Authored by Dexter Shin
McAfee’s Cell Analysis Crew found a brand new and lively Android malware marketing campaign focusing on Bengali-speaking customers, primarily Bangladeshi individuals residing overseas. The app poses as fashionable monetary companies like TapTap Ship and AlimaPay. It’s distributed by phishing websites and FacebookFacekbook pages, and the app steals customers’ private and monetary data. The marketing campaign stays extremely lively, with the command-and-control (C2) server operational and linked to a number of evolving domains. Whereas the assault strategies are usually not new, the marketing campaign’s cultural focusing on and sustained exercise replicate how cybercriminals proceed to adapt their methods to achieve particular communities. McAfee Cell Safety already detects this risk as Android/FakeApp. For extra data, go to McAfee Cell Safety.
Bangladeshi individuals residing overseas, significantly in nations equivalent to Saudi Arabia, the UAE, Malaysia, and the UK, rely closely on cell cash companies to ship remittances and confirm their identities for varied functions. Companies like bKash, TapTap Ship, and AlimaPay are broadly used and trusted inside this group.
In 2024, annual remittances despatched to Bangladesh reached almost $26.6 billion, rating sixth globally and third in South Asia. This huge stream of cross-border funds highlights the financial significance and digital engagement of the Bangladeshi diaspora.
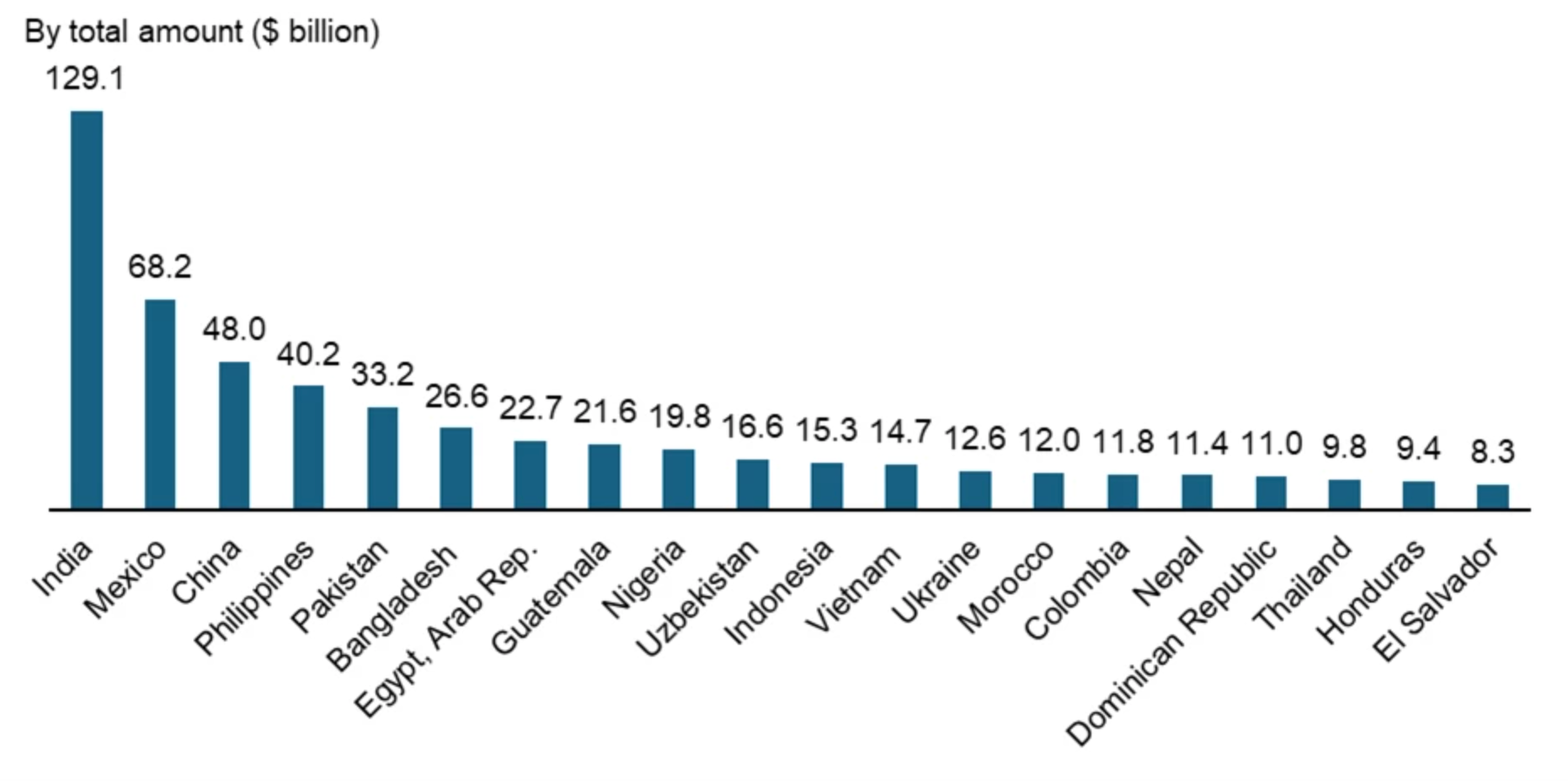
Determine 1. High Recipients of Remittances in 2024 (Supply: World Financial institution)
As extra individuals use cell monetary apps, cybercriminals are discovering new methods to trick them utilizing pretend apps and phishing web sites. Many customers belief apps shared by buddies or household, and a few could not know find out how to spot scams. This makes them straightforward targets for attackers.
