Take into account a safety operations heart (SOC) that displays community and endpoint knowledge in actual time to determine threats to their enterprise. Relying on the scale of its group, the SOC could obtain about 200,000 alerts per day. Solely a small portion of those alerts can obtain human consideration as a result of every investigated alert could require 15-to-20 minutes of analyst consideration to reply a essential query for the enterprise: Is that this a benign occasion, or is my group beneath assault? It is a problem for almost all organizations, since even small enterprises generate way more community, endpoint, and log occasions than people can successfully monitor. SOCs subsequently should make use of safety monitoring software program to pre-screen and downsample the variety of logged occasions requiring human investigation.
Machine studying (ML) for cybersecurity has been researched extensively as a result of SOC actions are knowledge wealthy, and ML is now more and more deployed into safety software program. ML shouldn’t be but broadly trusted in SOCs, and a significant barrier is that ML strategies endure from a lack of explainability. With out explanations, it’s affordable for SOC analysts to not belief the ML.
Exterior of cybersecurity, there are broad normal calls for for ML explainability. The European Basic Knowledge Safety Regulation (Article 22 and Recital 71) encodes into legislation the “proper to a proof” when ML is utilized in a approach that considerably impacts a person. The SOC analyst additionally has a necessity for explanations as a result of the choices they have to make, typically beneath time strain and with ambiguous data, can have important impacts on their group.
We suggest cyber-informed machine studying as a conceptual framework for emphasizing three sorts of explainability when ML is used for cybersecurity:
- data-to-human
- model-to-human
- human-to-model
On this weblog put up, we offer an outline of every kind of explainability, and we advocate analysis wanted to attain the extent of explainability essential to encourage use of ML-based programs supposed to help cybersecurity operations.
Knowledge-to-Human Explainability
Knowledge-to-human explainability seeks to reply: What’s my knowledge telling me? It’s the most mature type of explainability, and it’s a main motivation of statistics, knowledge science, and associated fields. Within the SOC, a fundamental use case is to grasp the traditional community visitors profile, and a extra particular use case is perhaps to grasp the historical past of a selected inside web protocol (IP) tackle interacting with a selected exterior IP tackle.
Whereas the sort of explainability could seem easy, there are a number of cybersecurity-specific challenges. For instance, contemplate the NetFlow fields recognized in Desk 1.
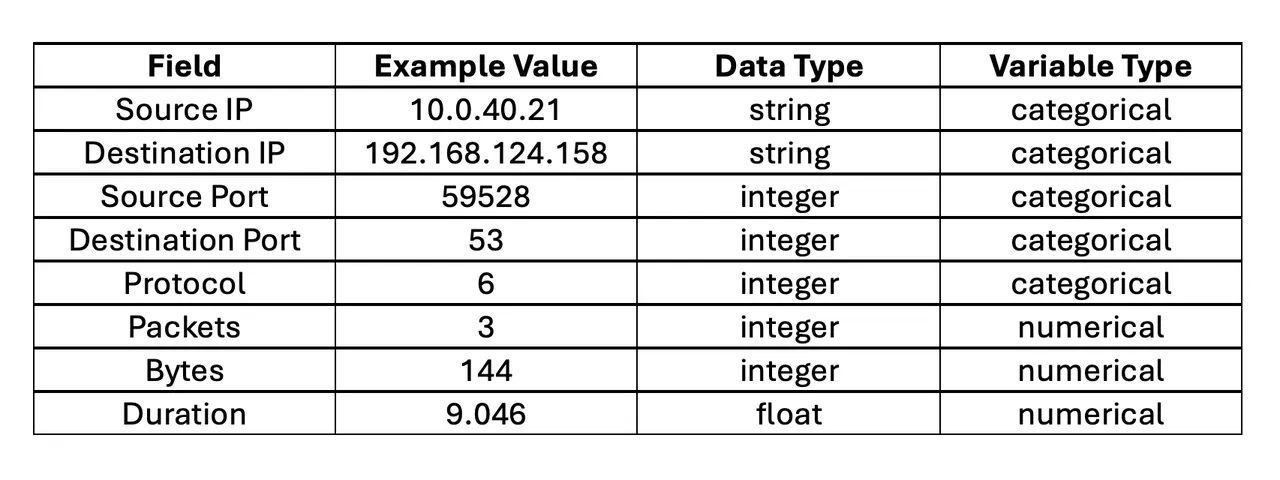
Desk 1: NetFlow instance fields
ML strategies can readily be utilized to the numerical fields: packets, bytes, and length. Nonetheless, supply IP and vacation spot IP are strings, and within the context of ML they’re categorical variables. A variable is categorical if its vary of doable values is a set of ranges (classes). Whereas supply port, vacation spot port, protocol, and kind are represented as integers, they’re really categorical variables. Moreover, they’re non-ordinal as a result of their ranges haven’t any sense of order or scale (e.g., port 59528 shouldn’t be in some way subsequent to or bigger than port 53).
