7 p.m., finish of the primary day of safety operations and first day of coaching course. My teammate and pal René Straube and I take pleasure in a well-deserved dinner at an Italian restaurant close to the Excel convention heart. That is his first time accompanying us to the Black Hat Community Operations Middle (NOC), so naturally, we talk about his impressions.
After sharing many constructive issues, René mentioned to me: “You realize, what’s irritating as an XDR analyst is that fairly often, throughout an incident, we see community detections to a public IP deal with, however we do not know why that connection was made as a result of we don’t have EDR (and agent on the endpoints), and it might be actually useful to at the very least know which area or URL the consumer was making an attempt to speak with.” He additionally instructed me that he thought we had all the data we would have liked in Splunk, as a result of we accumulate DNS logs from Palo Alto Networks NGFW and connection logs from Corelight OpenNDR, which often comprise details about the domains linked to that IP deal with. The NOC management enabled Cisco and different companions to introduce extra pre-approved software program and {hardware} options, enhancing our inside effectivity and increasing our visibility capabilities; nevertheless, Cisco isn’t the official supplier for Prolonged Detection & Response, Safety Occasion and Incident Administration, Firewall, Community Detection & Response or Collaboration.
“Okay, I perceive, René!” If we have now this data someplace, we are able to most likely automate the method and enrich your incident robotically or on the request of an analyst (playbook). Let’s go forward and attempt to take it a step additional with the alternative situation. Should you see a site in an incident, possibly what you’re making an attempt to discover out as an analyst is which IP deal with was linked to that area to confirm whether or not the connection was approved by the firewall.
The subsequent day, at 7 a.m., on the NOC/SOC, we start engaged on it and arrange two workflows:
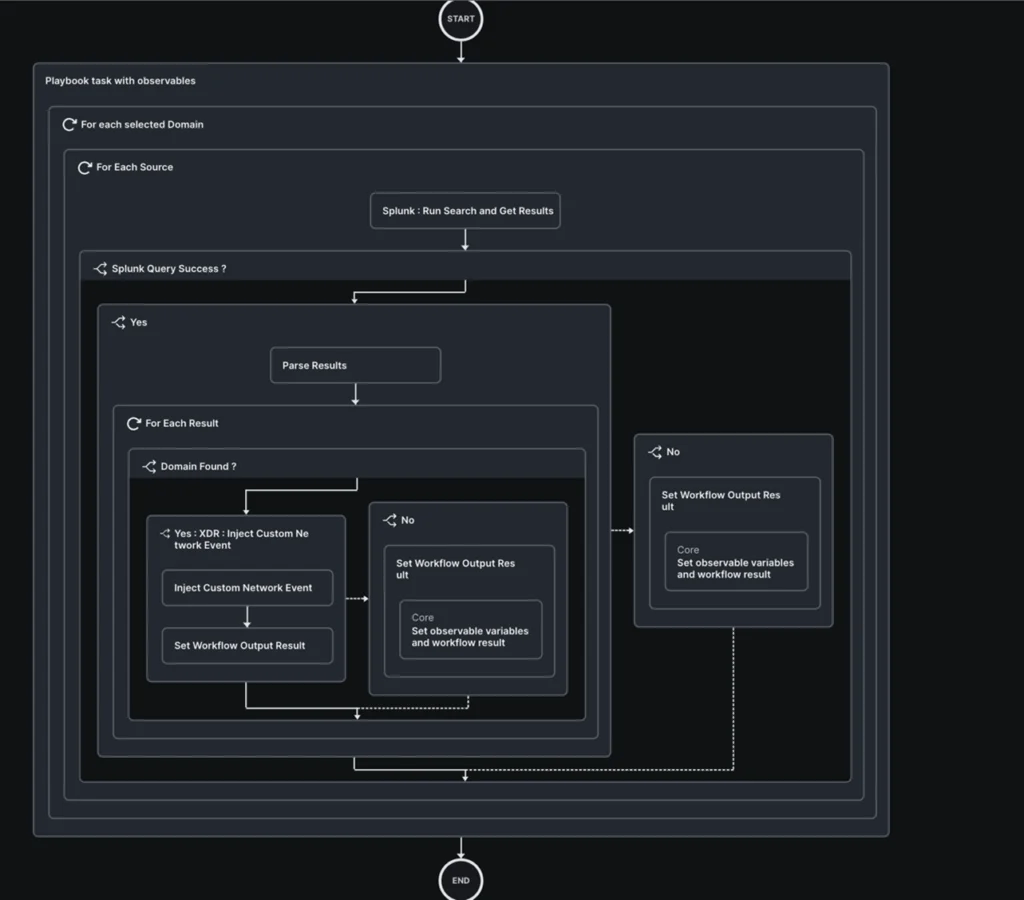
- Discover Domains associated to IPs
- Enter: IP deal with(es)
- Question Splunk to acquire Palo Alto Community firewall DNS logs and extract the area queried with this IP deal with because the response
- If no outcomes are obtained (DNS bypass), question Splunk to acquire Corelight connection logs and extract the domains related to this IP deal with
- Inject this DNS decision occasion into the XDR knowledge analytics platform, in order that it’s correlated along with your incident and enriched
- Discover IPs associated to Area
- Enter: Domains(s)
- Question Splunk to acquire Palo Alto Community firewall DNS logs and extract the area queried with this IP deal with because the response
- If no outcomes are obtained (DNS bypass), question Splunk to acquire corelight connection logs and extract the domains related to this IP deal with
- Inject this DNS decision or Community Connection occasion into the XDR knowledge analytics platform, in order that it’s correlated along with your incident and enriched.