In Could 2025, McAfee’s Cell Analysis Crew recognized a malware marketing campaign designed to use these circumstances. The pretend Android app impersonates well-known cash switch companies and steals private data such because the consumer’s title, electronic mail deal with, cellphone quantity, and photograph ID (equivalent to a passport or nationwide ID card). It additionally makes an attempt to gather monetary knowledge like card numbers by pretend in-app pages. Furthermore, the C2 server’s storage is publicly uncovered, that means that the stolen knowledge could be accessed by anybody, which considerably will increase the chance of abuse.
Technical Findings
Distribution Strategies
Over the previous few weeks, these pretend apps have continued to seem, suggesting an lively and sustained marketing campaign focusing on Bengali-speaking customers. These apps are primarily distributed by phishing web sites that mimic trusted remittance companies, typically shared through pretend Fb pages.
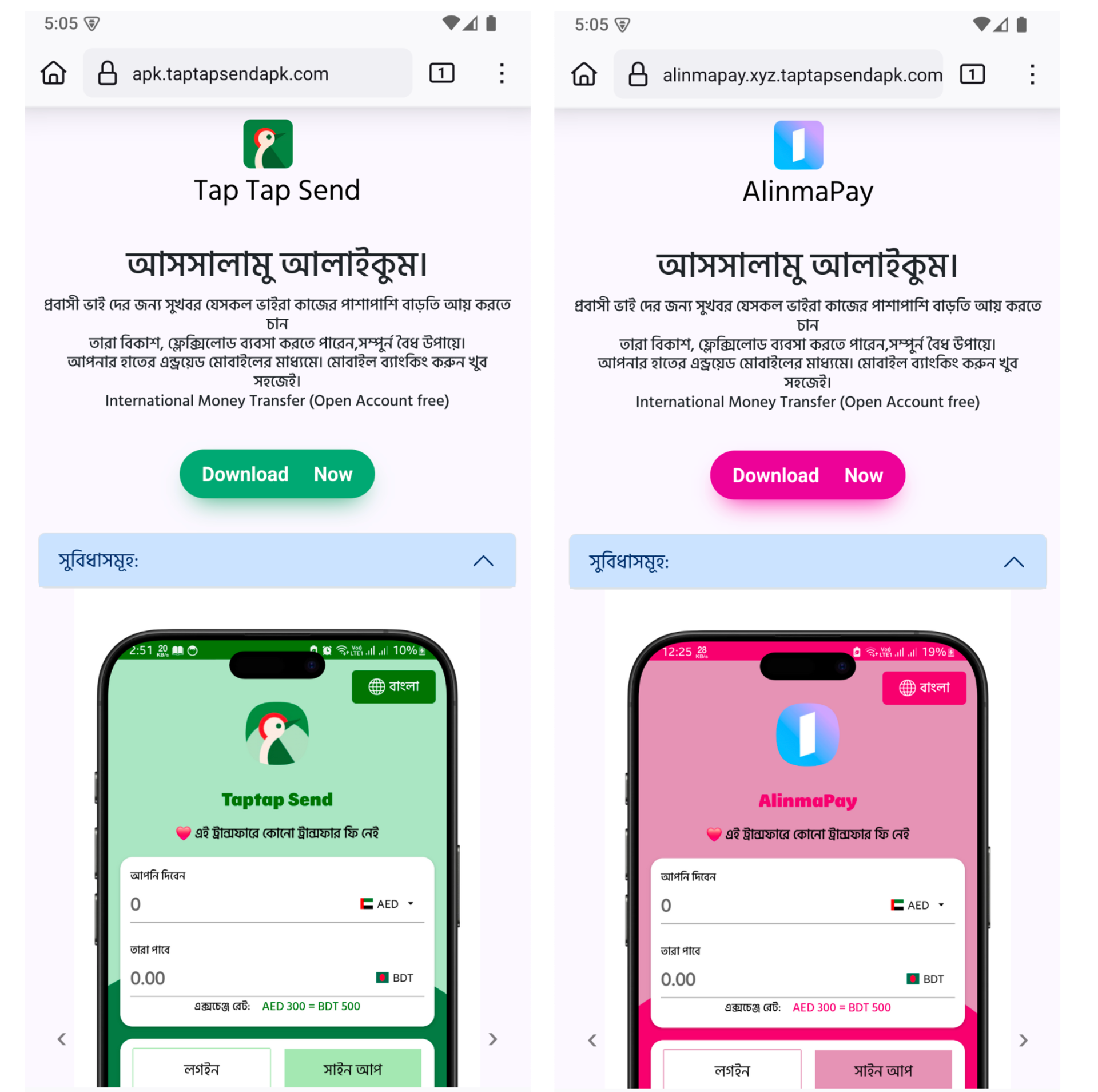
Determine 2. Screenshot of a phishing web site
