
Risk actors are abusing the ConnectWise ScreenConnect installer to construct signed distant entry malware by modifying hidden settings inside the consumer’s Authenticode signature.
ConnectWise ScreenConnect is a distant monitoring and administration (RMM) software program that enables IT admins and managed service suppliers (MSPs) to troubleshoot units remotely.
When a ScreenConnect installer is constructed, it may be personalized to incorporate the distant server the consumer ought to connect with, what textual content is proven within the dialog bins, and logos that needs to be displayed. This configuration information is saved inside the file’s authenticode signature.
This method, referred to as authenticode stuffing, permits for the insertion of information right into a certificates desk whereas retaining the digital signature intact.
ScreenConnect abused for preliminary entry
Cybersecurity agency G DATA noticed malicious ConnectWise binaries with similar hash values throughout all file sections apart from the certificates desk.
The one distinction was a modified certificates desk containing new malicious configuration info whereas nonetheless permitting the file to stay signed.
G DATA says the primary samples had been discovered within the BleepingComputer boards, the place members reported being contaminated after falling for phishing assaults. Related assaults had been reported on Reddit.
These phishing assaults utilized both PDFs or middleman Canva pages that linked to executables hosted on Cloudflare’s R2 servers (r2.dev).
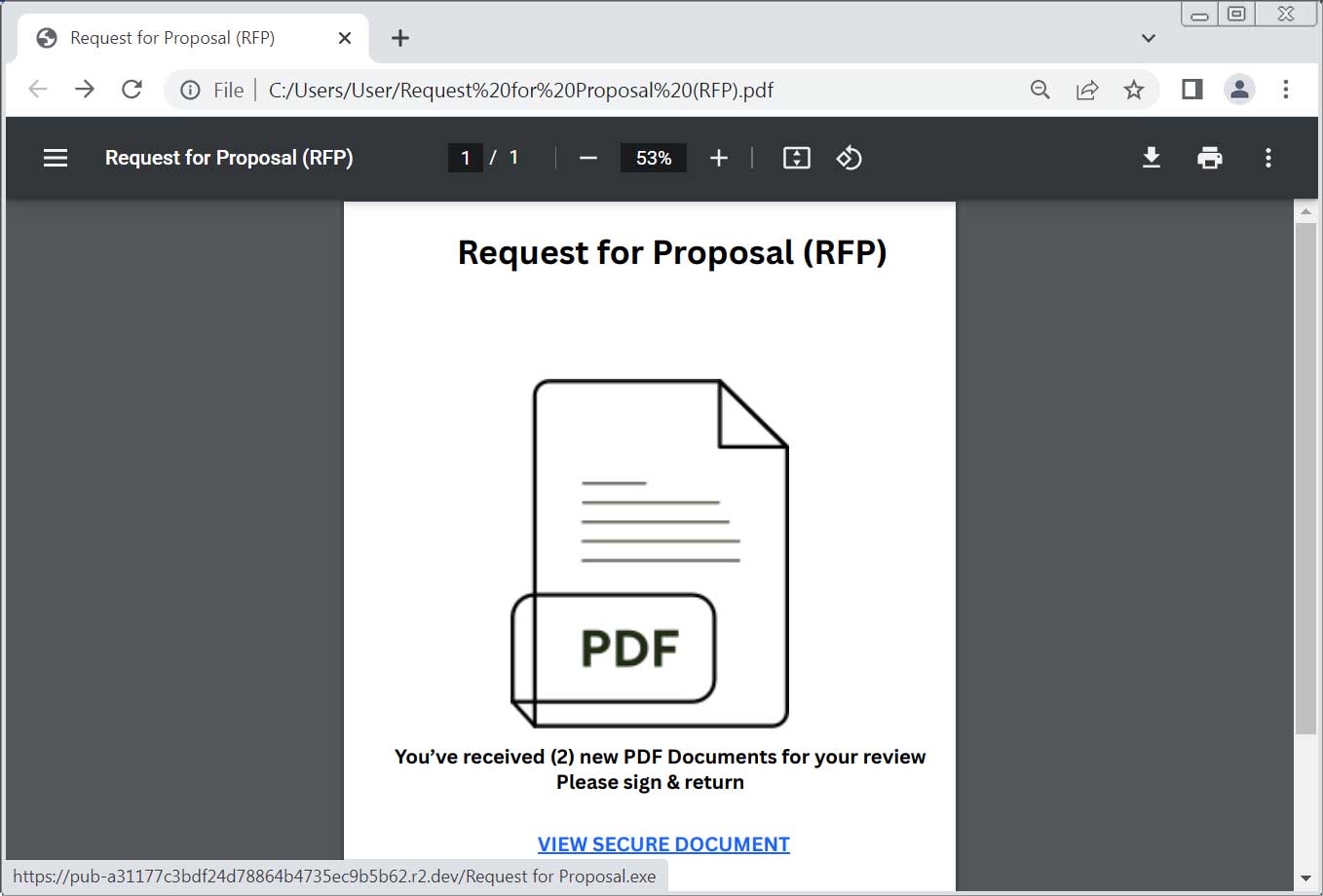
Supply: BleepingComputer
The file, referred to as “Request for Proposal.exe,” seen by BleepingComputer, is a malicious ScreenConnect consumer [VirusTotal] configured to attach to the attacker’s servers at 86.38.225[.]6:8041 (relay.rachael-and-aidan.co[.]uk)
G DATA constructed a software to extract and overview the settings present in these campaigns, the place the researchers discovered important modifications, akin to altering the installer’s title to “Home windows Replace” and changing the background with a pretend Home windows Replace picture proven beneath.
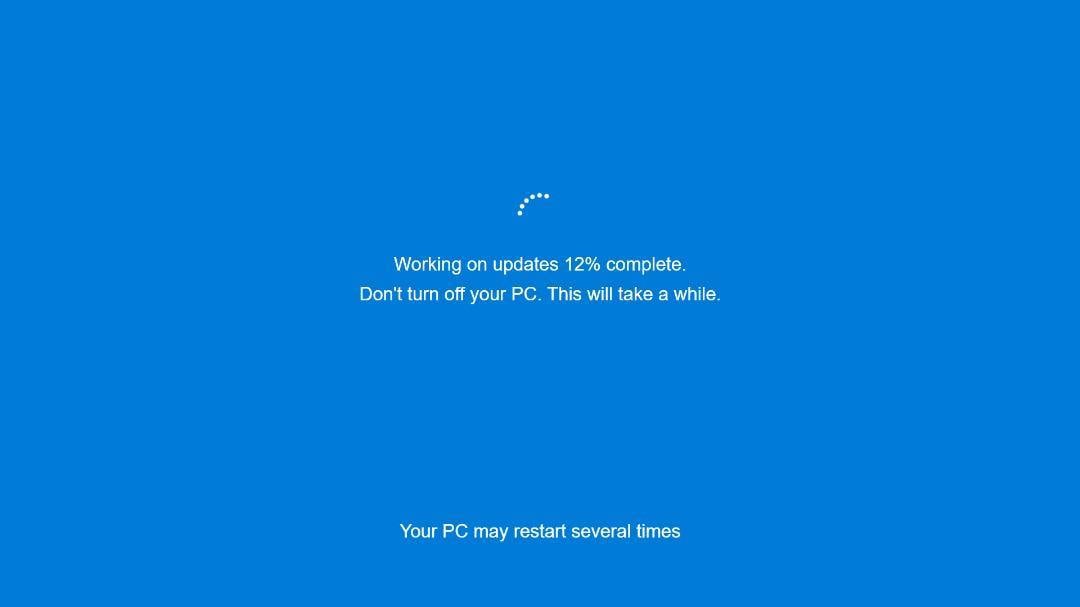
Supply: G DATA
Primarily, the risk actors transformed the official ConnectWise ScreenConnect consumer into malware that enables them to stealthily acquire entry to contaminated units.
After contacting G DATA, ConnectWise revoked the certificates utilized in these binaries, and G DATA is now flagging these samples as Win32.Backdoor.EvilConwi.* and Win32.Riskware.SilentConwi.*.
G DATA says they by no means obtained a reply from ConnectWise about this marketing campaign and their report.
One other marketing campaign can be enterprise software program, this time distributing trojanized variations of the SonicWall NetExtender VPN consumer to steal usernames, passwords, and area info.
In line with an advisory from SonicWall, these modified variations ship captured credentials to an attacker-controlled server, making it vital for customers solely to acquire software program shoppers from official websites.