Thirty minutes of coding later, two new actions had been made out there to the analyst within the incident response playbook, guiding them and saving them effort and time.


Let’s see how this is applicable to an incident:
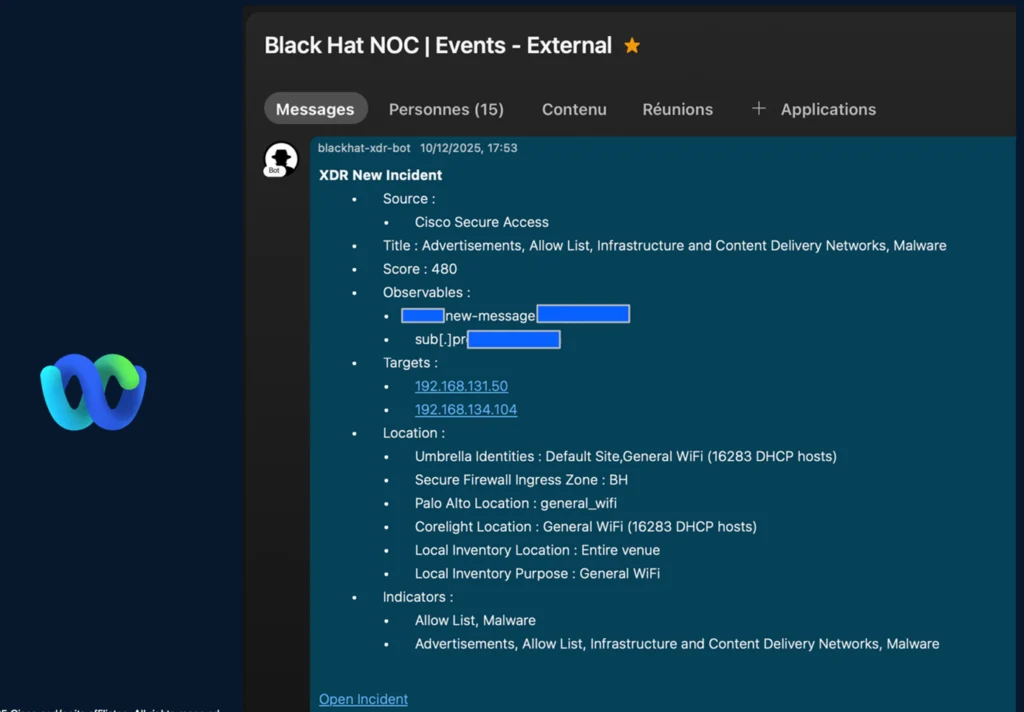
It all begins with a Webex notification a few new incident associated to domains related to malicious exercise by Cisco Safe Entry (Umbrella DNS) originating from two inside IP addresses linked to the Black Hat Europe normal Wi-Fi community.

