
Over 800 N-able N-central servers stay unpatched towards a pair of vital safety vulnerabilities tagged as actively exploited final week.
N-central is a well-liked platform utilized by many managed companies suppliers (MSPs) and IT departments to watch and handle networks and gadgets from a centralized web-based console.
Tracked as CVE-2025-8875 and CVE-2025-8876, the 2 flaws can let authenticated attackers to inject instructions resulting from improper sanitization of consumer enter and execute instructions on unpatched gadgets by exploiting an insecure deserialization weak point, respectively.
N-able has patched them in N-central 2025.3.1 and informed BleepingComputer on Thursday that the safety bugs are actually underneath lively exploitation, urging admins to safe their servers earlier than additional data on the bugs is launched.
“Our safety investigations have proven proof of any such exploitation in a restricted variety of on-premises environments. Now we have not seen any proof of exploitation inside N-able hosted cloud environments,” N-able informed BleepingComputer.
“You have to improve your on-premises N-central to 2025.3.1. (Particulars of the CVEs can be revealed three weeks after the discharge as per our safety practices.),” N-able added in a Wednesday advisory.
On Friday, the web safety nonprofit Shadowserver Basis is monitoring 880 N-central servers which are nonetheless weak to assaults exploiting the 2 vulnerabilities, most of them situated in the US, Canada, and the Netherlands.
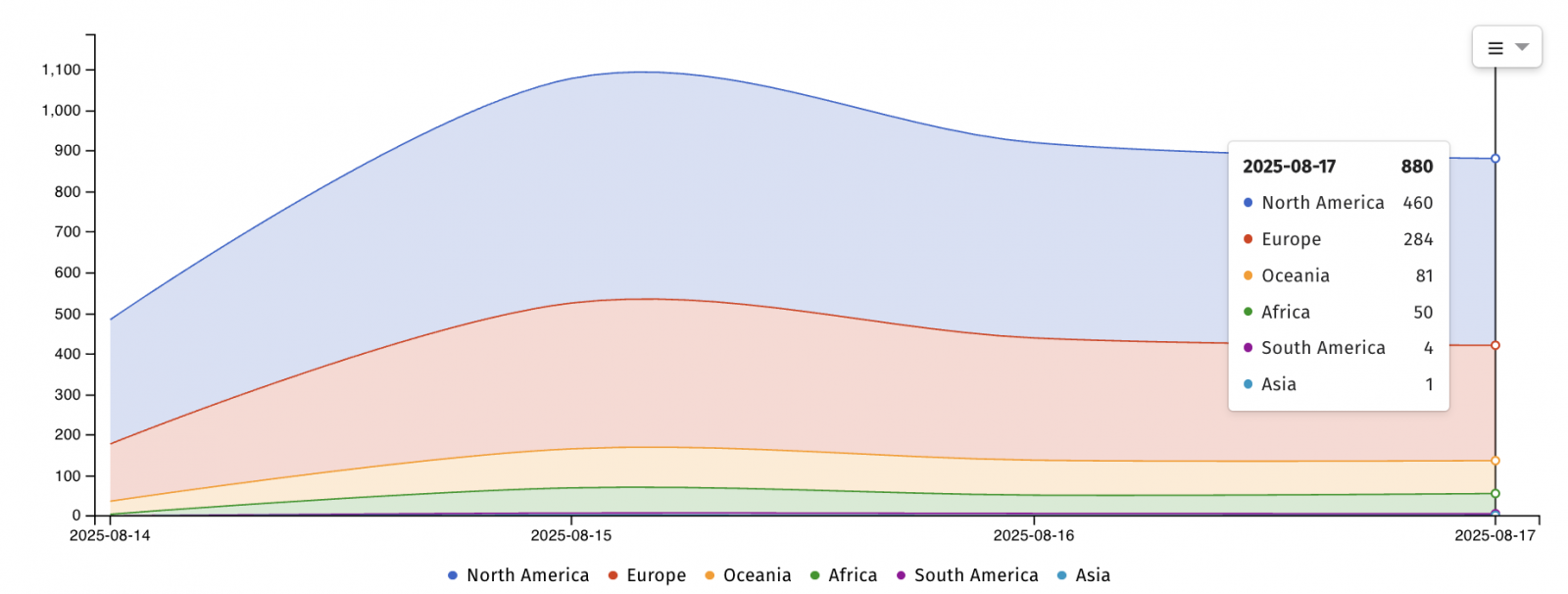
“These outcomes had been calculated by summing counts of distinctive IPs, which signifies that a ‘distinctive’ IP might have been counted greater than as soon as. Any figures ought to be handled as indicative fairly than precise,” Shadowserver stated.
In complete, roughly 2,000 N-central cases are at present uncovered on-line, in accordance with Shodan searches.
Federal companies ordered to mitigate inside every week
CISA has additionally added the failings to its Identified Exploited Vulnerabilities Catalog, tagging them as exploited in zero-day assaults at some point earlier than N-able confirmed the failings are being abused within the wild.
The U.S. cybersecurity company ordered all Federal Civilian Government Department (FCEB) companies, together with the Division of Homeland Safety, the Division of the Treasury, and the Division of Power, to patch their techniques inside one week, by August 20, as mandated by the November 2021 Binding Operational Directive (BOD) 22-01.
Though non-government organizations are usually not required to take motion, as BOD 22-01 primarily targets U.S. federal companies, CISA urged all community defenders to safe their techniques towards ongoing assaults.
“Apply mitigations per vendor directions, observe relevant BOD 22-01 steering for cloud companies, or discontinue use of the product if mitigations are unavailable,” CISA stated.
“All these vulnerabilities are frequent assault vectors for malicious cyber actors and pose important dangers to the federal enterprise.”



