Managing and sustaining deployments of complicated software program current engineers with a large number of challenges: safety vulnerabilities, outdated dependencies, and unpredictable and asynchronous vendor launch cadences, to call a number of.
We describe right here an strategy to automating key actions within the software program operations course of, with concentrate on the setup and testing of updates to third-party code. A key profit is that engineers can extra shortly and confidently deploy the newest variations of software program. This enables a staff to extra simply and safely keep updated on software program releases, each to help shopper wants and to remain present on safety patches.
We illustrate this strategy with a software program engineering course of platform managed by our staff of researchers within the Utilized Techniques Group of the SEI’s CERT Division. This platform is designed to be compliant with the necessities of the Cybersecurity Maturity Mannequin Certification (CMMC) and NIST SP 800-171. Every of the challenges above current dangers to the steadiness and safety compliance of the platform, and addressing these points calls for effort and time.
When system deployment is finished with out automation, system directors should spend time manually downloading, verifying, putting in, and configuring every new launch of any specific software program device. Moreover, this course of should first be achieved in a take a look at surroundings to make sure the software program and all its dependencies could be built-in efficiently and that the upgraded system is absolutely purposeful. Then the method is finished once more within the manufacturing surroundings.
When an engineer’s time is freed up by automation, extra effort could be allotted to delivering new capabilities to the warfighter, with extra effectivity, greater high quality, and fewer danger of safety vulnerabilities. Steady deployment of functionality describes a set of ideas and practices that present quicker supply of safe software program capabilities by bettering the collaboration and communication that hyperlinks software program growth groups with IT operations and safety employees, in addition to with acquirers, suppliers, and different system stakeholders.
Whereas this strategy advantages software program growth typically, we recommend that it’s particularly necessary in high-stakes software program for nationwide safety missions.
On this publish, we describe our strategy to utilizing DevSecOps instruments for automating the supply of third-party software program to growth groups utilizing CI/CD pipelines. This strategy is focused to software program programs which can be container suitable.
Constructing an Automated Configuration Testing Pipeline
Not each staff in a software-oriented group is targeted particularly on the engineering of the software program product. Our staff bears duty for 2 typically competing duties:
- Delivering beneficial expertise, equivalent to instruments for automated testing, to software program engineers that permits them to carry out product growth and
- Deploying safety updates to the expertise.
In different phrases, supply of worth within the steady deployment of functionality could typically not be straight centered on the event of any particular product. Different dimensions of worth embrace “the folks, processes, and expertise needed to construct, deploy, and function the enterprise’s merchandise. Normally, this enterprise concern consists of the software program manufacturing unit and product operational environments; nevertheless, it doesn’t encompass the merchandise.”
To enhance our capacity to finish these duties, we designed and applied a customized pipeline that was a variation of the standard steady integration/steady deployment (CI/CD) pipeline discovered in lots of conventional DevSecOps workflows as proven beneath.

Determine 1: The DevSecOps Infinity diagram, which represents the continual integration/steady deployment (CI/CD) pipeline discovered in lots of conventional DevSecOps workflows.
The principle distinction between our pipeline and a conventional CI/CD pipeline is that we aren’t creating the applying that’s being deployed; the software program is often supplied by a third-party vendor. Our focus is on delivering it to our surroundings, deploying it onto our info programs, working it, and monitoring it for correct performance.
Automation can yield terrific advantages in productiveness, effectivity, and safety all through a corporation. Which means engineers can hold their programs safer and deal with vulnerabilities extra shortly and with out human intervention, with the impact that programs are extra readily saved compliant, secure, and safe. In different phrases, automation of the related pipeline processes can improve our staff’s productiveness, implement safety compliance, and enhance the consumer expertise for our software program engineers.
There are, nevertheless, some potential destructive outcomes when it’s achieved incorrectly. You will need to acknowledge that as a result of automation permits for a lot of actions to be carried out in fast succession, there’s all the time the likelihood that these actions result in undesirable outcomes. Undesirable outcomes could also be unintentionally launched through buggy process-support code that doesn’t carry out the proper checks earlier than taking an motion or an unconsidered edge case in a posh system.
It’s due to this fact necessary to take precautions when you’re automating a course of. This ensures that guardrails are in place in order that automated processes can not fail and have an effect on manufacturing purposes, providers, or information. This could embrace, for instance, writing assessments that validate every stage of the automated course of, together with validity checks and secure and non-destructive halts when operations fail.
Growing significant assessments could also be difficult, requiring cautious and artistic consideration of the numerous methods a course of may fail, in addition to return the system to a working state ought to failures happen.
