
The VanHelsing ransomware-as-a-service operation printed the supply code for its affiliate panel, information leak weblog, and Home windows encryptor builder after an outdated developer tried to promote it on the RAMP cybercrime discussion board.
VanHelsing is a RaaS operation launched in March 2025, selling the power to focus on Home windows, Linux, BSD, ARM, and ESXi programs.
Since then, the operation has proven some success, with Ransomware.reside stating that there are eight recognized victims for the ransomware gang.
VanHelsing supply code leaked on cybercrime discussion board
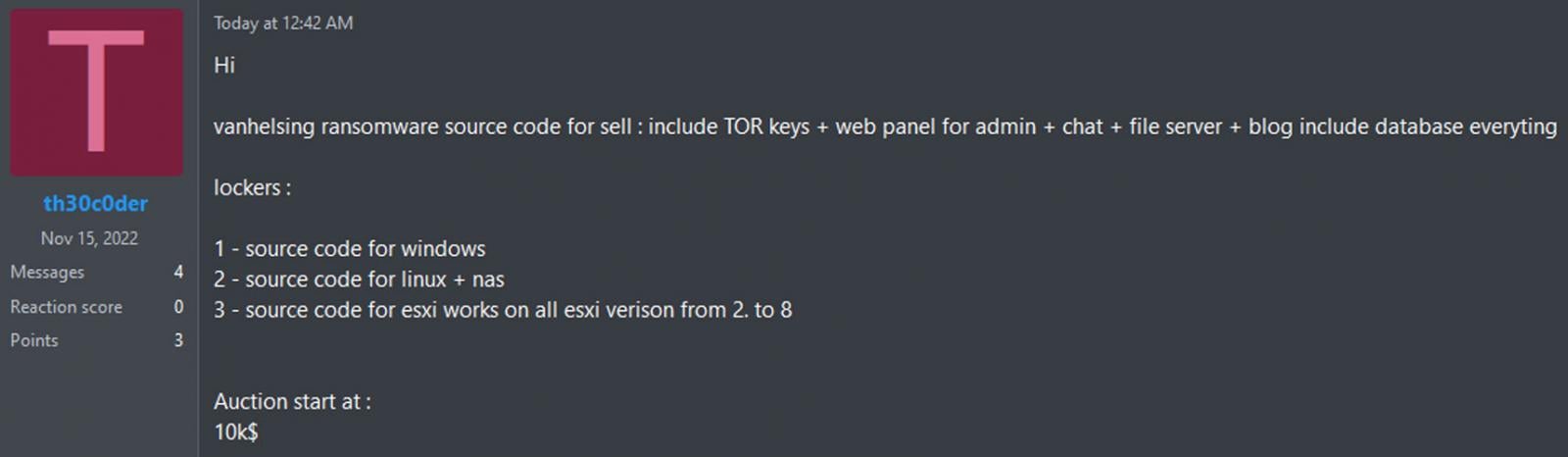
Early this morning, an individual utilizing the alias ‘th30c0der’ tried to promote the supply code for the VanHelsing affiliate panel and information leak Tor websites, in addition to the builders for the Home windows and Linux encryptors, for $10,000.
“vanhelsing ransomware supply code for promote: embrace TOR keys + internet panel for admin + chat + file server + weblog embrace database all the things,” th30c0der posted to the RAMP discussion board.
As first reported by Emanuele De Lucia, the VanHelsing operators determined to beat the vendor to punch, releasing the supply code themselves and stating that the th30c0der is considered one of their outdated builders making an attempt to rip-off individuals.
“Right this moment we’re asserting that we’re publishing the outdated sources codes and can quickly come again with the brand new and improved model of the locker(VanHelsing 2.0),” the VanHelsing operator posted to RAMP.
