The operators of the SystemBC proxy botnet are looking for susceptible business digital non-public servers (VPS) and preserve a mean of 1,500 bots day by day that present a freeway for malicious visitors.
Compromised servers are positioned everywhere in the world and have not less than one unpatched crucial vulnerability, a few of them being tormented by tens of safety points.
SystemBC has been round since not less than 2019 and has been utilized by varied menace actors, together with a number of ransomware gangs, to ship payloads.
It lets attackers route malicious visitors via the contaminated host and conceal command-and-control (C2) exercise to make detection harder.
SystemBC’s prospects
In keeping with researchers at Lumen Know-how’s Black Lotus Labs, the SystemBC proxy community is constructed for quantity with little concern for stealth. It additionally powers different felony proxy networks and has “extraordinarily lengthy common an infection lifetimes.”
Primarily based on the researchers’ findings, neither prospects nor operators of SystemBC care about conserving a low profile, because the bots’ IP addresses should not protected in any manner (e.g. via obfuscation or rotation).
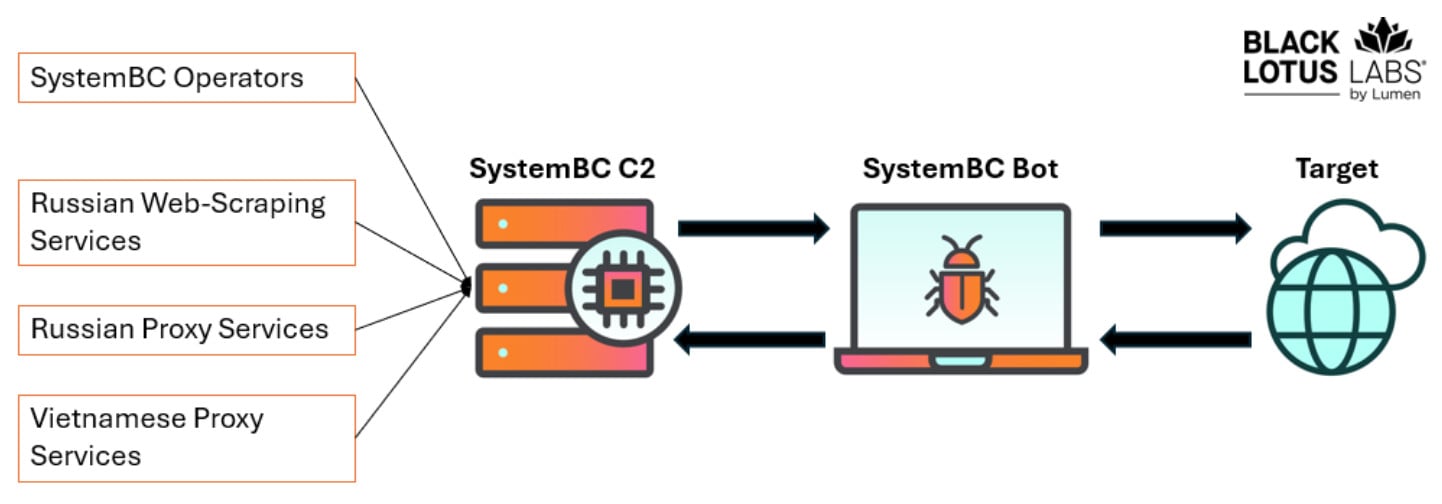
SystemBC has greater than 80 command-and-control (C2) servers, which join shoppers to an contaminated proxy server, and it fuels different proxy community providers.
One malicious service referred to as REM Proxy depends on round 80% of SystemBC’s bots, offering tiered providers to its prospects, relying on the required proxy high quality.
A big Russian web-scraping service is one other important SystemBC buyer, together with a Vietnamese-based proxy community referred to as VN5Socks or Shopsocks5.
supply: Black Lotus Labs
Nonetheless, the researchers say that SystemBC operators take advantage of use of it to brute-force WordPress credentials which can be seemingly offered to brokers who inject websites with malicious code.
Focusing on susceptible VPSs
Virtually 80% of the SystemBC community of 1,500 each day bots consists of compromised VPS techniques from a number of “massive business suppliers.”
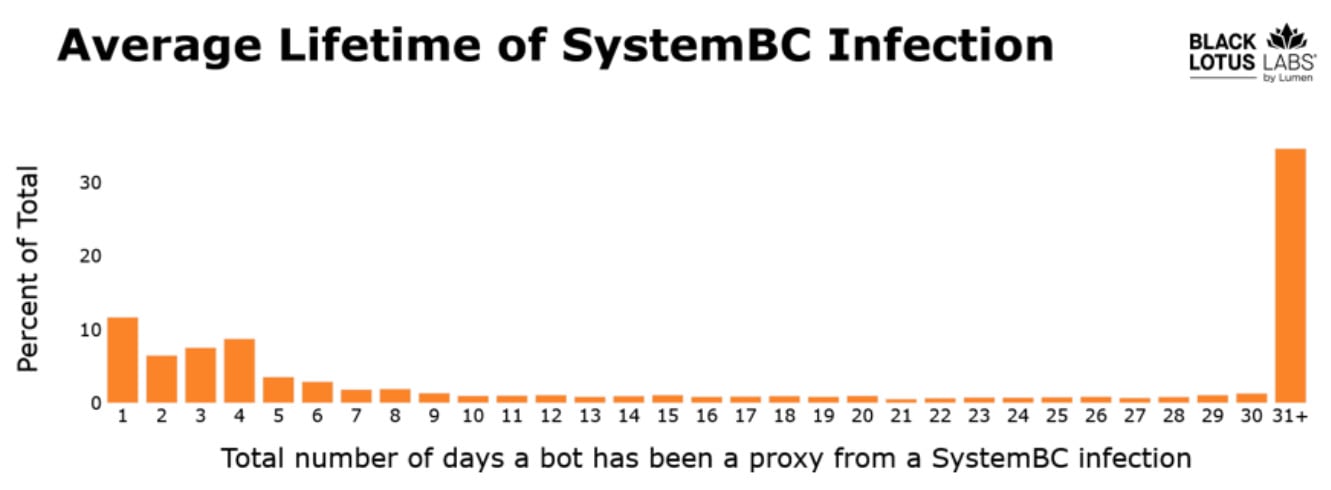
Black Lotus Labs says that this enables for a longer-than-average an infection lifespan, with almost 40% of the techniques staying compromised for greater than a month.
