
A gamer in search of monetary help for most cancers remedy misplaced $32,000 after downloading from Steam a verified recreation named Block Blasters that drained his cryptocurrency pockets.
Block Blasters is a 2D platformer that was accessible on Steam for nearly two months, between July 30 and September 21. The sport was secure till August 30, when a cryptodrainer element was added.
Printed by developer Genesis Interactive and now not on Steam, the retro-styled recreation was a free-to-play title promising fast-paced motion on responsive controls, and had just a few hundred ‘Very Constructive’ critiques on the gaming platform.
The malicious element within the recreation was revealed throughout a dwell fundraising from online game streamer RastalandTV, who was making an attempt to lift funds for all times saving remedy towards stage 4 high-grade sarcoma.
The gamer additionally began a GoFundMe crowdsourcing marketing campaign to obtain donations. On the time of writing, completion of the purpose is at 58%. Nevertheless, some members of the crypto neighborhood supplied to cowl the loss. Crypto influencer Alex Becker stated that he despatched Rastaland $32,500 to a secure pockets.
Because the Latvian gamer explains, he misplaced greater than $32,000 after downloading a verified recreation on Steam.
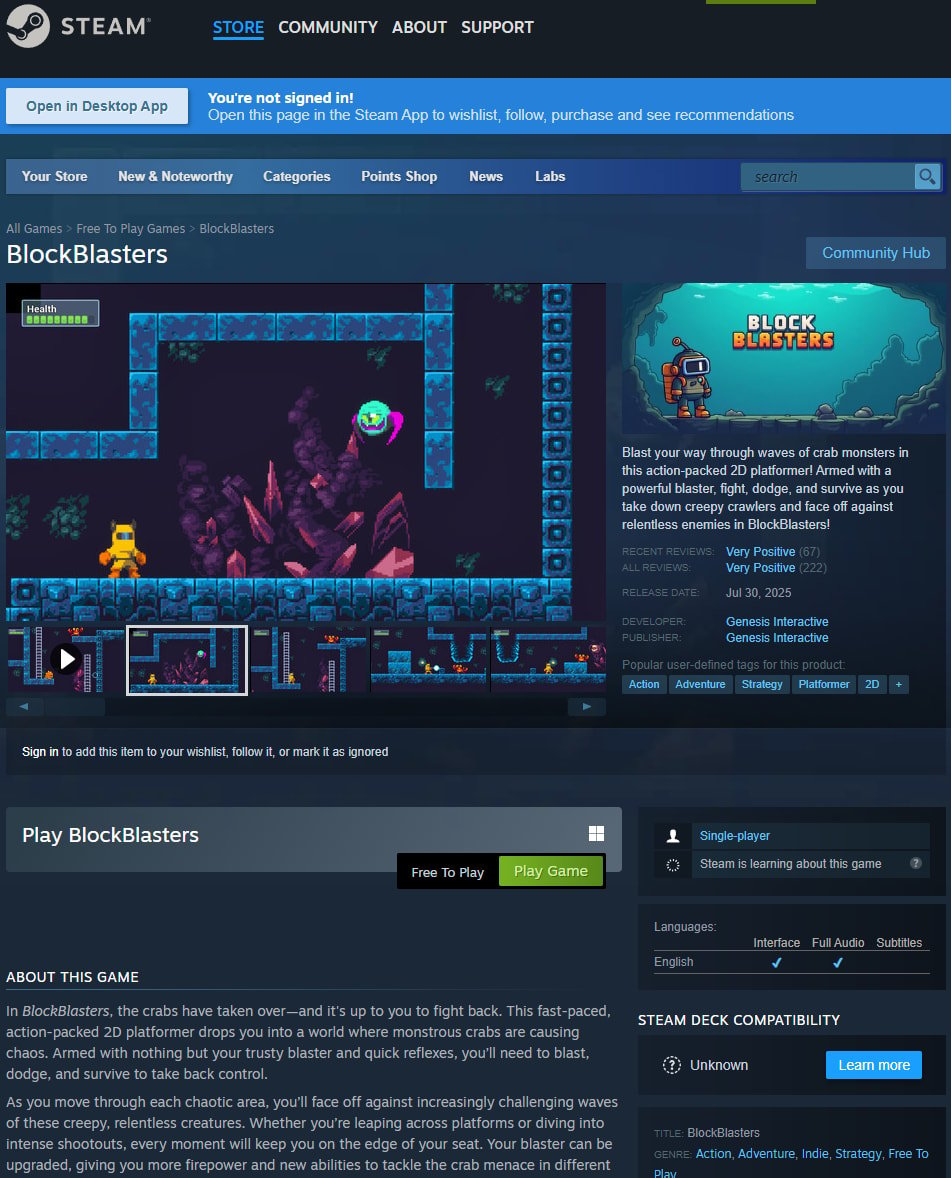
Supply: Web Archive
Crypto investigator ZachXBT instructed BleepingComputer that the attackers seem to have stolen a complete of $150,000 from 261 Steam accounts.
