A menace actor has re-released information from a 2021 AT&T breach affecting 70 million clients, this time combining beforehand separate recordsdata to straight hyperlink Social Safety numbers and delivery dates to particular person customers.
AT&T advised BleepingComputer that they’re investigating the info but additionally imagine it originates from the identified breach and was repackaged into a brand new leak.
“It’s not unusual for cybercriminals to repackage beforehand disclosed information for monetary achieve. We simply realized about claims that AT&T information is being made accessible on the market on darkish internet boards, and we’re conducting a full investigation,” AT&T advised BleepingComputer.
As first noticed by HackRead, the AT&T information was launched on a well-liked Russian-speaking hacking discussion board, the place a menace actor claimed it was stolen in the course of the 2024 AT&T Snowflake information theft assault, which uncovered the decision logs of 109 million clients.
“Initially one of many database from the snowflake breach right here is my backup I created which has bogus numbers resembling 00000 (I believe federal brokers…?) eliminated and I’ve additionally decrypted the SSNs and DOBs,” reads the discussion board put up.
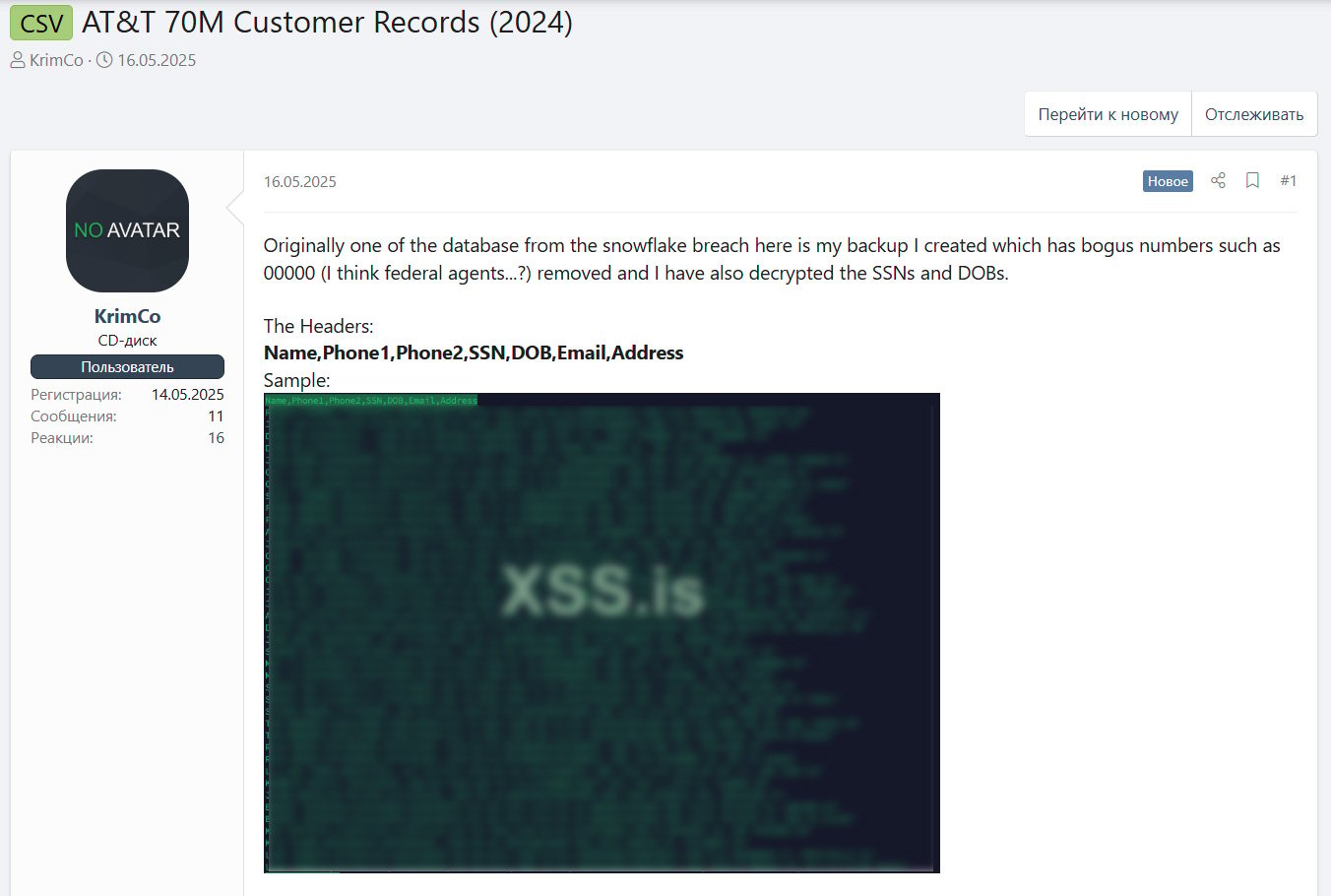
Supply: BleepingComputer
Nevertheless, BleepingComputer’s evaluation of the leak signifies that the info really originates from an AT&T information breach in 2021 carried out by a widely known menace actor named ShinyHunters, who tried to promote it for $200,000.
Three years later, in March 2024, one other menace actor leaked the whole AT&T information on a cybercrime discussion board without cost, stating it was from ShinyHunter’s 2021 AT&T breach.
This information included names, addresses, cell phone numbers, encrypted date of delivery, encrypted social safety numbers, and different inside info. Nevertheless, included within the leak had been particular person recordsdata that mapped the encrypted SSNs and DOBs with their unencrypted plain textual content strings.
On the time, AT&T first denied that the info was theirs however finally confirmed that the info was stolen from their programs and impacted 73 million clients.
Evaluation of the present leak by BleepingComputer exhibits it is the identical information leaked in 2024 however cleaned as much as take away inside AT&T information and add the unencrypted Social Safety quantity and date of delivery to every buyer report.
In whole, there are 88,320,017 strains of information within the leak, however while you take away duplicates, it goes all the way down to 86,017,088 distinctive information.
Additional processing of the info exhibits that it accommodates 48,896,044 distinctive telephone numbers with related buyer info.
This important drop is brought on by many purchasers having a number of information with the identical telephone quantity used at totally different addresses.
To reiterate, this isn’t a brand new AT&T leak or the stolen Snowflake information however fairly a repackaged model of the 2021 information breach.
Guide patching is outdated. It is gradual, error-prone, and difficult to scale.
Be part of Kandji + Tines on June 4 to see why previous strategies fall quick. See real-world examples of how trendy groups use automation to patch quicker, lower threat, keep compliant, and skip the complicated scripts.