The web page is written completely in Bengali, mimicking a professional remittance service generally utilized by Bangladeshi expatriates. Under is a translated excerpt of the principle message proven on the touchdown web page:
Bengali (unique):
আসসালামু আলাইকুম।
প্রবাসী ভাইদের জন্য সুখবর। যারা কাজের পাশাপাশি বাড়তি আয় করতে চান, তারা বিকাশ, ফ্ল্যাশলোড ব্যবসা করতে পারেন। সম্পূর্ণ বৈধ উপায়ে। আপনার হাতের মধ্যে রয়েছে মোবাইলের মাধ্যমে। মোবাইল ব্যাংকিং করুন খুব সহজেই।
English (translation):
Peace be upon you.
Excellent news for our brothers residing overseas. If you happen to’re seeking to earn further revenue alongside together with your job, you are able to do enterprise with bKash or FlashLoad in a very authorized manner. All the pieces is inside your attain by cell. Cell banking could be very straightforward.
Along with phishing web sites, the attackers additionally created pretend Fb pages that intently resemble professional remittance companies. These pages typically reuse official logos, promotional photos, and even movies taken from actual monetary platforms to seem reliable. Nevertheless, the location hyperlinks on these pages level to phishing web sites internet hosting the malicious app.
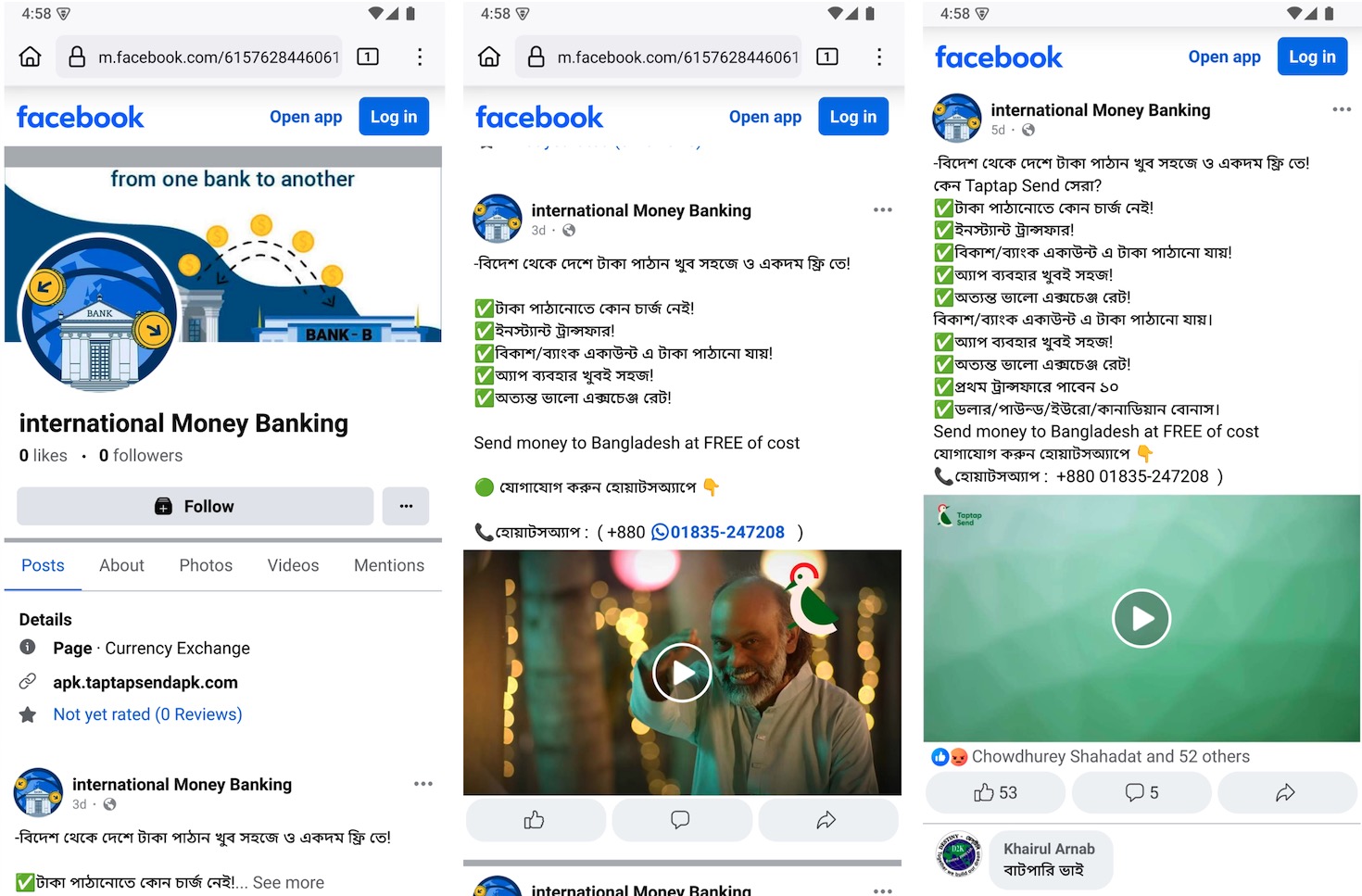
Determine 3. Faux Fb web page mimicking a professional remittance service
Faux App Evaluation
As soon as put in, the pretend app instantly presents an interface that intently resembles a professional remittance software. It helps each Bengali and English language choices and exhibits realistic-looking alternate charges.
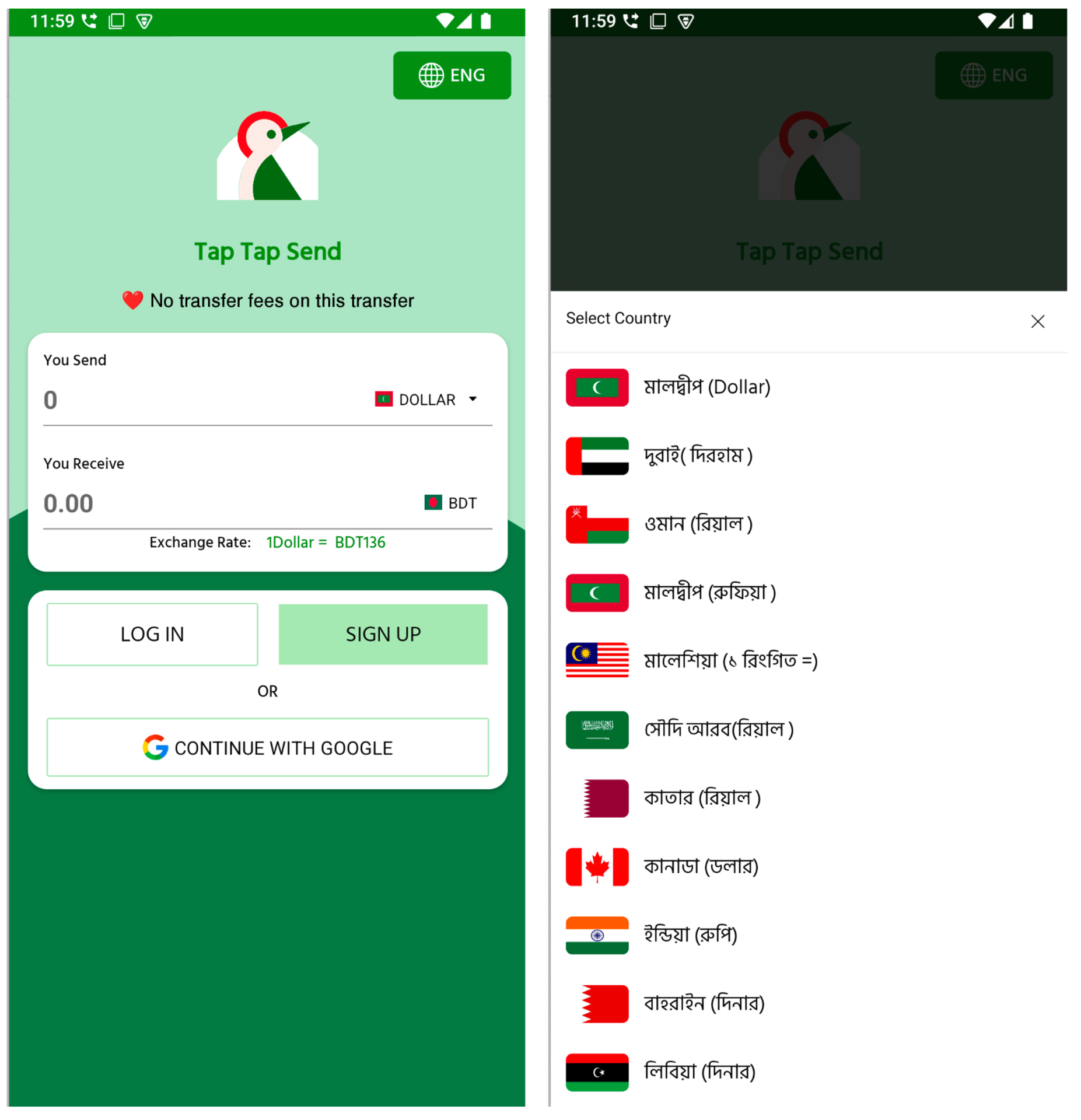
Determine 4. Preliminary UI of the pretend TapTap Ship app
Customers can choose from an inventory of nations with giant Bangladeshi expatriate populations, equivalent to Maldives, Dubai, Oman, Saudi Arabia, Malaysia, Canada, and India, to simulate cash transfers to Bangladeshi Taka (BDT). These particulars are possible included to ascertain belief and make the app seem practical. Nevertheless, these screens function bait to encourage customers to proceed with account creation and enter private data. As customers proceed by the registration stream, the app requests more and more delicate knowledge in a number of levels. First, it requests