
A brand new variant of the banking trojan ‘Coyote’ has begun abusing a Home windows accessibility function, Microsoft’s UI Automation framework, to establish which banking and cryptocurrency trade websites are accessed on the machine for potential credential theft.
Microsoft UIA is a Home windows accessibility framework designed to permit assistive applied sciences to work together with, examine, and management consumer interface (UI) parts in functions.
Home windows apps expose their UI parts by way of a UI Automation tree, and the UIA API offers a option to traverse it, question the properties of every factor, and work together with it.
Akamai researchers had warned about the opportunity of Home windows UIA being abused to steal credentials in December 2024, highlighting that the approach evades endpoint detection and response (EDR) protections.
Now, the identical researchers report that they’ve seen assaults leveraging the approach within the wild since February 2025, marking the primary real-world case of malware abusing Microsoft UIA for knowledge theft.
Coyote evolution and UIA abuse
Coyote is a banking trojan that makes an attempt to steal credentials for 75 banking and cryptocurrency trade apps, primarily concentrating on Brazilian customers.
The malware was first documented in February 2024, using ways resembling keylogging and phishing overlays, and has undergone important growth since then.
Akamai experiences that, whereas the newest Coyote variant continues to steal knowledge utilizing conventional strategies for hardcoded apps, it has added UIA abuse when the consumer opens web-based banking or cryptocurrency providers in a browser.
If Coyote can not establish a goal through the window title, it makes use of UIA to extract the online deal with from inside the browser’s UI parts (tabs or deal with bars). Lastly, it compares it in opposition to a hardcoded checklist of 75 focused providers.
“If no match is discovered, Coyote will then use UIA to parse by way of the UI youngster parts of the window in an try to establish browser tabs or deal with bars,” explains Akamai within the report.
“The content material of those UI parts will then be cross-referenced with the identical checklist of addresses from the primary comparability.”
