
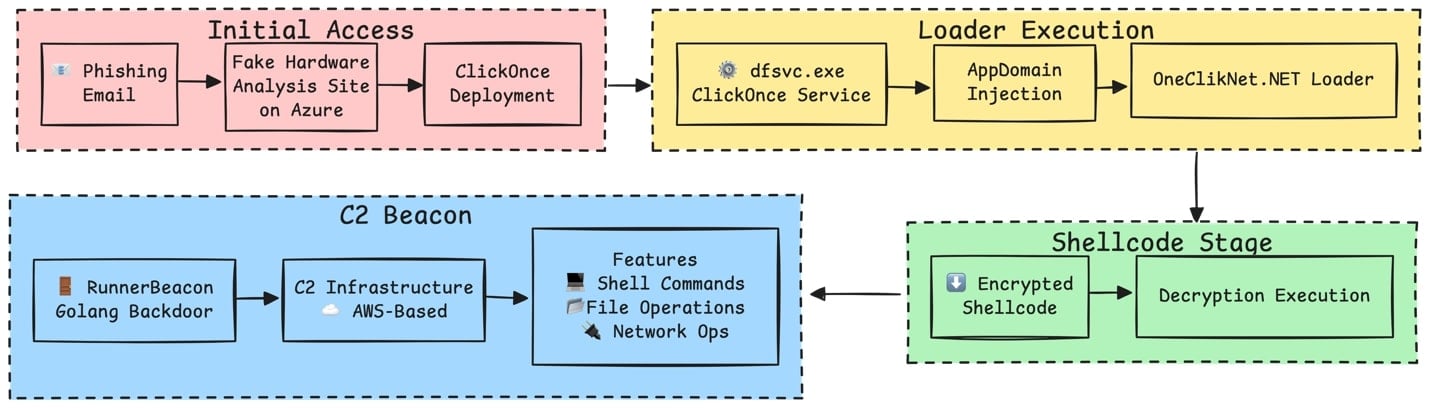
A classy malicious marketing campaign that researchers name OneClik has been leveraging Microsoft’s ClickOnce software program deployment software and customized Golang backdoors to compromise organizations inside the vitality, oil, and gasoline sectors.
The hackers depend on authentic AWS cloud companies (AWS, Cloudfront, API Gateway, Lambda) to maintain the command and management (C2) infrastructure hidden.
ClickOnce is a deployment expertise from Microsoft that permits builders to create self-updating Home windows-based purposes, decreasing person interplay to a minimal.
Safety researchers at cybersecurity firm Trellix analyzed three variants of the marketing campaign (v1a, BPI-MDM, and v1d), all of them deploying “a classy Golanguage backdoor” known as RunnerBeacon through a .NET-based loader tracked as OneClikNet.
In response to them, every model of the OneClik marketing campaign advanced with superior techniques and C2 obfuscation, sturdy anti-analysis, and sandbox evasion methods.
Whereas operational indicators level to China-affiliated menace actors, the researchers are cautious in making an attribution.
Abusing Microsoft’s ClickOnce deployment software
OneClik assaults mix authentic instruments with customized malware and cloud and enterprise tooling, which permits the menace actor to evade detection of the operation.
It begins with a phishing e-mail with a hyperlink to a faux {hardware} evaluation website hosted within the Azure ecosystem that delivers a .APPLICATION file (ClickOnce manifest) disguised as a authentic software.
Trellix researchers say that the attacker used ClickOnce apps as a supply mechanism for malicious payloads with out triggering the person account management mechanism.
“ClickOnce apps launch beneath the Deployment Service (dfsvc.exe), enabling attackers to proxy execution of malicious payloads via this trusted host.
As a result of ClickOnce purposes run with user-level privileges (no person account management required), they provide an interesting supply mechanism for menace actors aiming to keep away from privilege escalation,” the researchers clarify.
supply: Trellix
After execution, the ClickOnce loader runs malicious payloads by hijacking how the .NET software masses assemblies, a way known as AppDomainManager injection.
Within the case of OneClik, this allowed the menace actor to make use of a authentic .NET executable, corresponding to ZSATray.exe, umt.exe, or ied.exe, to load one thing else than the traditional dependencies.
“With the loader in place, payload execution proceeds beneath dfsvc.exe, mixing with benign ClickOnce actions,” Trellix researchers say.
To hide the operation for an extended interval, the menace actor leveraged authentic AWS companies, which made C2 communication seem as regular cloud utilization because it blended with innocent CDN site visitors.
Within the OneClik v1a variant, the beacon contacted a Cloudfront distribution area and an API Gateway endpoint. Within the v1d it used an AWS Lambda operate URL because the HTTP callback handle.
“By “hiding within the cloud,” attackers exploit the excessive belief and availability of AWS: defenders should decrypt SSL or denylist whole AWS domains to note this site visitors, which is commonly impractical,” Trellix researchers make clear.
Go-based RunnerBeacon backdoor
An evaluation of the Golang-based RunnerBeacon backdoor confirmed that its C2 protocol encrypted all site visitors utilizing the RC4 stream cipher algorithm and serialized knowledge utilizing MessagePack.
It includes a modular message protocol with a number of message varieties, amongst them BeaconData, FileRequest, CommandRequest, SOCKSRequest, and FileUpload.
Among the strategies the backdoor makes use of to hinder evaluation, the researchers discovered an “obfuscate_and_sleep” routine and randomized “jitter” in beacon intervals.
The researchers additionally noticed high-level instructions that enable the menace actor to:
- execute shell instructions (CreateProcessW)
- numerate processes
- run file operations (listing itemizing, add, obtain)
- perform network-related duties (port scanning)
- set up a SOCKS5 tunnel to proxy knowledge site visitors
Extra RunnerBeacon capabilities embody superior operations like course of injection and setting the stage for privilege escalation.
Trellix says that RunnerBeacon’s design is just like recognized Go-based Cobalt Strike beacons like these within the Geacon household.
Because of the similarities within the set of instructions and using cross-protocol C2, they are saying that “RunnerBeacon could also be an advanced fork or privately modified variant of Geacon, tailor-made for stealthier, and cloud-friendly operations”
Cautious attribution
Though the OneClik marketing campaign was found just lately, firstly of March, a variant of the RunnerBeacon loader was recognized in September 2023 at an organization within the Center East within the oil and gasoline sector.
The supply methodology couldn’t be decided however the variant’s code is sort of equivalent to the analyzed module from the OneClik operation.
The clues pointing to exercise associated to a China-affiliated state actor embody techniques, methods, and procedures seen in different campaigns attributed to Chinese language menace actors.
Trellix highlights that the .NET AppDomainManager injection method has been utilized in a number of cyberattacks attributed to Chinese language menace actors. The identical goes for the strategy used to deploy the encrypted payload.
Moreover, earlier China-linked campaigns present a choice for cloud-based staging utilizing companies from Alibaba and Amazon.
Nonetheless, these overlaps usually are not sufficient to attribute the OneClik assaults to a selected menace actor.
The report from Trellix features a complete record of indicators of compromise for all parts within the OneClik marketing campaign, starting from phishing lures and malware loaders to configuration information, backdoor binaries, authentic executables, domains, and configuration parameters.



