gap to wander down, and it gave us some concepts concerning the capabilities of our instruments, in addition to indicators to be looking out for.
From Heat-As much as Actual Menace: Uncovering Lively C2 Communication
After the warm-up train with the check file, we shifted our focus again to the continual stream of submissions from Endace to SAA. This time, a URL submission caught our consideration with a rating of 75, primarily flagged for “Social Engineering” indicators. Whereas not as dramatic as our earlier rating of 100, a mix of things made this price investigating: notably the area’s latest creation date, which added one other 15 factors to its danger rating. Lately created domains are sometimes a trademark of attackers organising new infrastructure for campaigns.
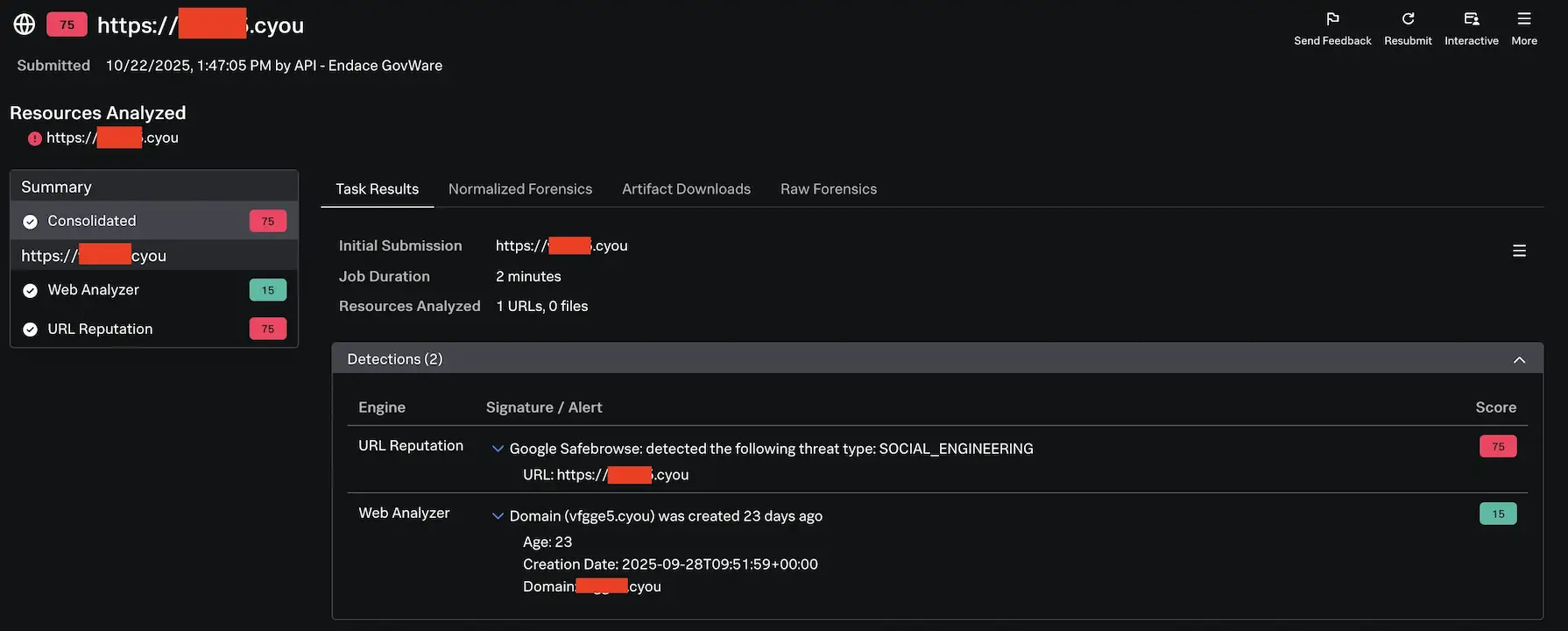

To broaden our investigation past SAA’s preliminary evaluation, I pivoted to VirusTotal for added context on the area. This cross-referencing revealed two IP addresses related to the suspicious area, with one notably standing out: 103.235.46[.]102. This IP instantly raised pink flags in our menace intelligence sources.
