
Within the period of interconnected gadgets, securing IoT programs is paramount to guard delicate information from unauthorized entry. This mission demonstrates an IoT Safety System leveraging AES (Superior Encryption Commonplace) encryption to remodel plain-text information right into a “secret code” that solely licensed customers can decipher.
By integrating AES with an IndusBoard Coin, we be certain that information transmitted over Wi-Fi, resembling sensor readings or consumer messages, stays confidential and tamper-proof. The system aligns with the IndusBoard Coin Safety System idea, emphasizing strong encryption for IoT purposes.
AES is a symmetric encryption algorithm broadly used for its effectivity and power. Right here, we use it to encrypt information on the Coin board, which helps hardware-accelerated AES through its cryptographic engine. This mission evolves in two elements:
- A standalone encryption demo utilizing AES-256.
- An IoT sender-receiver system with an online UI for encrypting and decrypting messages in AP/STA mode.
Supported on any board and CHIP that options built-in AES {hardware} acceleration. The IndusBoard Coin Safety System may theoretically combine with IoT, utilizing AES alongside safe components just like the ATECC608A for key storage, although this mission focuses on software-based AES for simplicity.
AES (Superior Encryption Commonplace) is a symmetric encryption algorithm established by the U.S. Nationwide Institute of Requirements and Expertise (NIST) in 2001. It’s broadly used to safe information in purposes starting from banking to IoT gadgets as a result of its velocity, effectivity, and strong safety. AES operates on fixed-size blocks of knowledge (16 bytes or 128 bits) and helps key sizes of 128, 192, or 256 bits—right here, we use AES-128 and AES-256 variants.
How AES Works