Take into account the info factors in Determine 1 to grasp why the excellence between numerical and categorical variables is essential. The underlying operate that generated the info is clearly linear. We will subsequently match a linear mannequin and use it to foretell future factors. Enter variables which might be non-ordinal categorical (e.g., IP tackle, ports, and protocols) problem ML as a result of there is no such thing as a sense of order or scale to leverage. These challenges typically restrict us to fundamental statistics and threshold alerts in SOC purposes.
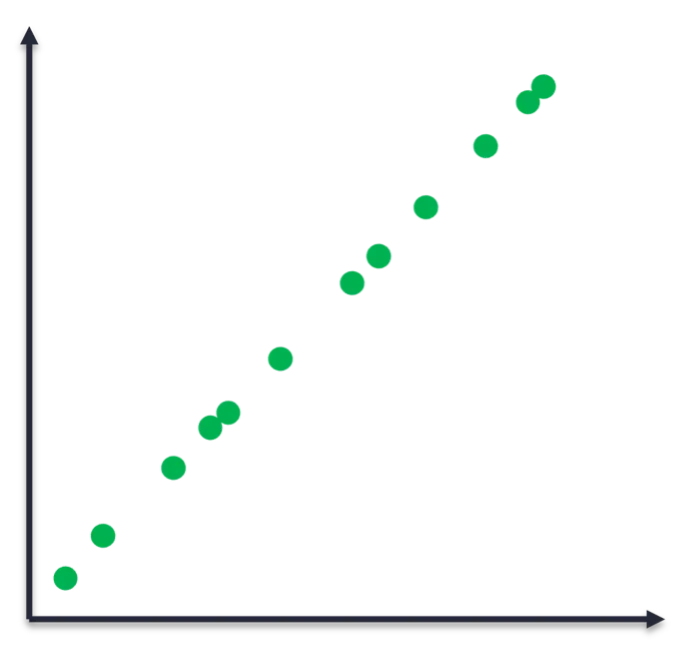
Determine 1: Empirically noticed knowledge factors that had been generated by an underlying linear operate
A associated problem is that cyber knowledge typically have a weak notation of distance. For instance, how would we quantify the space between the 2 NetFlow logs in Desk 2? For the numerical variable stream length, the space between the 2 logs is nineteen.417 – 7.639, or 11.787 milliseconds. Nonetheless, there is no such thing as a related notion of distance between the 2 ephemeral ports, in addition to the opposite categorical variables.
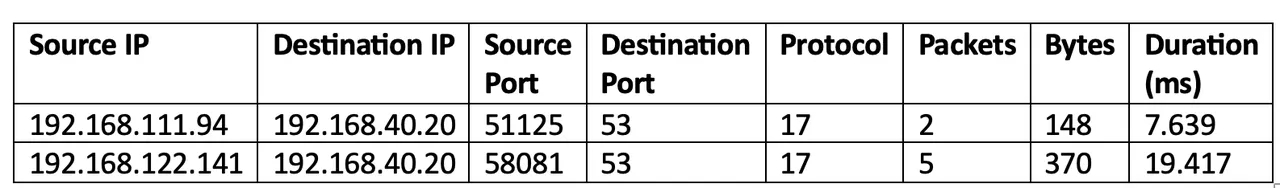
Desk 2: An instance of two NetFlow logs
There are some methods for quantifying similarity between logs with categorical variables. For instance, we may depend the variety of equivalently-valued fields between the 2 logs. Logs that share extra discipline values in widespread are in some sense extra related. Now that we’ve some quantitative measure of distance, we are able to attempt unsupervised clustering to find pure clusters of logs throughout the knowledge. We would hope that these clusters can be cyber-meaningful, akin to grouping by the appliance that generated every log, as Determine 2 depicts. Nonetheless, such cyber-meaningful groupings don’t happen in observe with out some cajoling, and that cajoling is an instance of cyber-informed machine studying: imparting our human cyber experience into the ML pipeline.
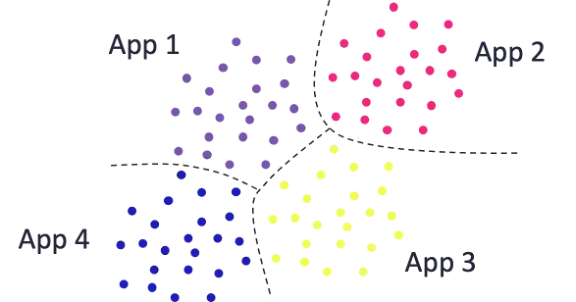
Determine 2: Optimistic illustration of clustering NetFlow logs
Determine 3 illustrates how we would impart human information right into a ML pipeline. As an alternative of naively clustering all of the logs with none preprocessing, knowledge scientists can elicit from cyber analysts the relationships they already know to exist within the knowledge, in addition to the sorts of clusters they wish to perceive higher. For instance, port, stream course, and packet volumetrics is perhaps of curiosity. In that case we would pre-partition the logs by these fields, after which carry out clustering on the ensuing bins to grasp their composition.