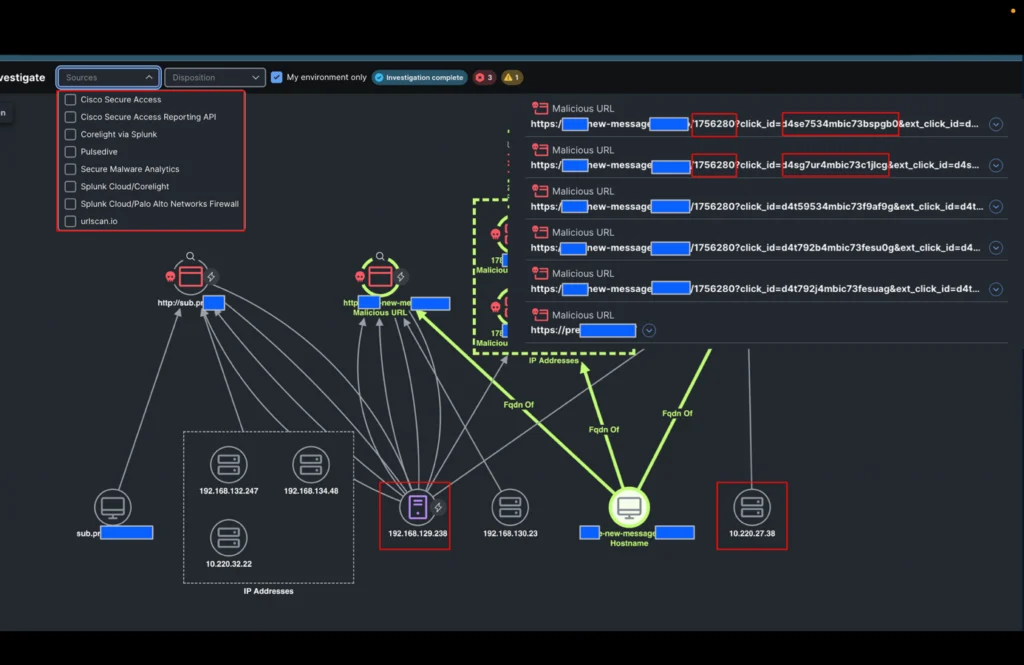
Once we opened the incident, a 3rd inside IP deal with was already recognized by Cisco XDR.
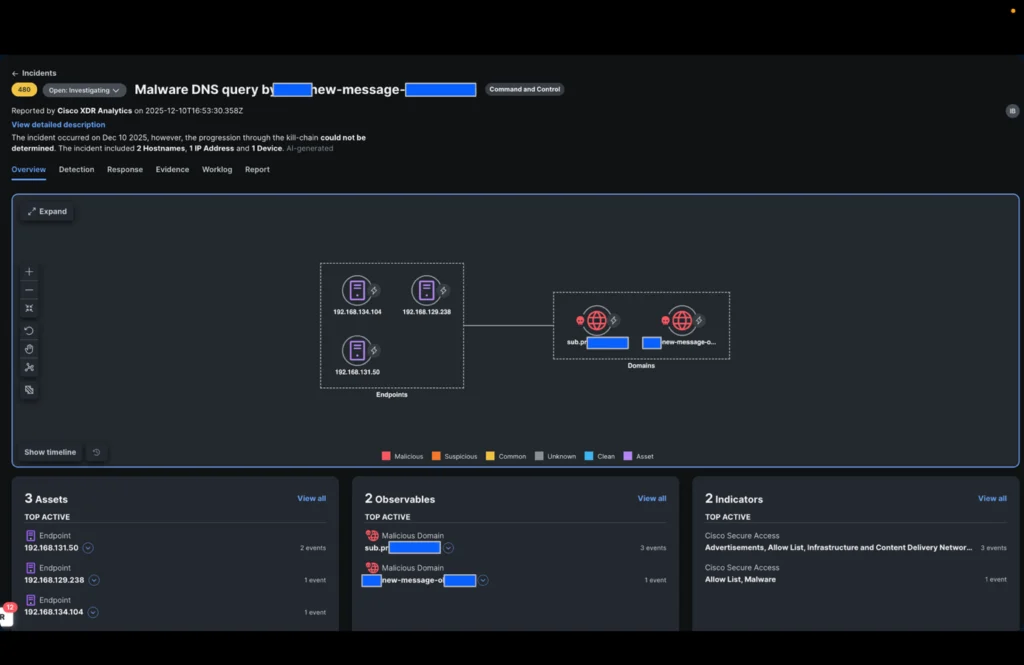

The XDR incident confirms that DNS queries had been allowed and enrichment from menace intelligence built-in into Cisco XDR confirmed that the domains had been certainly malicious.