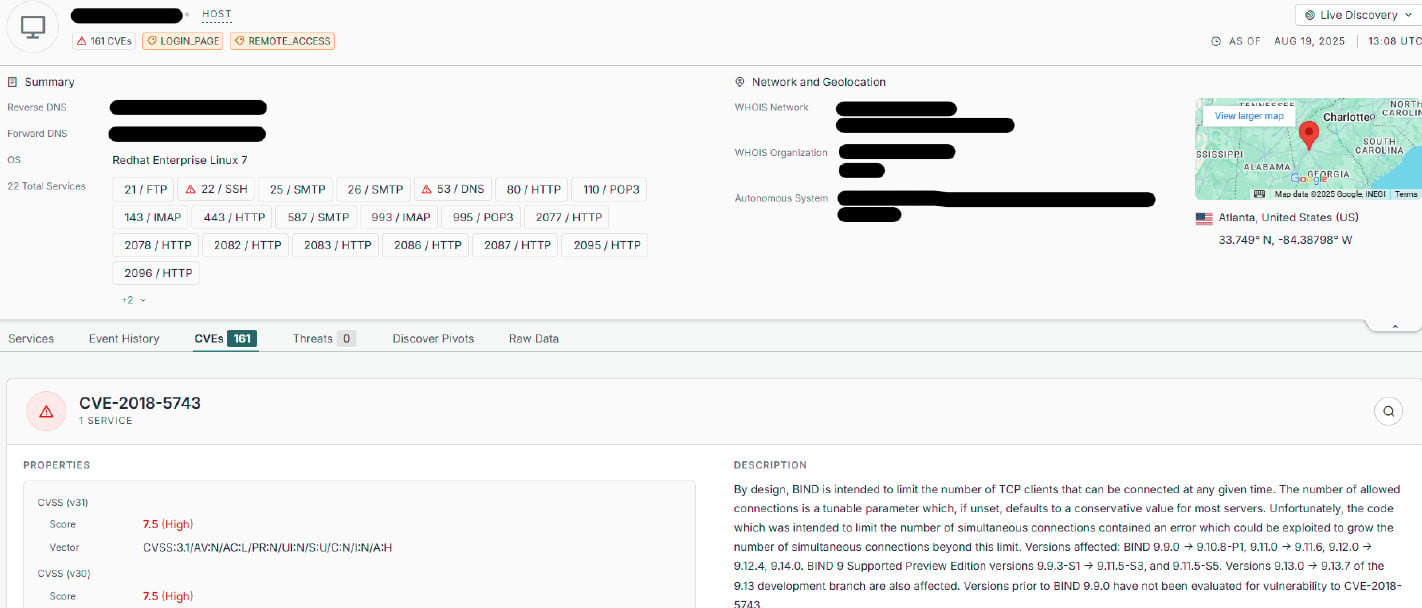
All of the contaminated servers have a number of “easy-to-exploit” vulnerabilities, the common being 20 unpatched safety points, and not less than one critical-severity one.
The researchers additionally discovered one system in Alabama, which the Censys web intelligence platform and search engine listed as having 161 safety vulnerabilities.
supply: Black Lotus Labs
By compromising VPS techniques, SystemBC allows high-volume, secure visitors for its prospects, which isn’t potential with residential proxy networks based mostly on SOHO gadgets.
By operating the SystemBC malware in a simulated surroundings, the researchers noticed “a selected IP tackle generate an extra of 16 gigabytes of proxy knowledge” in simply 24 hours.
“This quantity of knowledge is an order of magnitude higher than what is usually noticed in typical proxy networks,” mentioned Black Lotus Labs researchers in a report shared with BleepingComputer.
Primarily based on the corporate’s international IP telemetry, one tackle, 104.250.164[.]214, seems to be on the core of sufferer recruiting exercise and in addition hosts all 180 SystemBC malware samples.
In keeping with the researchers’ evaluation, a newly contaminated server downloads a shell script, which has feedback in Russian and directs the bot to run each SystemBC pattern on the identical time.
The proxy community has been energetic for a very long time and has resisted even regulation enforcement operations, resembling Endgame, which focused the malware droppers for a number of botnets, together with SystemBC.
Black Lotus Labs supplies an in depth technical evaluation of the SystemBC proxy malware, together with indicators of compromise, to assist organizations determine compromise makes an attempt or disrupt the operation.