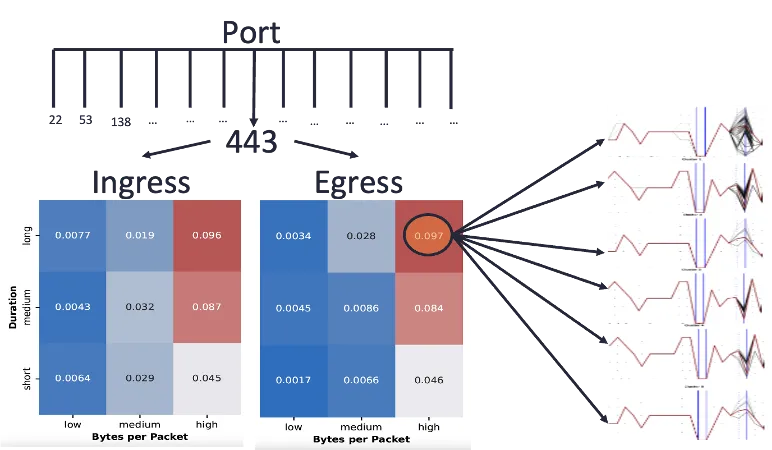
Determine 3: Illustration of cyber-informed clustering
Whereas data-to-human is essentially the most mature kind of explainability, we’ve mentioned among the challenges that cyber knowledge current. Exacerbating these challenges is the massive quantity of knowledge that cyber processes generate. It’s subsequently essential for knowledge scientists to interact cyber analysts and discover methods to impart their experience into the evaluation pipelines.
Mannequin-to-Human Explainability
Mannequin-to-human explainability seeks to reply: What’s my mannequin telling me and why? A typical SOC use case is knowing why an anomaly detector alerted to a selected occasion. To keep away from worsening the alert burden already dealing with SOC analysts, it’s essential that ML programs deployed within the SOC embody model-to-human explainability.
Demand for model-to-human explainability is growing as extra organizations deploy ML into manufacturing environments. The European Basic Knowledge Safety Regulation, the Nationwide Synthetic Intelligence Engineering initiative, and a broadly cited article in Nature Machine Intelligence all emphasize the significance of model-to-human explainability.
ML fashions could be categorised as white field or black field, relying on how readily their parameters could be inspected and interpreted. White field fashions could be totally interpretable, and the idea for his or her predictions could be understood exactly. Notice that even white field fashions can lack interpretability, particularly after they turn into very giant. White field fashions embody linear regression, logistic regression, determination tree, and neighbor-based strategies (e.g., okay-nearest neighbor). Black field fashions will not be interpretable, and the idea for his or her predictions should be inferred not directly by strategies like inspecting world and native characteristic significance. Black field fashions embody neural networks, ensemble strategies (e.g., random forest, isolation forest, XGBOOST), and kernel-based strategies (e.g., help vector machine).
In our earlier weblog put up, we mentioned the choice tree for example of a white field predictive mannequin admitting a excessive diploma of model-to-human explainability; each prediction is totally interpretable. After a call tree is educated, its guidelines could be applied instantly into software program options with out having to make use of the ML mannequin object. These guidelines could be introduced visually within the type of a tree (Determine 4, left panel), easing communication to non-technical stakeholders. Inspecting the tree supplies fast and intuitive insights into what options the mannequin estimates to be most predictive of the response.
