
Hackers are exploiting a essential privilege escalation vulnerability within the WordPress theme “Motors” to hijack administrator accounts and acquire full management of a focused website.
The malicious exercise was noticed by Wordfence, which had warned final month in regards to the severity of the flaw, tracked underneath CVE-2025-4322, urging customers to improve instantly.
Motors, developed by StylemixThemes, is a WordPress theme common amongst automotive-related web sites. It has 22,460 gross sales on the EnvatoMarket and is backed by an lively group of customers.
The privilege escalation vulnerability was found on Might 2, 2025, and first reported by Wordfence on Might 19, impacting all variations earlier than and together with 5.6.67.
The flaw arises from an improper consumer id validation throughout password updating, permitting unauthenticated attackers to alter administrator passwords at will.
StylemixThemes launched Motors model 5.6.68, which addresses CVE-2025-4322, on Might 14, 2025, however many customers failed to use the replace by Wordfence’s disclosure and received uncovered to elevated exploitation danger.
As Wordfence confirms in a brand new writeup, the assaults started on Might 20, solely a day after they publicly disclosed the main points. Vast-scale assaults have been noticed by June 7, 2025, with Wordfence reporting blocking 23,100 makes an attempt towards its clients.
.jpg)
Supply: Wordfence
Assault course of and indicators of breach
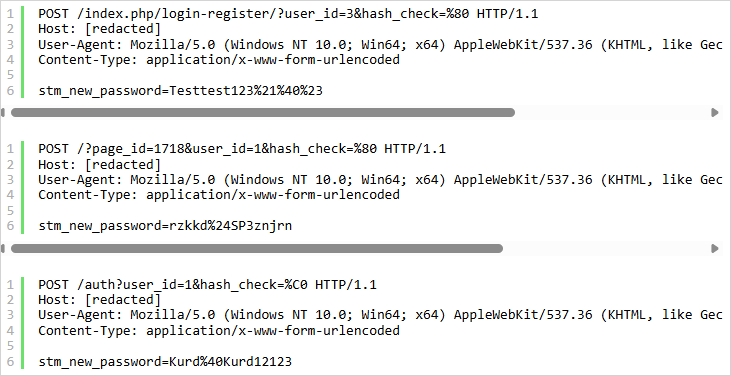
The vulnerability is within the Motors theme’s “Login Register” widget, together with password restoration performance.
The attacker first locates the URL the place this widget is positioned by probing /login-register, /account, /reset-password, /signin, and so on., with specifically crafted POST requests till they get successful.
The request comprises invalid UTF-8 characters in a malicious ‘hash_check’ worth, inflicting the hash comparability within the password reset logic to succeed incorrectly.
The POST physique comprises a ‘stm_new_password’ worth that resets the consumer password, focusing on consumer IDs that sometimes correspond to administrator customers.
Supply: Wordfence
Attacker-set passwords noticed within the assaults up to now embody:
- Testtest123!@#
- rzkkd$SP3znjrn
- Kurd@Kurd12123
- owm9cpXHAZTk
- db250WJUNEiG
As soon as entry is gained, the attackers log into the WordPress dashboard as directors and create new admin accounts for persistence.
The sudden look of such accounts mixed with current directors being locked out (passwords now not working) are indicators of CVE-2025-4322 exploitation.
Wordfence has additionally listed a number of IP addresses that launch these assaults within the report, which WordPress website homeowners are really useful to placed on their block record.
Patching used to imply advanced scripts, lengthy hours, and infinite fireplace drills. Not anymore.
On this new information, Tines breaks down how fashionable IT orgs are leveling up with automation. Patch quicker, scale back overhead, and concentrate on strategic work — no advanced scripts required.



