
A brand new malware-as-a-service (MaaS) platform named ‘SuperCard X’ has emerged, concentrating on Android gadgets by way of NFC relay assaults that allow point-of-sale and ATM transactions utilizing compromised fee card information.
SuperCard X is linked to Chinese language-speaking risk actors and exhibits code similarities with the open-source mission NFCGate and its malicious spawn, NGate, which has facilitated assaults in Europe since final yr.
The malware-as-a-service platform is promoted by means of Telegram channels that additionally supply direct help to “clients.”
SuperCard X was found by cellular safety agency Cleafy, which stories seeing assaults using this Android malware in Italy. These assaults concerned a number of samples with refined variations, indicating that associates are supplied the choice of customized builds tailor-made to regional or different particular wants.
How SuperCard X assaults unfold
The assault begins with the sufferer receiving a faux SMS or WhatsApp message impersonating their financial institution, claiming they should name a quantity to resolve points brought on by a suspicious transaction.
The decision is answered by a scammer posing as financial institution help, who makes use of social engineering to trick the sufferer into “confirming” their card quantity and PIN. They then try to persuade the person to take away spending limits by way of their banking app.
Lastly, the risk actors persuade customers to put in a malicious app (Reader) disguised as a safety or verification device that accommodates the SuperCard X malware.
Upon set up, the Reader app requests solely minimal permissions, primarily entry to the NFC module, which is sufficient to carry out the info theft.
The scammer instructs the sufferer to faucet their fee card to their cellphone to confirm their playing cards, permitting the malware to learn the cardboard chip information and ship it to the attackers.
The attackers obtain this information on their Android gadget, which runs one other app referred to as Tapper, which emulates the sufferer’s card utilizing the stolen information.
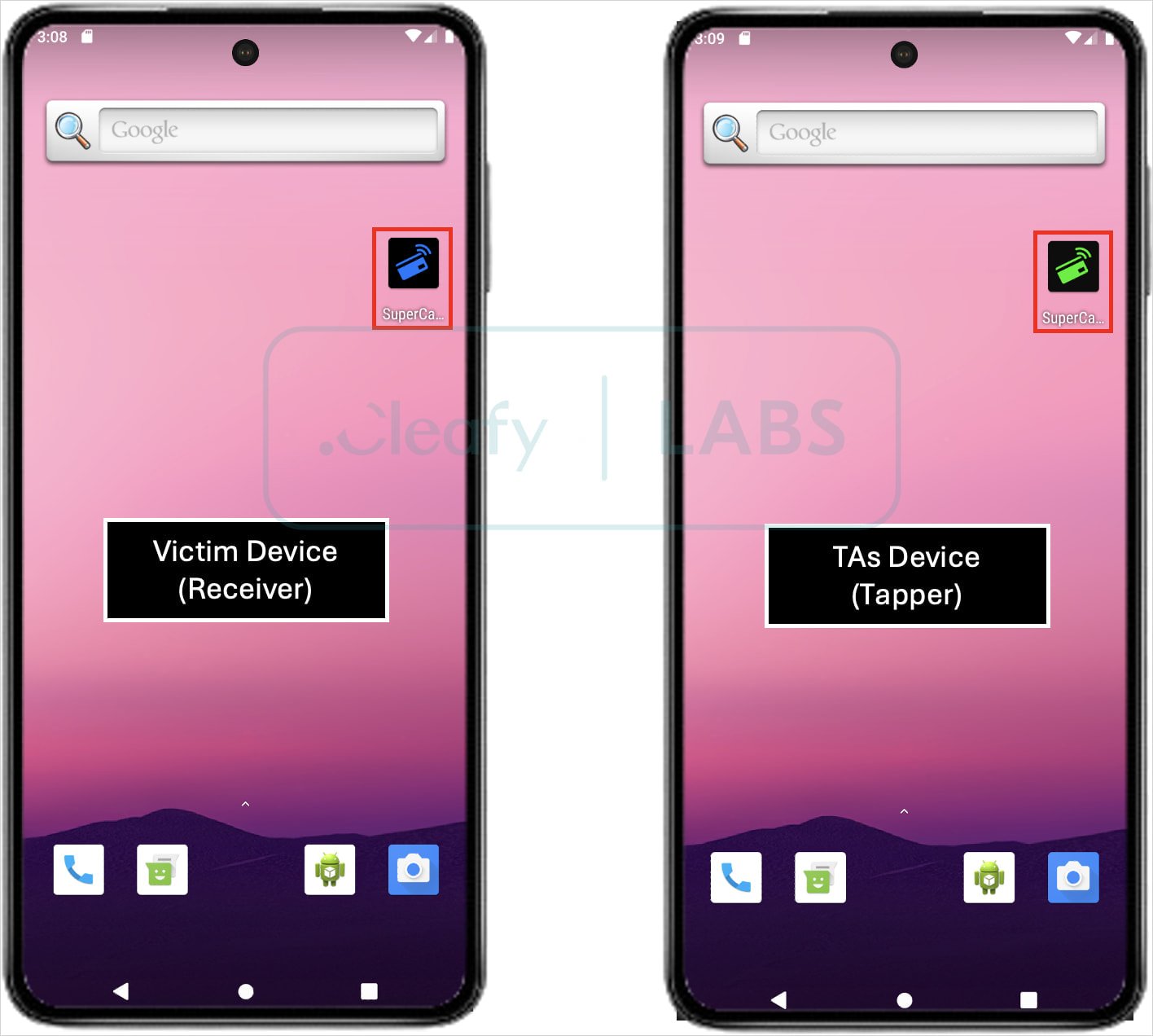
Supply: Cleafy
These ’emulated’ playing cards enable attackers to make contactless funds at shops and ATM withdrawals, although quantity limits apply. As these small transactions are immediate and seem authentic to the banks, they’re tougher to flag and reverse.