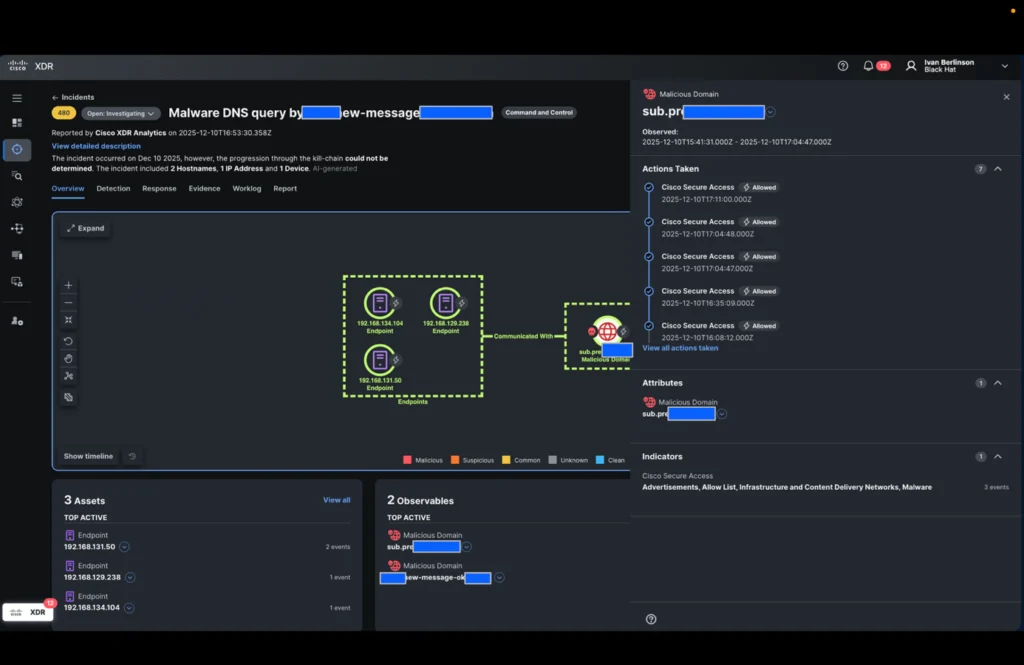

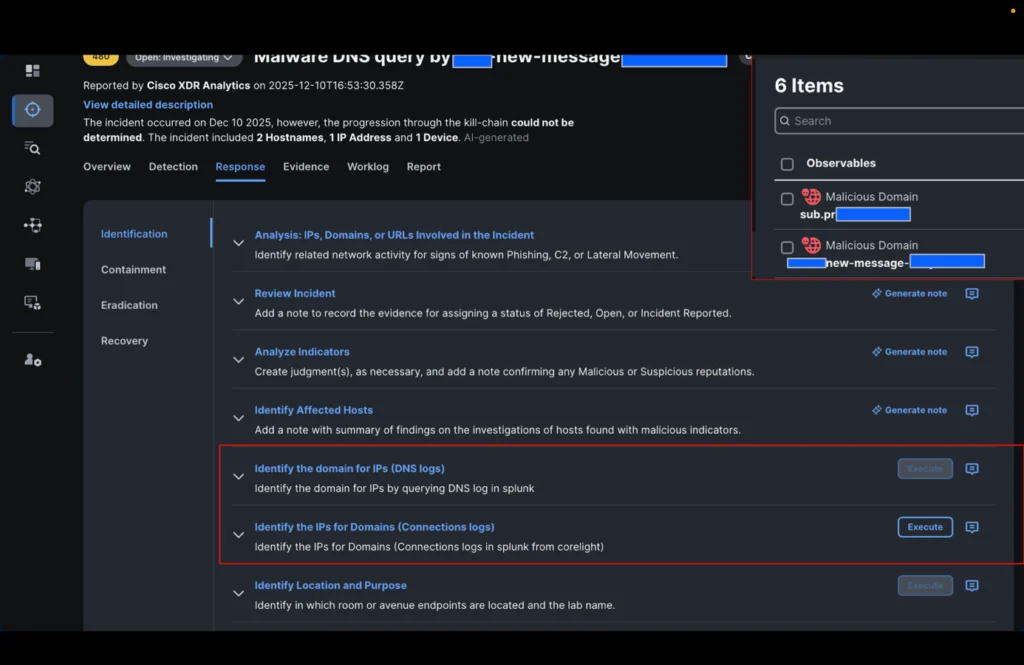
Our analyst should now decide whether or not the connections to the IP addresses related to these domains had been profitable and what they’re. He subsequently triggers the brand new playbook motion within the identification step: “Establish the IP addresses of the domains” and selects the 2 domains within the incident.
