
Cloudflare says it mitigated a record-breaking distributed denial of service (DDoS) assault in Could 2025 that peaked at 7.3 Tbps, focusing on a internet hosting supplier.
DDoS assaults flood targets with huge quantities of visitors with the only real intention to overwhelm servers and create service slowdowns, disruptions, or outages.
This new assault, which is 12% bigger than the earlier report, delivered a large information quantity of 37.4 TB in simply 45 seconds. That is the equal of about 7,500 hours of HD streaming or 12,500,000 jpeg images.
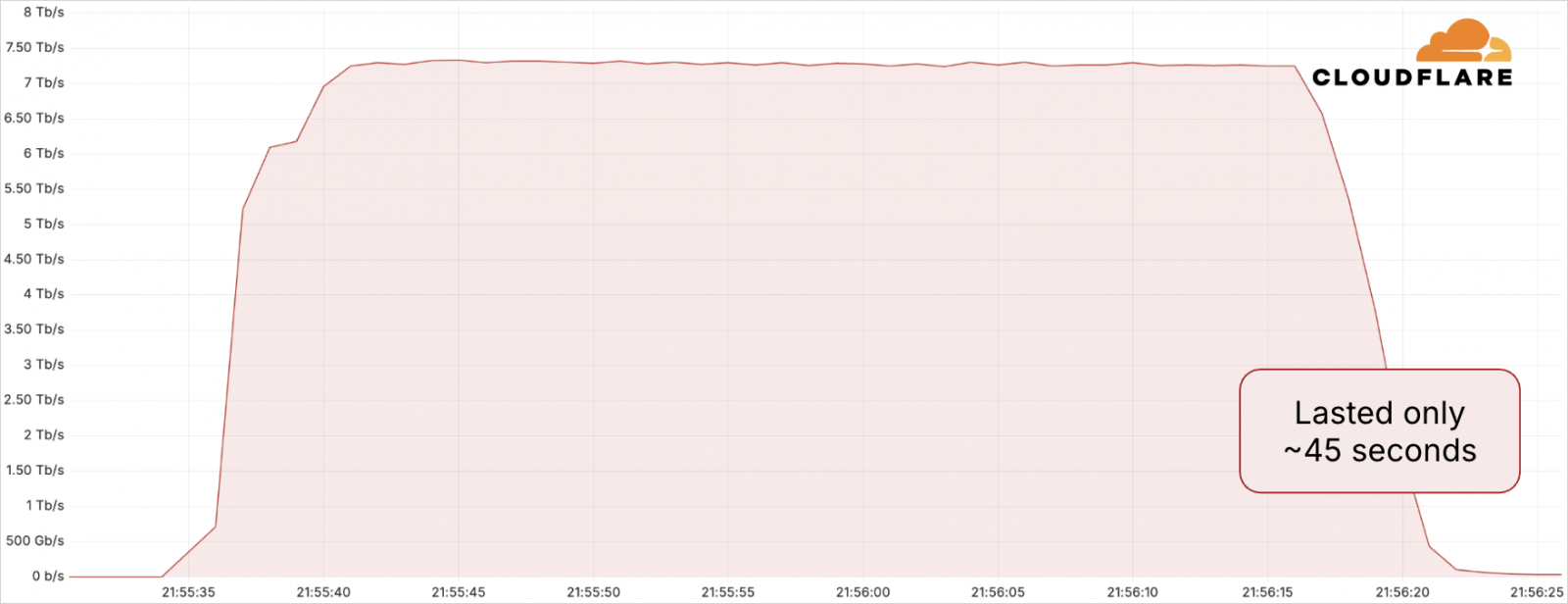
Supply: Cloudflare
Cloudflare, an online infrastructure and cybersecurity big specializing in DDoS mitigation, affords a network-layer safety service known as ‘Magic Transit,’ which was utilized by the focused buyer.
The assault got here from 122,145 supply IP addresses unfold throughout 161 nations, with the bulk based mostly in Brazil, Vietnam, Taiwan, China, Indonesia, and Ukraine.