VXUnderground safety group, who has additionally been following the assault, studies the next sufferer depend of 478, and revealed an inventory of usernames, urging their house owners to right away reset their passwords.
Reportedly, these individuals had been explicitly focused after being recognized over Twitter for managing important cryptocurrency quantities, and had been presumably despatched invites to check out the sport.
A group of researchers revealed a short report detailing the dropper batch script that performs surroundings checks earlier than it collects Steam login info together with the sufferer’s IP handle, and uploads the information to a command and management (C2) system.
GDATA researcher Karsten Hahn additionally documented a Python backdoor, and a StealC payload, used alongside the batch stealer.
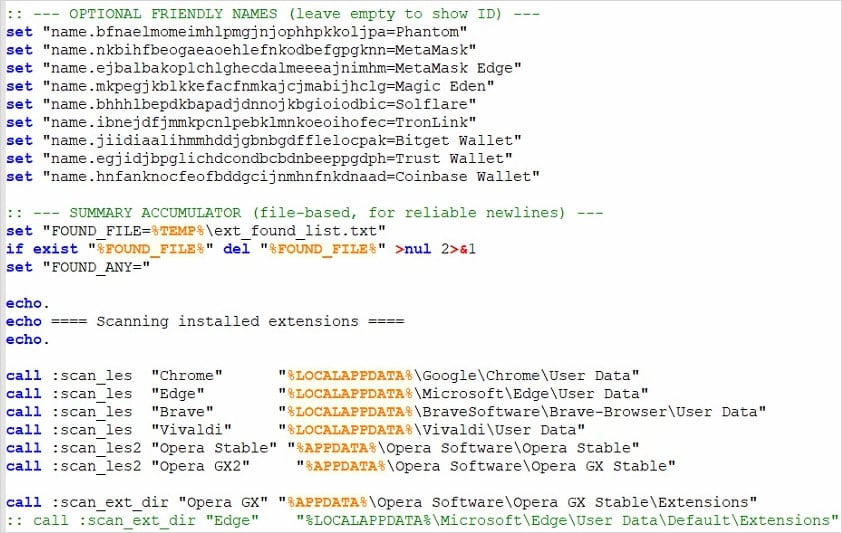
Supply: @struppigel | X
Investigators additionally highlighted an operational safety failure the place the attackers left their Telegram bot code and tokens uncovered.
There are unconfirmed studies that OSINT specialists collaborating within the hunt recognized the risk actor as an Argentinian immigrant dwelling in Miami, Florida.
BleepingComputer has contacted Valve for a touch upon Block Blasters and the alleged inaction following a number of studies, however now we have not obtained a response by publication time.
The Block Blasters incident isn’t an remoted one on Steam. Comparable instances earlier this 12 months embody the Chemia survival crafting recreation, Sniper: Phantom’s Decision, and PirateFi, all of which contaminated unsuspecting victims with information-stealing malware.
When you’ve got put in Block Blasters in your laptop, it is suggested to reset your Steam passwords instantly and transfer your digital belongings to new wallets.
Usually, it’s advisable to be cautious with Steam video games which have a small variety of downloads and critiques, and in addition titles in ‘beta’ improvement stage, as these can cover malware payloads.



