
A set of 57 Chrome extensions with 6,000,000 customers have been found with very dangerous capabilities, equivalent to monitoring shopping habits, accessing cookies for domains, and probably executing distant scripts.
These extensions are ‘hidden,’ that means they do not present up on Chrome Internet Retailer searches, nor do search engines like google index them, and may solely be put in if the consumer has the direct URL.
Sometimes, such extensions are non-public software program like inside firm instruments or add-ons nonetheless beneath growth. Nonetheless, risk actors is perhaps utilizing them to evade detection whereas aggressively pushing them by means of adverts and malicious websites.
Dangerous Chrome extensions
The extensions have been found by Safe Annex researcher John Tuckner, who uncovered the primary 35 after analyzing what he claims is a suspicious extension named ‘Hearth Protect Extension Safety.’
The extension is closely obfuscated and incorporates callbacks to an API for sending data collected from the browser.
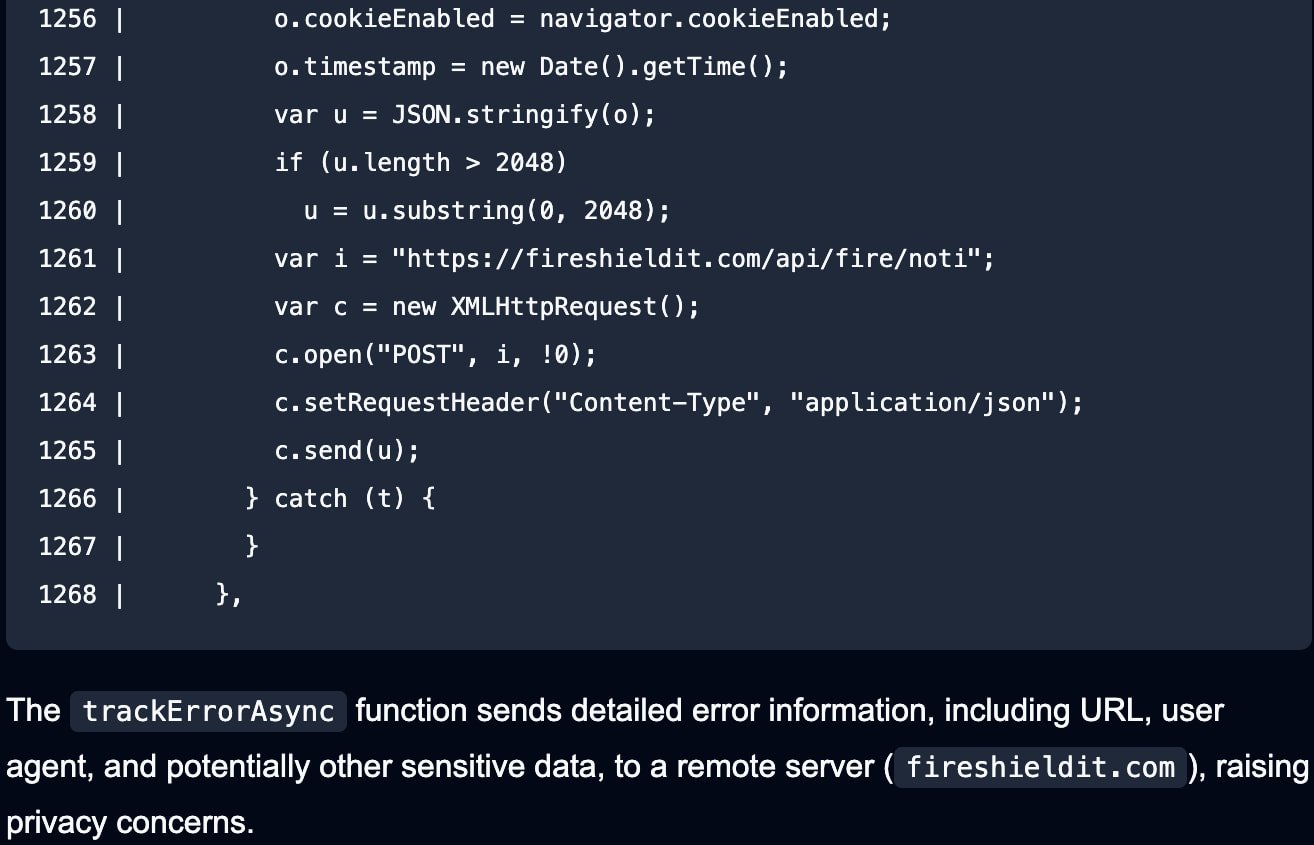
Supply: Safe Annex
By a website known as “unknow.com” contained within the extension, Tuckner discovered further extensions containing the identical area that declare to supply ad-blocking or privateness safety providers.
