
The Bumblebee malware web optimization poisoning marketing campaign uncovered earlier this week aimpersonating RVTools is utilizing extra typosquatting domainsi mimicking different in style open-source initiatives to contaminate units utilized by IT workers.
BleepingComputer was capable of finding two instances leveraging the notoriety of Zenmap, the GUI for the Nmap community scanning device, and the WinMTR tracerout utility.
Each of those instruments are generally utilized by IT workers to diagnose or analyze community visitors, requiring administrative privileges for a few of the options to work This makes customers of those instruments prime targets for menace actors trying to breach company networks and unfold laterally to different units.
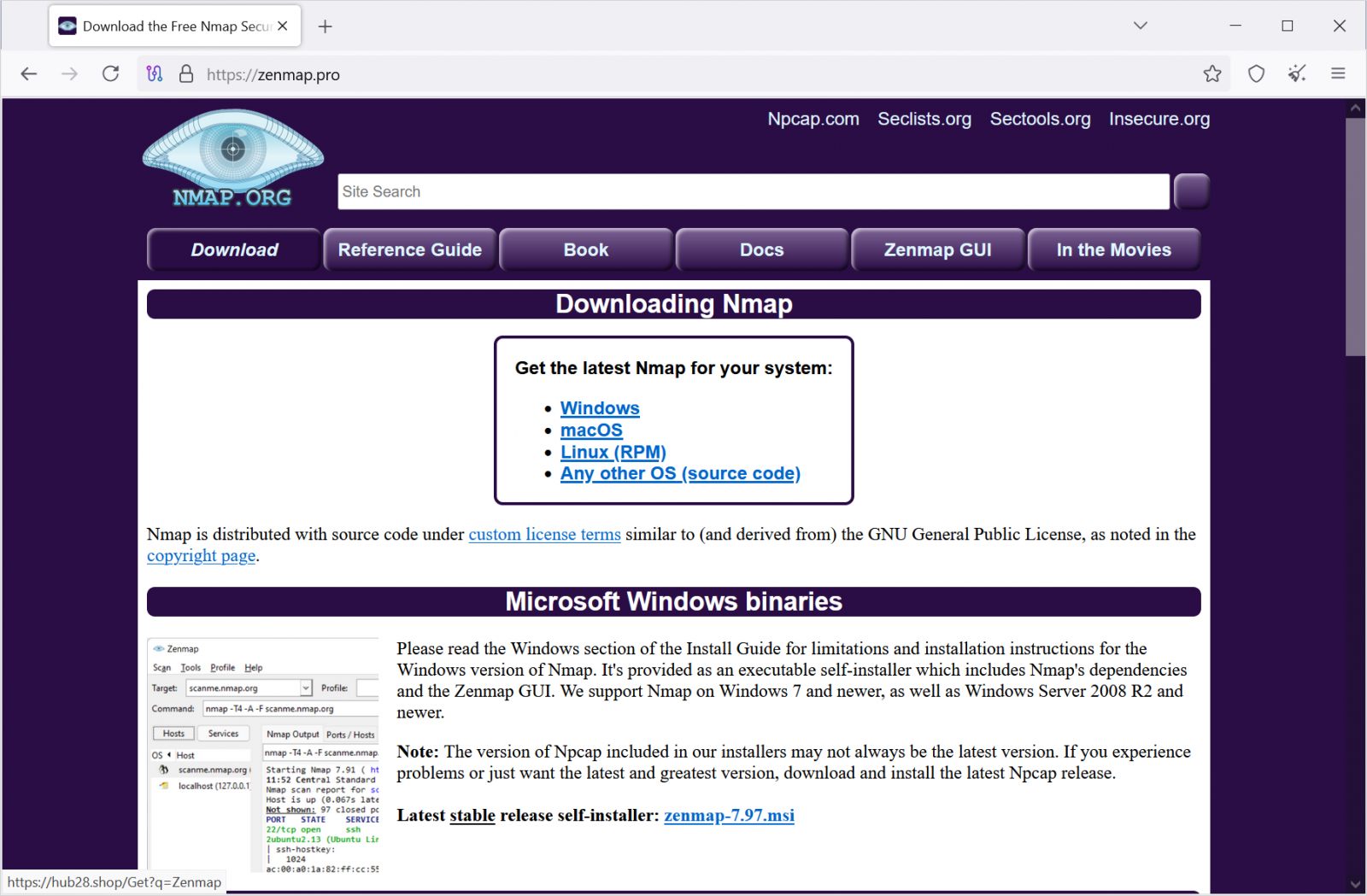
The Bumblebee malware loader has been pushed via at the least two domains – zenmap[.]professional and winmtr[.]org. Whereas the latter is at the moment offline, the previous remains to be on-line and reveals a faux weblog web page about Zenmap when visited immediately.
When customers are redirected to zenmap[.]professional from from search outcomes, although, it reveals a clone of the authentic web site for the nmap (Community Mapper) utility:
Supply: BleepingComputer
The 2 websites obtained visitors via web optimization poisoning and rank excessive in Google and Bing search outcomes for the related phrases.
