
Microsoft has fastened a recognized situation stopping Linux from booting on dual-boot techniques with Safe Boot enabled after putting in the August 2024 Home windows safety updates.
The listing of affected techniques consists of these working shopper (Home windows 10 and Home windows 11) and server (Home windows Server 2012 and later) OS variations.
This situation is triggered by a Safe Boot Superior Focusing on (SBAT) replace that blocks UEFI shim bootloaders susceptible to exploits focusing on the CVE-2022-2601 GRUB2 Safe Boot bypass.
Whereas Microsoft mentioned within the CVE-2022-2601 advisory that this SBAT replace would not be delivered to units the place twin booting is detected, it additionally acknowledged that the dual-boot detection did not detect some custom-made strategies of dual-booting and utilized the replace anyway.
As revealed by many Linux customers (working a variety of distros, together with however not restricted to Ubuntu, Zorin OS, Linux Mint, and Pet Linux), their techniques stopped booting after putting in the August 2024 Home windows updates, and the SBAT replace was incorrectly utilized.
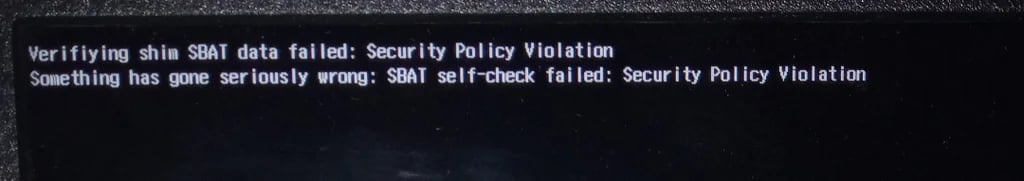
Microsoft confirmed the recognized situation following widespread stories, saying that affected customers noticed “One thing has gone severely unsuitable: SBAT self-check failed: Safety Coverage Violation” errors on techniques rendered unbootable.
Mounted after 9 months
This week, 9 months after confirming the difficulty, Microsoft introduced that the Might 2025 Patch Tuesday safety updates ought to repair the boot issues for all affected customers.
“This situation was resolved by Home windows updates launched Might 13, 2025 [..], and later,” Redmond famous in a Home windows launch well being replace. “We advocate you put in the most recent replace in your machine because it incorporates vital enhancements and situation resolutions, together with this one.”
The repair comes after the corporate shared a brief workaround in late August, weeks after the primary person stories surfaced, to assist revive impacted dual-boot techniques, requiring them to delete the SBAT replace and making certain that future SBAT updates would not be put in.
On September 19, it additionally stopped making use of the problematic SBAT replace to the firmware mechanically, advising those that wish to stop future SBAT updates in Home windows to run the next command:
reg add HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecureBootSBAT /v OptOut /d 1 /t REG_DWORD
“This recognized situation solely happens with the set up of the August 2024 safety and preview updates. The September 2024 safety replace and later updates don’t include the settings that prompted this situation,” Microsoft added.