the consumer’s electronic mail deal with and full title. Then, it prompts them to pick their nation of residence and supply a legitimate cell quantity. Subsequent, customers are requested to decide on an account kind, both “Private” or “Agent”, a distinction generally seen in actual remittance platforms.
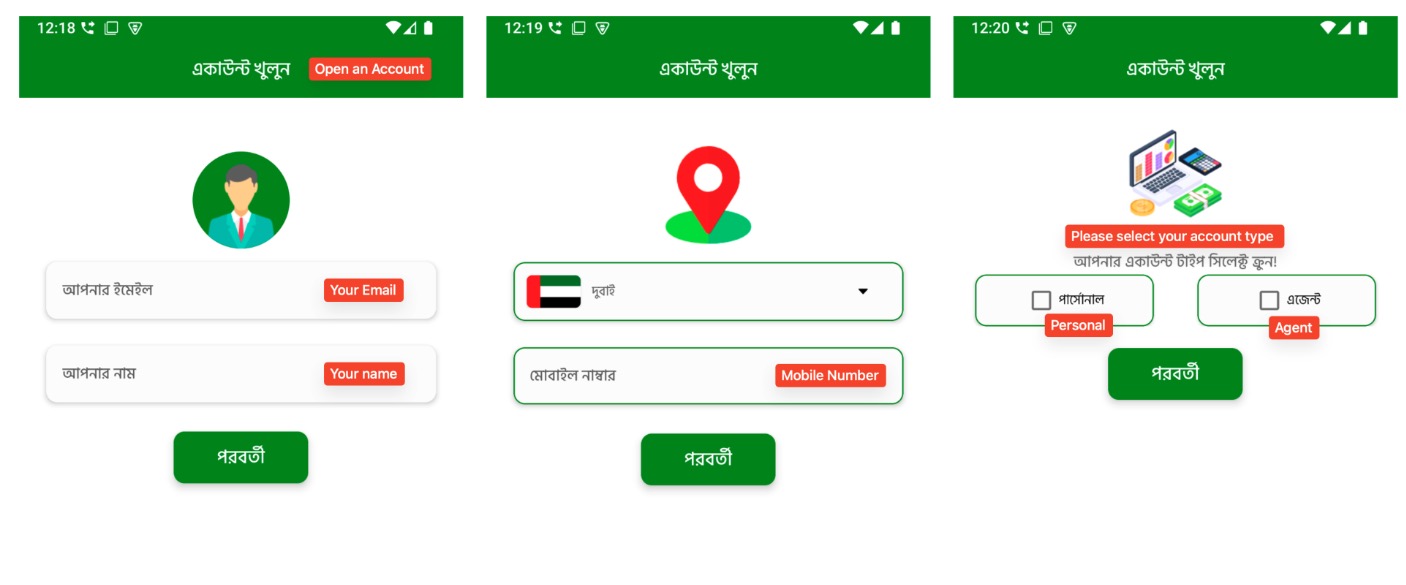
Determine 5. Multi-step registration stream (1)
Following this, the app reaches its most delicate stage: it asks the consumer to take and add a photograph of an official ID, equivalent to a passport, nationwide ID (NID), or an e-commerce verification photograph. This request is made within the native language and framed as a requirement to finish account setup. After importing the ID, customers are then requested to create a login password and a 5-digit PIN, identical to actual monetary apps. This step makes the app really feel extra reliable and safe, however the collected credentials may later be utilized in credential stuffing assaults. All of this data is distributed to the C2 server and saved, making it accessible for future fraud or identification theft.