Our strategy to addressing this problem revolves round integration, regression, and purposeful assessments that will be run robotically within the pipeline. These assessments are required to make sure that the performance of the third-party utility was not affected by adjustments in configuration of the system, and likewise that new releases of the applying nonetheless interacted as anticipated with older variations’ configurations and setups.
Automating Containerized Deployments Utilizing a CI/CD Pipeline
A Case Research: Implementing a Customized Steady Supply Pipeline
Groups on the SEI have intensive expertise constructing DevSecOps pipelines. One staff specifically outlined the idea of making a minimal viable course of to border a pipeline’s construction earlier than diving into growth. This enables the entire teams engaged on the identical pipeline to collaborate extra effectively.
In our pipeline, we began with the primary half of the standard construction of a CI/CD pipeline that was already in place to help third-party software program launched by the seller. This gave us a possibility to dive deeper into the later phases of the pipelines: supply, testing, deployment, and operation. The top end result was a five-stage pipeline which automated testing and supply for the entire software program parts within the device suite within the occasion of configuration adjustments or new model releases.
To keep away from the numerous complexities concerned with delivering and deploying third-party software program natively on hosts in our surroundings, we opted for a container-based strategy. We developed the container construct specs, deployment specs, and pipeline job specs in our Git repository. This enabled us to vet any desired adjustments to the configurations utilizing code critiques earlier than they may very well be deployed in a manufacturing surroundings.
A 5-Stage Pipeline for Automating Testing and Supply within the Device Suite
Stage 1: Automated Model Detection
When the pipeline is run, it searches the seller website both for the user-specified launch or the newest launch of the applying in a container picture. If a brand new launch is discovered, the pipeline makes use of communication channels set as much as notify engineers of the invention. Then the pipeline robotically makes an attempt to soundly obtain the container picture straight from the seller. If the container picture is unable to be retrieved from the seller, the pipeline fails and alerts engineers to the difficulty.
Stage 2: Automated Vulnerability Scanning
After downloading the container from the seller website, it’s best observe to run some kind of vulnerability scanner to ensure that no apparent points that may have been missed by the distributors of their launch find yourself within the manufacturing deployment. The pipeline implements this additional layer of safety by using frequent container scanning instruments, If vulnerabilities are discovered within the container picture, the pipeline fails.
Stage 3: Automated Utility Deployment
At this level within the pipeline the brand new container picture has been efficiently downloaded and scanned. The following step is to arrange the pipeline’s surroundings in order that it resembles our manufacturing deployment’s surroundings as intently as doable. To realize this, we created a testing system inside a Docker in Docker (DIND) pipeline container that simulates the method of upgrading purposes in an actual deployment surroundings. The method retains observe of our configuration information for the software program and masses take a look at information into the applying to make sure that every little thing works as anticipated. To distinguish between these environments, we used an environment-based DevSecOps workflow (Determine 2: Git Department Diagram) that provides extra fine-grained management between configuration setups on every deployment surroundings. This workflow allows us to develop and take a look at on function branches, have interaction in code critiques when merging function branches into the principle department, automate testing on the principle department, and account for environmental variations between the take a look at and manufacturing code (e.g. completely different units of credentials are required in every surroundings).
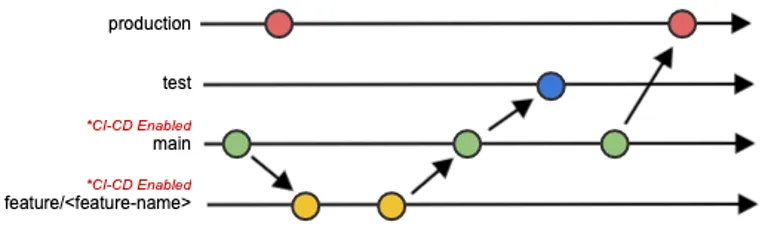
Determine 2: The Git Department Diagram
Since we’re utilizing containers, it’s not related that the container runs in two fully completely different environments between the pipeline and manufacturing deployments. The end result of the testing is predicted to be the identical in each environments.
Now, the applying is up and working contained in the pipeline. To higher simulate an actual deployment, we load take a look at information into the applying which can function a foundation for a later testing stage within the pipeline.
Stage 4: Automated Testing
Automated assessments on this stage of the pipeline fall into a number of classes. For this particular utility, essentially the most related testing methods are regression assessments, smoke assessments, and purposeful testing.
After the applying has been efficiently deployed within the pipeline, we run a sequence of assessments on the software program to make sure that it’s functioning and that there are not any points utilizing the configuration information that we supplied. A method that this may be achieved is by making use of the applying’s APIs to entry the information that was loaded in throughout Stage 3. It may be useful to learn by the third-party software program’s documentation and search for API references or endpoints that may simplify this course of. This ensures that you simply not solely take a look at fundamental performance of the applying, however that the system is functioning virtually as properly, and that the API utilization is sound.