.jpg)
Supply: Safe Annex
Nonetheless, all of those embody overly broad permissions permitting them to carry out the next actions:
- Entry cookies, together with delicate headers (e.g., ‘Authorization’)
- Monitor consumer shopping habits
- Modify search suppliers (and outcomes)
- Inject and execute distant scripts on visited pages by way of iframes
- Activate superior monitoring remotely
Whereas Tuckner did not catch any extensions stealing consumer passwords or cookies, the excessively dangerous capabilities, closely obfuscated code, and hidden logic have been sufficient for the researcher to label them as dangerous and, probably, spyware and adware.
“There are further obfuscated alerts in different capabilities that there’s important command and management potential like the flexibility to checklist prime websites visited, open/shut tabs, get prime websites visited, and run lots of the capabilities above in an advert hoc method,” explains Tuckner.
“Many of those capabilities haven’t been validated, however once more, the presence of this functionality in 35 extensions which declare to do easy issues like shield you from malicious extensions is sort of regarding.”
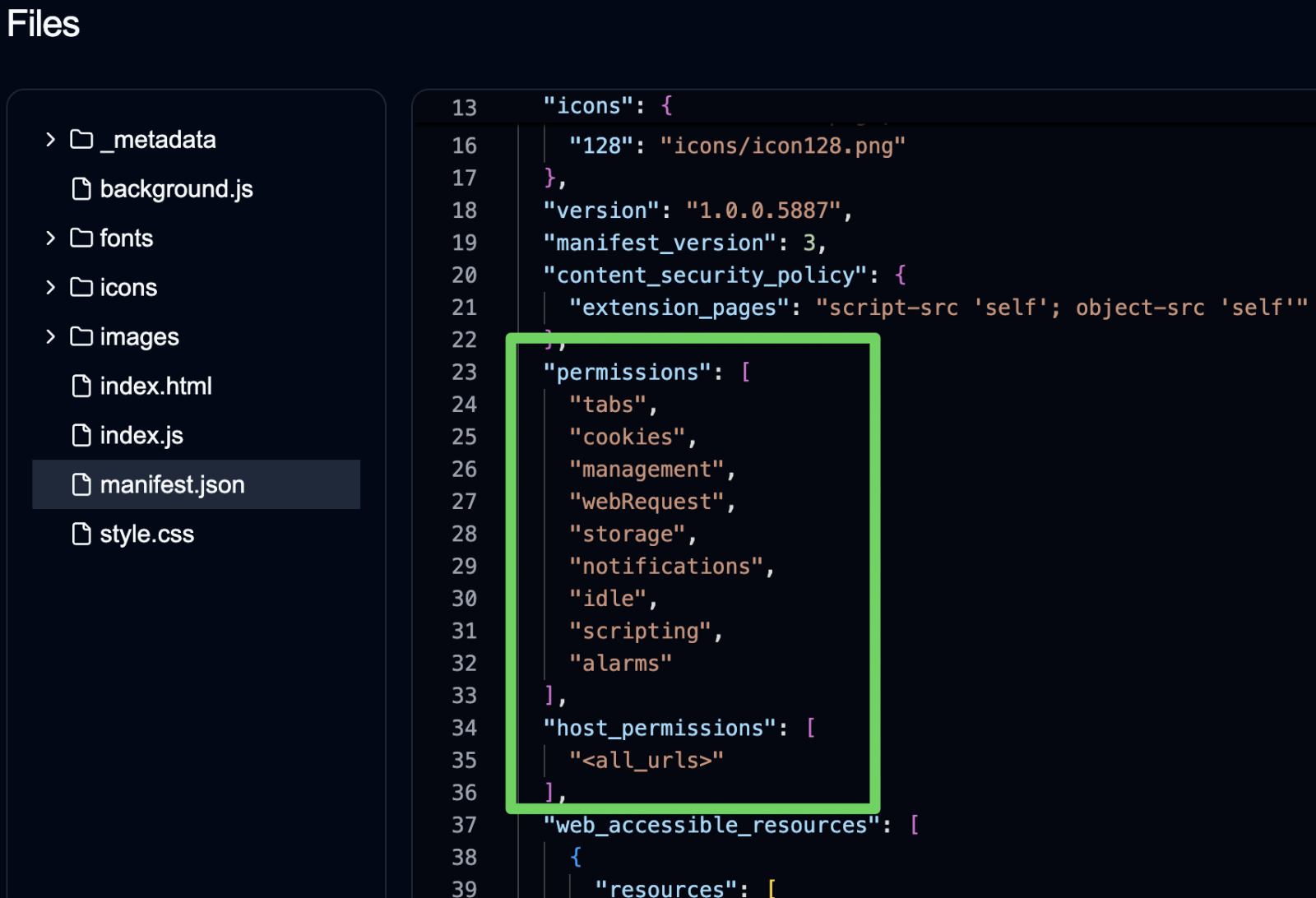
Supply: Safe Annex
Earlier as we speak, the researcher added 22 extra extensions believed to belong to the identical operation, taking the whole to 57 extensions utilized by 6 million folks. A number of the newly added extensions are public, too.
Tuckner says that lots of the extensions have been faraway from the Chrome Internet Retailer following his report from final week, however others nonetheless stay.