.jpg)
Supply: BleepingComputer
Bleepingcolputer’s assessments present that in case you go to the faux Zenmap website immediately, it reveals a number of AI-generated articles as a substitute, as seen within the picture beneath:
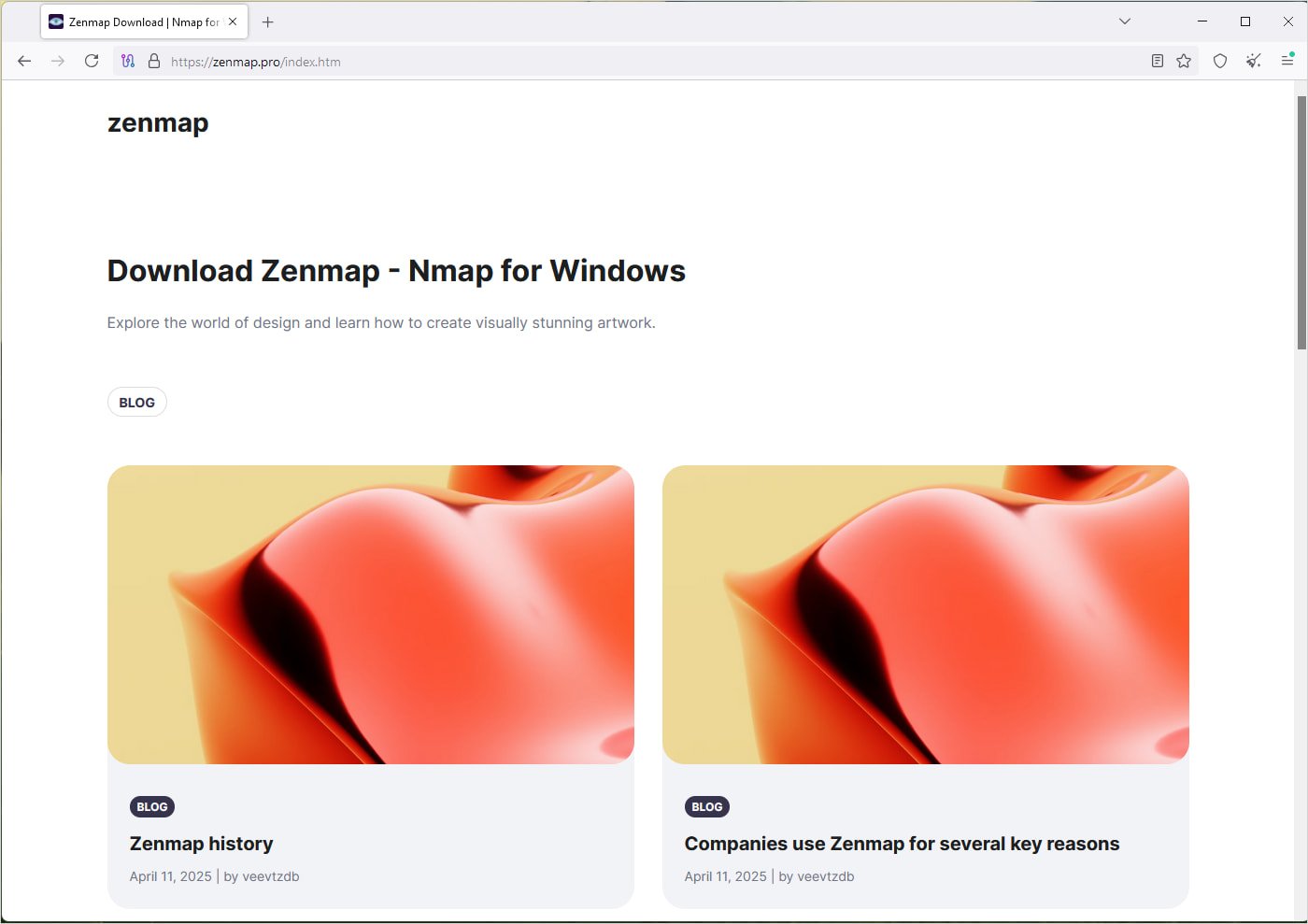
Supply: BleepingComputer
The payloads delivered via the obtain part ‘zenmap-7.97.msi’ and ‘WinMTR.msi, they usually each evade detection from most antivirus engines on VirusTotal [1, 2].
The installers ship the promised software together with a malicious DLL, as within the case of RVTools, which drops a Bumblebee loader on customers’ units.
From there, the backdoor can be utilized to profile the sufferer and introduce further payloads, which can embody infostealers, ransomware, and different forms of malware.
Aside from the open-source instruments talked about above, BleepingComputer has additionally seen the identical marketing campaign concentrating on customers in search of Hanwha safety digital camera administration software program WisenetViewer.
Cyjax’s researcher Joe Wrieden additionally noticed a trojanized model of the video administration software program Milestone XProtect being a part of the identical marketing campaign, the malicious installers being delivered ‘milestonesys[.]org’ (on-line).
Official RVTools nonetheless offline
Each official RVTools domains – Robware.internet and RVTools.com – are at the moment exhibiting a warning for customers to not obtain the software program from unofficial websites however do not make accessible the obtain hyperlink themselves.
Following allegations that the official RVTools website pushed a malware-laced installer, Dell Applied sciences denied the accusation saying that its websites didn’t distribute a trojanized variant of the product.
Dell acknowledged that the official RVTools websites had been taken offline as a result of they had been being the targets of distributed denial-of-service (DDoS) assaults.
One rationalization for the assaults can be that the menace actor behind Bumblebee determined to take down the official obtain portals to drive to the malicious websites customers trying to find different sources for the device.
To mitigate the chance of putting in trojanized variations of authentic software program, the most effective advice is to ensure to get it from official sources and bundle managers.
It’s also price checking the downloaded installer’s hash with a recognized, clear model earlier than operating it.