The “rubbish” information packages have been delivered throughout a number of vacation spot ports on the sufferer’s system, averaging 21,925 ports per second and peaking at 34,517 ports/second.
This tactic of scattering visitors helps overwhelm firewall or intrusion detection programs, however Cloudflare claims to have in the end been in a position to mitigate the assault with out human intervention.
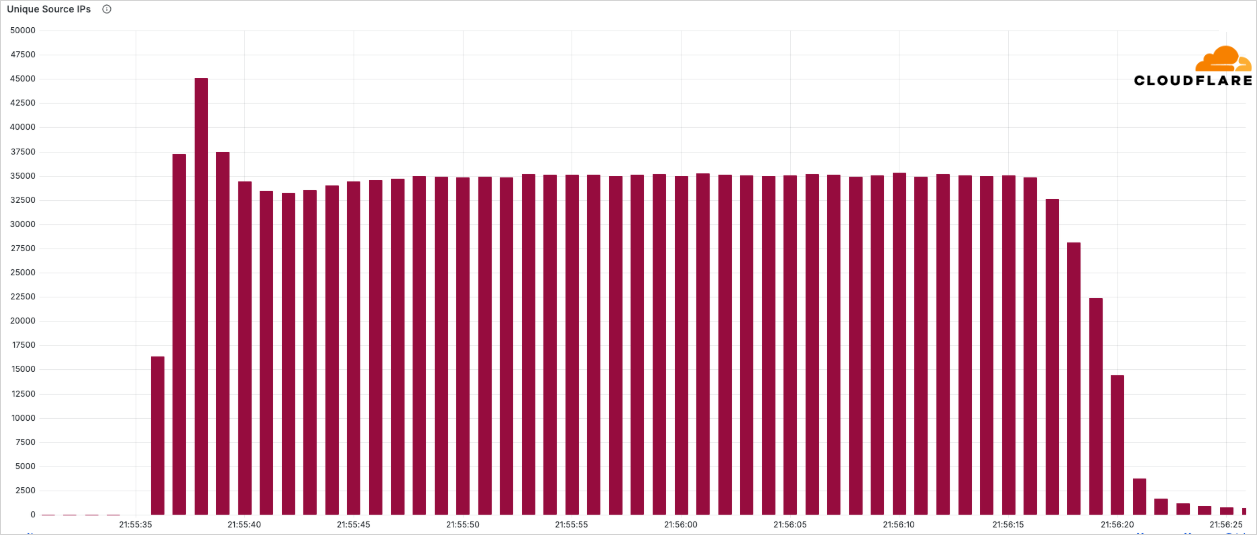
Supply: Cloudflare
Cloudflare’s anycast community dispersed assault visitors to 477 information facilities in 293 places, leveraging key applied sciences corresponding to real-time fingerprinting and intra-data middle gossiping for real-time intelligence sharing and automatic rule compilation.
Although practically the whole assault quantity got here from UDP floods, accounting for 99.996% of the entire visitors, there have been a number of different vectors concerned, together with:
- QOTD reflection
- Echo reflection
- NTP amplification
- Mirai botnet UDP flood
- Portmap flood
- RIPv1 amplification
Every vector exploited legacy or poorly configured companies. Whereas this was solely a tiny share of the assault, it served as a part of the attackers’ evasion and effectiveness technique and will additionally assist probe for weaknesses and misconfigurations.
Cloudflare says helpful IoCs from this assault have been well timed included in its DDoS Botnet Menace Feed, a free service that helps organizations block malicious IP addresses preemptively.
Over 600 organizations have subscribed to this feed, and the web big calls any others liable to huge DDoS assaults to do the identical and block the assaults earlier than they attain their infrastructure.
Patching used to imply complicated scripts, lengthy hours, and limitless fireplace drills. Not anymore.
On this new information, Tines breaks down how fashionable IT orgs are leveling up with automation. Patch quicker, cut back overhead, and deal with strategic work — no complicated scripts required.