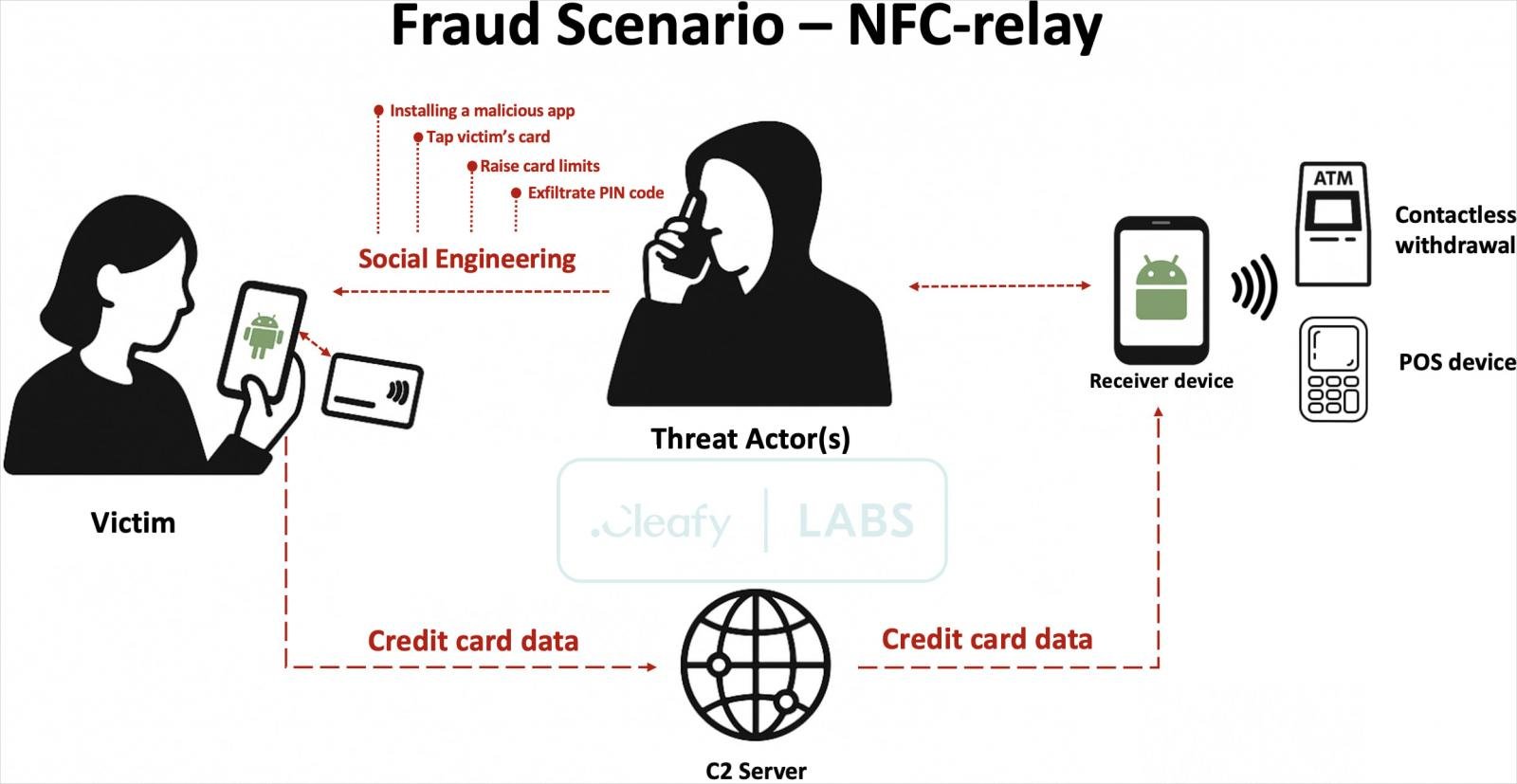
Supply: Cleafy
Evasive malware
Cleafy notes that SuperCard X is at present not flagged by any antivirus engines on VirusTotal and the absence of dangerous permission requests and aggressive assault options like display overlaying ensures it stays off the radar of heuristic scans.