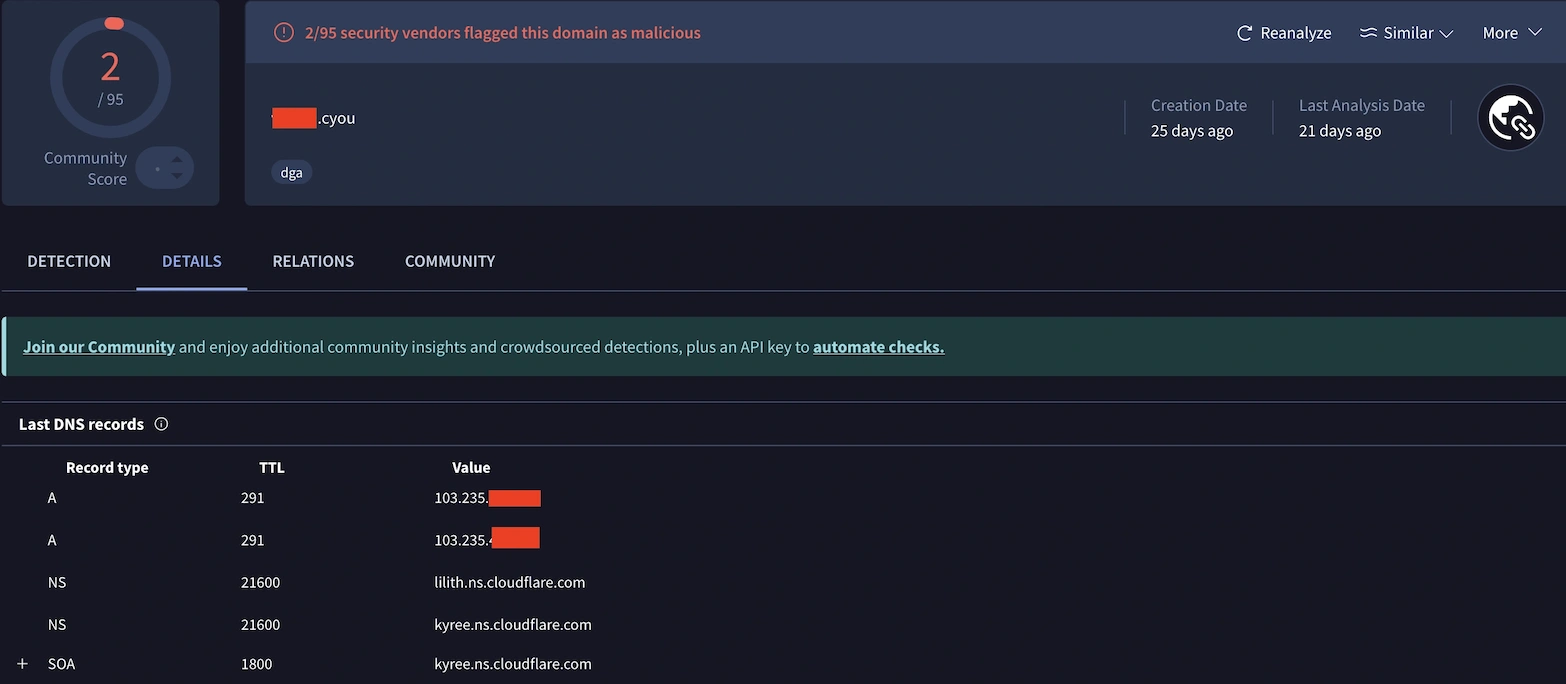

Connecting the Dots: From Suspicious Area to Recognized Menace Actor Infrastructure
The IP deal with 103.235.46[.]102 wasn’t simply one other suspicious indicator. Our Talos Menace Hunter working alongside us identified that it had a documented historical past as command-and-control infrastructure. Based on Google Cloud’s menace intelligence reporting, this IP was beforehand related to a ViewState deserialization zero-day vulnerability marketing campaign, the place it served as an attacker-controlled node for C2 operations. This context reworked our investigation from a routine suspicious area verify into a possible lively menace state of affairs.
Leveraging Endace’s packet-level visibility, we have been capable of definitively reply the important query: was anybody on our convention community truly speaking with this known-bad infrastructure? The reply was regarding, as I discovered three distinct hosts on the visitor community that confirmed lively communication patterns with 103.235.46[.]102. Endace’s forensic capabilities allowed us to not solely affirm the connections but in addition study the character and timing of the visitors, offering essential proof for our incident response.