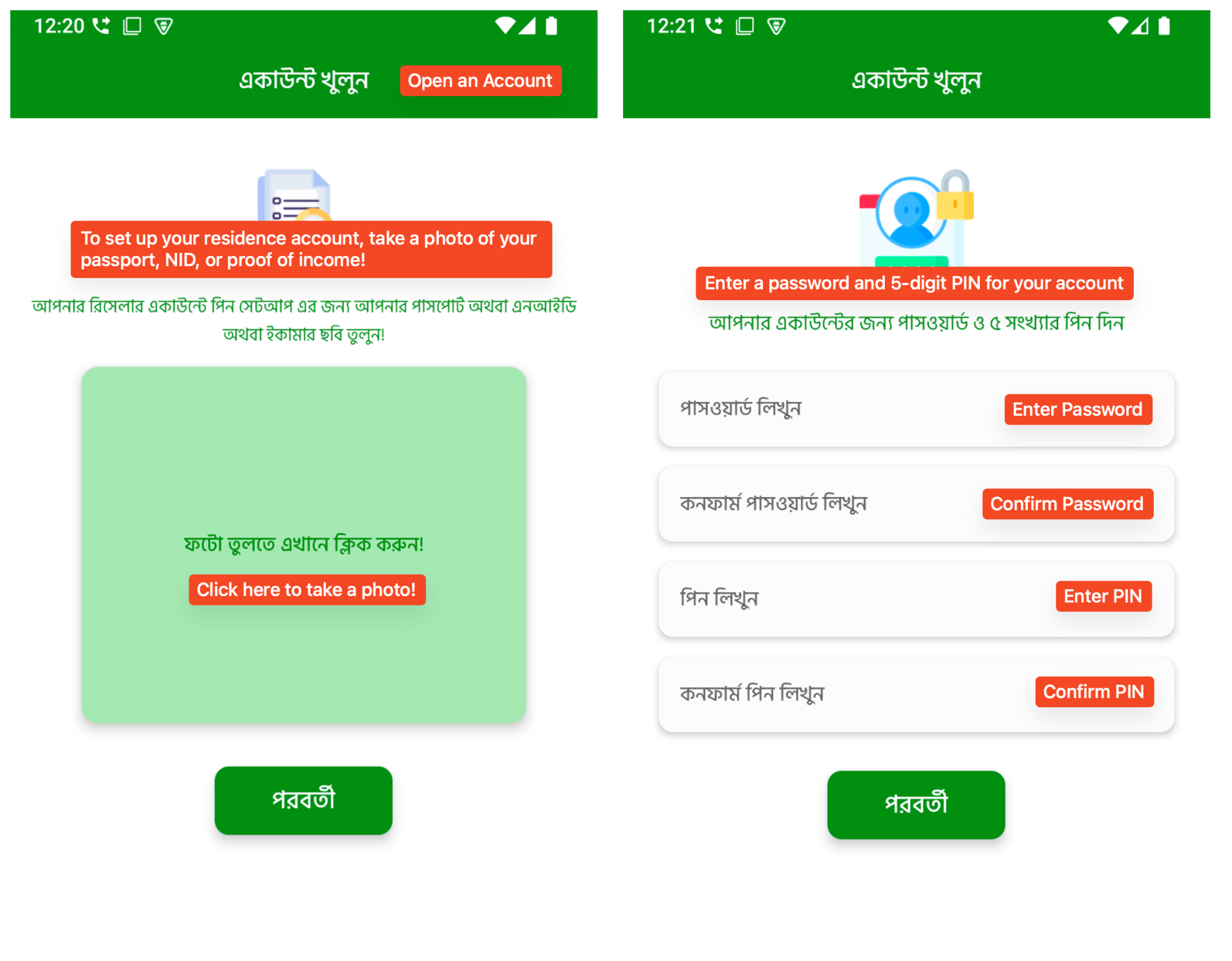
Determine 6. Multi-step registration stream (2)
After finishing the registration course of, customers are taken to a totally designed dashboard. The interface mimics an actual monetary or remittance app, full with icons for cash switch, invoice fee, cell banking, and even buyer help options.

Determine 7. The pretend TapTap Ship app’s predominant dashboard
The malware consists of a number of pretend transaction interfaces. These screens simulate cell cash transfers, invoice funds, and financial institution transfers utilizing logos from actual companies. Though no precise transaction is carried out, the app collects all entered data equivalent to cellphone numbers, account particulars, PINs, and fee quantities. This knowledge is then transmitted to the C2 server.