The emulation of the cardboard is ATR-based (Reply to Reset), which makes the cardboard seem authentic to fee terminals and exhibits technical maturity and understanding of smartcard protocols.
One other notable technical facet is the usage of mutual TLS (mTLS) for certificate-based shopper/server authentication, securing C2 communications from interception and evaluation by researchers or legislation enforcement.
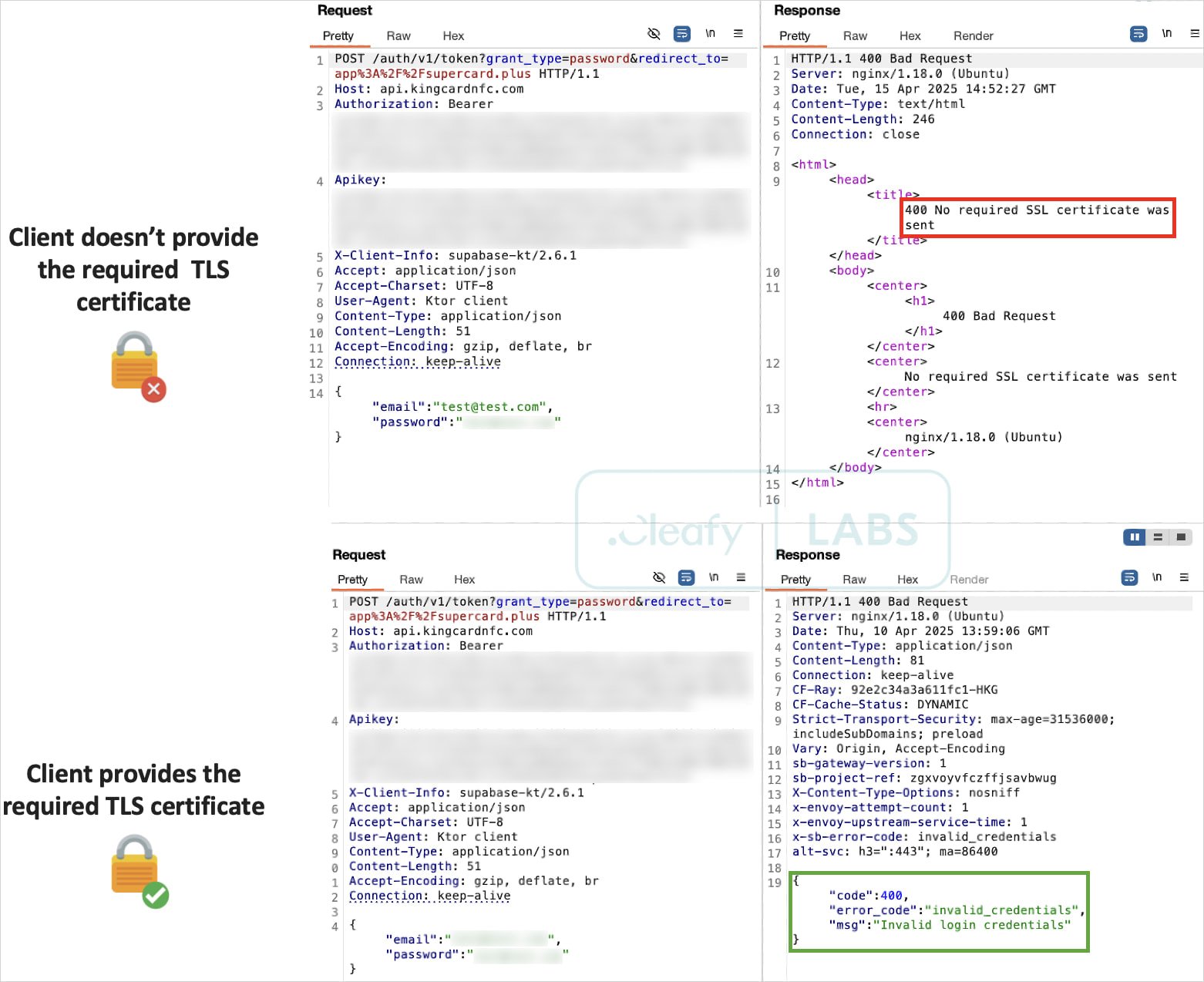
Supply: Cleafy
BleepingComputer contacted Google to touch upon the SuperCard X exercise and a spokesperson despatched the beneath assertion.
“Primarily based on our present detection, no apps containing this malware are discovered on Google Play. Android customers are routinely protected by Google Play Defend, which is on by default on Android gadgets with Google Play Companies. Google Play Defend can warn customers or block apps recognized to exhibit malicious habits, even when these apps come from sources outdoors of Play.” – A Google spokesperson