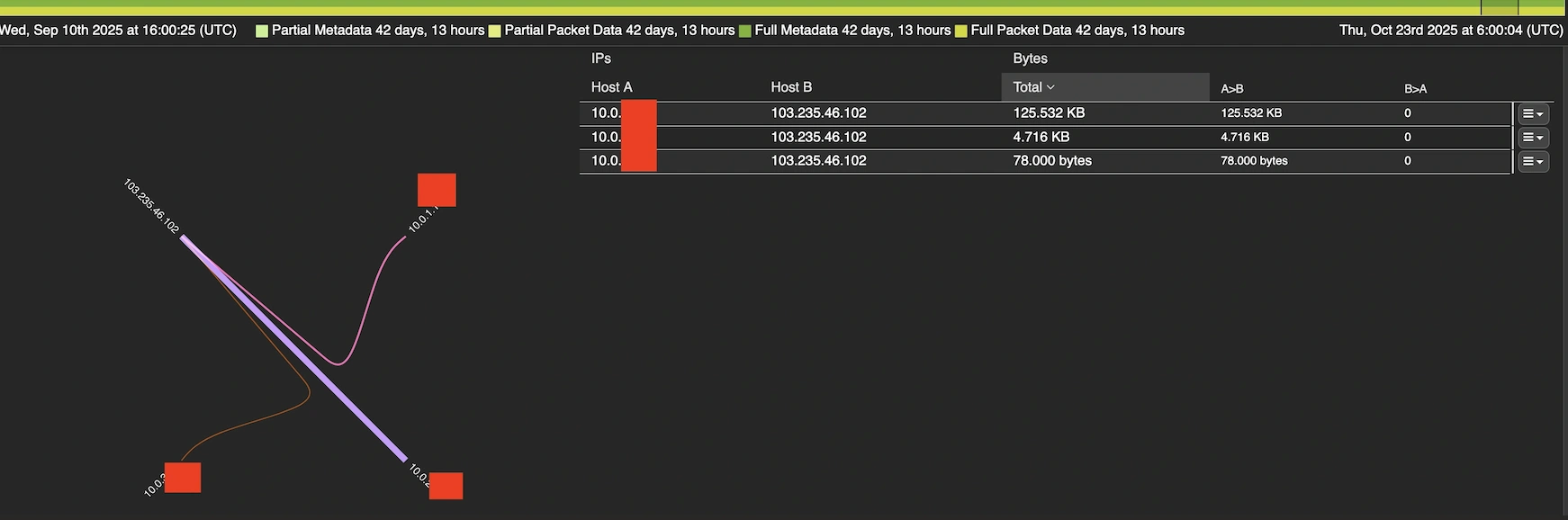

Speedy Response: From Detection to Mitigation
With concrete proof of convention gadgets speaking with identified C2 infrastructure, we instantly escalated from investigation to containment. The mixture of SAA’s behavioral evaluation, exterior menace intelligence validation, and Endace’s definitive packet proof gave us the boldness to take decisive motion. We wrote up an Incident Report for the SOC managers, who approved an instantaneous block on IP deal with 103.235.46[.]102 throughout our convention community infrastructure.
This incident completely illustrated the ability of our built-in menace searching stack. SAA’s automated evaluation caught the preliminary suspicious URL, exterior menace intelligence supplied essential context concerning the infrastructure’s malicious historical past, and Endace delivered the packet-level proof we would have liked to verify lively threats and justify our response. Within the high-stakes atmosphere of convention safety, the place false positives can disrupt legit actions and false negatives can compromise attendee knowledge, this multi-layered validation course of has proved invaluable.
Try the different blogs by my colleagues within the GovWare SOC.
About GovWare
GovWare Convention and Exhibition is the area’s premier cyber info and connectivity platform, providing multi-channel touchpoints to drive neighborhood intel sharing, coaching, and strategic collaborations.
A trusted nexus for over three many years, GovWare unites policymakers, tech innovators, and end-users throughout Asia and past, driving pertinent dialogues on the most recent developments and significant info movement. It empowers progress and innovation via collective insights and partnerships.
Its success lies within the belief and assist from the cybersecurity and broader cyber neighborhood that it has had the privilege to serve through the years, in addition to organisational companions who share the identical values and mission to counterpoint the cyber ecosystem.
We’d love to listen to what you suppose! Ask a query and keep related with Cisco Safety on social media.
Cisco Safety Social Media