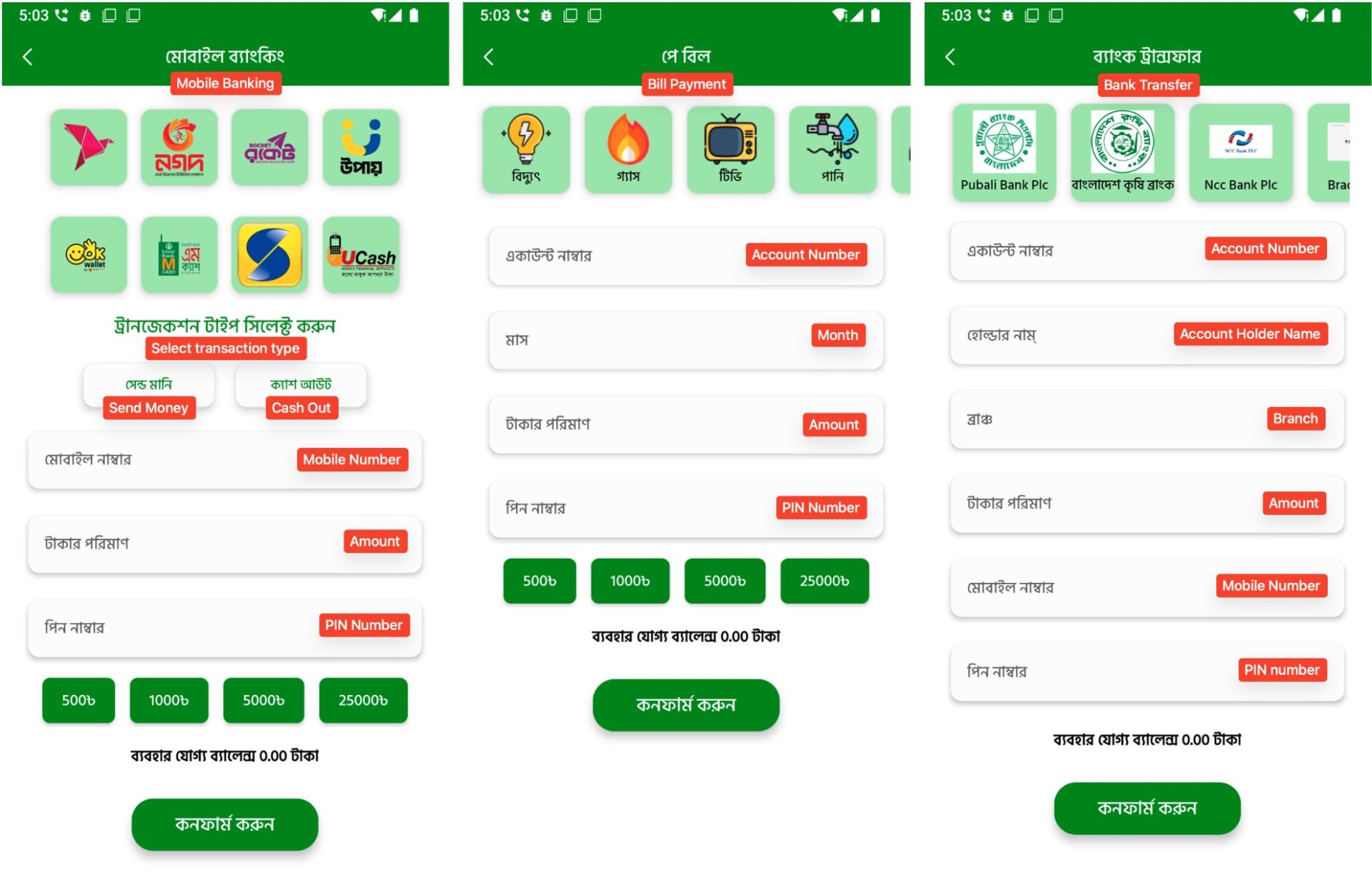
Determine 8. Faux transaction screens that imitate actual monetary companies
C2 Server and Information Exfiltration
All the knowledge collected by the pretend app, together with credentials, contact particulars, and photograph IDs, is saved on the C2 server. Nevertheless, the server lacks primary safety settings. Listing itemizing is enabled, which suggests anybody can entry the uploaded recordsdata with out authentication. Throughout our investigation, we discovered that one of many C2 domains contained 297 picture recordsdata. These recordsdata look like photograph IDs uploaded by customers in the course of the registration course of.