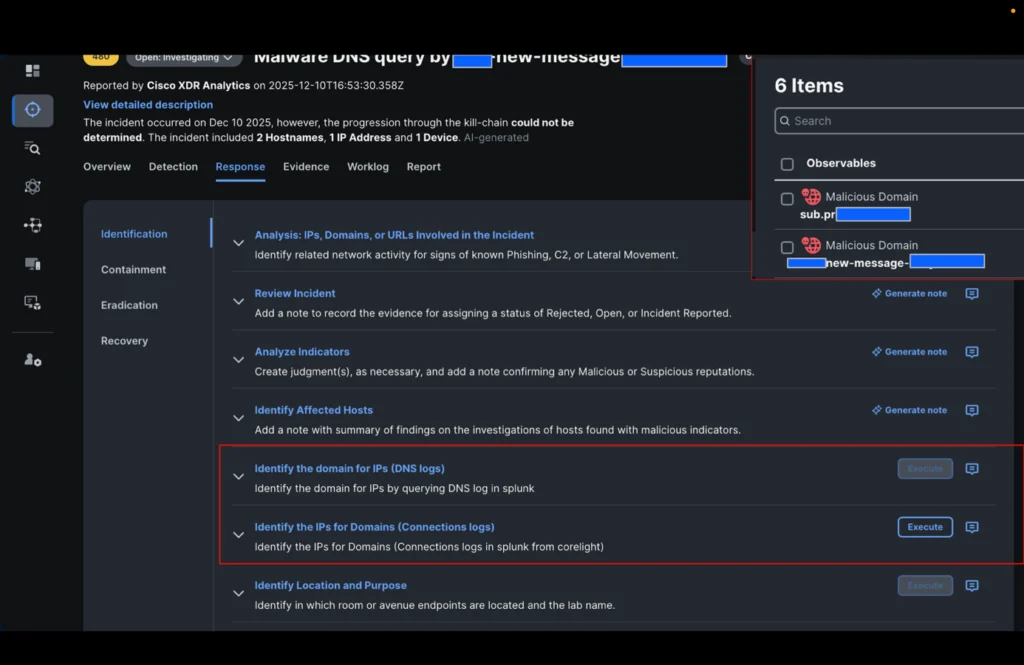

Within the time it took to drink a cup of espresso, the incident was enriched with all of the IP addresses seen in Black Hat Palo Alto Networks’ DNS logs and Corelight connection logs associated to those domains.
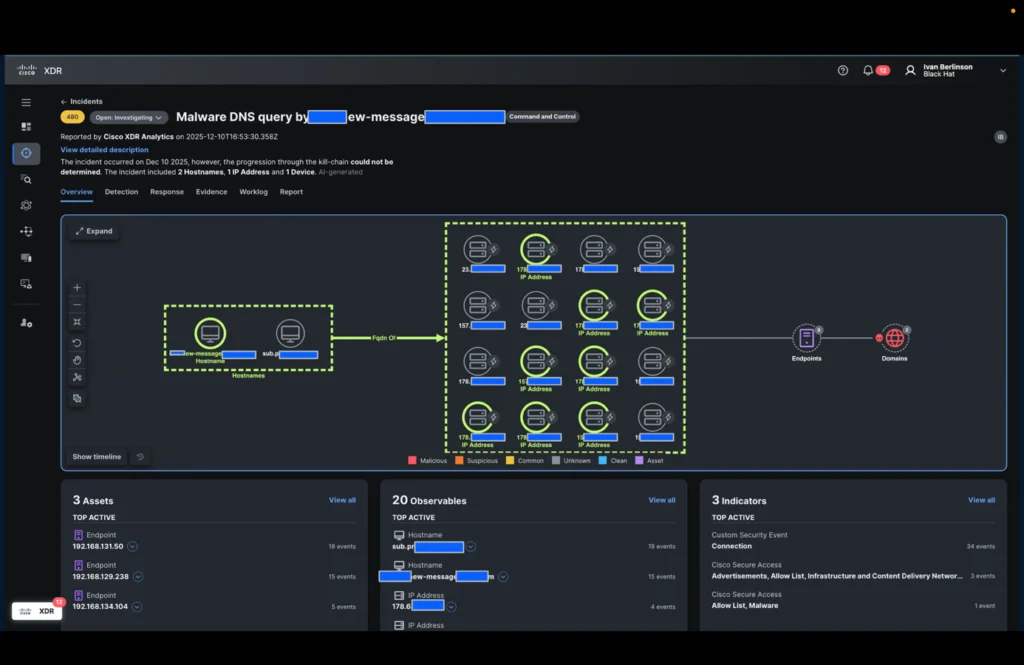

It was then simple for the analyst to analyze all IP addresses concerned within the incident with a single click on (utilizing XDR ribbons) and procure extra data.