A few of the banks and exchanges which might be recognized utilizing this methodology are Banco do Brasil, CaixaBank, Banco Bradesco, Santander, Unique financial institution, Sicredi, Banco do Nordeste, Expanse apps, and Cryptocurrency (Binance, Electrum, Bitcoin, Foxbit, and others).
Though the abuse of this Home windows accessibility function stops on the reconnaissance part, Akamai shared a proof-of-concept demonstration of how UIA will also be abused to steal inputted credentials for these websites.
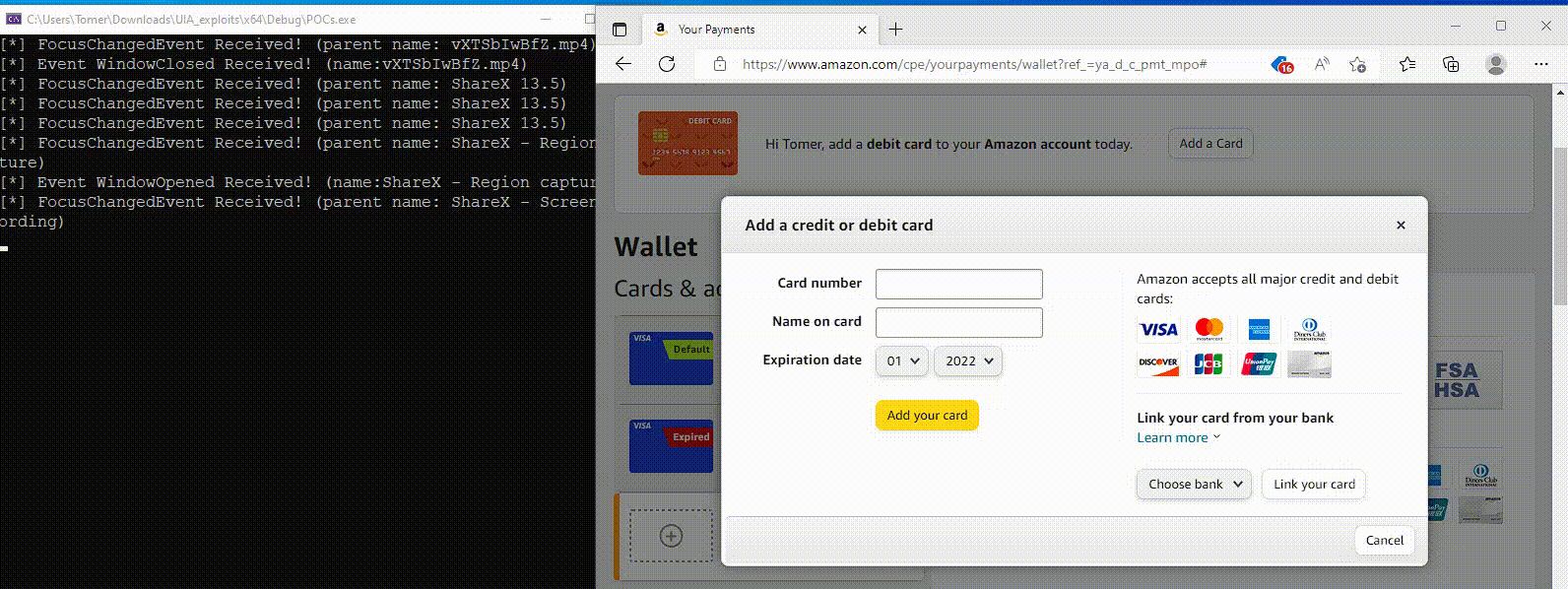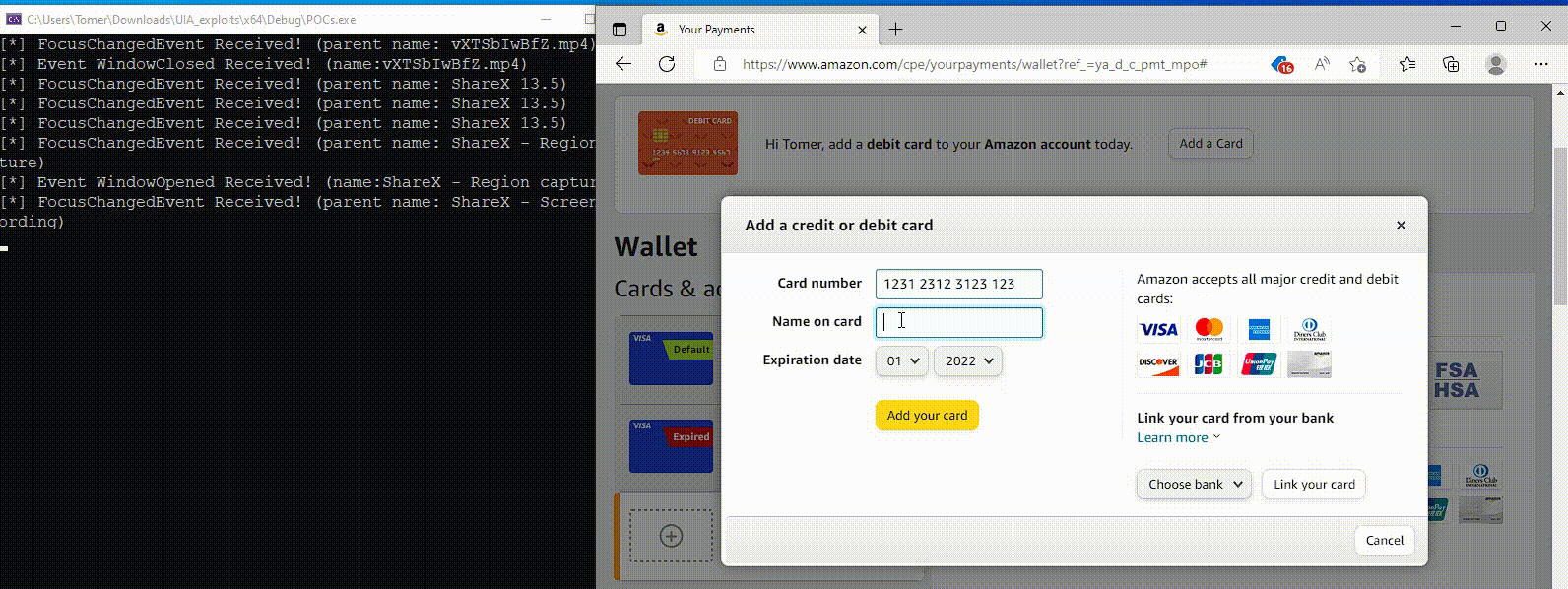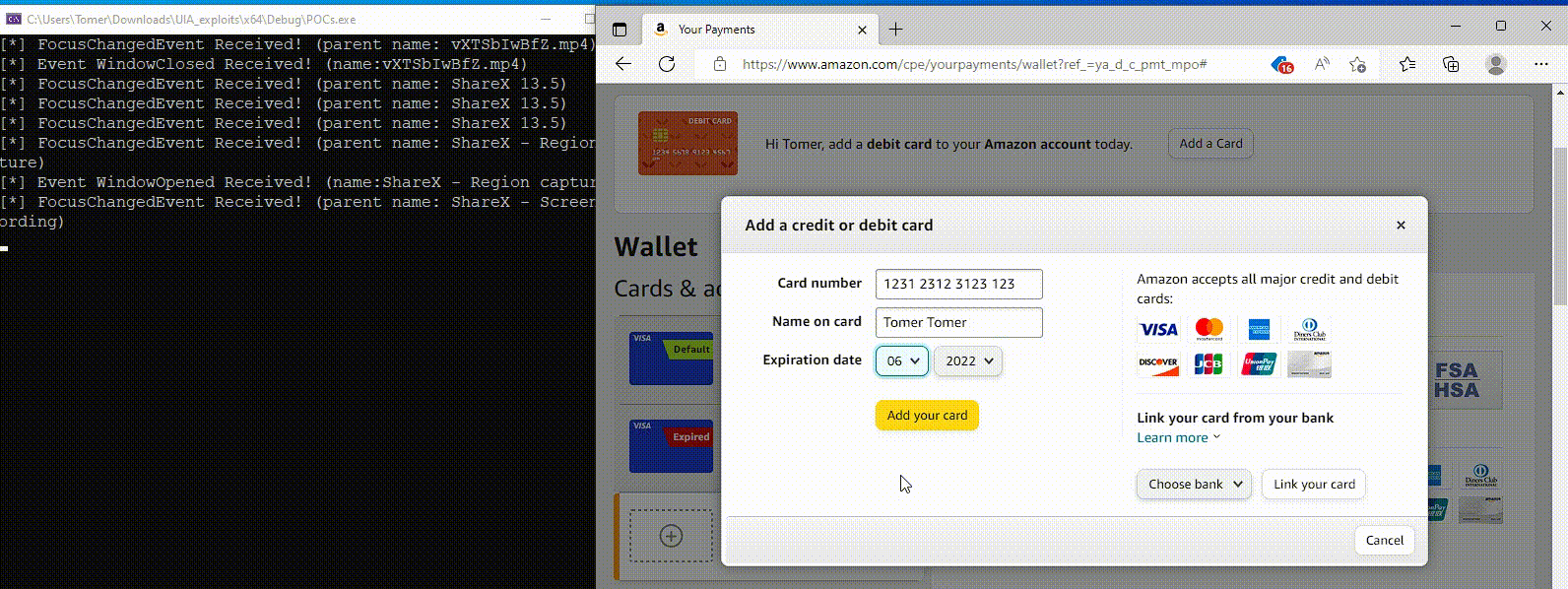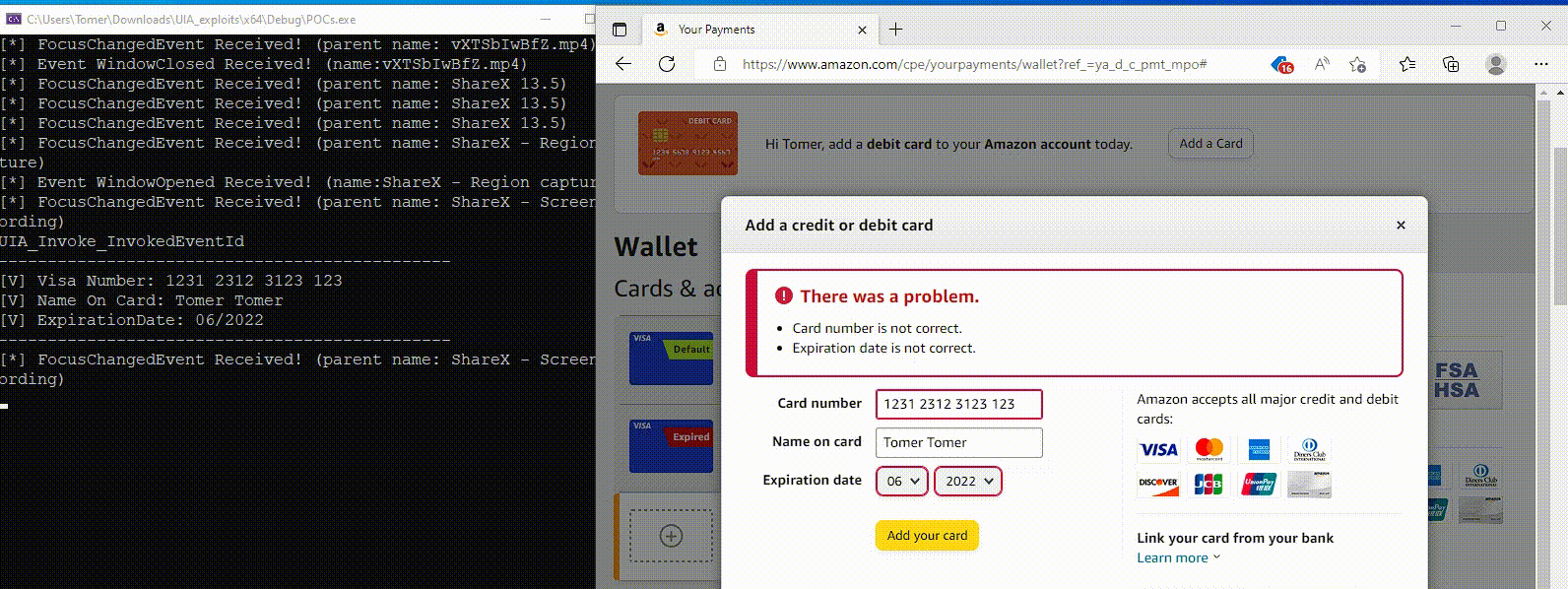
Supply: Akamai
BleepingComputer has contacted Microsoft to ask in regards to the potential introduction of safeguards to cease the abuse of UIA on Home windows, however a remark wasn’t instantly out there.
Accessibility methods are designed to be highly effective, permitting folks with disabilities to completely make the most of the capabilities of their units. Nonetheless, this energy additionally invitations malicious use.
In Android, this drawback has taken large proportions, with malware abusing Accessibility Companies extensively. Through the years, Google has applied a number of measures to handle this situation.