- Key Enlargement: The encryption key (e.g. 32 bytes for AES-256) is expanded right into a set of spherical keys utilizing a key schedule. Every spherical secret’s utilized in subsequent transformation steps.
- Encryption Course of:
- SubBytes: Every byte of the 16-byte block is substituted utilizing a predefined S-box (Substitution field), including non-linearity.
- ShiftRows: Rows of the block are shifted cyclically to diffuse the info.
- MixColumns: Columns are combined utilizing a mathematical transformation to additional scramble the info.
- AddRoundKey: The block is XORed with a spherical key. This course of repeats for a number of rounds (10 for AES-128, 14 for AES-256).
- Decryption: The inverse operations (InvSubBytes, InvShiftRows, and so forth.) are utilized with the identical key to recuperate the unique information.
- Modes: AES can function in modes like ECB (Digital Codebook) or CBC (Cipher Block Chaining). ECB encrypts every block independently, whereas CBC makes use of an Initialization Vector (IV) to chain blocks, enhancing safety.
Invoice of Supplies
| Merchandise | Description | Amount |
|---|---|---|
| Board with AES Help and has a built-in safe engine (IndusBoard Coin) | IoT Board with AES encryption system | 1 |
| Wi-Fi Community | For testing | 1 |
| Micro USB Cable | For programming and energy | 1 |
Half 1: Standalone AES-256 Encryption Demo
Code Rationalization
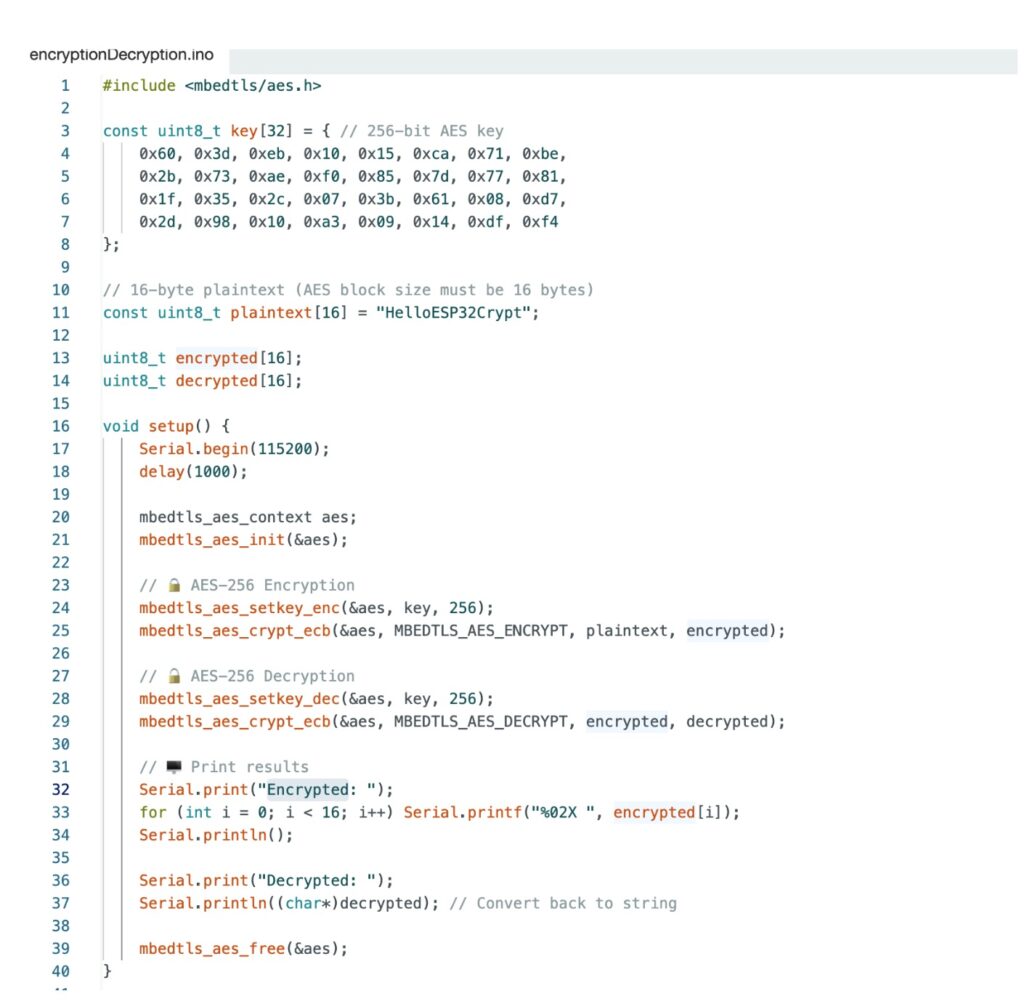
The primary code demonstrates AES-256 encryption and decryption utilizing the mbedtls library.
Right here in code, the inbuilt AES encryption is named, then a 256-bit AES encryption KEY is inserted within the code array. Subsequent, it has a default message that you would be able to change for encryption. Now, add the code.
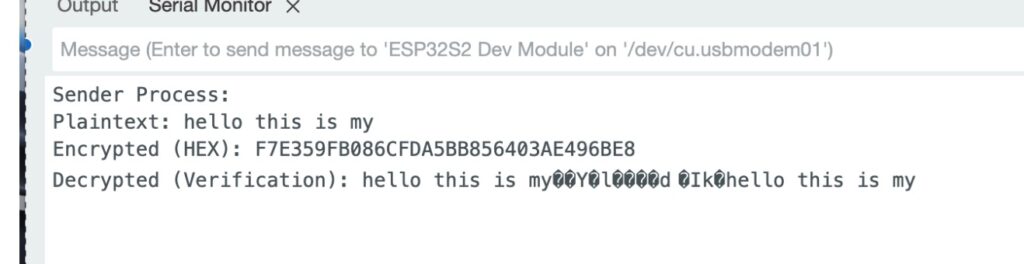
Testing AES-256 Encryption and Decryption
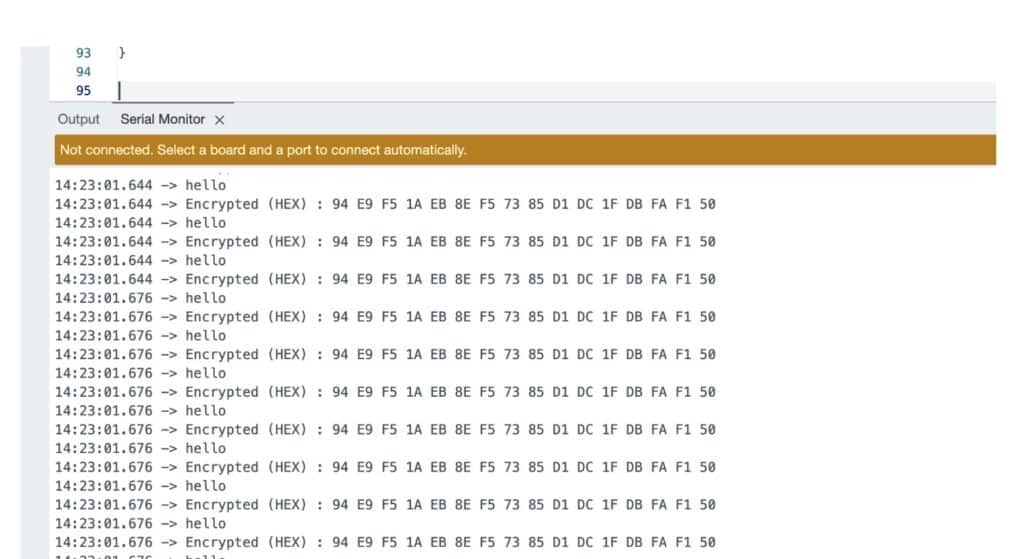
Add the code to Coin through Arduino IDE. Open the Serial Monitor (115200 baud).
