
The Russian state-backed hacking group Gamaredon (aka “Shuckworm”) has been concentrating on a navy mission of a Western nation in Ukraine in assaults probably deployed from detachable drives.
Symantec risk researchers say the marketing campaign began in February 2025 and continued till March, with hackers deploying an up to date model of the GammaSteel info-stealing malware to exfiltrate information.
In accordance with the report, preliminary entry to the contaminated methods was in all probability achieved through detachable drives containing malicious .LNK recordsdata, a vector that Gamaredon has used up to now.
The researchers be aware a change within the risk actor’s techniques, together with a shift from VBS scripts to PowerShell-based instruments, extra obfuscation for payloads, and elevated use of official providers for evasion.
Newest Gamaredon assaults in Ukraine
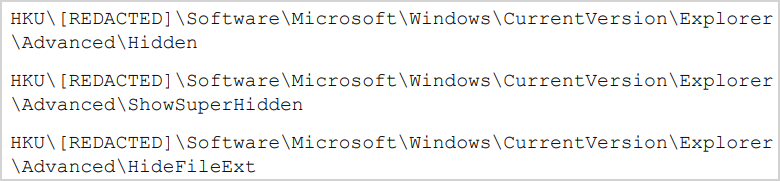
Through the investigation, the researchers seen within the Home windows Registry of the compromised system a brand new worth below the UserAssist key, indicating that the an infection began from an exterior drive from a shortcut file named recordsdata.lnk.
Subsequent, a closely obfuscated script creates and runs two recordsdata. The primary handles command and management (C2) communications, resolving the server tackle utilizing official providers, and connecting to Cloudflare-protected URLs.
The second file handles the spreading mechanism to contaminate different detachable and community drives utilizing LNK recordsdata, whereas additionally hiding sure folders and system recordsdata to cover the compromise.
Supply: Symantec
Subsequent, Gamaredon used a reconnaissance PowerShell script that may seize and exfiltrate screenshots of the contaminated system and collect details about put in antivirus instruments, recordsdata, and working processes.
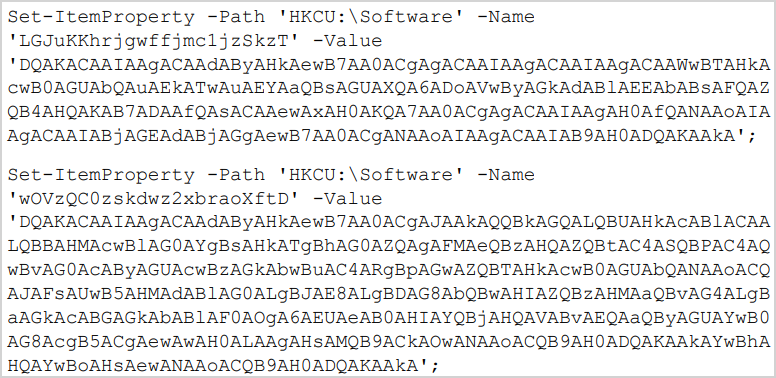
The ultimate payload used within the noticed assaults is a PowerShell-based model of GammaSteel that’s saved in Home windows Registry.
Supply: Symantec
The malware can steal paperwork (.DOC, .PDF, .XLS, .TXT) from numerous places like Desktop, Paperwork, and Downloads, confirming Gamaredon’s persevering with curiosity in espionage.
Finally, the malware makes use of ‘certutil.exe’ to hash the recordsdata and exfiltrates them utilizing PowerShell internet requests. If the exfiltration fails, Gamaredon makes use of cURL over Tor to switch the stolen information.
Lastly, a brand new secret is added to ‘HKCUSoftwareMicrosoftWindowsCurrentVersionRun’ to ascertain persistence on the goal pc.
The latest Gamaredon marketing campaign displays an effort to extend operational stealth and effectiveness regardless of the risk group’s restricted sophistication in comparison with different Russian state actors.
Symantec feedback that numerous incremental however significant enhancements within the risk group’s TTPs (techniques, methods, and procedures) elevate the dangers it poses to Western networks, particularly contemplating Gamaredon’s unwavering tenacity.