Determine 9. Publicly accessible listing itemizing on the C2 server
These ID photos embody extremely delicate private data and are publicly accessible. If downloaded or misused, they might pose a severe privateness and identification theft threat.

Determine 10. Instance of a delicate photograph ID picture uploaded throughout app registration
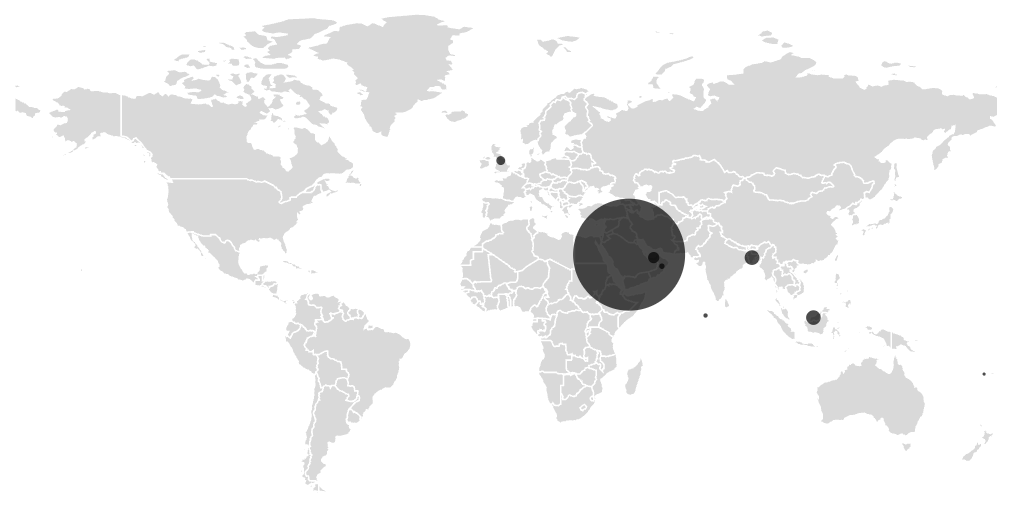
Determine 11. Geographic distribution of contaminated units
As anticipated, telemetry exhibits exercise in nations with giant Bangladeshi populations overseas, equivalent to Saudi Arabia, Malaysia, Bangladesh, and the United Arab Emirates. This aligns with the app’s focusing on of Bengali-speaking customers by culturally acquainted language and visuals. The marketing campaign stays lively, with new phishing domains and variants persevering with to seem. Given the evolving nature of this risk and its use of trusted platforms like Fb to distribute malicious content material, customers ought to keep cautious when encountering monetary service promotions by social media or unknown web sites. We advocate downloading apps solely from trusted sources equivalent to Google Play, avoiding hyperlinks shared through social media, and being further cautious when requested to offer private or banking data. Utilizing cell safety software program that may detect and block these threats can also be strongly suggested.
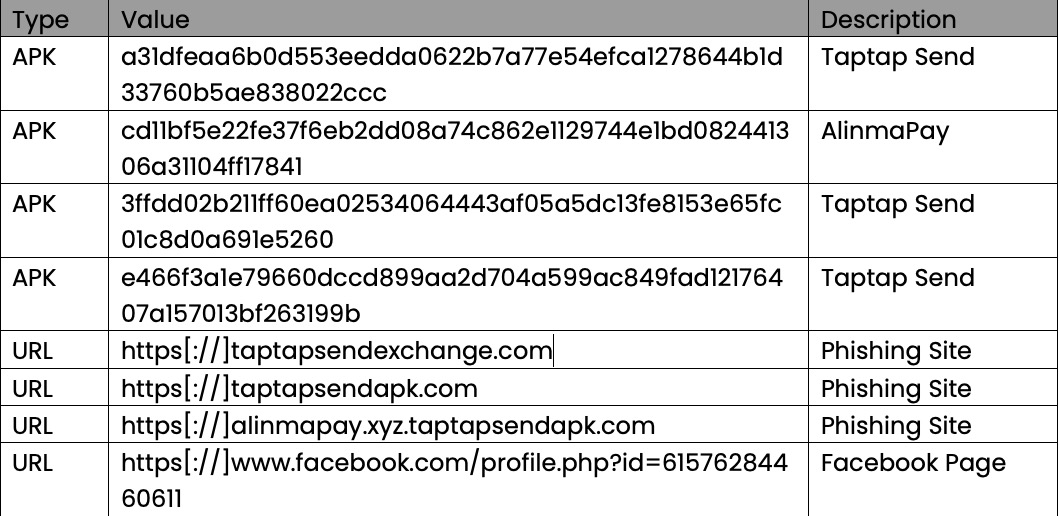
Indicators of Compromise (IOCs)