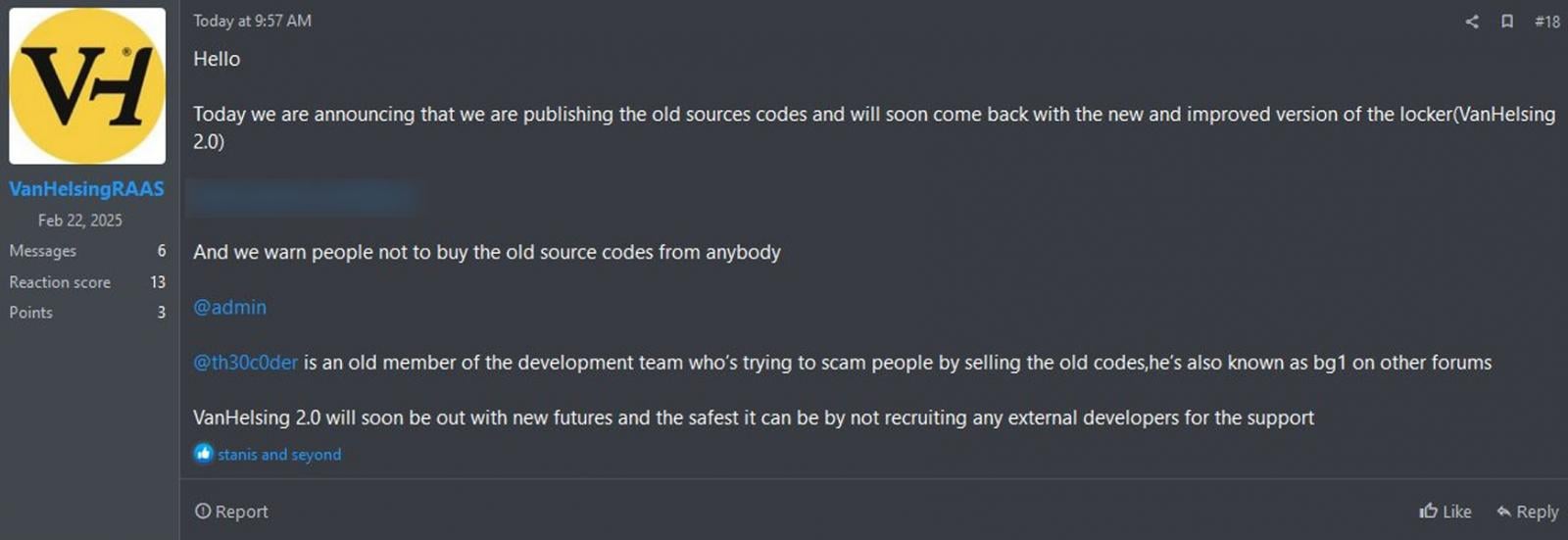
Nevertheless, this leaked information is incomplete in comparison with what the 30c0der says they’ve, because it doesn’t embrace the Linux builder or any databases, which might be far more useful for regulation enforcement and cybersecurity researchers.
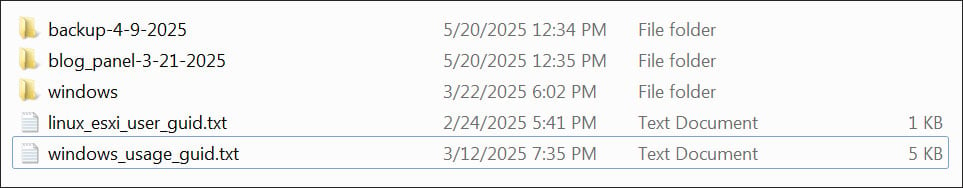
BleepingComputer has obtained the leaked supply code and has confirmed that it accommodates the respectable builder for the Home windows encryptor and the supply code for the affiliate panel and information leak website.
Supply: BleepingComputer
The builder’s supply code is considerably of a multitude, with the Visible Studio undertaking information discovered within the “Launch” folder, which is usually used to carry compiled binaries and construct artifacts.
Whereas full, utilizing the VanHelsing builder would require some work, because it connects again to the affiliate panel, which was operating 31.222.238[.]208, to obtain information used for the construct course of.
Supply: BleepingComputer
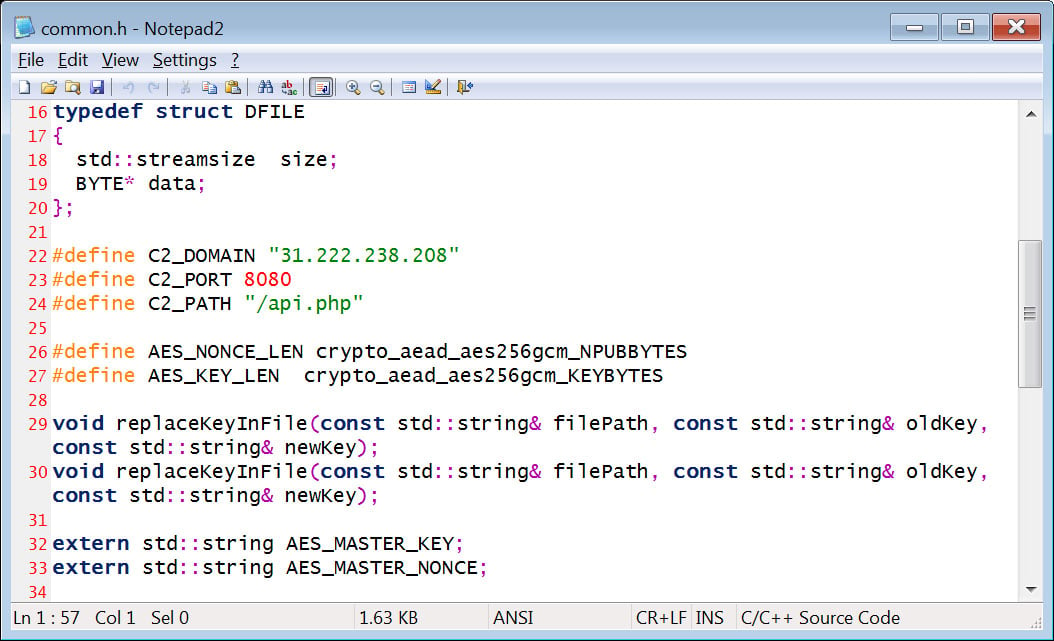
Nevertheless, the leak additionally consists of the supply code for the affiliate panel, which hosts the api.php endpoint, so risk actors may modify the code or run their very own model of this panel to get the builder to work.
