
CISA warned on Wednesday that attackers are actively exploiting two safety vulnerabilities in N‑in a position’s N-central distant monitoring and administration (RMM) platform.
N-central is usually utilized by managed companies suppliers (MSPs) and IT departments to watch, handle, and keep consumer networks and units from a centralized web-based console.
In keeping with CISA, the 2 flaws can enable risk actors to realize command execution by way of an insecure deserialization weak spot (CVE-2025-8875) and inject instructions by exploiting an improper sanitization of consumer enter vulnerability (CVE-2025-8876).
Though N-able has but to substantiate CISA’s report that the safety bugs at the moment are being exploited within the wild, the corporate patched them in N-central 2025.3.1. It additionally urged admins to safe their programs earlier than additional data on the bugs is launched.
“This launch features a important safety repair for CVE-2025-8875 and CVE-2025-8876. These vulnerabilities require authentication to take advantage of. Nonetheless, there’s a potential danger to the safety of your N-central setting, if unpatched,” N-able stated in a Wednesday advisory.
“You need to improve your on-premises N-central to 2025.3.1. (Particulars of the CVEs shall be printed three weeks after the discharge as per our safety practices.)”
Whereas the U.S. cybersecurity company has not but shared particulars concerning the assaults exploiting these N-central safety bugs, it said that there is not any proof that they are being utilized in ransomware assaults.
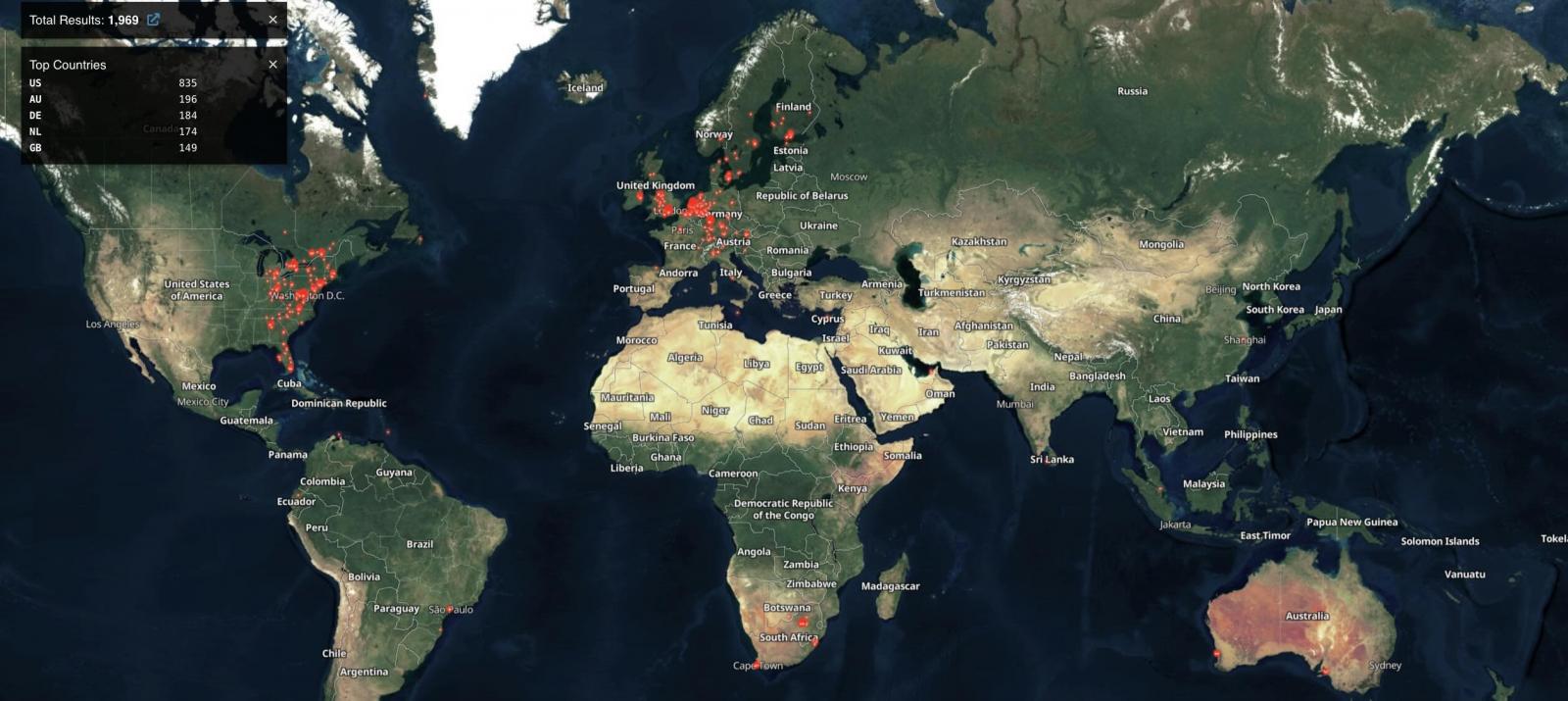
In keeping with Shodan searches, roughly 2,000 N-able N-central situations are uncovered on-line (a few of that are seemingly already patched), with the bulk originating from america, Australia, and Germany.
CISA has additionally added the failings to its Identified Exploited Vulnerabilities Catalog, giving Federal Civilian Govt Department (FCEB) businesses only one week to patch their programs by August 20, as mandated by the November 2021 Binding Operational Directive (BOD) 22-01.
Regardless that BOD 22-01 primarily targets U.S. federal businesses, CISA inspired all organizations, together with these within the personal sector, to prioritize securing their units towards this actively exploited safety flaw as quickly as potential.
“Apply mitigations per vendor directions, observe relevant BOD 22-01 steerage for cloud companies, or discontinue use of the product if mitigations are unavailable,” CISA cautioned on Monday.
“A lot of these vulnerabilities are frequent assault vectors for malicious cyber actors and pose important dangers to the federal enterprise.”
Final week, CISA issued an emergency directive ordering non-military businesses throughout the U.S. govt department to mitigate a important Microsoft Change hybrid vulnerability (CVE-2025-53786) by 9:00 AM ET on Monday morning.



