
Risk actors are utilizing Grok, X’s built-in AI assistant, to bypass hyperlink posting restrictions that the platform launched to scale back malicious promoting.
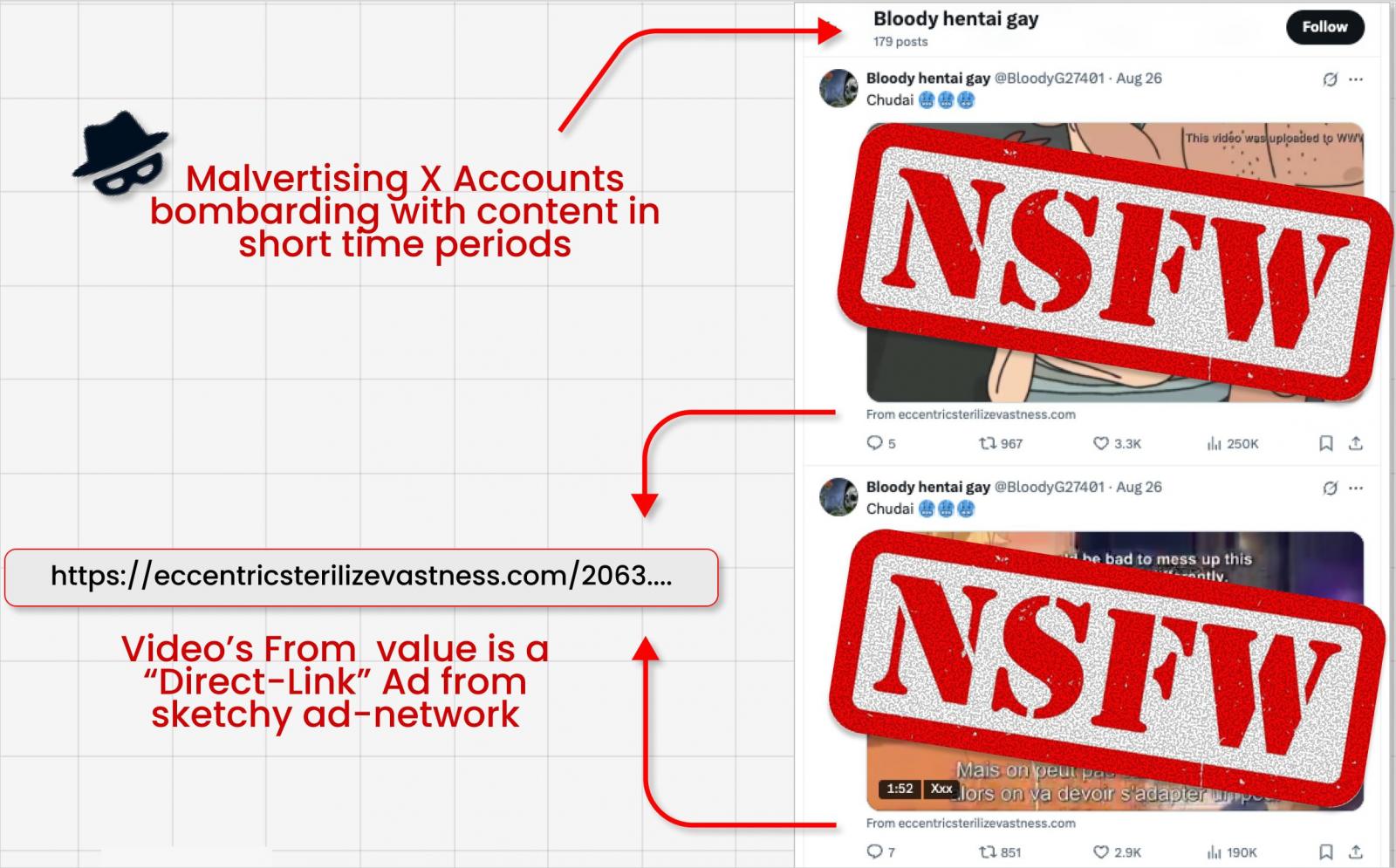
As found by Guardio Labs’ researcher Nati Tal, mavertisers usually run sketchy video adverts containing grownup content material baits and keep away from together with a hyperlink to the principle physique to keep away from being blocked by X.
As a substitute, they cover it within the small “From:” metadata discipline below the video card, which apparently is not scanned by the social media platform for malicious hyperlinks.
Supply: @bananahacks
Subsequent, (seemingly) the identical actors ask Grok through a reply to the advert one thing in regards to the submit, like “the place is that this video from,” or “what’s the hyperlink to this video.”
Grok parses the hidden “From:” discipline and replies with the complete malicious hyperlink in clickable format, permitting customers to click on it and go straight to the malicious web site.
As a result of Grok is routinely a trusted system account on the X platform, its submit boosts the hyperlink’s credibility, attain, search engine optimisation, and status, growing the probability that it will likely be broadcast to a lot of customers.
The researcher has discovered that many of those hyperlinks funnel by means of shady advert networks, resulting in scams similar to faux CAPTCHA exams, information-stealing malware, and different malicious payloads.
As a substitute of being blocked by X, they’re as an alternative promoted to customers on the platform through malicious adverts that obtain an extra enhance from Grok.
Tal calls the strategy of exploiting this loophole “Grokking,” and notes that it is very efficient, in some circumstances amplifying malicious adverts to achieve thousands and thousands of impressions, as proven beneath.
Potential options embrace scanning all fields, blocking hidden hyperlinks, and including context sanitization to Grok, so the AI assistant doesn’t blindly echo hyperlinks when requested by customers, however as an alternative filters and checks them in opposition to blocklists.
Tal confirmed to us that he has contacted X to report the problem and obtained unofficial affirmation that Grok engineers obtained the report.
BleepingComputer has additionally contacted X to ask in the event that they’re conscious of this abuse and whether or not they plan to do something about it, however we obtained no response by publication time.