Stage 5: Automated Supply
Lastly, after the entire earlier phases are accomplished efficiently, the pipeline will make the absolutely examined container picture out there to be used in manufacturing deployments. After the container has been completely examined within the pipeline and turns into out there, engineers can select to make use of the container in whichever surroundings they need (e.g., take a look at, high quality assurance, staging, manufacturing, and so forth.).
An necessary facet to supply is the communication channels that the pipeline makes use of to convey the data that has been collected. This SEI weblog publish explains the advantages of speaking straight with builders and DevSecOps engineers by channels which can be already part of their respective workflows.
It is crucial right here to make the excellence between supply and deployment. Supply refers back to the course of of creating software program out there to the programs the place it should find yourself being put in. In distinction, the time period deployment refers back to the strategy of robotically pushing the software program out to the system, making it out there to the tip customers. In our pipeline, we concentrate on supply as a substitute of deployment as a result of the providers for which we’re automating upgrades require a excessive diploma of reliability and uptime. A future objective of this work is to ultimately implement automated deployments.
Dealing with Pipeline Failures
With this mannequin for a customized pipeline, failures modes are designed into the method. When the pipeline fails, analysis of the failure ought to establish remedial actions to be undertaken by the engineers. These issues may very well be points with the configuration information, software program variations, take a look at information, file permissions, surroundings setup, or another unexpected error. By working an exhaustive sequence of assessments, engineers can come into the state of affairs geared up with a higher understanding of potential issues with the setup. This ensures that they’ll make the wanted changes as successfully as doable and keep away from working into the incompatibility points on a manufacturing deployment.
Implementation Challenges
We confronted some specific challenges in our experimentation, and we share them right here, since they could be instructive.
The primary problem was deciding how the pipeline could be designed. As a result of the pipeline remains to be evolving, flexibility was required by members of the staff to make sure there was a constant image concerning the standing of the pipeline and future targets. We additionally wanted the staff to remain dedicated to constantly bettering the pipeline. We discovered it useful to sync up frequently with progress updates so that everybody stayed on the identical web page all through the pipeline design and growth processes.
The following problem appeared in the course of the pipeline implementation course of. Whereas we have been migrating our information to a container-based platform, we found that lots of the containerized releases of various software program wanted in our pipeline lacked documentation. To make sure that all of the information we gained all through the design, growth, and implementation processes was shared by the complete staff, , we discovered it needed to write down a considerable amount of our personal documentation to function a reference all through the method.
A last problem was to beat a bent to stay with a working course of that’s minimally possible, however that fails to profit from trendy course of approaches and tooling. It may be simple to settle into the mindset of “this works for us” and “we’ve all the time achieved it this fashion” and fail to make the implementation of confirmed ideas and practices a precedence. Complexity and the price of preliminary setup generally is a main barrier to vary. Initially, we needed to grasp the effort of making our personal customized container photos that had the identical functionalities as an present, working programs. At the moment, we questioned whether or not this additional effort was even needed in any respect. Nevertheless, it grew to become clear that switching to containers considerably diminished the complexity of robotically deploying the software program in our surroundings, and that discount in complexity allowed the time and cognitive area for the addition of in depth automated testing of the improve course of and the performance of the upgraded system.
Now, as a substitute of manually performing all of the assessments required to make sure the upgraded system features appropriately, the engineers are solely alerted when an automatic take a look at fails and requires intervention. You will need to contemplate the assorted organizational obstacles that groups may run into whereas coping with implementing complicated pipelines.
Managing Technical Debt and Different Selections When Automating Your Software program Supply Workflow
When making the choice to automate a serious a part of your software program supply workflow, you will need to develop metrics to reveal advantages to the group to justify the funding of upfront effort and time into crafting and implementing all of the required assessments, studying the brand new workflow, and configuring the pipeline. In our experimentation, we judged that’s was a extremely worthwhile funding to make the change.
Fashionable CI/CD instruments and practices are a few of the greatest methods to assist fight technical debt. The automation pipelines that we applied have saved numerous hours for engineers and we anticipate will proceed to take action over time of operation. By automating the setup and testing stage for updates, engineers can deploy the newest variations of software program extra shortly and with extra confidence. This enables our staff to remain updated on software program releases to higher help our clients’ wants and assist them keep present on safety patches. Our staff is ready to make the most of the newly freed up time to work on different analysis and initiatives that enhance the capabilities of the DoD warfighter.


