
A 3AM ransomware affiliate is conducting extremely focused assaults utilizing e-mail bombing and spoofed IT assist calls to socially engineer workers into giving credentials for distant entry to company techniques.
This tactic was beforehand linked to the Black Basta ransomware gang and later noticed in FIN7 assaults, however its effectiveness has pushed a wider adoption.
Sophos reviews seeing not less than 55 assaults leveraging this method between November 2024 and January 2025, linked to 2 distinct risk clusters.
These assaults adopted the BlackBasta playbook, together with e-mail bombing, vishing by way of Microsoft Groups, and Fast Help abuse. The leak of Black Basta’s inside conversations helped different risk actors stand up to hurry, because it included a template to make use of throughout Microsoft Groups phishing assaults impersonating IT assist desks.
The 3AM ransomware assault, focusing on a Sophos shopper, occurred within the first quarter of 2025 and used the same method however with a twist of actual cellphone phishing as an alternative of Microsoft Groups.
The risk actors spoofed the goal’s actual IT division’s cellphone quantity to make the decision seem reliable. The decision occurred throughout an e-mail bombing wave of 24 unsolicited emails obtained in three minutes.
The attacker satisfied the worker to open Microsoft Fast Help and grant distant entry, supposedly as a response to malicious exercise.
Subsequent, the attacker downloaded and extracted a malicious archive from a spoofed area, containing a VBS script, a QEMU emulator, and a Home windows 7 picture pre-loaded with QDoor backdoor.
QEMU was used to evade detection by routing community visitors by digital machines created on the platform, which allowed persistent, but undetected, entry to the community.
Via this implies, the attackers carried out reconnaissance utilizing WMIC and PowerShell, created an area admin account to attach by way of RDP, put in the industrial RMM instrument XEOXRemote, and compromised a site administrator account.
Though Sophos says its merchandise blocked lateral motion and protection deactivation makes an attempt, the attacker nonetheless exfiltrated 868 GB of information to Backblaze cloud storage utilizing the GoodSync instrument.
Sophos’ instruments additionally blocked subsequent makes an attempt to run the 3AM ransomware encryptor, so the harm was contained to information theft and the encryption of the compromised host.
Supply: Sophos
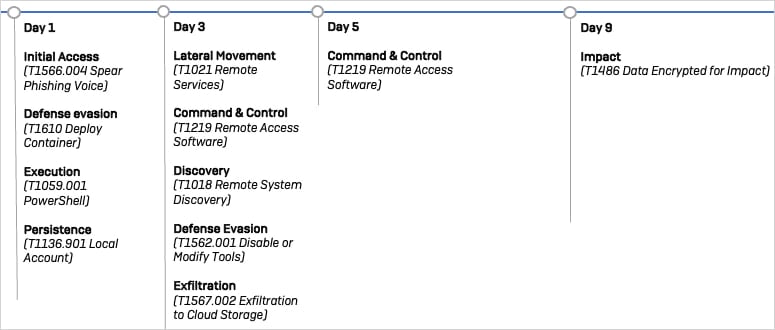
The assault lasted 9 days, with information theft concluded by day three, with the risk actors subsequently blocked from spreading additional.
Supply: Sophos
Sophos advised a number of key protection steps that may be taken to dam these assaults, together with auditing administrative accounts for poor safety, utilizing XDR instruments to dam unapproved reliable instruments like QEMU and GoodSync, and implementing signed scripts solely by way of PowerShell execution insurance policies.
It’s also really useful that obtainable indicators of compromise be used to arrange blocklists that forestall intrusion from recognized malicious sources.
Finally, e-mail bombing and voice phishing can solely be successfully blocked by growing worker consciousness.
The 3AM ransomware operation launched in late 2023 and was later linked to the Conti and Royal ransomware gangs.



