
A PoisonSeed phishing marketing campaign is bypassing FIDO2 safety key protections by abusing the cross-device sign-in characteristic in WebAuthn to trick customers into approving login authentication requests from faux firm portals.
The PoisonSeed risk actors are identified to make use of large-volume phishing assaults for monetary fraud. Previously, distributing emails containing crypto seed phrases used to empty cryptocurrency wallets.
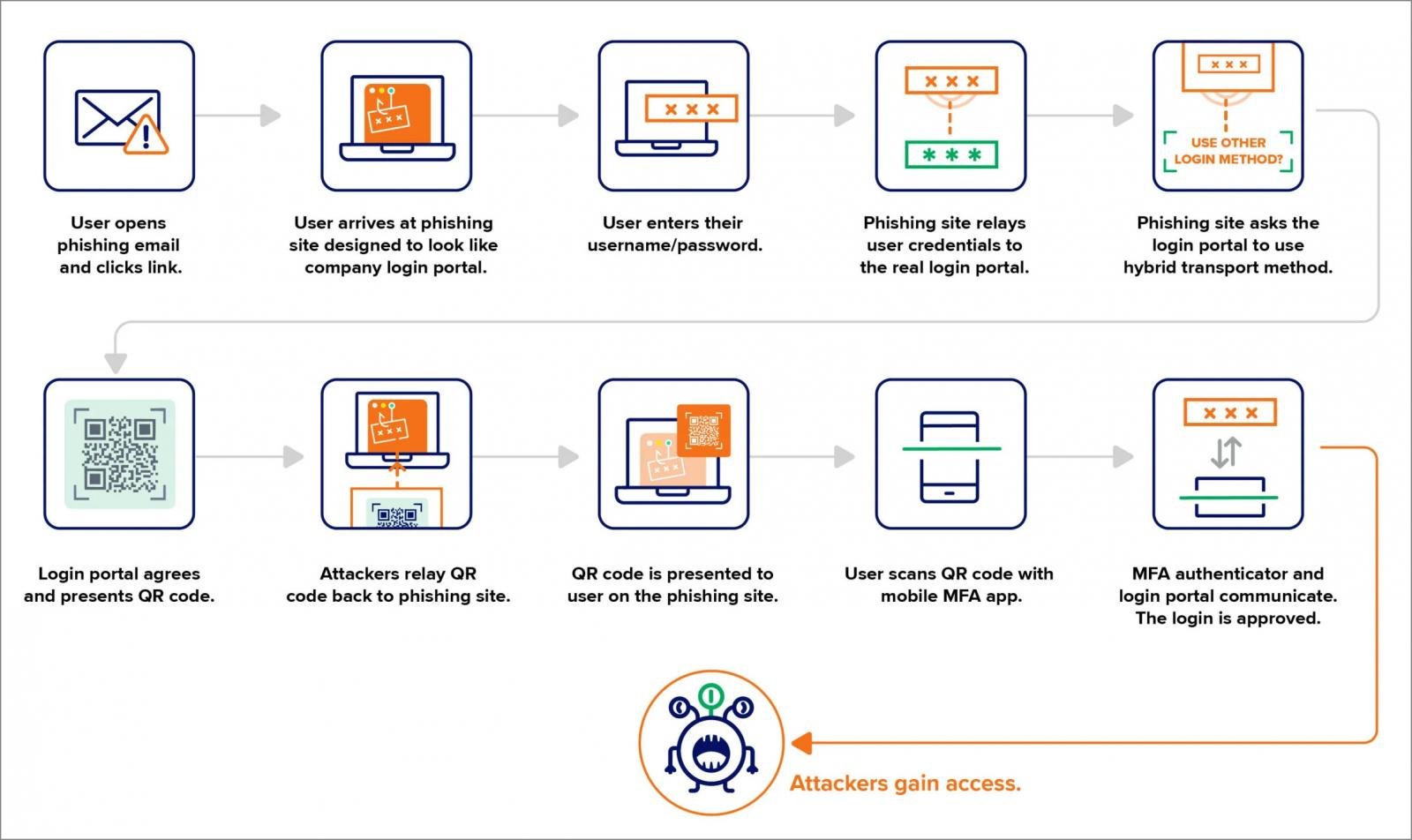
Within the latest phishing assault noticed by Expel, the PoisonSeed risk actors don’t exploit a flaw in FIDO2’s safety however somewhat abuse the official cross-device authentication characteristic.
Cross-device authentication is a WebAuthn characteristic that enables customers to check in on one gadget utilizing a safety key or authentication app on one other gadget. As a substitute of requiring a bodily connection, resembling plugging in a safety key, the authentication request is transmitted between units through Bluetooth or a QR code scan.
The assault begins by directing customers to a phishing web site that impersonates company login portals, resembling from Okta or Microsoft 365.
When the person enters their credentials into the portal, the marketing campaign makes use of an adversary-in-the-middle (AiTM) backend to silently log in with the submitted credentials on the official login portal in real-time.
The person focused within the assault usually would use their FIDO2 safety keys to confirm multi-factor authentication requests. Nevertheless, the phishing backend as a substitute tells the official login portal to authenticate utilizing cross-device authentication.
This causes the official portal to generate a QR code, which is transmitted again to the phishing web page and exhibited to the person.
When the person scans this QR code utilizing their smartphone or authentication app, it approves the login try initiated by the attacker.
Supply: Expel
This methodology successfully bypasses FIDO2 safety key protections by permitting attackers to provoke a login circulate that depends on cross-device authentication as a substitute of the person’s bodily FIDO2 key.
Expel warns that this assault doesn’t exploit a flaw within the FIDO2 implementation, however as a substitute abuses a official characteristic that downgrades the FIDO key authentication course of.
To mitigate the chance, Expel recommends the next defenses:
- Limiting geographic areas from which customers are allowed to log in and establishing a registration course of for people touring.
- Routinely verify for the registration of unknown FIDO keys from unknown areas and unusual safety key manufacturers.
- Organizations can take into account implementing Bluetooth-based authentication as a requirement for cross-device authentication, which considerably reduces the effectiveness of distant phishing assaults.
Expel additionally noticed a separate incident the place a risk actor registered their very own FIDO key after compromising an account through what’s believed to be phishing and resetting the password. Nevertheless, this assault didn’t require any strategies to trick the person, like a QR code.
This assault highlights how risk actors are discovering methods to bypass phishing-resistant authentication by tricking customers into finishing login flows that bypass the necessity for bodily interplay with a safety key.