Then you possibly can see the encryption and decryption course of in serial.
Half 2: IoT Encrypted Knowledge Transmission with Net UI
Venture Continuation: Sender-Receiver with Encryption
In our IoT system, AES encrypts messages despatched from an online UI to a COIN sender, making certain that intercepted Wi-Fi site visitors seems as gibberish (e.g., 6EF23A…) with out the important thing. The receiver decrypts it utilizing the shared key, restoring the unique message.
This protects confidentiality and aligns with the InusBoard Coin Safety System idea by making information readable solely to licensed events.
This code modifies the earlier sender-receiver system to make use of AES-128 with an online UI, permitting customers to enter messages, see encrypted output, and decrypt them on the Serial Monitor.
Code
- WiFi.h: Configures the ESP32 as a Wi-Fi Entry Level (AP) to host the UI.
- WebServer.h: Manages HTTP requests and responses for the net interface.
- mbedtls/aes.h: Supplies the AES encryption/decryption capabilities from the mbedTLS library, included within the ESP32 Arduino core.
ssid and password: Outline the AP’s identify and password (should be 8+ characters).
server(80): Creates an online server on port 80, the default HTTP port.
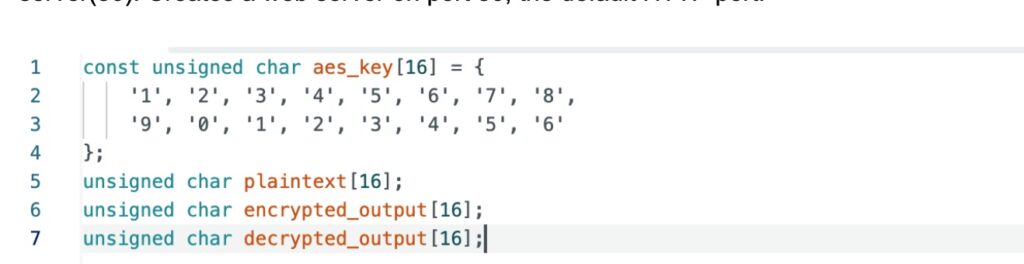
aes_key: A 16-byte (128-bit) key for AES-128, specified as particular person characters to keep away from string termination points.
plaintext: Shops the 16-byte enter message.
encrypted_output: Holds the encrypted ciphertext.
decrypted_output: Shops the decrypted outcome for verification.
Testing IoT Encrypted Knowledge Transmission with Net UI

- Hook up with the “IndusIoT safety” Wi-Fi community (password: “12345678”).
- Open a browser and go to http://192.168.4.1.
- Enter a message (e.g., “Test1234”) and submit.
- Verify the Serial Monitor (115200 baud) for encrypted output and decrypted message