- An extra inside IP deal with speaking with a number of the IP addresses
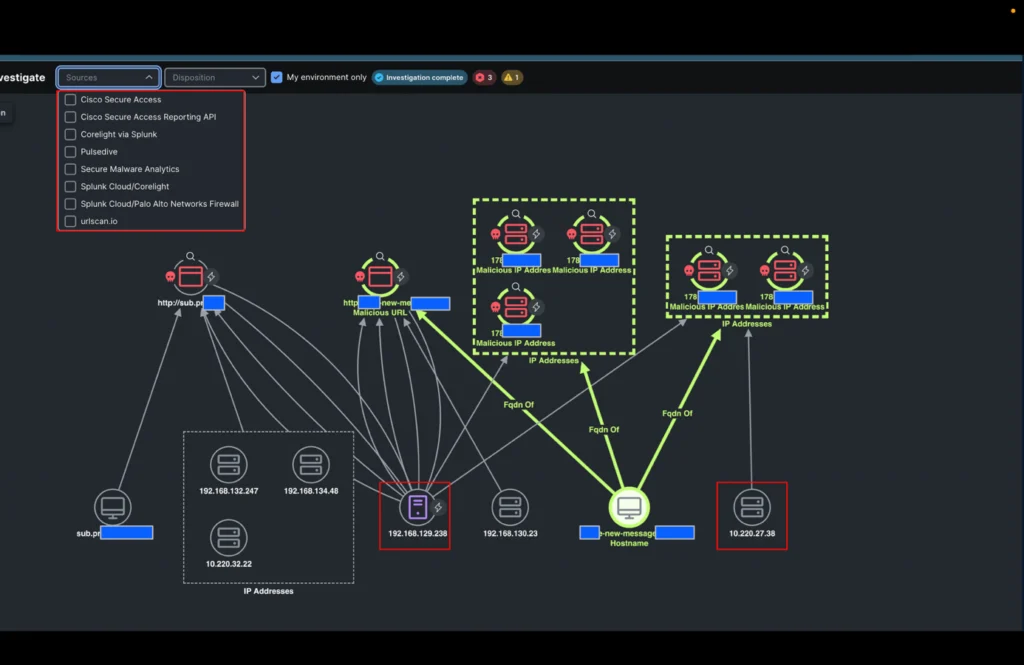

- A sample within the URLs linked to those domains confirming a doubtlessly profitable phishing assault

Conclusion
Because of this innovation from Rene’s thought, it took the analyst only some minutes to substantiate the incident and collect sufficient helpful data earlier than forwarding it to our Stage 3 analyst, Tony Iacobelli, Supervisor of the Splunk Cloud Incident Response group.
He additionally emphasizes the significance of listening to analysts’ suggestions and utilizing automation to unravel their issues.
You possibly can learn the opposite blogs from our colleagues at Black Hat Europe.
About Black Hat
Black Hat is the cybersecurity trade’s most established and in-depth safety occasion sequence. Based in 1997, these annual, multi-day occasions present attendees with the most recent in cybersecurity analysis, growth, and traits. Pushed by the wants of the group, Black Hat occasions showcase content material instantly from the group by way of Briefings shows, Trainings programs, Summits, and extra. Because the occasion sequence the place all profession ranges and educational disciplines convene to collaborate, community, and talk about the cybersecurity subjects that matter most to them, attendees can discover Black Hat occasions in america, Canada, Europe, Center East and Africa, and Asia. For extra data, please go to the Black Hat web site.
We’d love to listen to what you suppose! Ask a query and keep linked with Cisco Safety on social media.
Cisco Safety Social Media