The archive additionally accommodates the supply code for the Home windows encryptor, which can be utilized to create a standalone construct, the decryptor, and a loader.
Supply: BleepingComputer
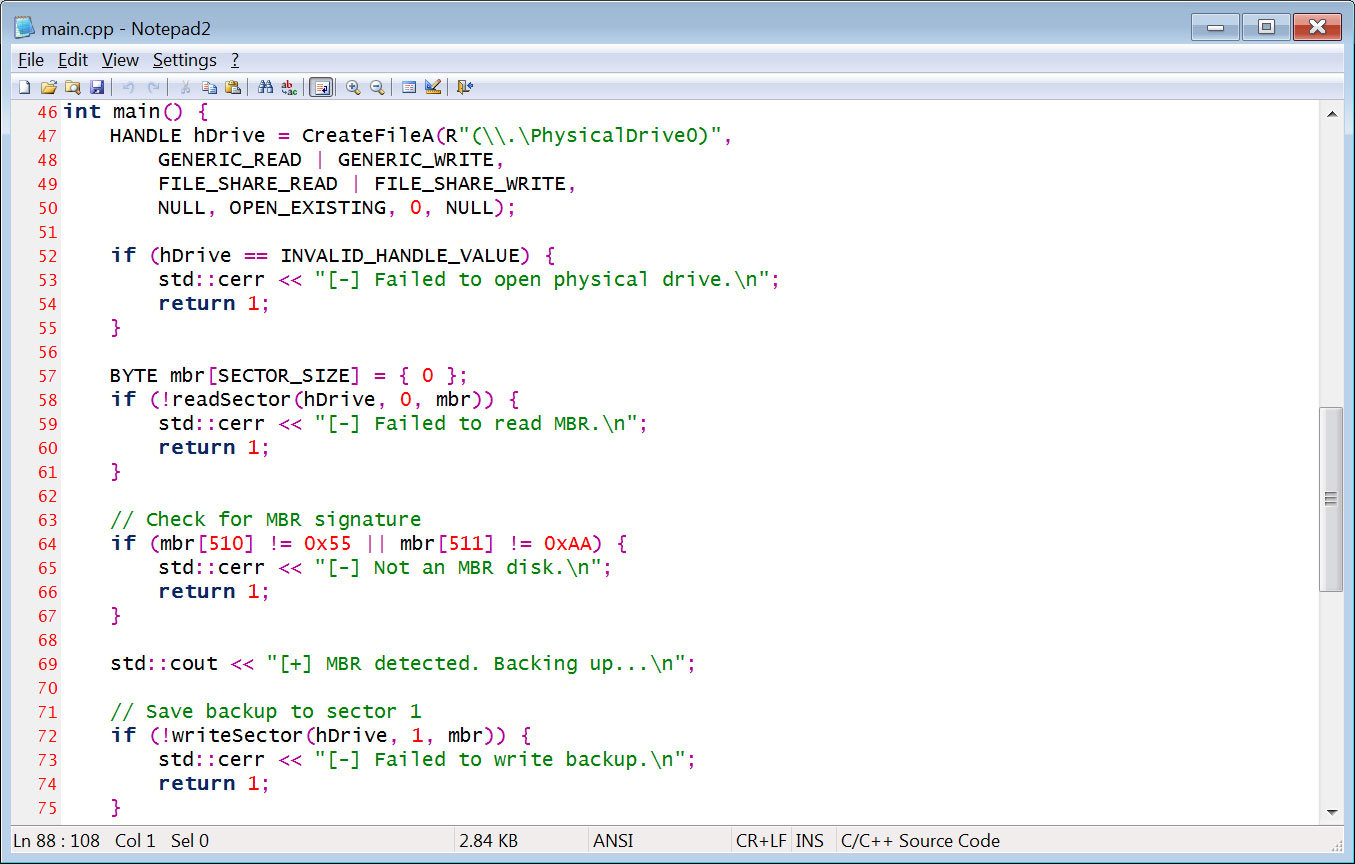
The leaked supply code additionally revealed that the risk actors have been making an attempt to construct an MBR locker that might change the grasp boot report with a customized bootloader that shows a lock message.
Supply: BleepingComputer
This leak isn’t the primary time a ransomware builder or encryptor supply code has been leaked on-line, which allowed new ransomware teams or particular person risk actors to rapidly conduct assaults.
In June 2021, the Babuk ransomware builder was leaked, permitting anybody to create encryptors and decryptors for Home windows and VMware ESXi. The Babuk leak has turn out to be one of many most generally used builders to conduct assaults on VMware ESXi servers.
In March 2022, when the Conti ransomware operation suffered a knowledge breach, its supply code was additionally leaked on-line. Different risk actors rapidly used this supply code in their very own assaults.
In September 2022, the LockBit ransomware operation suffered a breach when an allegedly disgruntled developer leaked the gang’s builder. This too has turn out to be extensively utilized by different risk actors to at the present time.