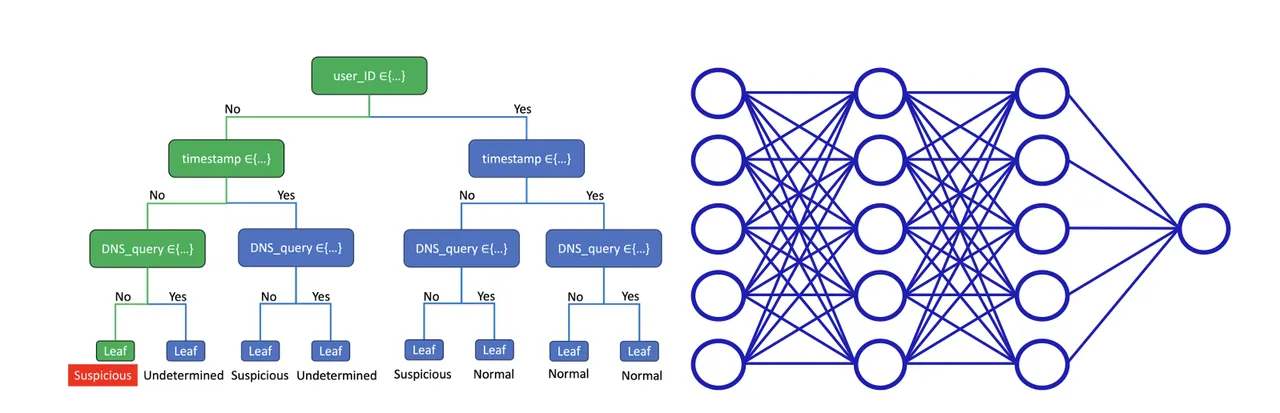
Determine 4: White field determination tree (left) and a black field neural community (proper)
Though complicated fashions like neural networks (Determine 4, proper panel) can extra precisely mannequin complicated programs, this isn’t at all times the case. For instance, a survey by Xin et al. compares the efficiency of varied mannequin types, developed by many researchers, throughout many benchmark cybersecurity datasets. This survey reveals that straightforward fashions like determination timber typically carry out equally to complicated fashions like neural networks. A tradeoff happens when complicated fashions outperform extra interpretable fashions: improved efficiency comes on the expense of diminished explainability. Nonetheless, the survey by Xin et al. additionally reveals that the improved efficiency is commonly incremental, and in these circumstances we predict that system architects ought to favor the interpretable mannequin for the sake of model-to-human explainability.
Human-to-Mannequin Explainability
Human-to-model explainability seeks to allow finish customers to affect an present educated mannequin. Take into account an SOC analyst wanting to inform the anomaly detection mannequin to not alert to a selected log kind anymore as a result of it’s benign. As a result of the tip person is seldom a knowledge scientist, a key a part of human-to-model explainability is integrating changes right into a predictive mannequin primarily based on judgments made by SOC analysts. That is the least mature type of explainability and requires new analysis.
A easy instance is the encoding step of an ML pipeline. Recall that ML requires numerical options, however cyber knowledge embody many categorical options. Encoding is a way that transforms categorical into numerical options, and there are lots of generic encoding methods. For instance, integer encoding may assign every IP tackle to an arbitrary integer. This may be naïve, and a greater method can be to work with the SOC analyst to develop cyber-meaningful encoding methods. For instance, we would group IP addresses into inside and exterior, by geographic area, or by utilizing risk intelligence. By doing this, we impart cyber experience into the info science pipeline, and that is an instance of human-to-model explainability.
We take inspiration from a profitable motion known as physics-informed machine studying [Karniadakis et al. and Hao et al.], which is enabling ML for use in some engineering design purposes. In physics, we’ve governing equations that describe pure legal guidelines just like the conservation of mass and the conservation of power. Governing equations are encoded into fashions used for engineering evaluation. If we had been to train these fashions over a big design house, we may use the ensuing knowledge (inputs mapped to outputs) to coach ML fashions. That is one instance of how our human experience in physics could be imparted into ML fashions.
In cybersecurity, we do not need steady mathematical fashions of system and person conduct, however we do have sources of cyber experience. We have now human cyber analysts with information, reasoning, and instinct constructed on expertise. We even have cyber analytics, that are encoded types of our human experience. Just like the physics neighborhood, cybersecurity wants strategies that allow our wealthy human experience to affect ML fashions that we use.
Suggestions for Cybersecurity Organizations Utilizing ML
We conclude with just a few sensible suggestions for cybersecurity organizations utilizing ML. Knowledge-to-human explainability strategies are comparatively mature. Organizations searching for to be taught extra from their knowledge can transition strategies from present analysis and off-the-shelf instruments into observe.
Mannequin-to-human explainability could be tremendously improved by assigning, at the very least within the early phases of adoption, a knowledge scientist to help the ML finish customers as questions come up. Creating cybersecurity knowledge residents internally can also be useful, and there are ample skilled improvement alternatives to assist cyber professionals purchase these abilities. Lastly, finish customers can inquire with their safety software program distributors as as to whether their ML instruments embody varied sorts of explainability. ML fashions ought to at the very least report characteristic significance—indicating which options of inputs are most influential to the mannequin’s predictions.
Whereas analysis is required to additional develop human-to-model explainability strategies in cybersecurity, there are just a few steps that may be taken now. Finish customers can inquire with their safety software program distributors as as to whether their ML instruments could be calibrated with human suggestions. SOCs may additionally contemplate gathering benign alerts dispositioned by guide investigation right into a structured database for future mannequin calibration. Lastly, the act of retraining a mannequin is a type of calibration, and evaluating when and the way SOC fashions are retrained is usually a step towards influencing their efficiency.