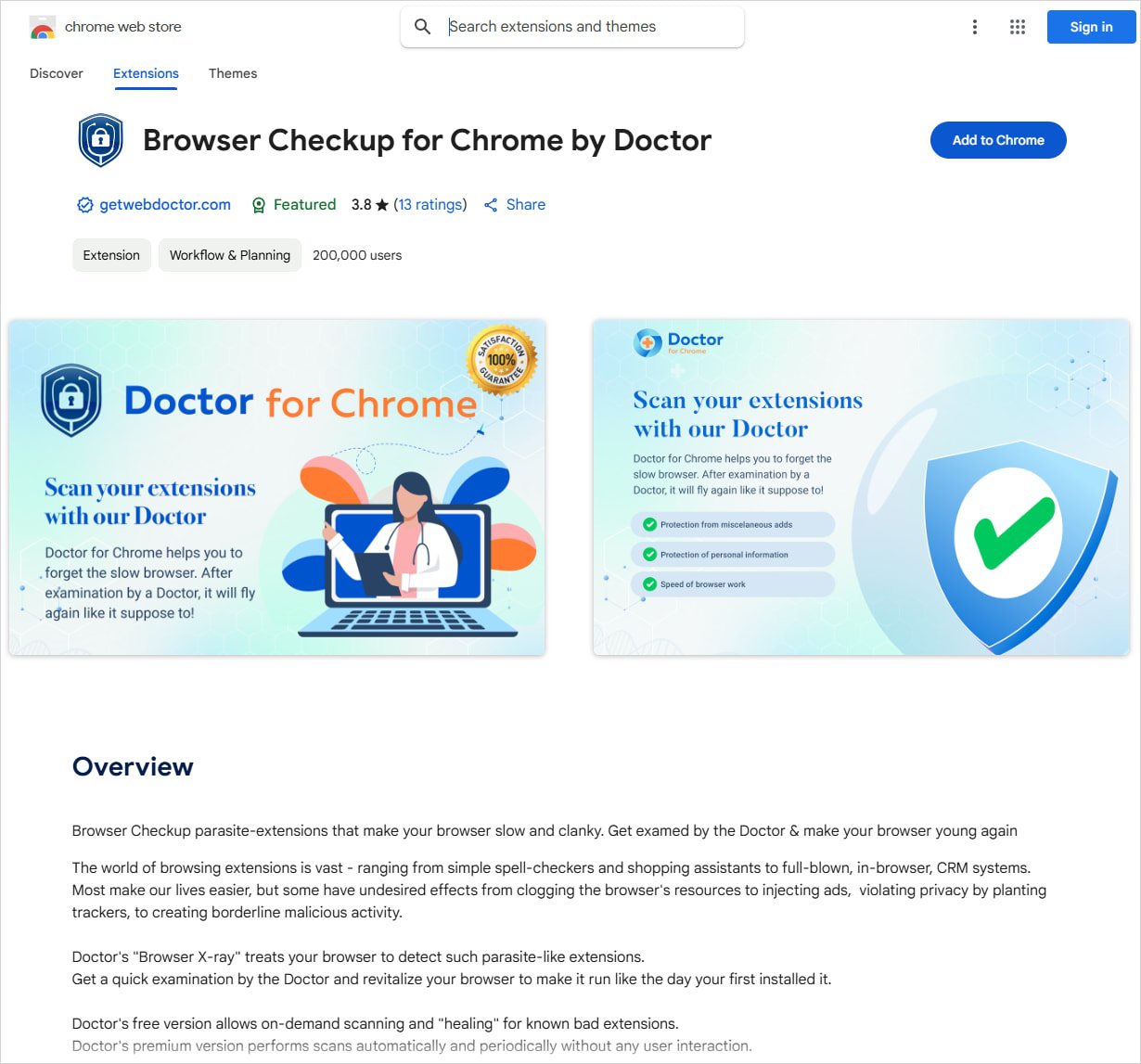
Supply: BleepingComputer
The whole checklist is out there right here, with those with the best obtain counts listed beneath:
- Cuponomia – Coupon and Cashback (700,000 customers, public)
- Hearth Protect Extension Safety (300,000 customers, unlisted)
- Whole Security for Chrome™ (300,000 customers, unlisted)
- Protecto for Chrome™ (200,000 customers, unlisted)
- Browser WatchDog for Chrome (200,000 customers, public)
- Securify for Chrome™ (200,000 customers, unlisted)
- Browser Checkup for Chrome by Physician (200,000 customers, public)
- Select Your Chrome Instruments (200,000 customers, unlisted)
In case you have any of the above put in, it’s endorsed that you simply take away them instantly and, out of an abundance of warning, carry out password resets on on-line accounts.
Google instructed BleepingComputer that they’re conscious of Tuckner’s report and are investigating the extensions.
BleepingComputer additionally contacted the developer of those extensions with questions in regards to the obfucated code however has not acquired a reply right now.


